MazeRunner Responder Monitor
"Cymmetria’s MazeRunner platform lets you dominate an attacker’s movements from the very beginning and lead them to a monitored deception network."
I really like this product but after my first installation, I felt like I sort of rushed the process and I wanted to start over again. With a fresh install, I headed over to the Responder monitor. For those of you unfamiliar with Responder.py, it's wicked fun if you're an attacker, and not so much fun if you're a defender.
Even in situations where (you think) the environment is locked down, Responder might find a way. If you want to see an example of one of those situations: Domain Takeover with Responder, Runfinger, and Multirelay
MazeRunner offers us an opportunity to deceive the attacker. From the Story Wizard, we select Responder Monitor: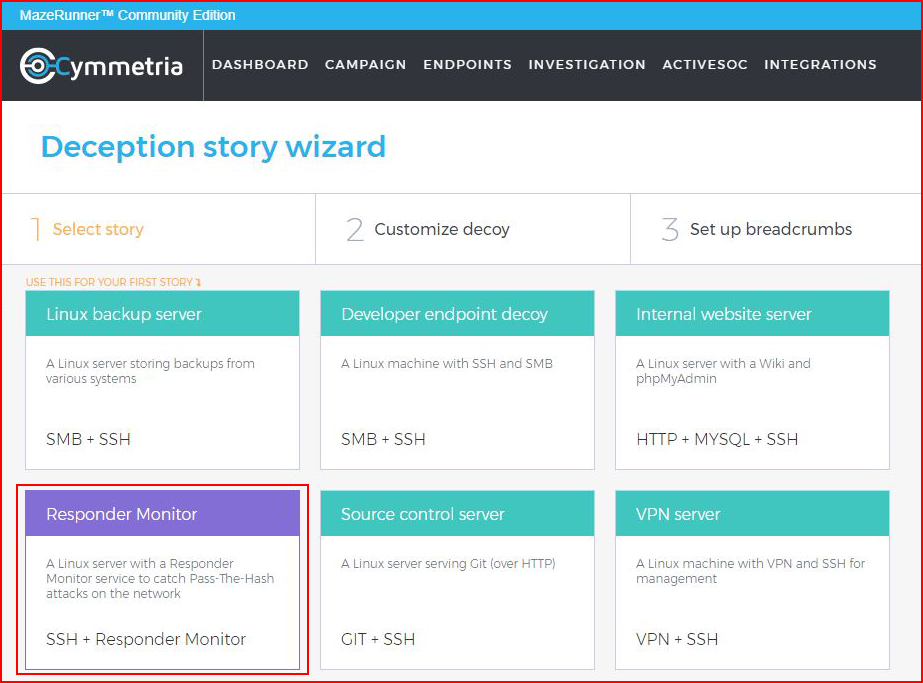
We configure our decoy:
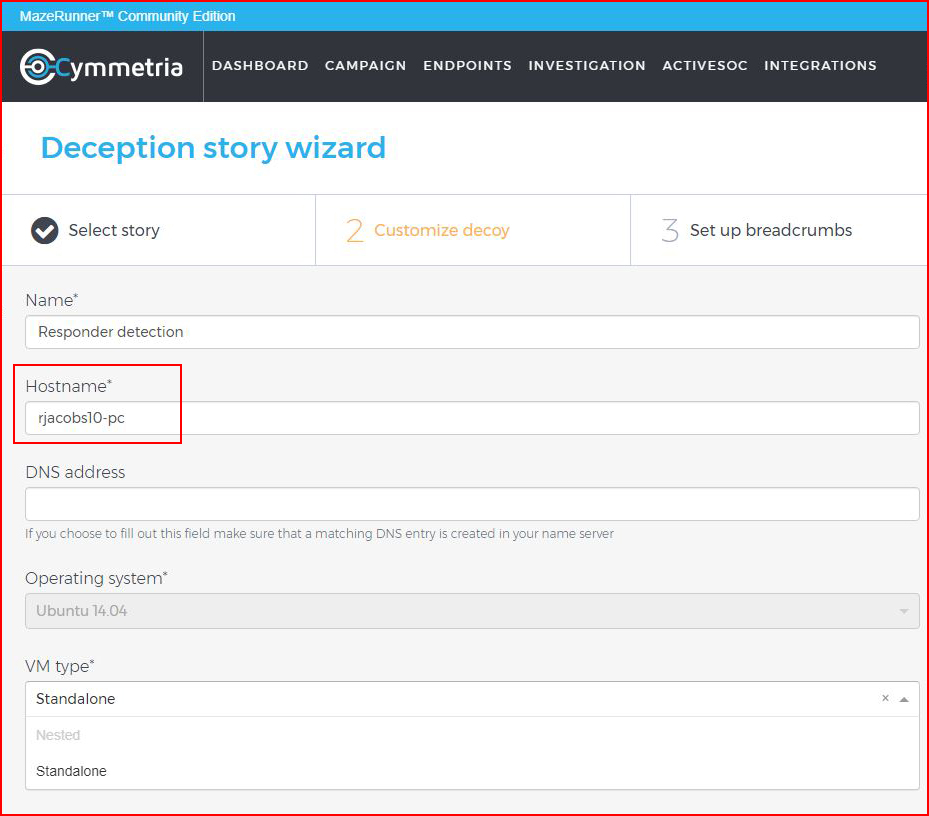
When we're finished, we have our configured decoy:
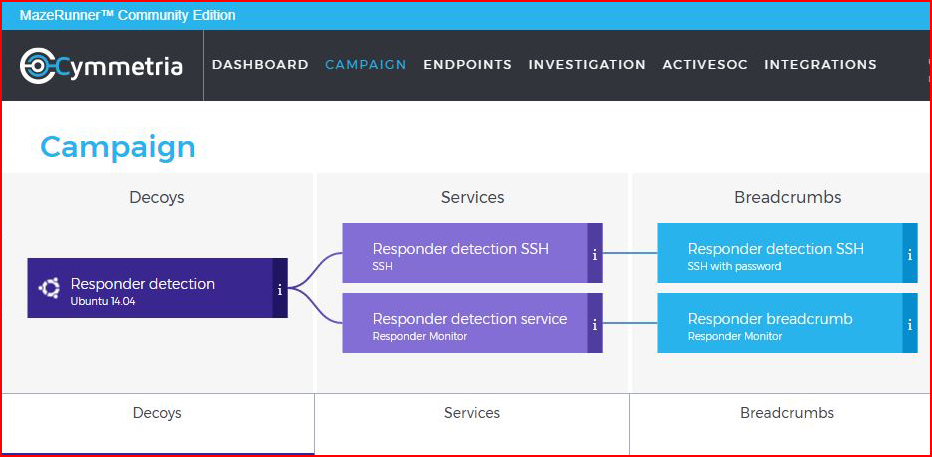
Here's the thing -- I've been playing around with this for a while now and I don't really care for the "Story" configuration. If we kill that decoy and we create another from scratch, we can have something specific. It's Burger King, have it your way:
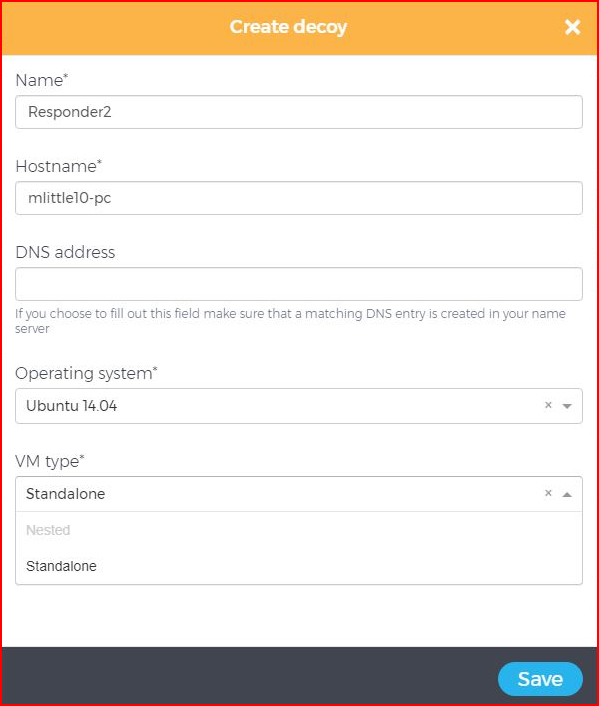
With our blank decoy, we add a service:
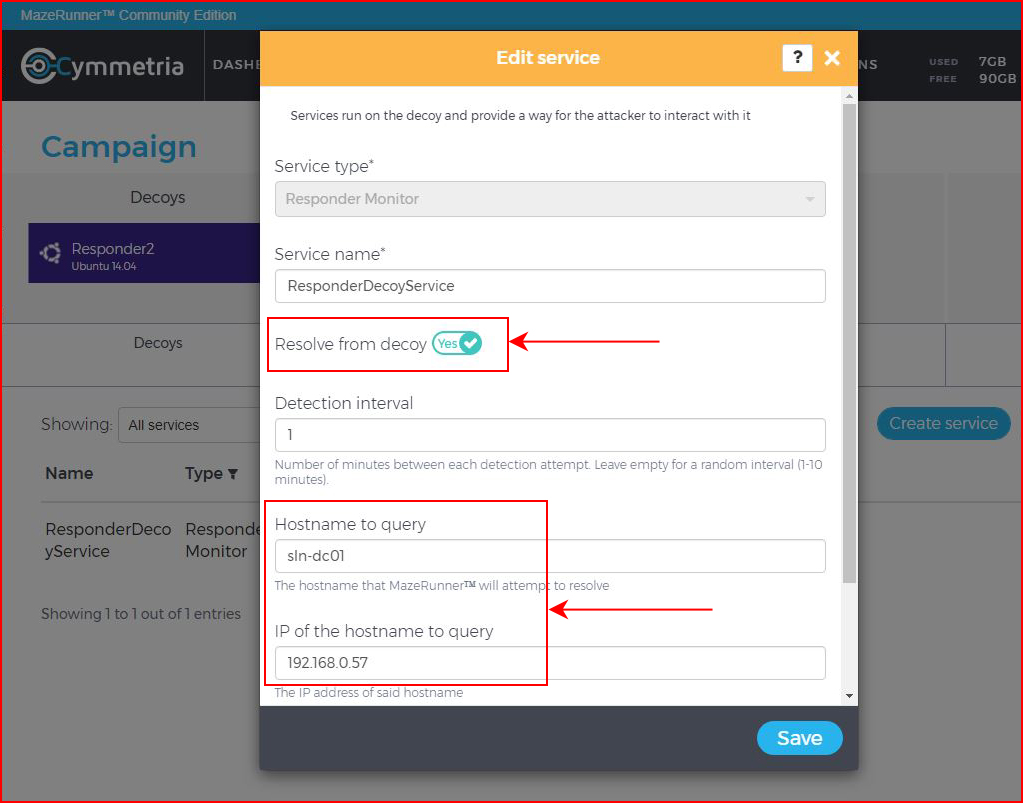
I'm still learning how this product works but if you don't enable Resolve from Decoy, we create a system but it won't trigger an alert because it won't send out a request to Responder. Configure it like I have above, create a fake Hostname but configure the IP address to the decoy. You could have another decoy on the network and point to it but I just have it pointing back to itself and that works well.
When we're finished, we have a slightly scaled down version of the "Story" decoy:
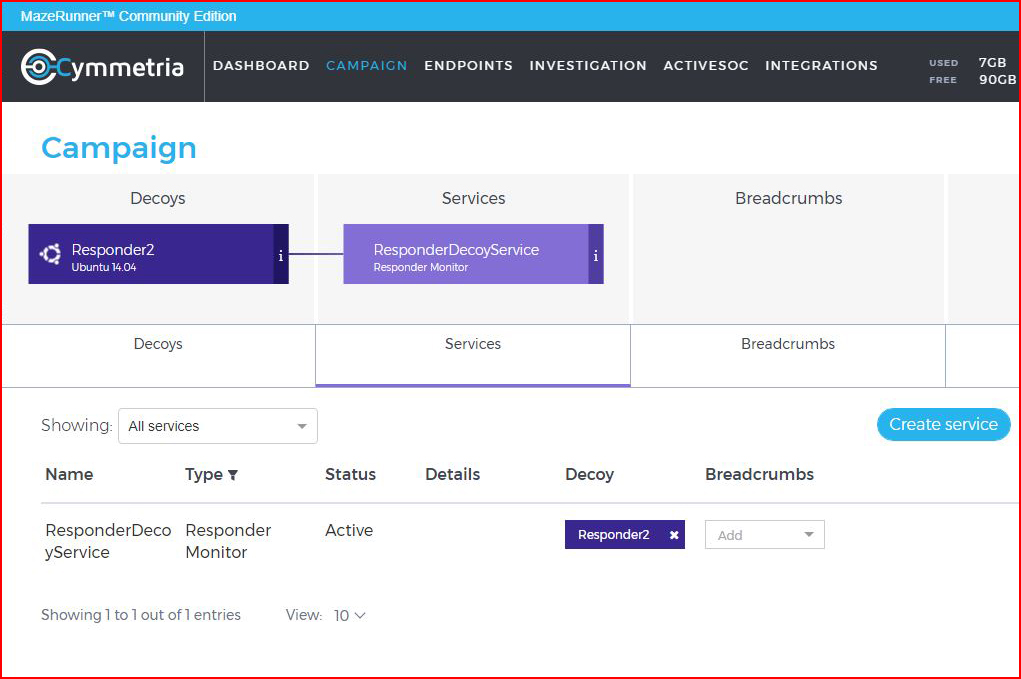
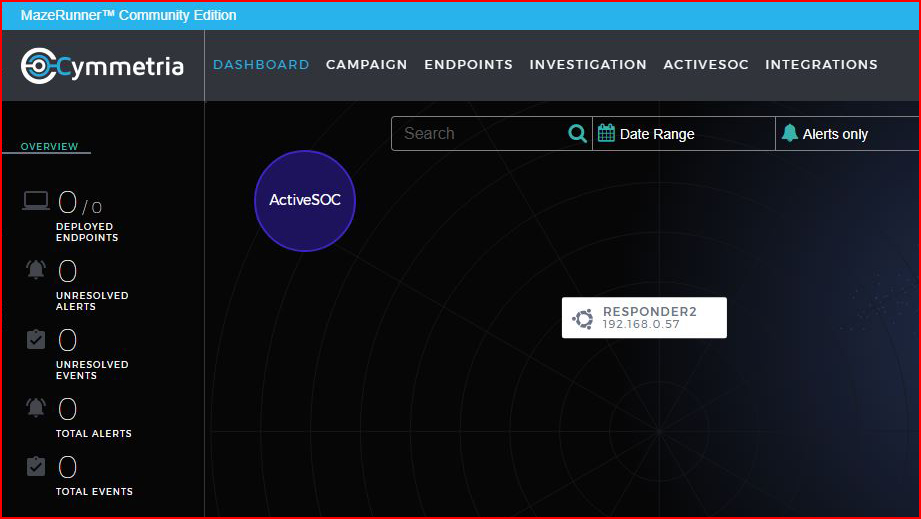
Once our decoy is active, we see it sitting happily on our dashboard:
We fire up Responder:
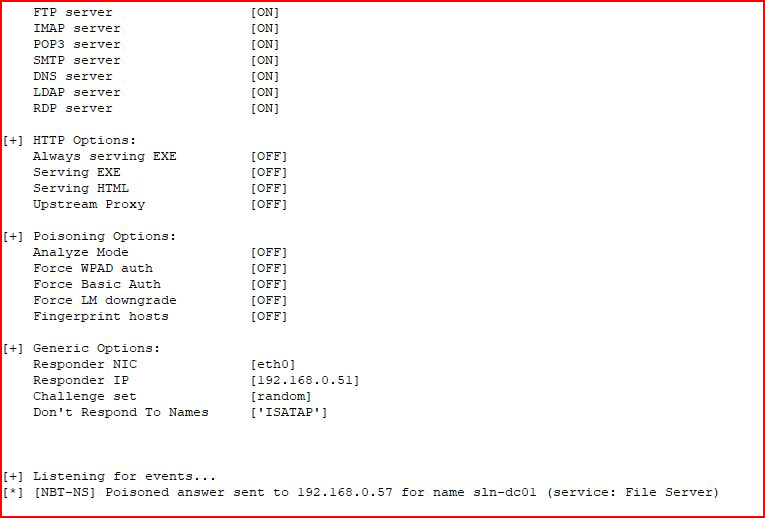
Moments later, it poisons our decoy and we see the alert on the dashboard:
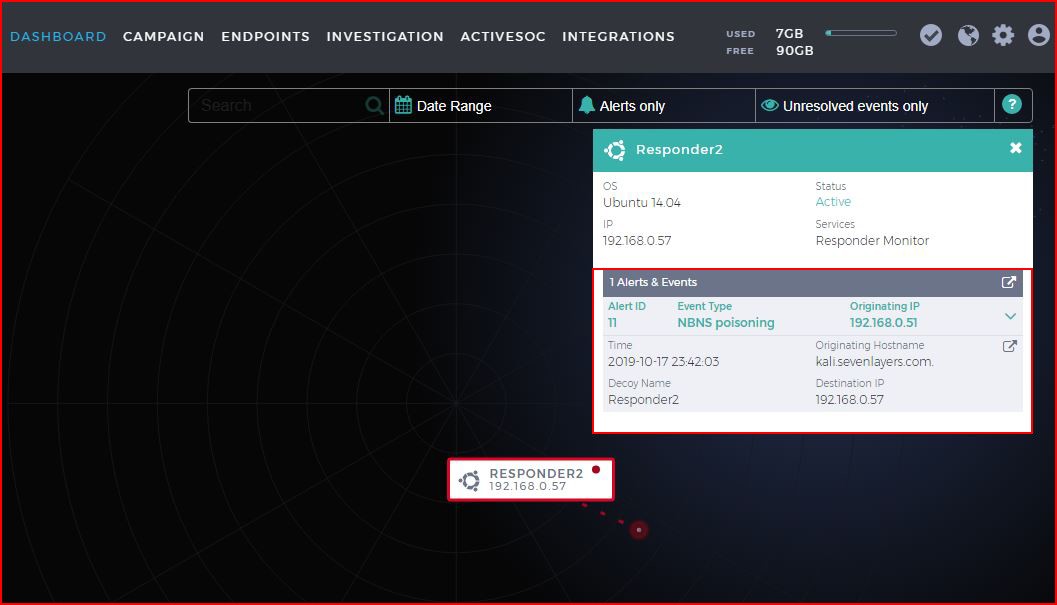
We also get an email alert:
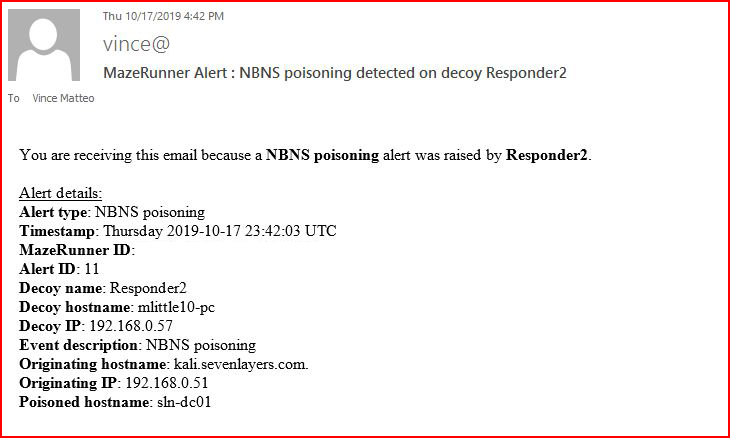
I've been working with a lot of honeypots, canary, and deception products lately but this one is the first I've seen with this feature. That is a must have!