GoPhish : Phishing and More...
"Gophish is a powerful, open-source phishing framework that makes it easy to test your organization's exposure to phishing."
Depending on where you look, and what they are trying to sell you, the percentage of attacks from phishing range from 30% - 90%. The Verizon Data Breach Investigations Report shows the percentage dropped in 2019 from 2018 by about 40%. Regardless, phishing is still an easy and viable attack vector. I can send phishing emails over and over again and the recipient only needs to make a mistake once. It's simple and it's effective.
For phishing awareness training, there are pay services, there are services that offer phishing as a secondary feature -- like Duo, and there are free products like GoPhish. Not only can you use phishing awareness tools test phishing, you can also use them as a tripwire of sorts -- more on that at the end of this post.
When we install GoPhish, unless we're running it from the same machine, we need to edit config.json to replace the localhost IP with our network IP.
We replace:
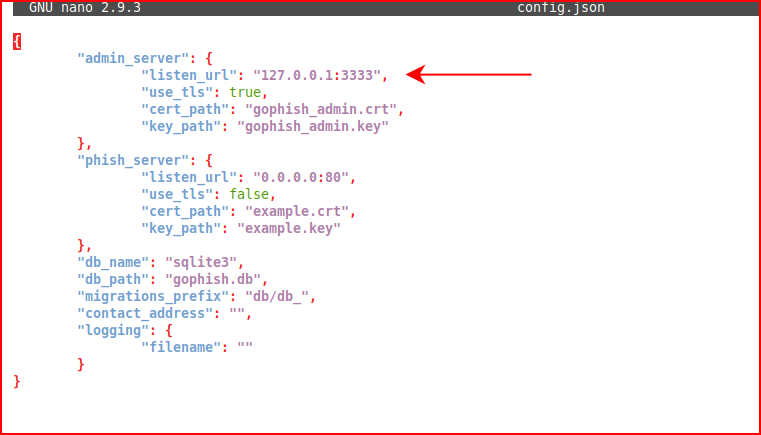
With this (your IP, of course):
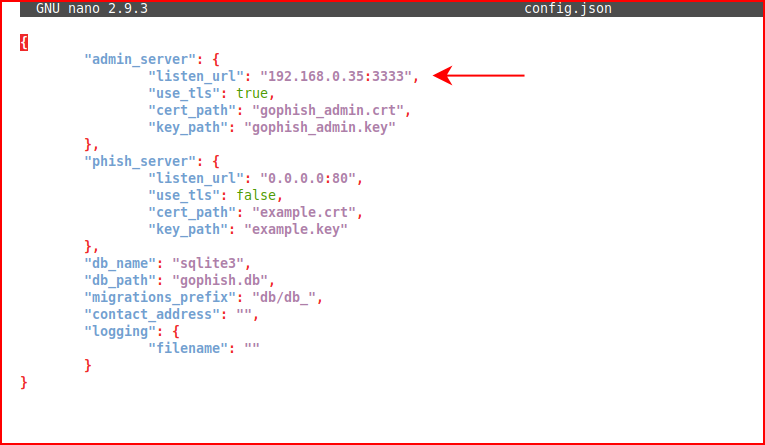
I'm running GoPhish out of /opt/phishing and I would point out that when you extract the zip, it dumps a bunch of files into the root of your working directory. In other words, don't unzip it into /opt or you'll have a mess.
For now, we're running GoPhish as root which is not a great idea but at this moment, we just want to get it running:
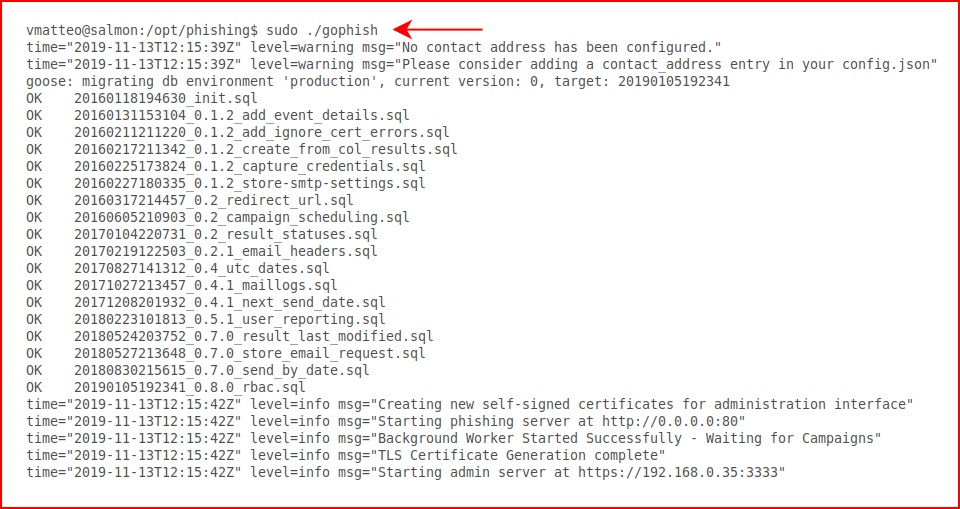
Looks like everything is functioning as it should, we browse to: https://server_ip:3333
The default username / password combo is --> admin : gophish
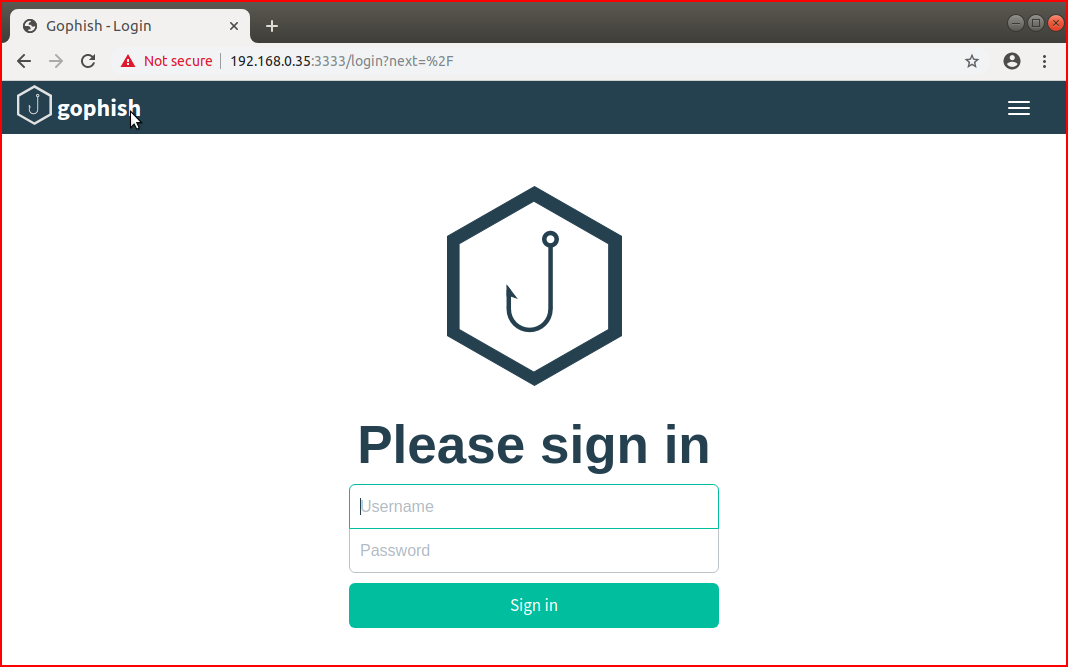
My inclination is to jump straight to the fun but since GoPhish doesn't make us change the password on login, I would be remiss if I didn't change the password to something stronger prior to doing anything else.
Enter the new password:
We hit Save:
And we're set.
In order to setup a campaign, we need to complete everything else first. In other words, the campaign will ask for users, landing page, etc., if those aren't built, we can't complete the campaign.
We start with users and groups:
We configure the user info and we select add:
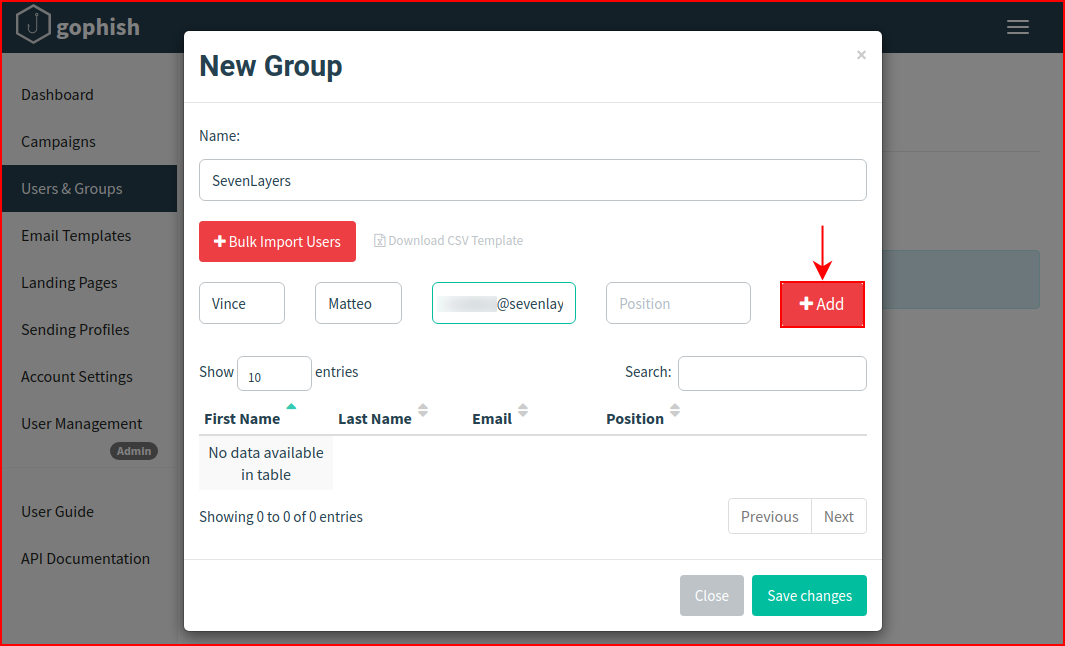
When we're finished adding our users, we select Save changes:
When we're finished, we get our confirmation:
Next, we need to setup an email template:
If you do a search for GoPhish Email Templates GitHub, you will find plenty of premade templates. You'll want to do this if for no other reason than to see the syntax for calling the various parameters. After that, you can construct your own.
Using a template I pulled from GitHub, I edit the source and add the template:
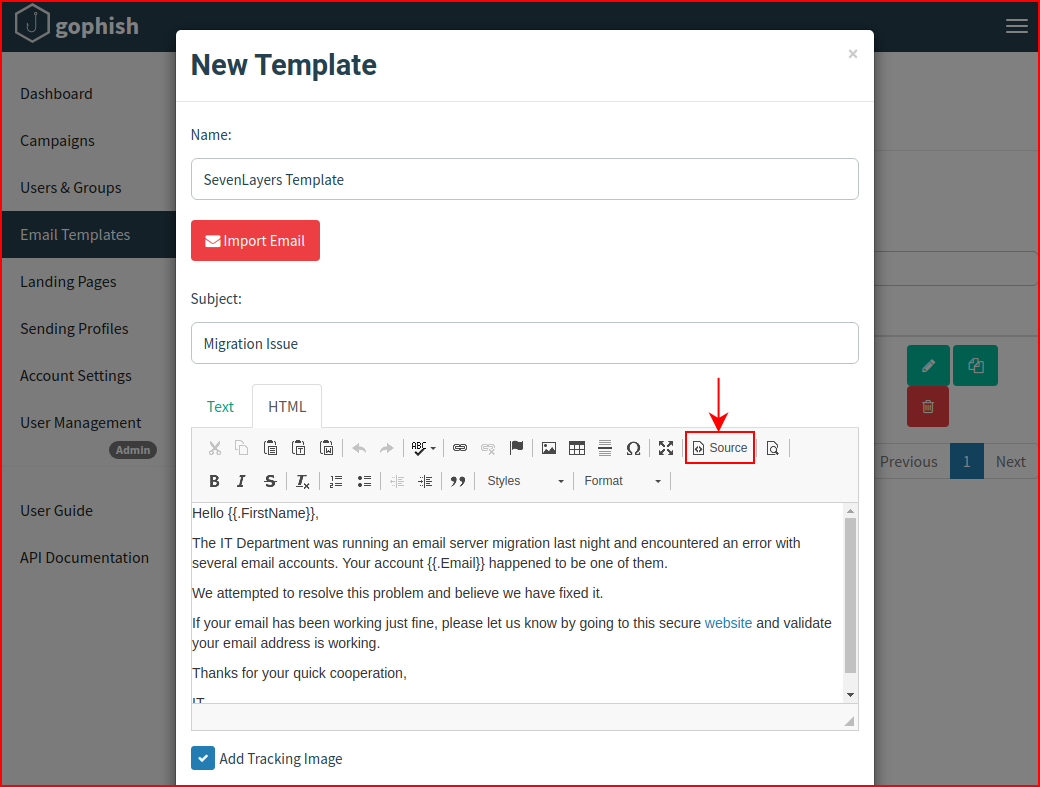
If you select the Add Tracking Image option, it will add the tracker syntax at the bottom of the template.
Next, we need to configure a sending profile:
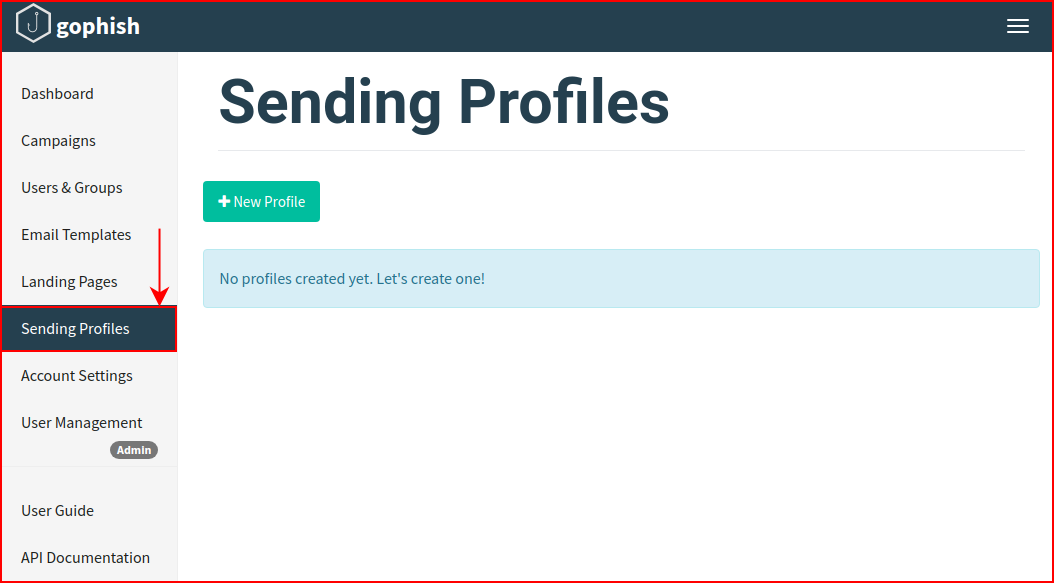
We populate this with our outbound SMTP information. I think I've mentioned this previously, it's wise to use a third party to handle this kind of traffic -- I wouldn't route this through my mail server. It also adds legitimacy if you route it through a reputable source.
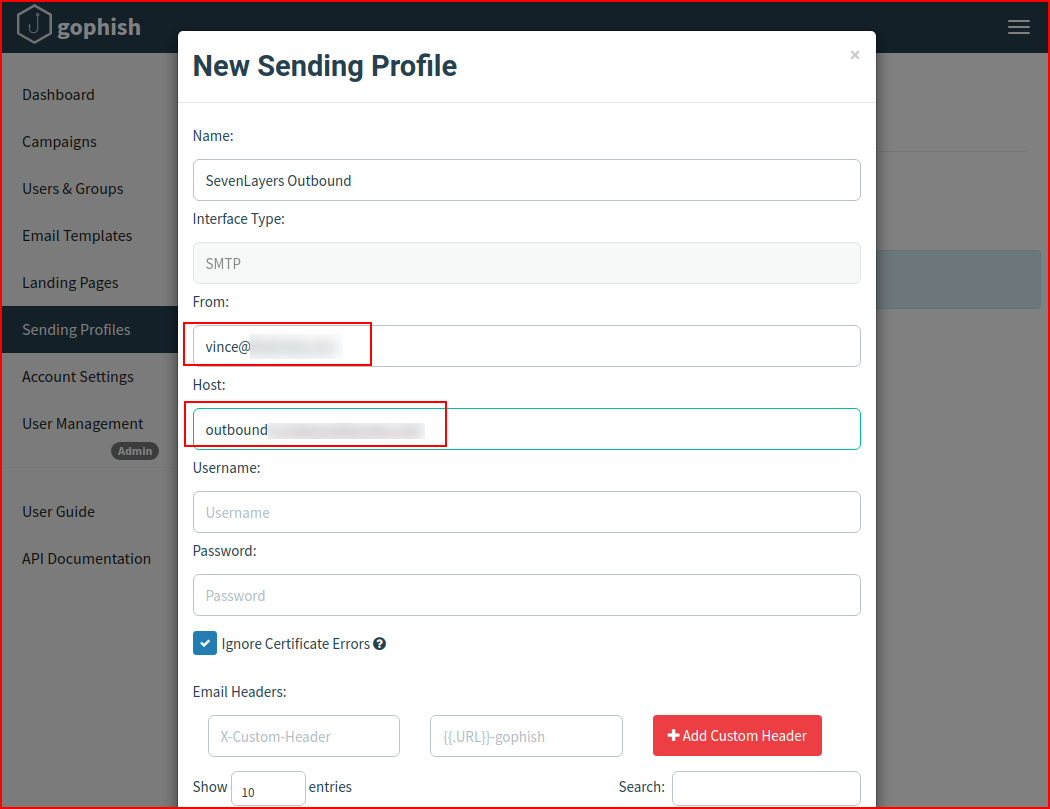
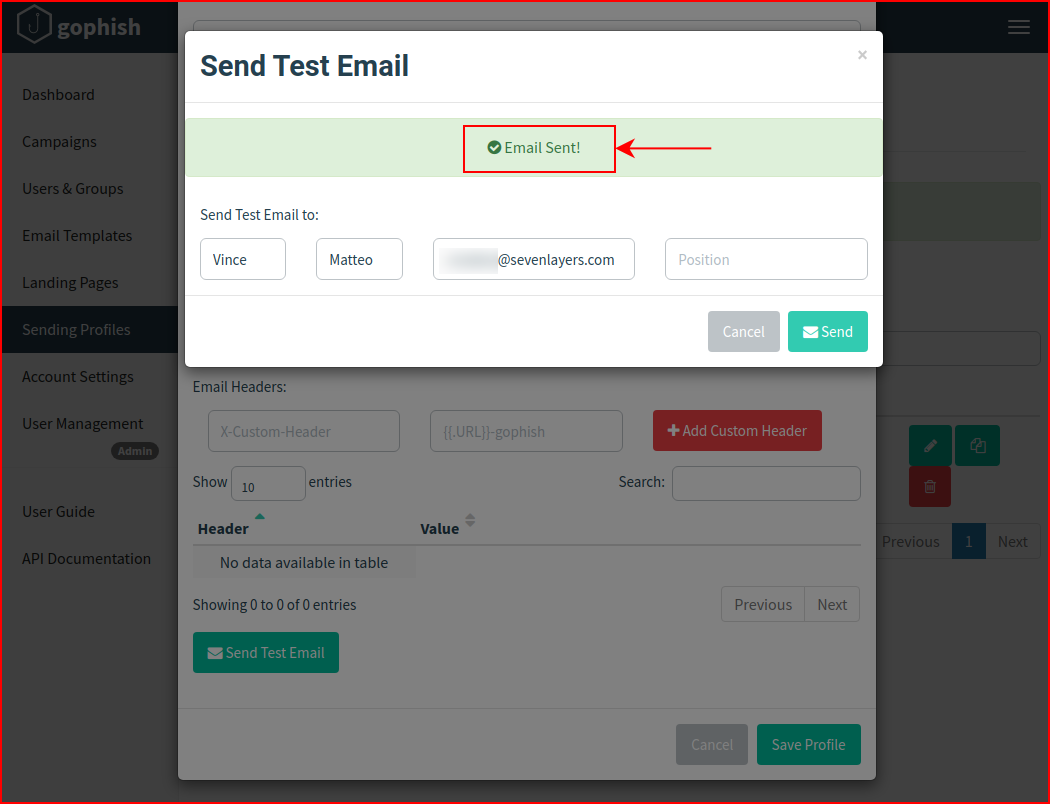
When we're finished configuring the outbound SMTP information, we run a test to make sure it's working:
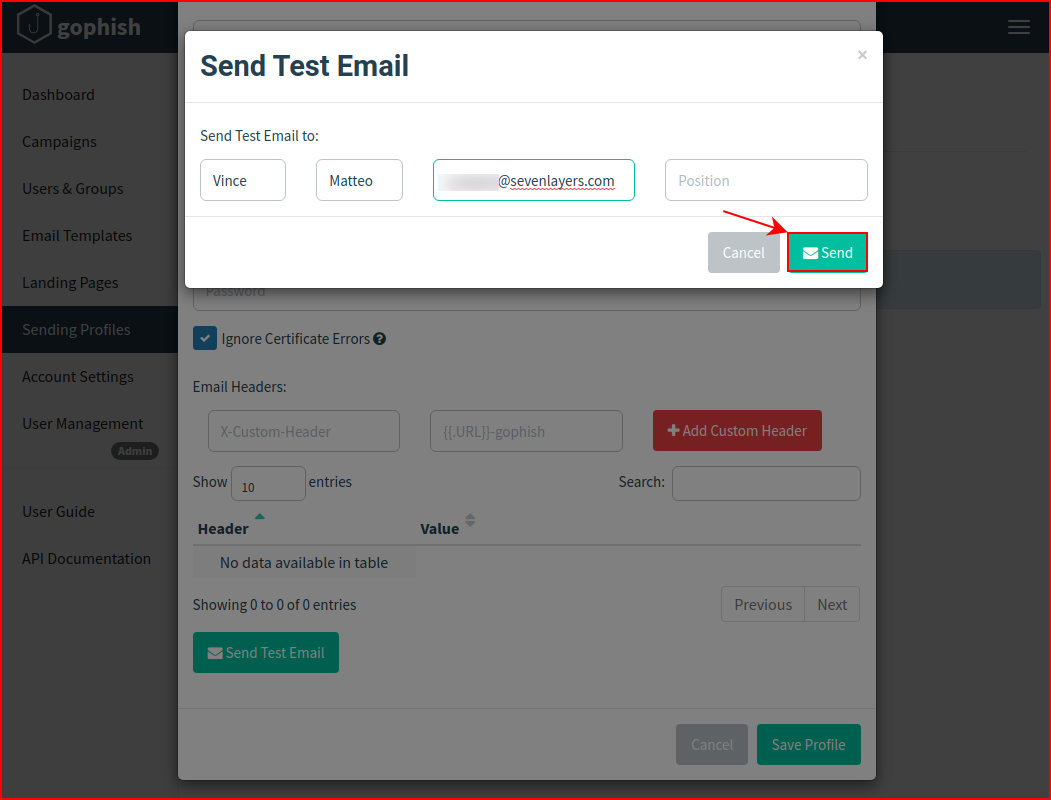
Our test was successful:
And now, we move on to Landing Pages:
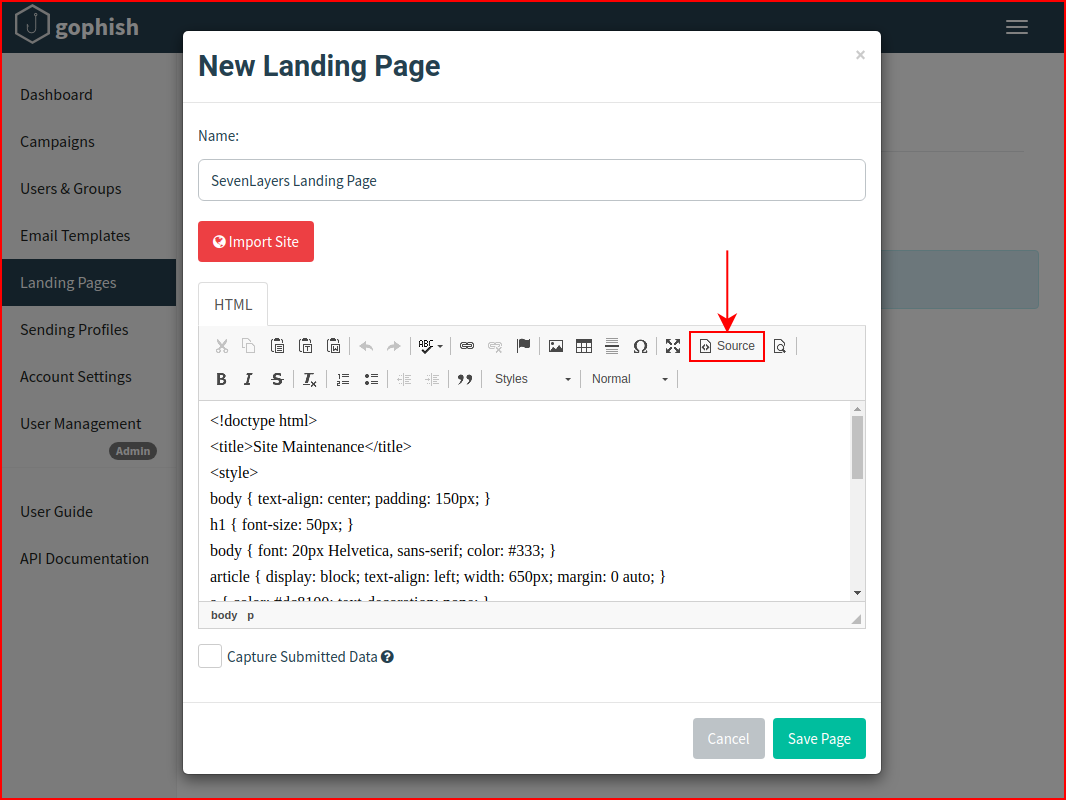
Our plan is to phish someone, and we're going to send them a link, where will they go and what will they see? Depending on what we're trying to accomplish, it could be any number of possibilities. Are we just testing whether they'll click a link? Are we testing to see if they'll click a link and enter credentials? Where we send them and what they see will vary based on those answers. For this test, I want to see if I can get them to click a link. When they hit the landing page, it will show the site in maintenance mode:
When we're finished:
Finally! We can create a campaign:
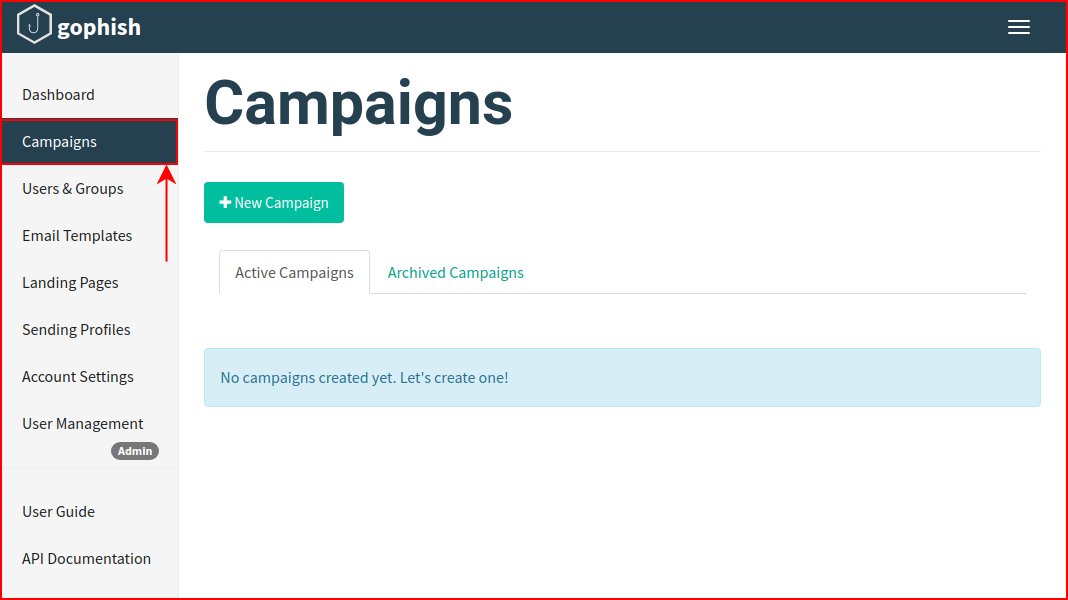
We start a new campaign and we populate it with all of the previously configured options:
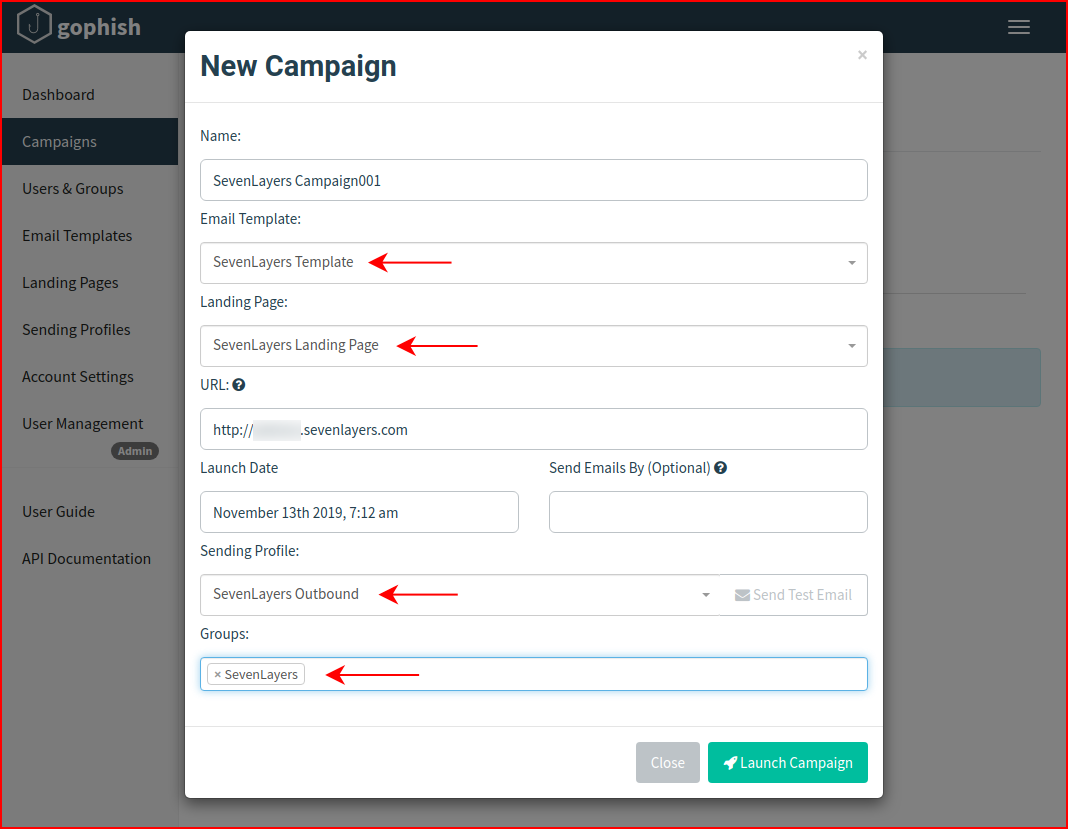
When we're finished, we launch the campaign:
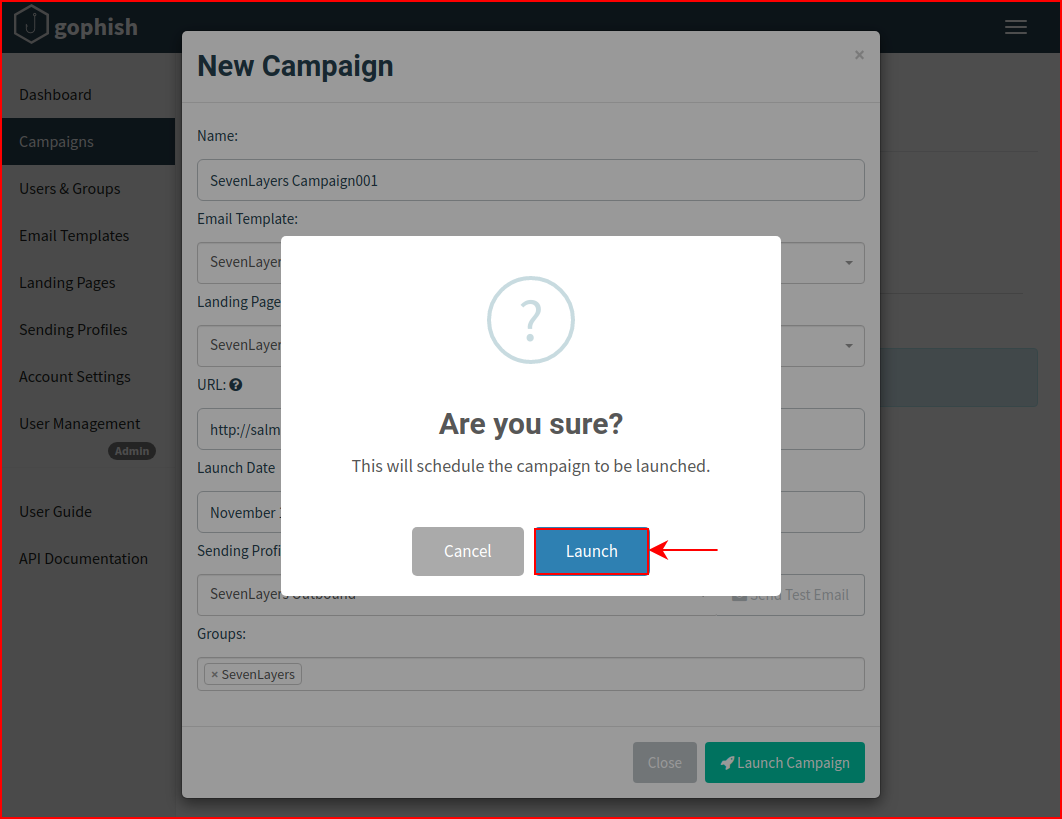
We see that the campaign is scheduled and since I didn't give it a future launch date, it will start immediately:
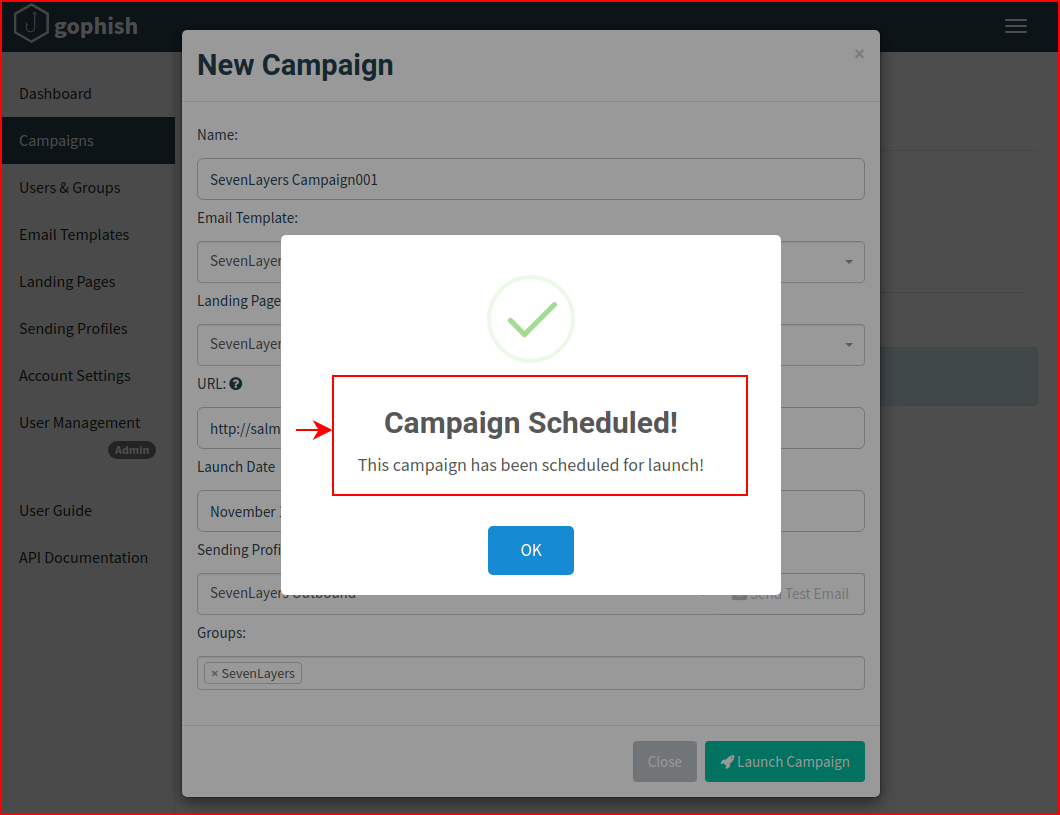
When we move back to the Dashboard:
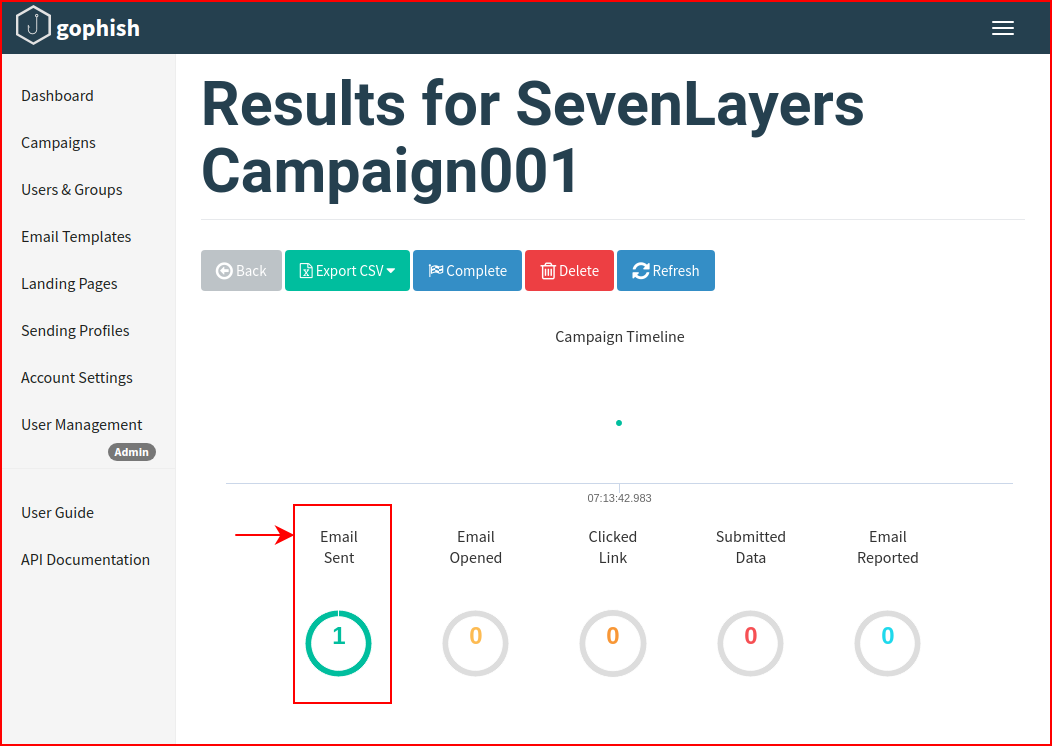
We see one email has been sent. When we open our mailbox, we see the message:
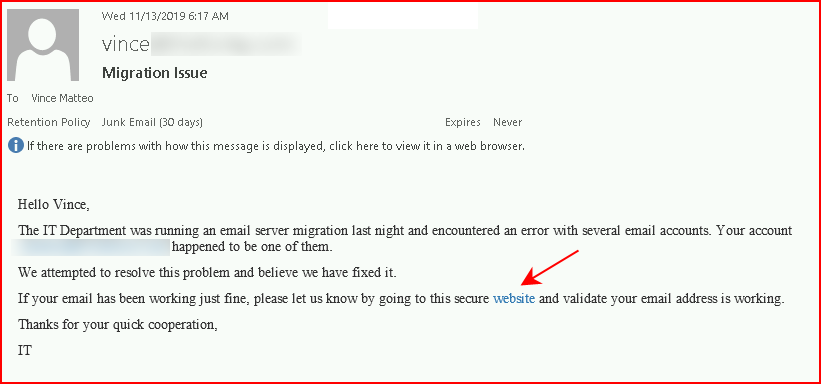
We click the link to the website and we are brought to the maintenance page:
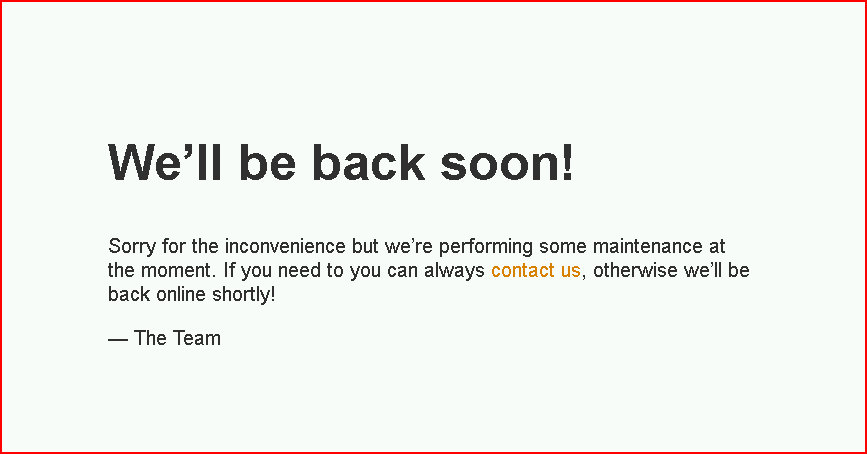
When we move back to the Dashboard:
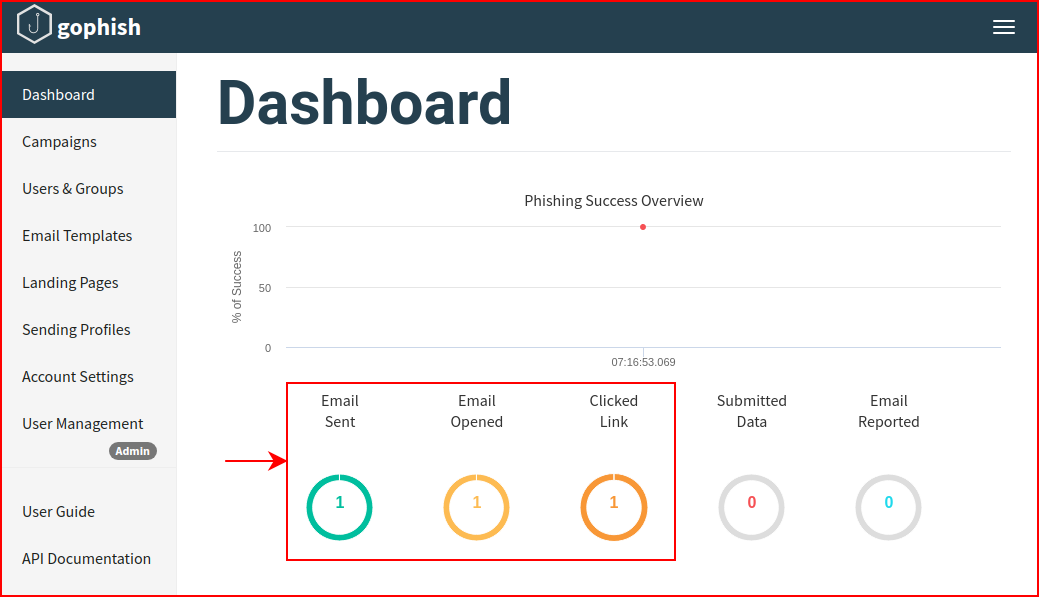
We see that the email was opened and the link was clicked. We dig into the details:
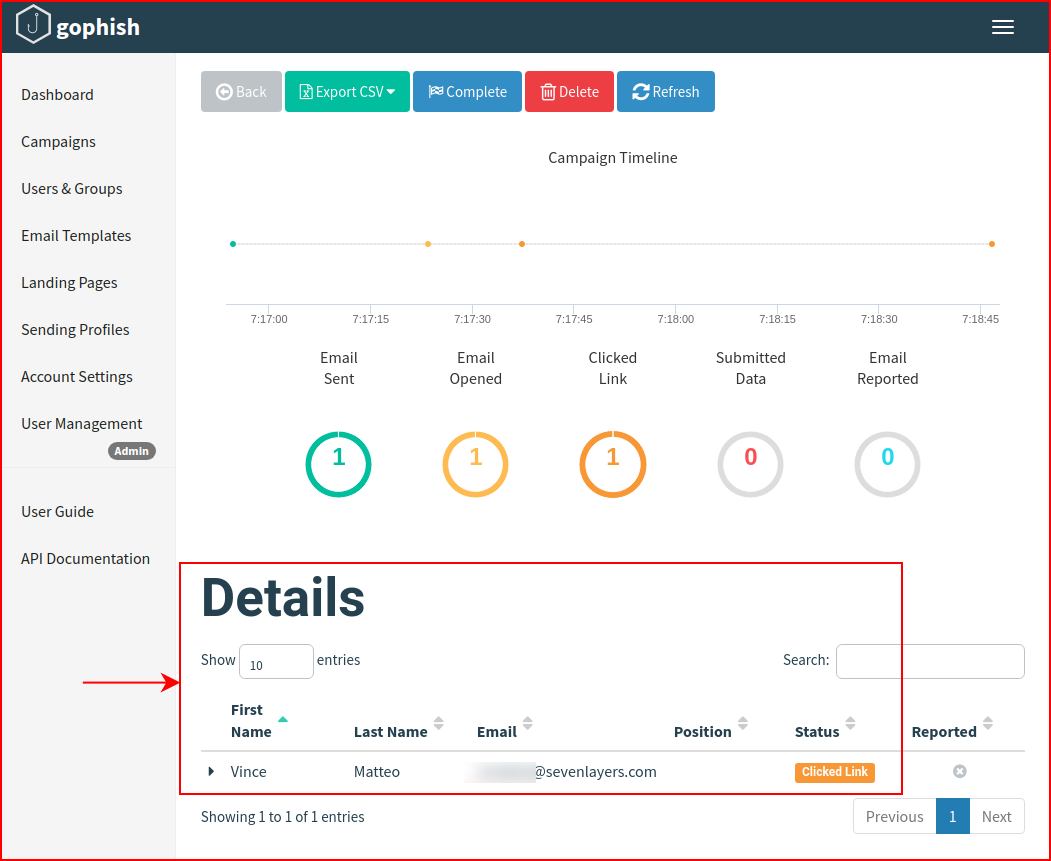
We see the offending user, yours truly.
That's a basic setup. Now let's clean it up. First, I want this to start as a service and not as root.
Create a user:sudo useradd -r gophish
Edit the service file:sudo nano /etc/systemd/system/gophish.service
In the file:[Unit]Description=Gophish Open-Source Phishing FrameworkAfter=network.target[Service]WorkingDirectory=/opt/phishingUser=gophishEnvironment='STDOUT=/var/log/gophish/gophish.log'Environment='STDERR=/var/log/gophish/gophish.log'PIDFile=/var/run/gophishExecStart=/bin/sh -c "/opt/phishing/gophish >>${STDOUT} 2>>${STDERR}"[Install]WantedBy=multi-user.targetAlias=gophish.service
Create the log directory and give our user permission:mkdir /var/log/gophishsudo chown -R gophish:gophish /opt/gophish/ /var/log/gophish/
Give our user permission to launch the service on TCP ports:sudo setcap cap_net_bind_service=+ep /opt/gophish/gophish
And finally, we're going to add the service, start the service, enable the service, and check the status of the service. sudo systemctl daemon-reloadsudo systemctl start gophishsudo systemctl enable gophishsudo systemctl status gophish
If all goes well, the service should be running as the user gophish and it will launch on reboot.
Lately, I've been spending quite a bit of time looking into canaries, deception products, etc. In that line of thinking, GoPhish could easily be used as an early warning detection system. Think about it like this -- you notify your users that every Monday morning, they will receive an email with the subject: "Credentials Change" and in the body, some message about changing credentials for some resource. You could add a link to a landing page. Everyone in the company knows about the email, nobody opens it. It just sits in every mailbox as bait. You could script the removal and send another the following Monday. Btw, you can use Google Analytics similarly.