Windows Privilege Escalation
If you blink, there will be another privilege escalation script and as far as I can tell, they seem to be the work of people honing their skills with a particular language or platform. As such, they tend to go without updating not long after they are produced. On the Linux side, there is (was) a popular script, in Kali, unix-privesc-check from Pentest Monkey. When you're working with old machines, this is a good one and one that I've used for many reasons. First, it works a lot of the time. Second, when it's finished, it lists kernel exploits. This is all great until you move into modern systems, then the script produces a whole lot of something without the glaring "use this to get root" at the end. Then you're destined to hunt through the miles of information it provides.
But that's sort of the point to these scripts. Most of them are just an aggregate of information. Here's what's installed. Here are the processes running. Here are the THIS and THAT. Finding the nugget is up to you. Does that mean they are all the same? No. I most definitely prefer some over others but that's the case with most of these tools I like GoBuster but some like DirBuster -- it's just a preference. For Linux, I like a few, BeRoot is one that isn't stock with Kali that I'll use from time to time.
Initially, I shy away from the scripts because sifting through the lines is tedious and I'll manually search for the obvious. The same can be said for when I land on a Windows machine. Rather than go into the manual enumeration, I'll just point you to the NUMEROUS posts on the subject that you can search out. Fuzzy Security's post on Windows Privilege Escalation is comprehensive.
This post is about the tools. I mostly like the tools developed in Powershell because Powershell is native. BeRoot also works on Windows but it's written in Python which is not native. Moving along...
So here we are, we have a low privileged shell on a Windows machine: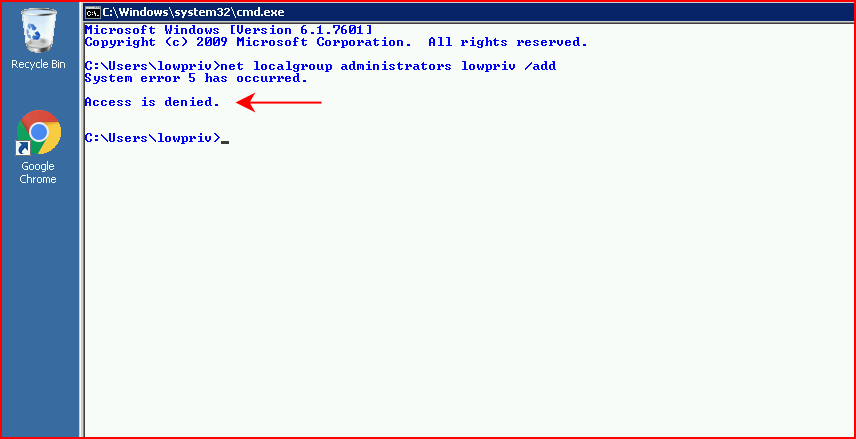
Seatbelt is written in C# and you'll need to compile it. There isn't a binary available for download and if you find one, you might want to think about that for a moment. ;)
In order to compile, we need Visual Studio Community and we want to open the solution:
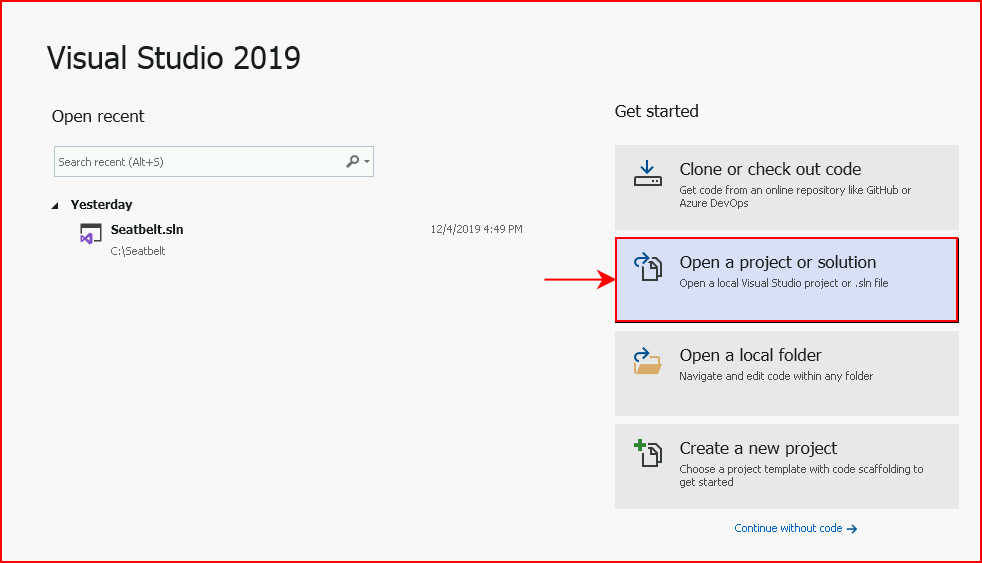
We point it to Seatbelt.sln:
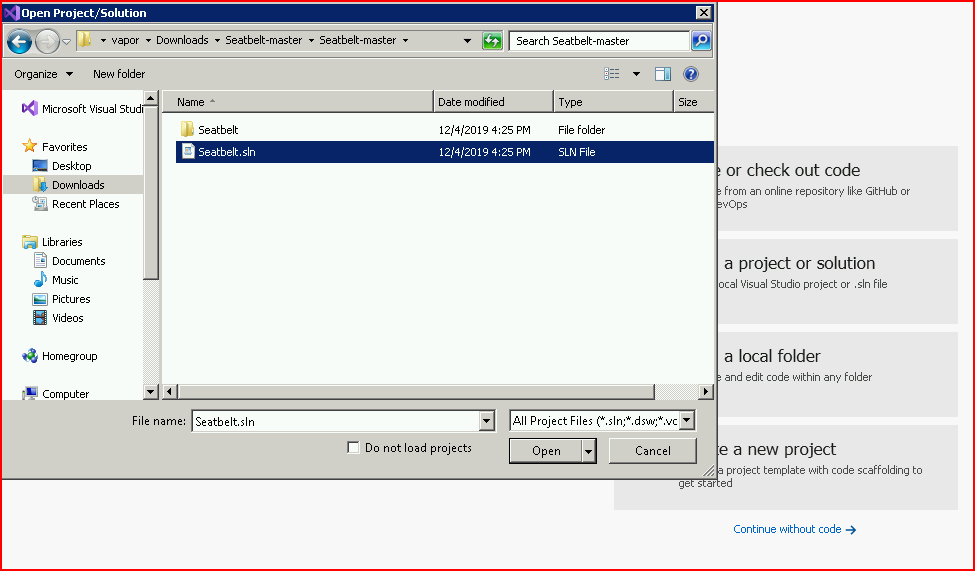
It loads:
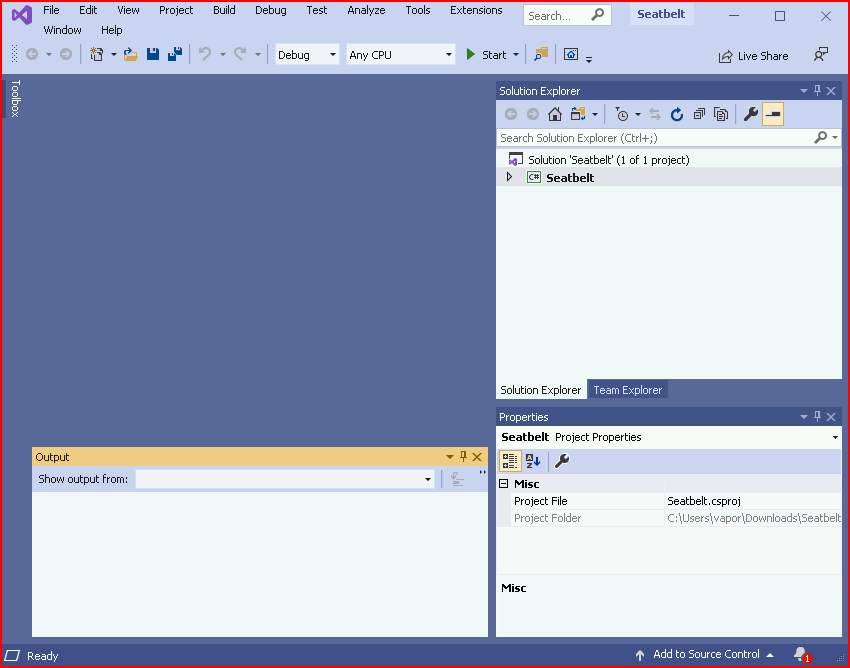
Under Build, we choose Build Solution:
When it's finished building, it provides us with the location of the Binary:
When we execute it without any flags:
The screen scrolls by while all of the options are shown to us: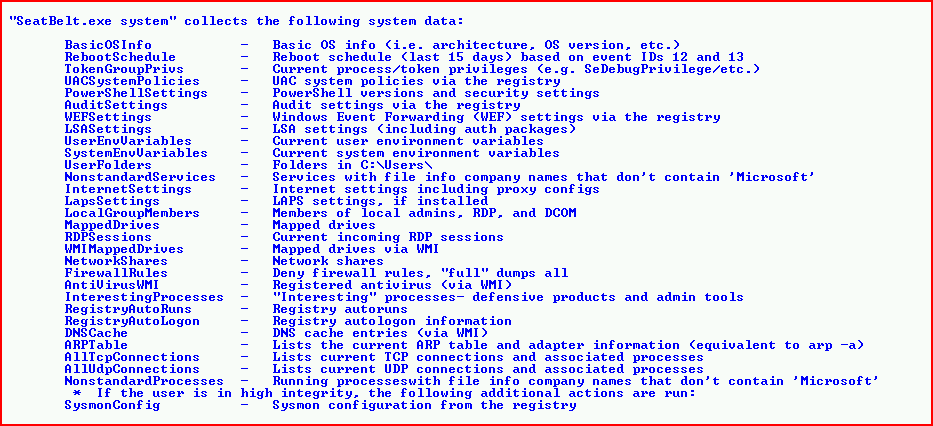
If we choose BasicOSInfo:
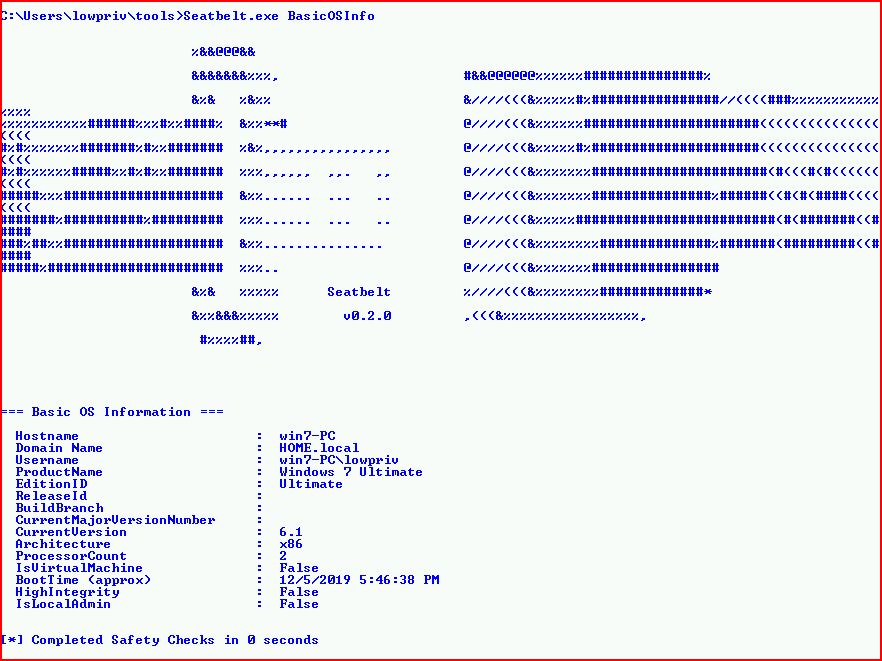
We get just that. If we choose all and direct it to an output file:
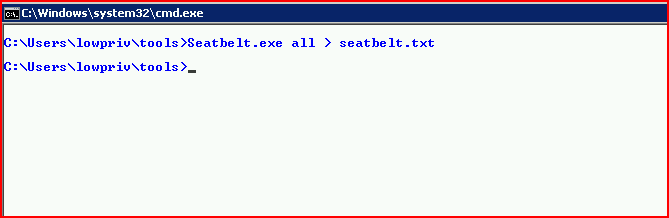
We get a lengthy output to sift through:
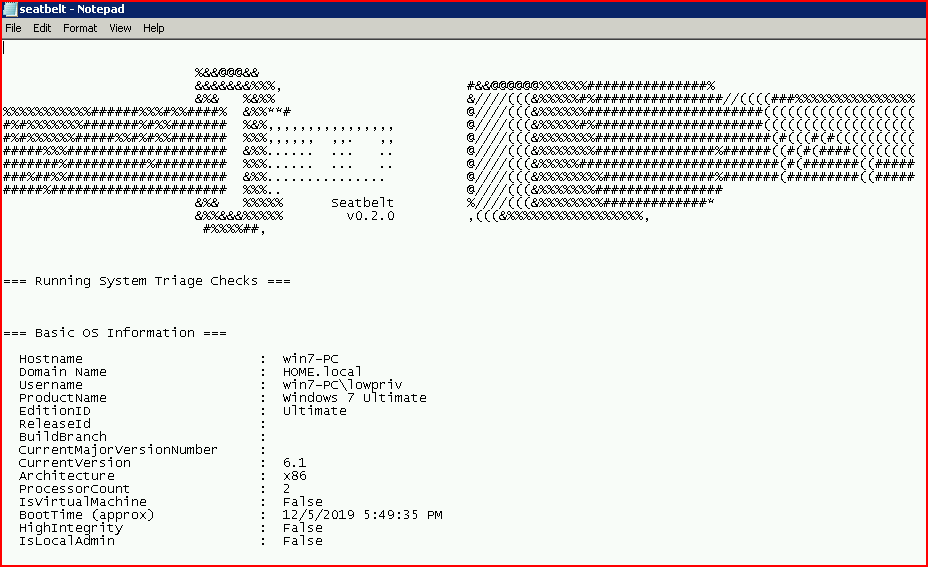
Complete with tons of information:
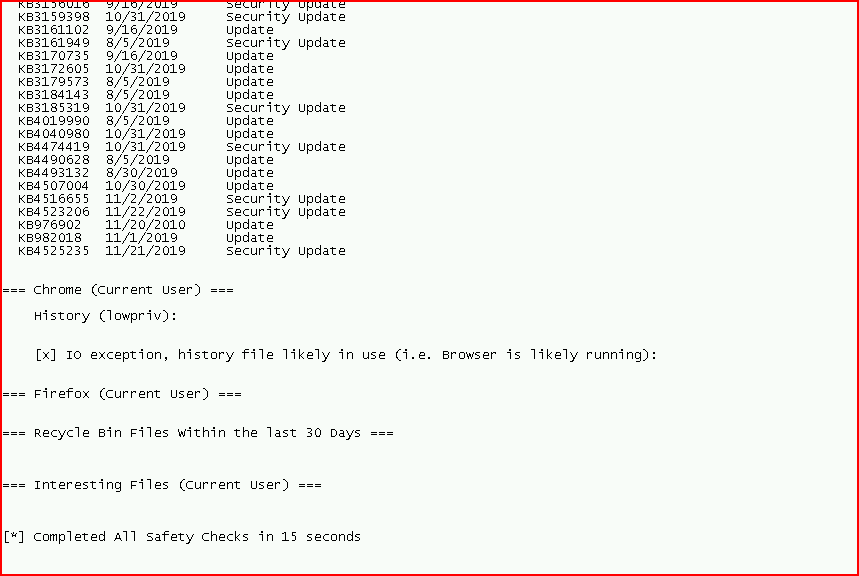
Not dissimilar to Pentest Monkey's script, we have the equivalent of Standard and Detailed with all and full:

No need to provide a screenshot of the output, you can imagine it's just like what you saw above but more.
From here, we move to the Powershell scripts -- first, Sherlock:
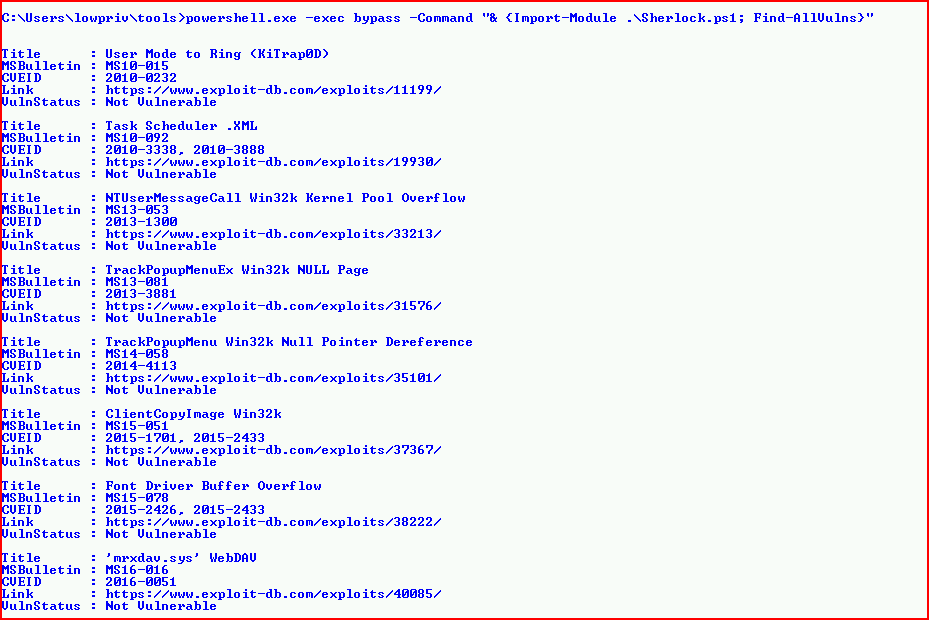
This one is a little more specific and less broad. Its purpose as far as I can tell is to hunt for unpatched vulns. With the system above, it doesn't find anything of use to us. Moving to another machine though:
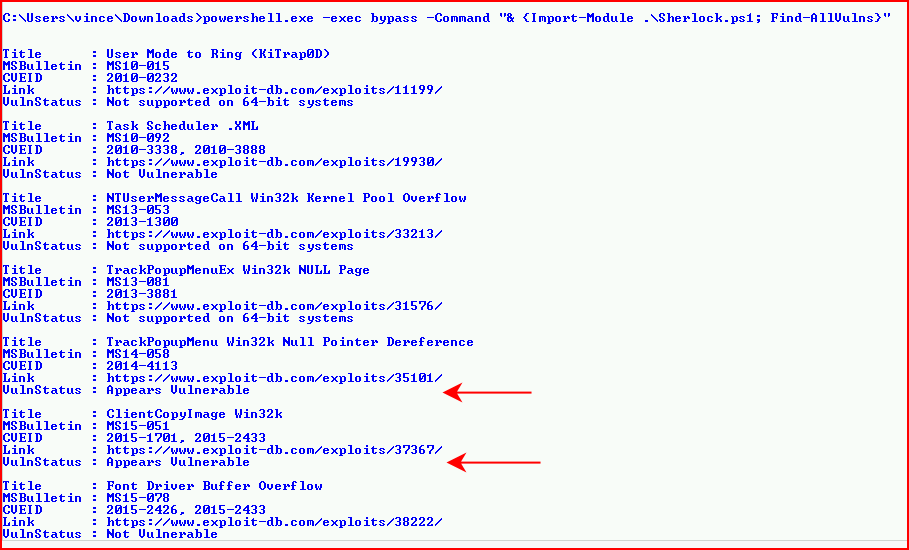
We find a few unpatched vulns which we can exploit. I think the Metasploit Exploit-Suggester would also find these, FYI.
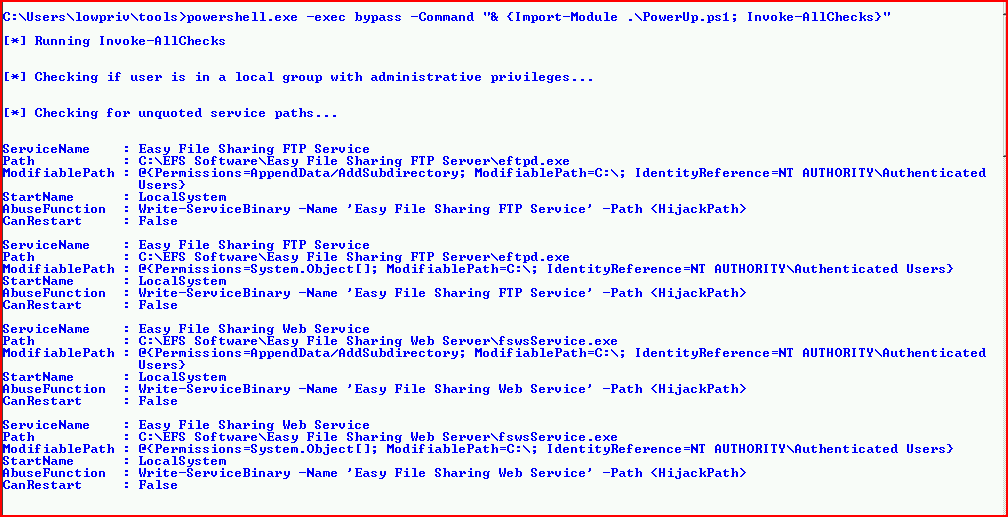
Next, PowerUp which is more along the lines of seeking out every detail about the system:
And last for this post but not the last of existing scripts, Jaws (Just Another Windows Enumeration Script):
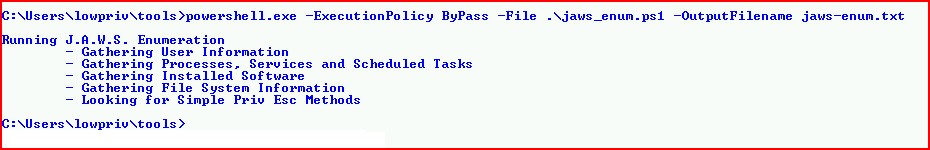
Personally, I like this one because of the output. It's a preference and I wouldn't say it's any better or worse than the others.
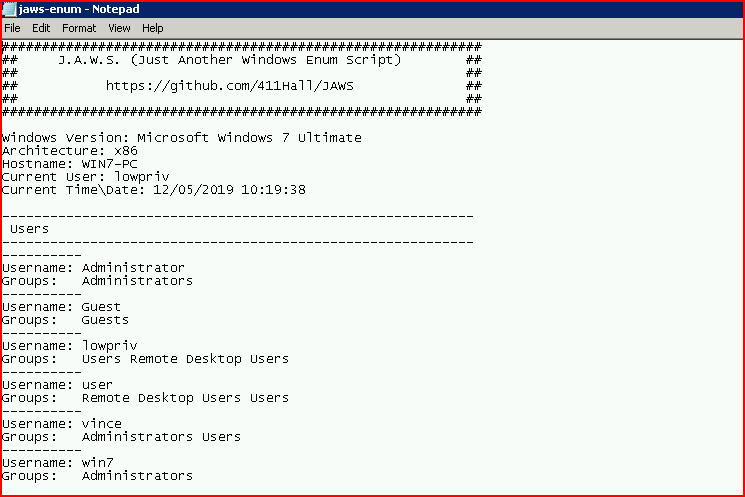
The real point is not that one is better than another, it's that you don't even know if they exist unless you happen to stumble across one. I only stopped using the Pentest Monkey script because I found the Linux Privilege Escalation script. I stopped using it when I found BeRoot. Rather, I shouldn't say that I stopped using it, I stopped leading with it.
As I mentioned above, I like Powershell scripts because the language is native. I want what works well and what gives me the least amount of grief. Powershell fits that bill most of the time. Seatbelt is good too because it's an exe and it goes unnoticed by some antivirus.
Hope this helps....