Parameth Parameter Brute Force
I had a need for a tool the other day and when I searched for: "php parameter brute force tool" -- I came up with Parameth. The description states: "This tool can be used to brute discover GET and POST parameters. Often when you are busting a directory for common files, you can identify scripts (for example test.php) that look like they need to be passed an unknown parameter. This hopefully can help find them."
I've only played with this a bit and it doesn't seem to work on everything but it did work when I needed it.
This is their example that I modified because, honestly, it didn't make sense and it makes more sense this way: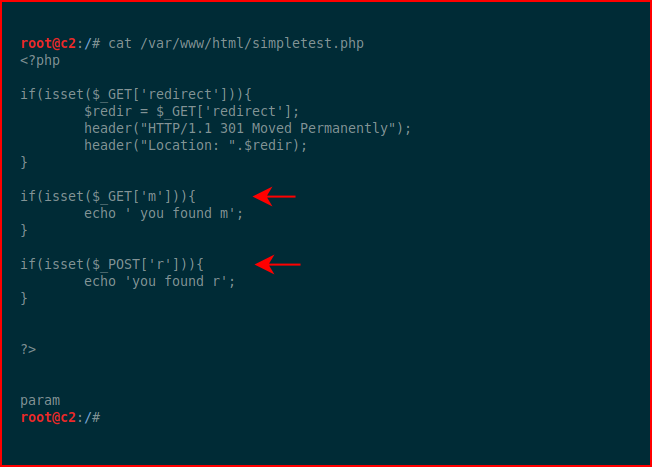
Basically, we have a GET parameter and a POST parameter. Let's say in our fuzzing process, we find simpletest.php but we don't know what's under the hood:
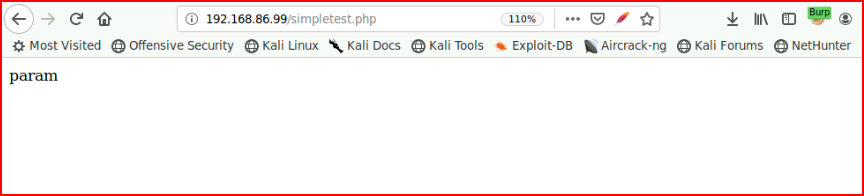
We point Parameth at it and it does its thing:
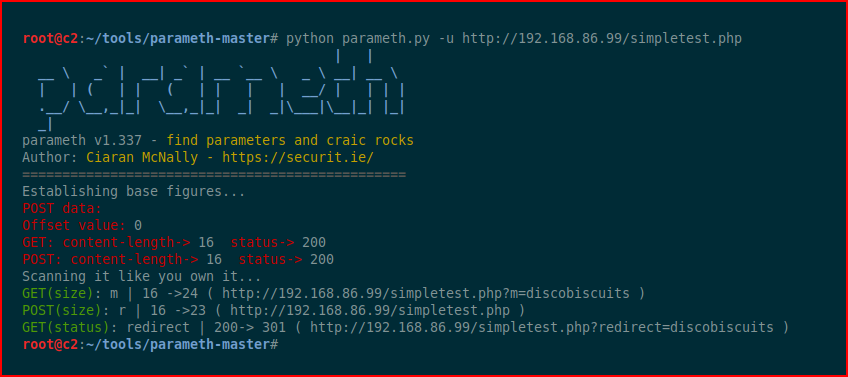
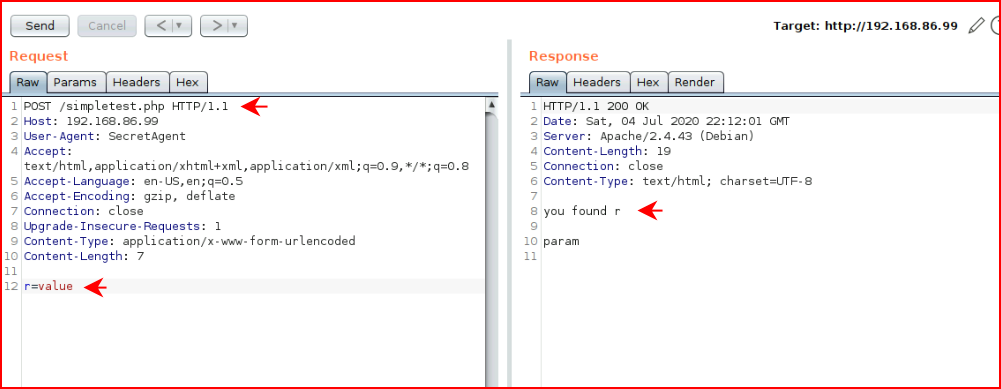
It uncovers both the GET and POST which allows us to do the following for the GET:
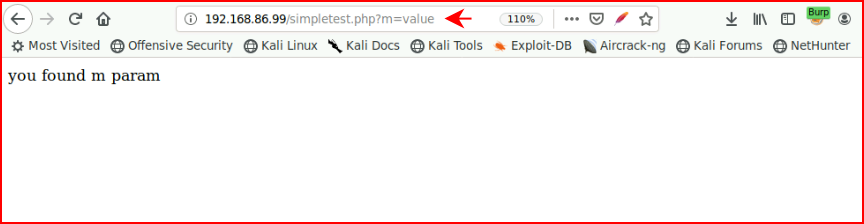
And for the POST, I moved this over to Burp:
I've already used this a couple of times in the last week and it was able to uncover the parameters. Pretty cool...