EmailGen Email Harvester
EmailGen (found here) is an email harvester that was based off of another tool but simplified. Those are my words, not those of the maker. Prior to using this tool, you could setup a free Hunter.io account and use the API but that is not necessary.
From their Github page:
The example given is as follows:
./EmailGen.rb -c "Microsoft" -d "microsoft.com" -f "{first}.{last}@{domain}" -o microsoft-emails.txt
Searching on a known domain:
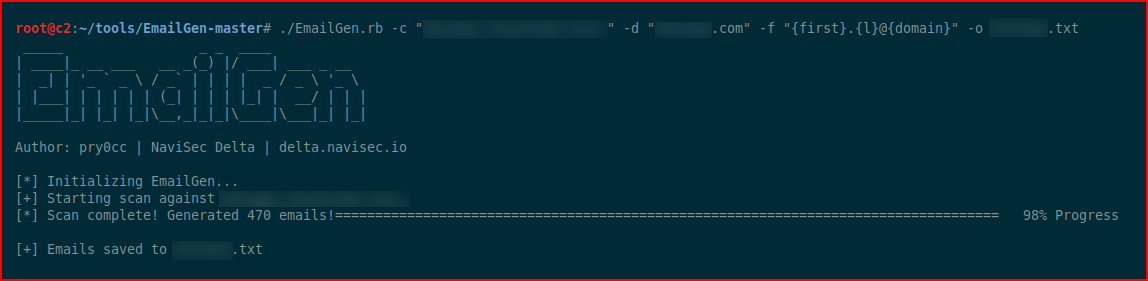
It harvests 470 email addresses. Here's what I can tell you about those email addresses:
1. Some of them are legitimate.
2. Some of them have never existed and I don't know where they came from. If you Google some of those invalid email addresses, you come up with nothing.
3. Some of the targets you'd like to get are in the list and some of them aren't. For example, this list contains all of the C-level positions except for the CFO.
4. It takes SECONDS to create this list which is awesome.
5. This list is by far the most comprehensive list of addresses and it would be a great way to start off a phishing campaign.
6. ^^ To that point, if this were a black box audit, I don't have a better / faster way of generating this type of list.
When we view the list, the valid addresses mostly appear in the top and when you get down to the bottom, especially 450-470, those addresses are a mystery.
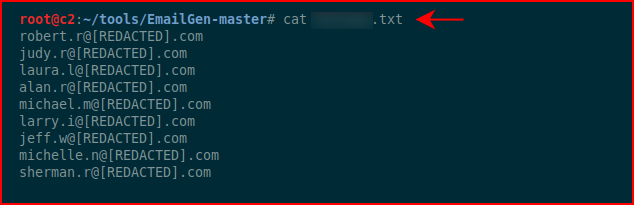
If you were trying to rule out good from bad, there are tools that can help with that as well but that's for another day.